How to block random VPN attempts
-
How to block random VPN attempts
Easy !
Instead of using the 'default' WAN firewall rule like :
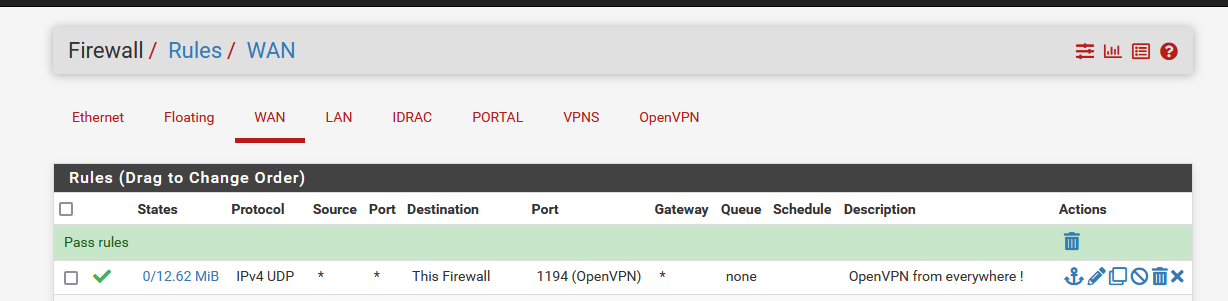
Make this :
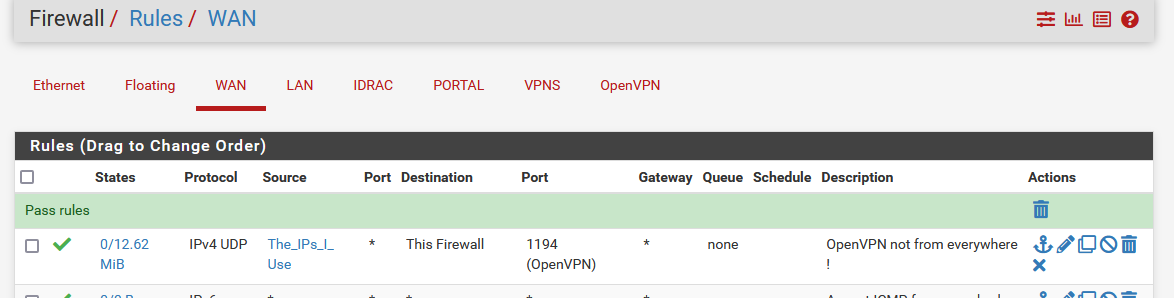
Don't relax yet, there is still something to do.
You saw the source alias called "The_IPs_I_Use" ? You have to add all the IPs that you allow. These are the one you use when you connect to pfSense OpenVPN.
It won't take long before you discover that this isn't the perfect solution yet ;)Situation : you live in the USA.
You could use the pfSense package pfBlockerng, and place a firewall above the OpenVPN firewall I've shown above, where you block all IPs that do not come from "USA" with GEOIP blocking (still not perfect, but it would help).Btw : OpenVPN is secure. Normally, you can leave the OpenVPN visible = exposed on the Internet. If 'they' don't have the key, they can't enter. Like your house front door or phone number, if you don't want them to 'knock' or call you, remove the front door (or put a guy or 'thing' in front of it that 'filters' who approaches your house), or stop / quit using the phone.
You are using, and are part of a public network. If you don't want the public coming over : stop the OpenVPN service. They will still keep trying to connect to your VPN, even if you didn't have it activated. That's how Internet is these days. -
Yes, when you create an IPSec instance on WAN it automatically adds rules to allow traffic from the configured remote side. If that's a remote access instance it allows connections from any IP.
So disable those automatic rules and add your own pass rules to limit that.
-
An idea ?? Maybe move the server instance from Wan to Localhost. Then create port-forwards for the IKE VPN, restricted to only your mobile provider subnet. That way the FW rules should block the rest of the world even starting the VPN process on port 500 ?
-
@pwood999 said in How to block random VPN attempts:
Wan to Localhost
That solution, needs one step more : the NAT rule coupled with the firewall rule.
Have the VPN service/process listen on the WAN interface, that's where the traffic comes in.
This needs a firewall PASS rule (not a firewall+NAT rule) that can be set up with to match :
Protocol used
Destination Port
Source AddressesThe destination would be "This firewall" as it includes the WAN IP.
