No connection to internal Vlans
-
Hi to everybody.
I have A Sophos FW for many years and considering start using PfSense for my organization.
As for now I'm still in a learning curve and try to figure it out.
Lan, Wan and DMZ work great.
My problem is, that my internal Net are divided to Vlans, and I can't reach the FW from my vlans.
The way my Lan configured, is each department has a unique Vlan (Native) and all of them connected to a Core switch which doing all the routing in between.
It works greate and I can ping from one area to another.
How do I configure PfSense to be accessed for all Vlans.Thanks.
Goldy
-
If the vlans arrive at pfsense tagged over a trunk(s), then you need to specify each physical link/vlan in pfsense (Interfaces->vlans). Then, assign each of those to logical interfaces (interfaces->assignments).
https://docs.netgate.com/pfsense/en/latest/vlan/configuration.html -
-
@Goldy That seems ok to me. Assuming the interface IP/subnet aligns with the existing vlans.
Have you configured the firewall for the vlan backed interfaces? Rules to allow the hosts on them to reach and/or traverse the router? IIRC, pfsense doesn't create default permit rules for interfaces other than the initial LAN. You could also turn on default drop logging and check the firewall log.
Hope that helps. -
@darcey
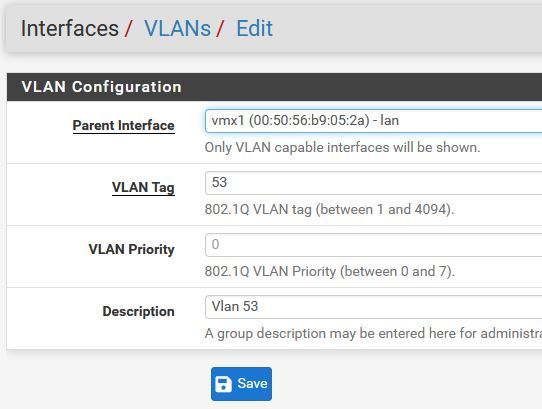
Thanks for helping.That's my Firewall config:
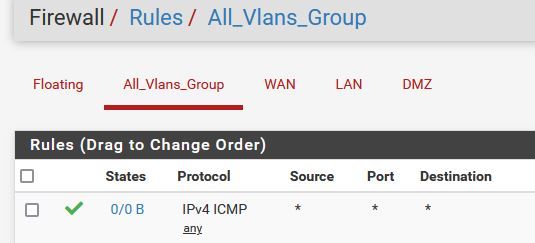
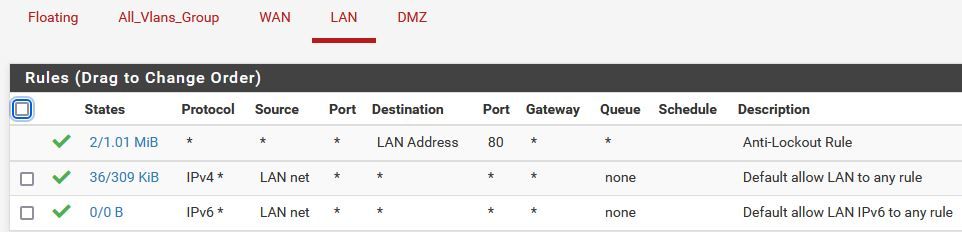
The Lan Interface connected to a Switch, and I have no problem ping from the switch to Vlan 53 and back, so it seems it has something to do with the FW.
Don't I have to set somewhere the next hop of the Lan interface?Where can I find the default drop logging?
Best regards,
Goldy. -
@Goldy said in No connection to internal Vlans:
My problem is, that my internal Net are divided to Vlans, and I can't reach the FW from my vlans.
your switch is routing these vlans, you mention? You mention next hop in your last post?
