Multi WAN and Blocking DNS
-
Hi,
I have the following scenario;
When using WAN1 you can't access the internet but can access a particular host (e.g bbc.co.uk) and when using WAN2 you can access the open internet
WAN1 - Block DNS requests to outside DNS servers (e.g 8.8.8.8) from LAN, but also allow DNS to one particular host (e.g bbc.co.uk)
WAN2 - Allow all traffic from LANHow would you achieve this with Firewall rules?
Many Thanks
-
@mspeed
How do you intend to switch between the WANs?
Should it be an automatic failover in case, primary is down? If so, which is the primary? -
@viragomann WAN1 as the primary, and if WAN1 is unplugged it would auto failover to WAN2 and auto fail back when WAN2 is unplugged
I have set the Muti WAN as
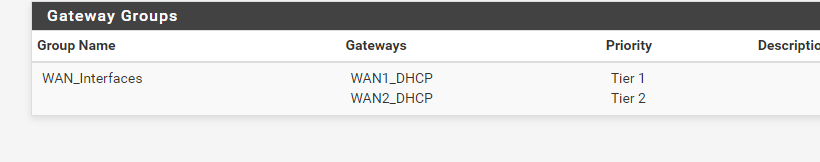
-
@mspeed
So you only want to restrict outbound traffic on WAN1.You can do this with floating quick rules.
Just add the host names or IPs you want to allow to an alias and the allowed ports to a second one.
Then add a floating pass rule, check Quick, select WAN1 interface, protocol TCP/UDP and set the direction to out.
Source: LAN net
destination: your whitelist alias
dest. port: port alias
enter a descriptionAdd another floating rule, but with block action, check Quick, interface WAN1 selected, protocol any, direction out and again select LAN net as source.
The pass rule should be on the top, followed by the block rule. -
@viragomann Hi,
Thanks, for the help so far
So I have set the following under Floating
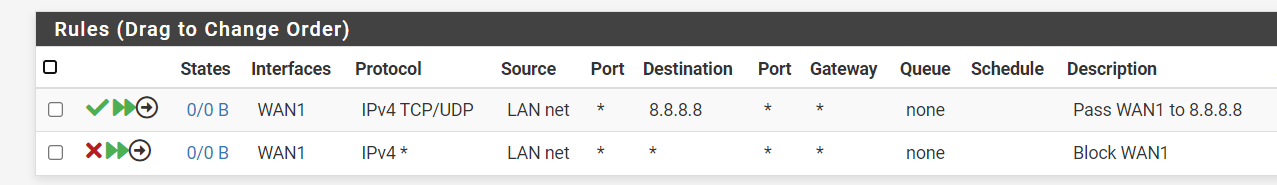
and this is under LAN rules
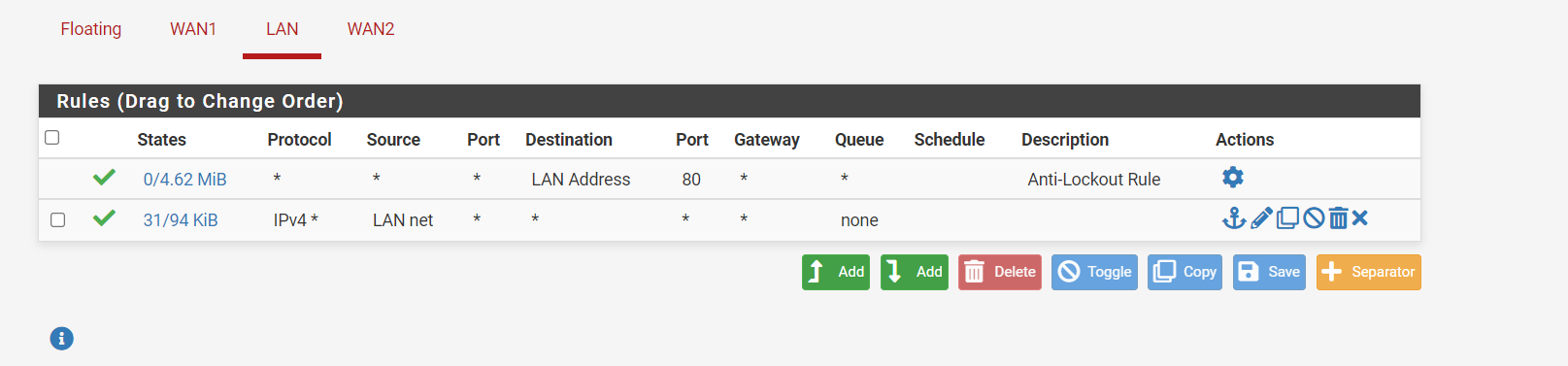
When I have the LAN Net to Any (LAN rules) I can access everything in WAN1, when I remove it I can't access anything at all not even 8.8.8.8 (from the floating rules)
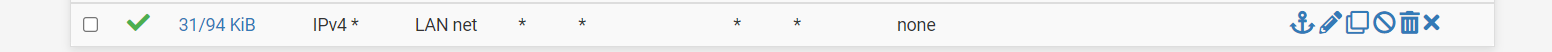
-
@mspeed
I suspect, the LAN net is not seen on the WAN as source. My bad.So you will have to make this work by tagging the packets.
See Marking and MatchingTo be honest, I've never setup such rule.
But as I understand it, you have to put the pass rule with the aliases on the LAN tab and enter a tag in the advanced options, e.g. wan1.In the floating block rule set the source back to any, open the advanced options and check "invert" at Tagged and enter the tag name (wan1).
So this rule blocks only packets which are not tagged with wan1 then (all you want to allow is tagged).The floating pass rule can be removed.
-
Can this be done like so, I need to block outside DNS servers on WAN1 but Allow WAN2 to send DNS outside, this is in the DNS Resolver settings?
But also allow WAN 1 DNS to allow DNS to one host?
-
@mspeed I think you might be looking for this:
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#enforcing-gateway-usere: Unbound network interfaces, that is what Unbound will query on. It's not related to the PCs on LAN.
I'm a little unclear of your goal. If you literally want to block DNS, as opposed to blocking connections out over WAN1, there are several steps involved. This page has a PDF to block DNS over HTTP but may help with those rules, and you can also block port 53 (allow LAN Net to LAN IP:53, block to any:53). Blocking DNS doesn't block connections to web sites though, and "bbc.co.uk" is not a DNS server.
edit: forgot the guide URL: https://github.com/jpgpi250/piholemanual
-
Okay let me explain more and swap the WANs around
WAN1 - Standard Internet
WAN2 - Expensive satellite-based InternetAllow all traffic to work on WAN1 as "normal" when WAN1 is down auto-failover to WAN2 and only allow critical data through, the goal is to reduce the traffic on WAN2 in this example to as little as possible and only allow one application to work to a particular DNS name
-
@mspeed OK, so I'd say that's not a DNS issue. The policy routing doc should explain what you want...that link and further up that page. I would think "bbc.co.uk" has multiple IPs/servers so you will probably have to compile a list of IPs yourself. If you put bbc.co.uk in an alias pfSense will resolve it every 5 minutes but I expect that would resolve to one IP.