-
@Gertjan said in How to block random VPN attempts:
That solution, needs one step more : the NAT rule coupled with the firewall rule.
Have the VPN service/process listen on the WAN interface, that's where the traffic comes in.
This needs a firewall PASS rule (not a firewall+NAT rule) that can be set up with to match :
Protocol used
Destination Port
Source AddressesThe problem here is the OP is using a road warrior where the source address is unknown.
I had been thinking to use schedule so things are not left open all the time...that's what attracted me to pfSense.
-
@NollipfSense said in How to block random VPN attempts:
The problem here is the OP is using a road warrior where the source address is unknown.
True.. But you can take an educated guess for example that it would be some IP from the US only.. Or some other country where your users reside.. Etc..
I have no idea what IP my plex users might come from.. But pretty sure it won't be from Russia or China, etc.. Or any other IP other than some US ip.. Same goes for users connecting to my openvpn, etc.
So I created this list of IPs that are allowed.
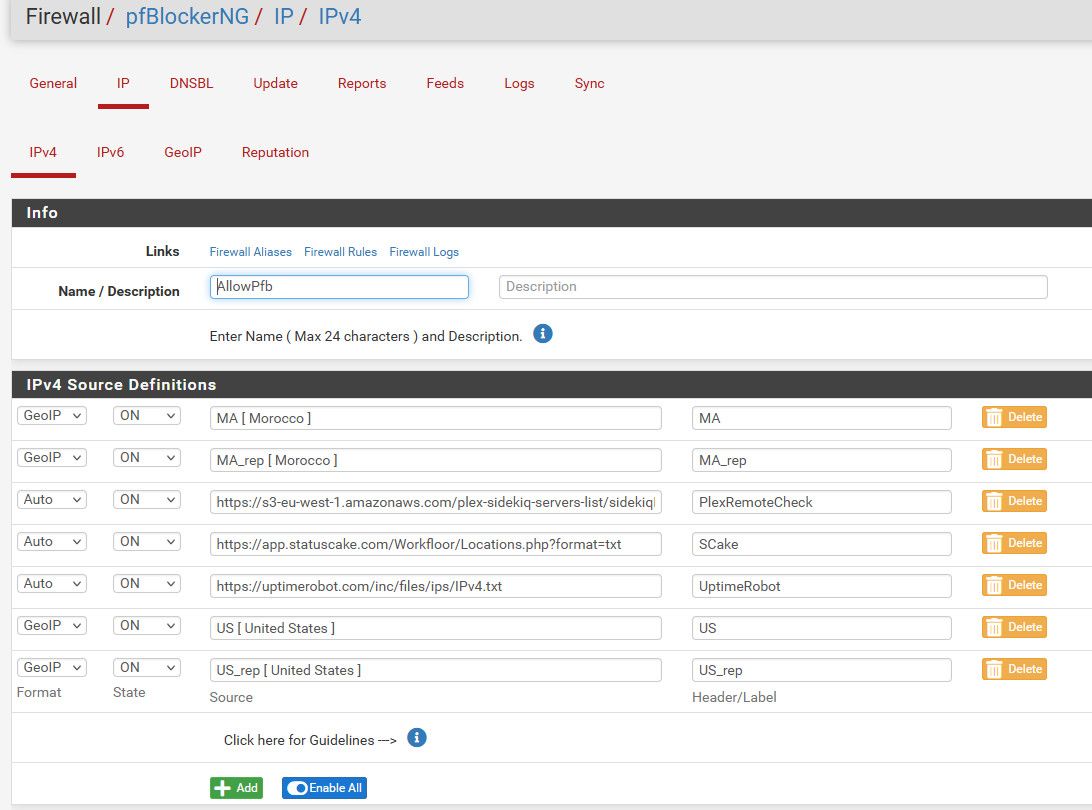
Now I use those in my forwards/Rules - so only included in that allowPfb list are allowed to talk to those ports and services that are forwarded.