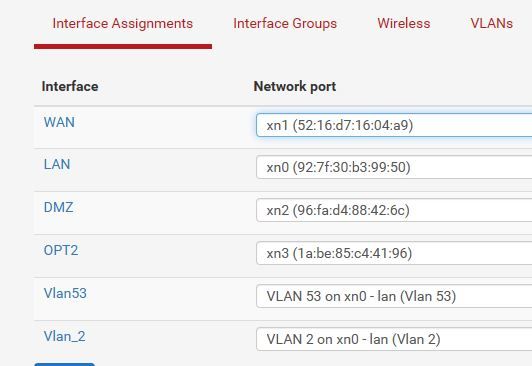
And you pictures don't line up... In your one picture you show vlan 53 on vmx1 ? Which pfsense is virtual? But then in your assingments of interfaces vlan 53 shows to be on xn0 ?
-
@Goldy said in No connection to internal Vlans:
Where can I find the default drop logging?
"Log packets matched from the default block rules in the ruleset" under Status->System->LogsSettings.
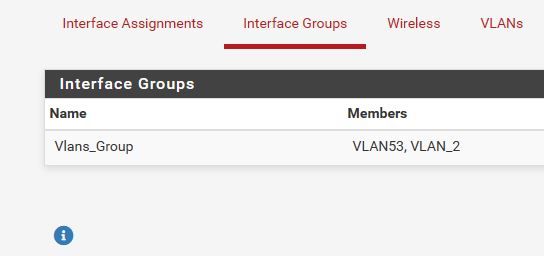
The source net in your interface group firewall rules above would not seem to cover the vlan interfaces, would it?However @johnpoz has pointed out an inconsistency in your interface assignments - that needs checking first!
-
Hi.
Hope this one will explain it better:
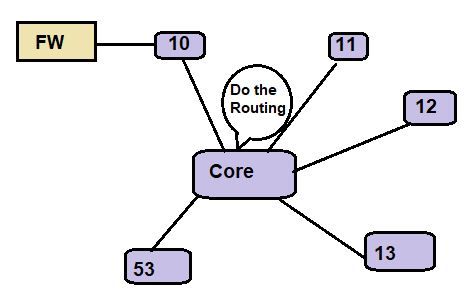
Vlan 53 assassin to Lan (Xn0) .
I add a wrong Picture
PS: For experiment reason, this PfSense is installed on a Xenserver Machine.
As i found (in the hard way) the last version of Pfsense - 2.7 doesn't support multi CPU.
There was no issue with 2.6, but when i upgraded to 2.7 the FW crashed.
Also clean install crashed.
It took me a while to find out the reason.
Hope it will help someone.... -
@Goldy if you have a downstream router - you would not setup the vlans on pfsense. You would just setup a gateway and route to the networks.
here is how you would setup a downstream router.
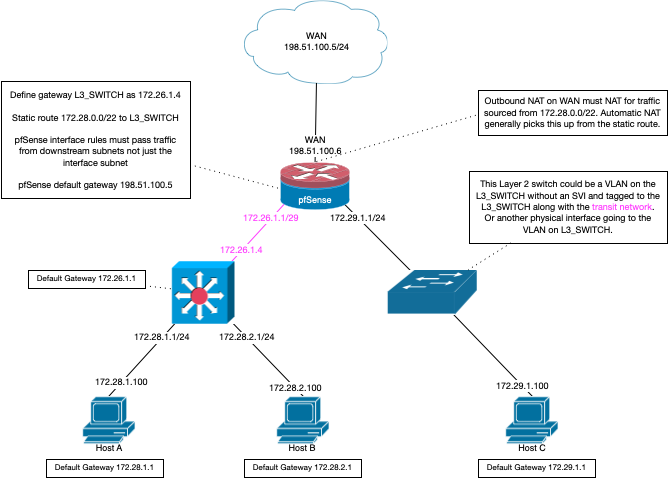
-
Thank.
This is my config:
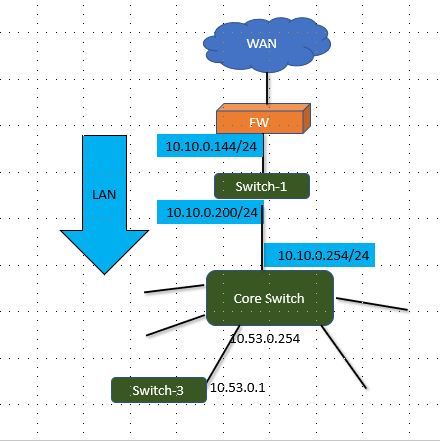
Pinging from any subnet to switch-1- All is well.
pinging from 10.10. subnet (Lan on FW) to FW Lan address - All is well.
