Can't reach printers after enabling 802.1x
-
@johnpoz Thanks for the response. I use a directprint.io cloud server to communicate with the printers and have been successful in having them on different vlans via the netgear switch and firewall rules (which I'm still locking down). I lose communication only when separating netgate port 4 out as a vlan via pfsense.
Netgear switch vlan config:
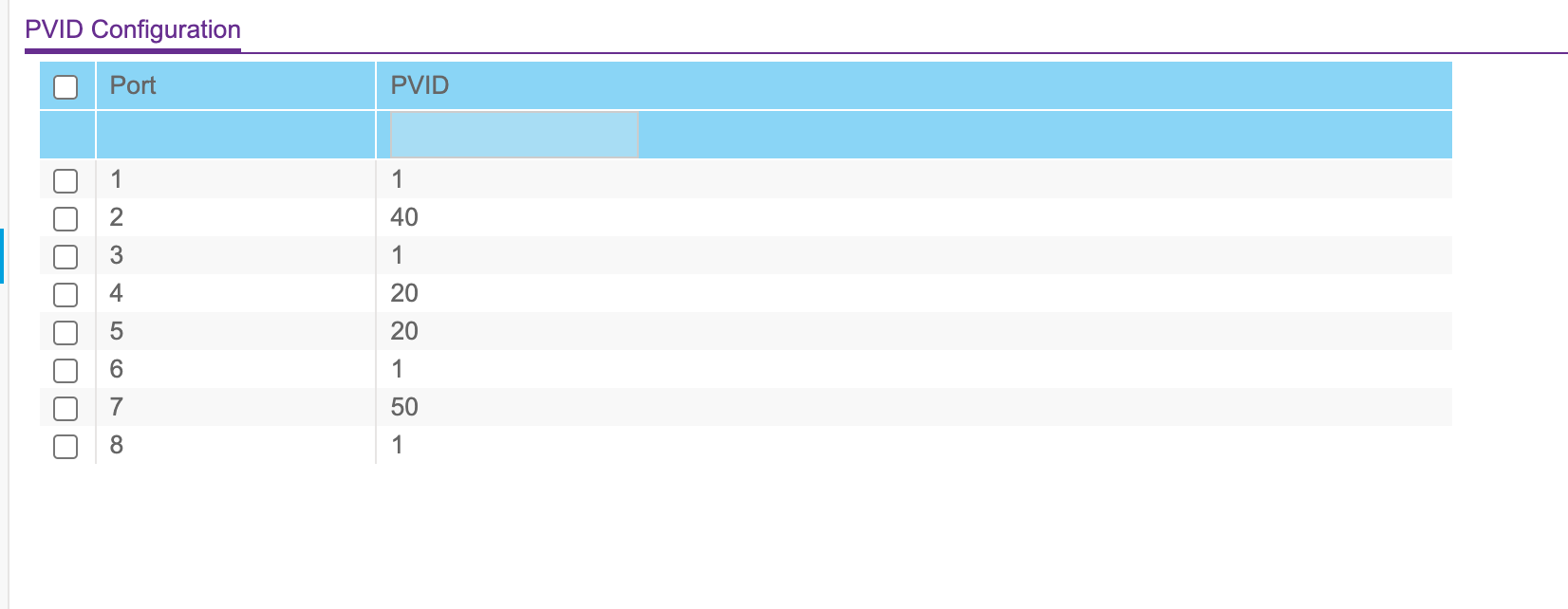
Wired printer is on vlan 40 through port 2 on the switch.
Pfsense rules:
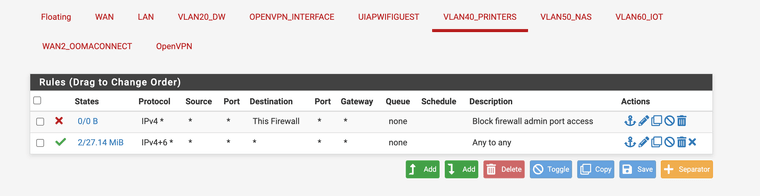
-
@SteveITS Thank you. I am trying to just isolate the one port as second WAN and I might be off the mark but I followed this guide to isolate the port.
-
@gmoye0124 the rules on the printer vlan would have nothing to do with someone talking to it from another vlan. The rules on the source of the traffic would be what would allow traffic to the printer or not. The return traffic would be allowed by the state.
I am not sure what directprint.io is, but I would guess your printer needs to be able to reach that?
If so your rules might be blocking it, because what is the printer using for dns - if its pointing to a pfsense IP, like the IP on pfsense vlan 40 interface. Your first rule would block access to that because its a any rule to any IP on the firewall "this firewall" alias is every IP on pfsense. You might want to allow dns to pfsense IP for example.
But I don't see any hits on the rule, that 0/0 B under states..
I would have to do some research on how that directprint.io thing works... But say you wanted to print to printer on vlan 40, lets for example say your printer IP is 192.168.40.100, and you wanted to print to that IP from the lan network, lets say its 192.168.1/24 then the rules on the lan would need to allow access to 192.168.40.100 on the printer port your using 9100??