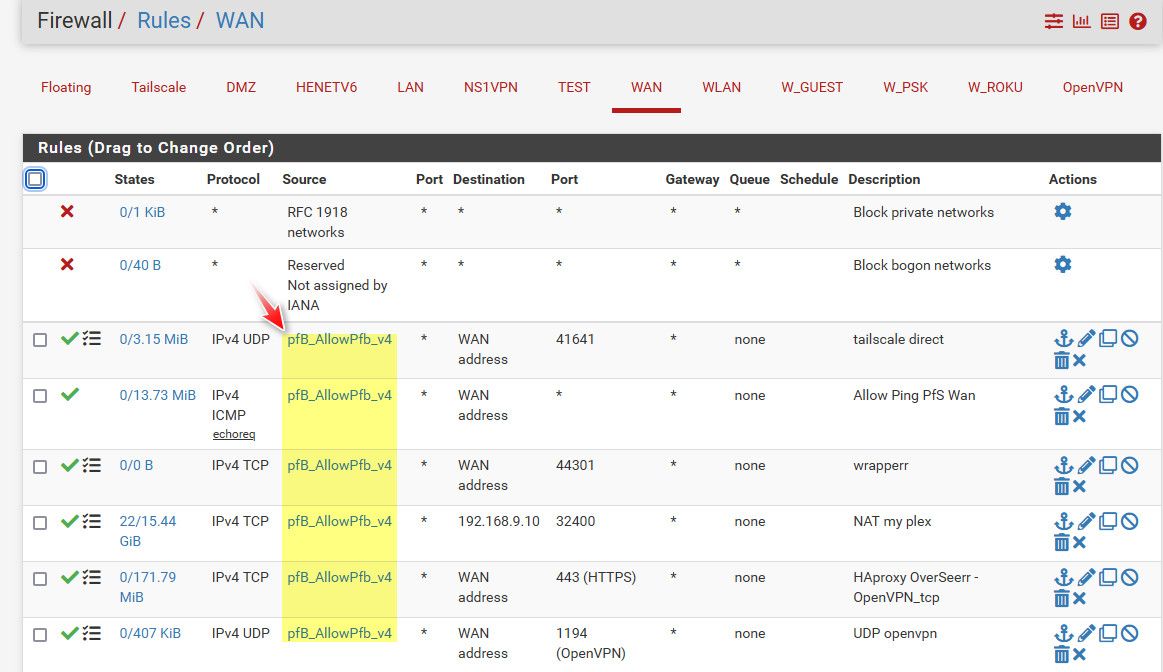
I have a family member currently living in Morocco is why those are included.. And I allow IPs from status cake and uptime robot - since they might be from outside the US, they change now and then. And then the service from plex to check if your plex is available remotely - which also can be from international IPs..
Now allowing any IP from US is pretty open, but is far less open than the whole planet ;)
-
@johnpoz To me, schedule is the best solution as only I know the schedule...I cannot see any situation where schedule wouldn't work for a road warrior setup...the best thing about pfSense firewall to me.
-
@NollipfSense you can for sure use schedules as well.. But if you don't limit what IPs can talk.. Which is what the OP was asking about, during your scheduled allowed time, he would be seeing the same random connection attempts - which he doesn't want to see.
-
@NollipfSense said in How to block random VPN attempts:
wouldn't work for a road warrior setup...
Yes he wants to allow road warrior access but what is known about valid road warrior users?
- is it only the time of day access starts?
- are all countries valid?
- is access required from all telcos?
- is access required from known bad internet addresses
- is access required from external vpn suppliers
For my use case the answer to all the above is no. I also use a white list of specific IP4 & URL addresses I know are OK and which pfblocker does not log for me.
Unfortunately before I can use IP6 I would need pfsense to support an alias with masking the least significant portion of addresses to turn device addresses back to site addresses.
-
OP reminds me of myself back in 2013 when I first setup a l2tp over IPsec then, discovered lots of folks banging on my firewall door...that was Mikrotik, but then comes 2016 I discovered pfSense...it had a firewall schedule...hooray.
Now, I can set a schedule that only I know so when I am on the road, road warrior-ing, I don't need to leave the VPN door unarmed 24/7 waiting for my key or any key...I schedule a time in advance when to put my key in and turn the knob.
-
@NollipfSense said in How to block random VPN attempts:
The problem here is the OP is using a road warrior where the source address is unknown.
A good reason to set Source address to "*" or 'everybody'.
So everybody, using protocol 'X' and going to destination port 'Y'.
Because @MarioG wants to block random OpenVPN server access attempts, I see (I'm repeating what has been proposed already) :
- above the OpenVPN server pass rule : block IPs that want to use protocol X and destination port Y.
- Use an alias as "Source Adrress' in the OpenVPN server access rule that contains IP that are allowed.
or a combination of the two.
-
@MarioG if the remote PCs have dynamic DNS clients on them you can allow only those dyndns hostnames. Otherwise maybe by country as suggested, or maybe ASN (IP blocks).