Pinging from switch-3 to FW - Nothing
Wan works OK.
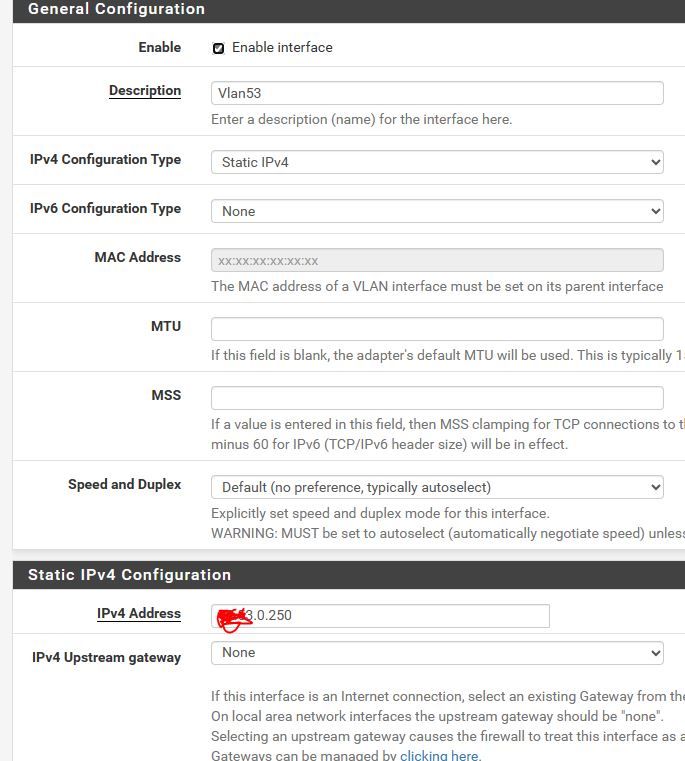
Default gateway of subnet 10 (Lan) - 10.10.0.254 -
@Goldy said in No connection to internal Vlans:
Default gateway of subnet 10 (Lan) - 10.10.0.254
Well that is wrong.. Your lan should not have a Default on it or gateway set.. Since now pfsense thinks its a wan..
Create a gateway.. And then routes to what networks you want to get to..
Pfsense should a gateway setup to 10.10.0.254, and then route to 10.53.0.0/24 and any other networks that can be accessed via that gateway.. your core switch default gateway should be 10.10.0.144..
If your going to use your "lan" as your transit - which is really bad idea if you have any actual hosts on this network - since you will run into asymmetrical traffic flow.
If you are going to have a downstream network it should be connected to pfsense via a transit network, ie no hosts on this network. The drawing I posted shows exactly how to setup a downstream router with pfsense.
You only setup networks/vlans on pfsense when it is directly connected to them. The only networks be tagged or native that should be setup on pfsense are ones its directly connected to.
If networks are via some other router, then you create a gateway to that router IP on your transit network. And then routes via that gateway for networks you can get to via that gateway. Then setup appropriate rules for any traffic that will flow through the transit network. Your firewall rules wouldn't ever allow 10.53.x.x because that is not the lan net.. Unless your downstream was natting?
-
Thanks for your patience.
i will try it.Also, it seems that pinging 10.53.0.1 goes to WAN Interface instead of Lan:

-
Two more things.
- As fore now, I can't change my core Gateay since it direct all my traffic to my real Firewall.
- All i need is to reach the Pfsence from another address.
I'm not planning to use it, but to study it.
-
@Goldy well then don't change the default gateway on the core. But create routes on it to use pfsense to get to what networks you want to get to via pfsense.
-
Eureka



 .
.You were right.
Sometime things are simpler than you expected.
A simple gateway rout did the trick
My mistake was i have tried always to ping the firewall, but forget to enable the LAN for allowing ICMP.Works like a charm.
Thanks a lot.
Great forum.