And if your doing policy routing on the lan, and sending out some gateway that could be a problem as well. Can we see the rules on the interface your trying to print from.
Can you ping the printer IP from the device your wanting to print from?
My printer is on my 192.168.2/24 vlan, see I can ping it from my device on my lan 192.168.9/24
$ ping brother.local.lan Pinging brother.local.lan [192.168.2.50] with 32 bytes of data: Reply from 192.168.2.50: bytes=32 time=1ms TTL=254 Reply from 192.168.2.50: bytes=32 time=1ms TTL=254 Reply from 192.168.2.50: bytes=32 time=1ms TTL=254What is the configuration of pfsense opt2 interface.. How is it connected to that switch? this vlan 40 needs to be setup to get to that switch, either via tags or native (untagged)..
-
@johnpoz Sorry, I should have posted lan rules instead of vlan. My lan rules are not locking much down currently except GUI access (still working on that) and I have been successful in reaching the printers when 802.1q isn't enabled on pfsense.
LAN Rules:
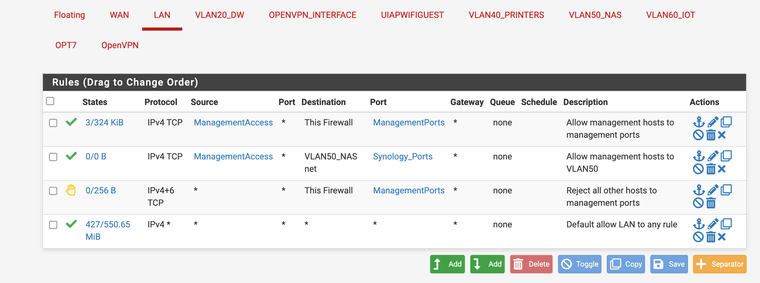
The issue only occurs when I enable 802.1q. Once I click enable, I am unable to ping or reach any printer. I would think there is an issue with having one vlan on the router and then another on a layer 2 switch but it's a bit beyond my knowledge.
-
@gmoye0124 said in Can't reach printers after enabling 802.1x:
The issue only occurs when I enable 802.1q. Once I click enable
Well if your going to tag the network pfsense - it would have to be tagged on the switch..
You only need to tag when you carry more than one network on the wire. Again how is this printer network from pfsense connected to the switch.. I saw only a pvid set on the port printer is on.
Where is the uplink from the printer to pfsense?
-
@johnpoz said in Can't reach printers after enabling 802.1x:
@gmoye0124 said in Can't reach printers after enabling 802.1x:
The issue only occurs when I enable 802.1q. Once I click enable
Well if your going to tag the network pfsense - it would have to be tagged on the switch..
You only need to tag when you carry more than one network on the wire. Again how is this printer network from pfsense connected to the switch.. I saw only a pvid set on the port printer is on.
Where is the uplink from the printer to pfsense?
I see what you're saying. I was definitely thinking about it wrong...
I have two separate switches with a printer on each. These switches are connected to ports 2 and 3 on Netgate. I believe I have the vlan groups figured out but need to test.I'll post my new setup and results shortly. Thanks!
-
@gmoye0124 if you have 2 different switches for 2 different interface on pfsense, that are native - ie not tagged vlans. Why are you tagging traffic on the switch?
Tags are "needed" when you carry more than 1 network on the same wire. If all that is going to travel on the wire is one network, then there is no need for tags. You could if you want tag the traffic. But then pfsense and the switch port its connected to would have to be setup for the tag.
-
@johnpoz Unfortunately the two switches do both carry multiple vlans. One switch is located at the Pfsense but because of wiring difficulties and location of some devices, the second switch is located in a different room. I have vlan 1 and 40 going through one switch and vlan 1,20,40, and 50 on the other. Then, I have a Unifi AP with vlan 1,30,40, and 60.
I see that I was setting up the pfsense network completely wrong but I believe my switches are in the correct configuration.
-
@gmoye0124 said in Can't reach printers after enabling 802.1x:
vlan 1 and 40 going through one switch and vlan 1,20,40, and 50 on the other.
pfsense 1U,20T,30T,40T,50T,60T -- switch1 -1U,20T,30T,40T,50T,60T-- switch2 -1U,30T,40T,60T-AP
You can if you want break up those on 2 different switches and use 1U on both - but this wouldn't be the same network if connected to different ports on pfsense.
And or your AP.. But you can not really put same multiple vlans on different ports on pfsense.
if your going to have 3 different interfaces on pfsense connected to 3 switches and AP.. You can not really handle vlans over the multiple interfaces without some bridge setup. If you need a vlan on more than one switch/ap - then best to plug in to another switch.. That has all the vlans on it you want, etc.
And Tags over a bridge more than likely going to be very problematic if even possible.
-
@johnpoz Interesting. I thought I could break out one of the ports and keep the other three as a switch. I do have an extra port that I can connect the second switch to the first but I'll need a bigger switch to add the ap. I guess that's the direction I will go since I don't want to go down the bridging route.