Best topology for my network
-
Okay, another point or two for my own clarity.
If I want AAA to talk to BBB, the firewall rule would be:
On adapter AAA allow traffic from AAA to destination BBB. Yes?
The firewall is then smart enough to do that, I don't ALSO need a rule on adapter BBB to allow the incoming traffic, right?
Also, so far every rule I've seen written have the adapter and the source be the same. Is that always the case or is there a rule where the adapter is different from the network?
-
@tknospdr said in Best topology for my network:
On adapter AAA allow traffic from AAA to destination BBB. Yes?
If the adapter is an Interface, Yes
@tknospdr said in Best topology for my network:
The firewall is then smart enough to do that, I don't ALSO need a rule on adapter BBB to allow the incoming traffic, right?
Yes, you don't need, no.
@tknospdr said in Best topology for my network:
Also, so far every rule I've seen written have the adapter and the source be the same. Is that always the case or is there a rule where the adapter is different from the network?
Not sure what you're speaking of...
-
@tknospdr said in Best topology for my network:
If I want AAA to talk to BBB, the firewall rule would be:
On adapter AAA allow traffic from AAA to destination BBB. Yes?
Yes
The firewall is then smart enough to do that, I don't ALSO need a rule on adapter BBB to allow the incoming traffic, right?
Correct, rules are applied as the packet enters an interface not when it leaves. (Aside from floating which behave differently, ignore those while you get started)
Also, so far every rule I've seen written have the adapter and the source be the same. Is that always the case or is there a rule where the adapter is different from the network?
Well see my post above https://forum.netgate.com/topic/181507/best-topology-for-my-network/16. It’s rare but possible to route a network behind pfSense LAN, without using NAT. As you get familiar just assume they are the same.
-
S SteveITS referenced this topic on
-
For the sake of FW rules, the physical adapter is completely divorced from the "interface" right?
I think part of my confusion lies in the fact that I have a physical adapter called ETH3, and I have a pfSense interface also called ETH3.My WAP is connected to physical adapter ETH3.
There are 3 pfSense interfaces going to the WAP.
ETH3 - 10.100.10.0 - WPA2 personal for authentication - HomeKit devices - SSID subspace
ETH3_20_SECURE - 10.100.20.0 - WPA2 enterprise for auth - computers and tablets - SSID secure_subspace
ETH3_30_LEGACY - 10.100.30.0 - WPA2 personal for authentication - older game handhelds - SSID legacy_subspaceSo when I remove all rules from interface ETH3, I can no longer get on secure_subspace because the WAP can't contact the RADIUS server to auth against. I surmised this based on the fact that if I was already connected to secure_subspace when I removed the rules I could stay on it, but no new devices could connect.
Also, so far every rule I've seen written have the adapter and the source be the same. Is that always the case or is there a rule where the adapter is different from the network?
Not sure what you're speaking of...
Sorry, wrong terms.
So far, every rule I've seen has the interface and the source being the same. For example:FW rule for interface CCC, source is always CCC.
If there's never a reason to build a rule for interface CCC where the source is BBB, why can we choose a different source? -
@tknospdr said in Best topology for my network:
why can we choose a different source?
Because if the interface network is a transit..
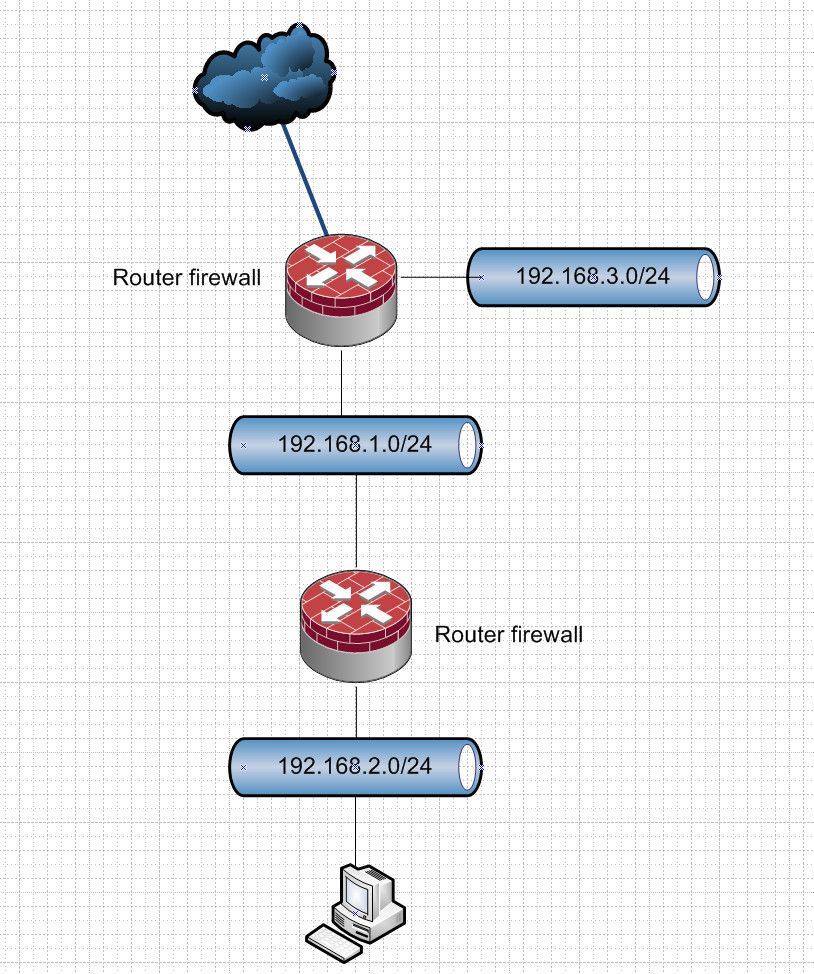
In such a setup for network 192.168.2/24 to get to say 192.168.3.0 it transits through the 192.168.1 network. So on this interface on the upstream router you would need to allow this downstream network 192.168.2/24 that is not the interfaces directly attached network 192.168.1
-
@tknospdr the interface is on Interfaces/Assignment. The physical adaptor the interface uses is the port column. The port can be a VLAN. Firewall rules are on interfaces.
-
So in order to get RADIUS auth working on my WAP I had to put a rule on the ETH3 interface, even though the auth happens for clients on the ETH3_20_SECURE interface.
A little confusing when you're just starting out. -
@tknospdr what? Auth from an AP would come from the management IP, and what network that is on. Not what network you have setup for clients to use.
-
Trying to post a reply, but getting a error that Akismet thinks I'm spamming the forum.
-
@tknospdr IIRC that is relaxed when you get 5 upvotes, here.
-
@SteveITS
Appreciate it. -
@tknospdr I gave you some thumbs up - I show your at 5 now, you should hopefully be able to post what you were trying to post now.
-
Thanks. I figured we've beaten this thread for all it's worth and I should post additional FW questions in the proper section of the forum, so I had tried to post:
You seem surprised. Did I mention that I'm just learning all this? :)
My AP has no reference to or configuration options for a 'Management IP', so I had no idea the auth would be on anything other than the network that it was using that auth on.
I know now, and I appreciate all the help I'm receiving here.
But be prepared, I'll continue to have "dumb" questions, especially about the FW, until I... get it.
Like this one for instance