Source IP of VPN traffic being changed
-
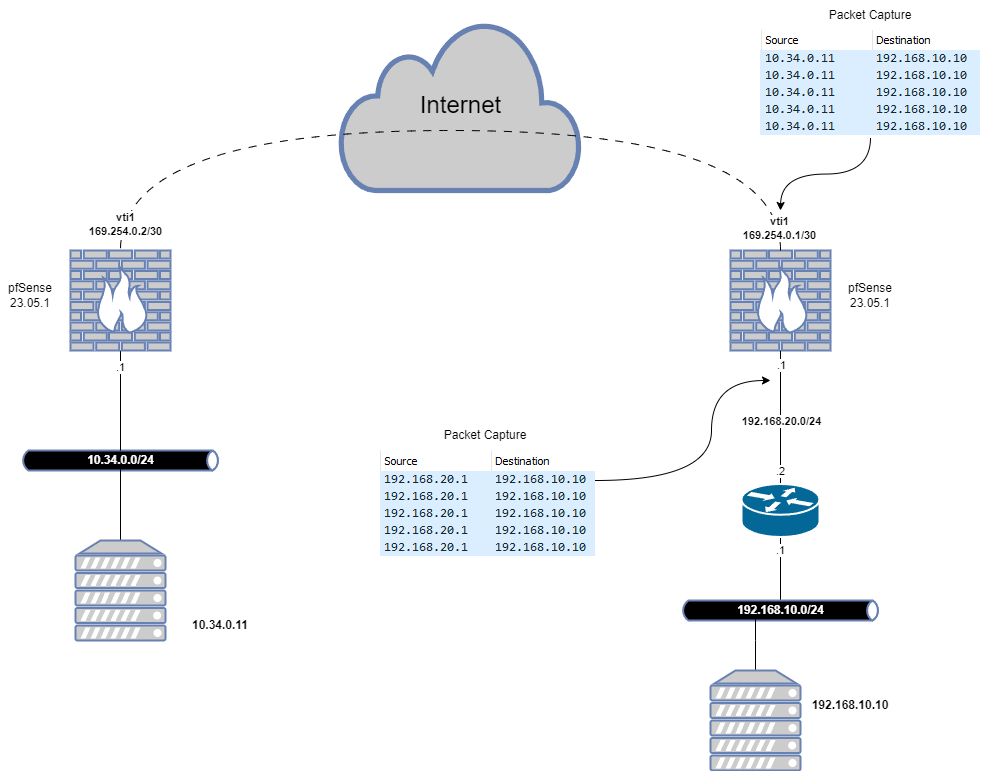
I have a routed IPSec tunnel between two pfSense firewalls using vti interfaces. Traffic initiated from the remote 10.34.0.0/24 subnet (see attached diagram) is traversing the tunnel. However, my local pfSense firewall (the one on the right of the diagram) is changing the source IP address of this traffic and replacing it with the IP address of its own LAN interface.
Packet captures taken on vti1 show that that source IP is unchanged when entering the firewall but is being changed upon egressing to my local LAN. I have a second IPSec VPN (not shown in the diagram) that is a policy-based tunnel (no vti interfaces) and the source IP of the ingress traffic from that VPN is NOT being altered. I do not have NAT configured anywhere except for outbound NAT to the Internet.
I have been unable to determine why this is happening. Any ideas?
-
@kf4zmt
Check the outbound NAT. Presumably pfSense has automatically created a rule on the Lan.
This is the case if you state a gateway in the interface settings. -
@viragomann I think I see what you mean.
Any idea why this NAT is happening only for traffic coming in from the routed VPN? I have a second IPSec tunnel (policy-based) and the source IPs are not being NATed for traffic coming in over it.
Is there a way to add a "NO NAT" rule to make it stop NATing the VPN traffic?
-
@kf4zmt
So is there an outbound NAT rule on the internal interface?
I'd expect that it would also nat other sources in this case. -
-
@kf4zmt
Do you need the LAN gateway?
This option is meant for stating an upstream gateway. For other routing purposes it's sufficient to add a gateway in System > Routing. -
@viragomann I also just noticed that the subnet (10.50.x.x) associated with remote network from the second IPSec tunnel is not included in the automatic NAT rules.
I suppose that would explain why those source IPs aren't being changed.
-
@viragomann I don't know when or why I set that, but I removed it and that appears to have resolved the issue.
Thank you!!! I don't think I'd have ever figured this out on my own.