-
@SteveITS yeah ddns is also an option.. To limit to specific known clients - that is a good option as well. If your users are smart enough to do that. But it doesn't really work with say phones - that love to change their IP as they move towers etc.
-
@NollipfSense said in How to block random VPN attempts:
OP reminds me of myself back in 2013 when I first setup a l2tp over IPsec then, discovered lots of folks banging on my firewall door...
After reading that, I left Packet Capture running overnight, watching for attempts to connect to my OpenVPN. I saw only 5 attempts, all from different addresses and none had more than a single packet.
23:44:36.016993 IP 64.20.37.190.36695 > 99.246.121.125.1194: UDP, length 14
03:30:16.965371 IP6 2607:ff10:594:c8::e.56666 > 2607:fea8:4c82:5900:202:55ff:fe47:e07b.1194: UDP, length 18
04:25:20.254762 IP 205.210.31.53.52898 > 99.246.121.125.1194: UDP, length 18
04:44:40.743888 IP 38.132.109.107.48280 > 99.246.121.125.1194: UDP, length 14
06:11:27.663894 IP 144.126.201.49.51303 > 99.246.121.125.1194: UDP, length 19My addresses have been changed to protect the guilty.

OpenVPN Protocol
Type: 0x38 [opcode/key_id]
0011 1... = Opcode: P_CONTROL_HARD_RESET_CLIENT_V2 (0x07)
.... .000 = Key ID: 0
Session ID: 7647933796043154430
Message Packet-ID Array Length: 0
Message Packet-ID: 0As you can see, there's no response from pfSense.
-
@johnpoz said in How to block random VPN attempts:
that love to change their IP as they move towers etc.
Do they?
I have done a bit of work on cell networks, for two different carriers. A few months ago, I was also doing some work in the local office of my ISP/cable company/cell carrier. All the servers were located in the office and not at the cell sites. Also, there's a fair bit of cell network underneath the IP layers, to connect the phones to the office. At the cell sites, there are Ethernet switches but not routers, so no local means of providing IP addresses.
-
@JKnott said in How to block random VPN attempts:
Do they?
Tmobile does for damn sure - I can not walk down the block with out bunch of different IPs being used. I have tautulli setup to email when new Ips are used by a client.. Normally its just now and then.. But from phones I can get a flood of them..
It could have to do with cells that only get IPv6 and have to go through the carriers translation to IPv4..
Not saying it happens ever single time - but it can for sure happen. I turned of email notifications on my phone for them - because when I was talking a walk and listening to music off my plex, I would keep getting popups on my phone when another email came in about a new IP, etc
-
@NollipfSense said in How to block random VPN attempts:
To me, schedule is the best solution as only I know the schedule...I cannot see any situation where schedule wouldn't work for a road warrior setup...the best thing about pfSense firewall to me.
Hello!
Not sure I understand the complete use case, but maybe some form of port-knocking would be an option...
fwknop
https://redmine.pfsense.org/issues/8547John
-
I've never used T-Mobile. I've only roamed on AT&T when in the U.S.. The carriers I've worked on are Rogers and Wind/Freedom. I first worked on the Wind network when they were getting ready to start up and later, as Freedom, to upgrade the power supplies and batteries. I was working on Rogers for their LTE rollout and more recently when they were setting up a 2nd office in my city. I have never seen a router at a cell site, but several in their office.
One of the reasons the cell networks are IPv6 now is they need a contiguous network for all the devices & VoIP, etc.. RFC1918 is not adequate. My phone is IPv6 only and uses 464XLAT to access IPv4 addresses. It has a single IPv4 address, 192.0.0.4, which is reserved for 464XLAT. I don't ever recall seeing anything different. I haven't checked the IPv6 address at different locations. I guess that's something I should do sometime.
BTW, I'm on Rogers.
-
@JKnott said in How to block random VPN attempts:
All the servers were located in the office and not at the cell sites. Also, there's a fair bit of cell network underneath the IP layers, to connect the phones to the office. At the cell sites, there are Ethernet switches but not routers, so no local means of providing IP addresses.
Good to know...my T-Mobile (fast 8856w) sure do go through some IP's.
-
@NollipfSense said in How to block random VPN attempts:
Good to know...my T-Mobile (fast 8856w) sure do go through some IP's.
IPv4 or IPv6? As I mentioned, with 464XLAT, you shouldn't see any address change.