advice on new home network and curious about SG1100 vs MikroTik's RB960PGS
-
I already have a SG1100 router that I used at another house. I've moved, been lazy, long story short my SG1100 is in a box and I'm using an awful router provided by my ISP that needs to be power cycled at least 4 times a week.
So I've been brainstorming how I want to setup the network for my new(ish) home. It's a two story house, currently with on AP upstairs and WiFi works downstairs but no where near optimal. I've decided I want to use a POE AP upstairs, and a POE AP downstairs. Eventually I will have up to 6 POE cameras when I'm all wired for it. Networking is not my area of expertise, so all advice is welcome.
I recall the SG1100 leaving much to be desired. It worked fine on my old 60Mbps cable connection constantly streaming Plex locally on one to three TVs at any given time. It was just something about it that seemed slow. I recall the boot time and working in the web GUI always being a bit sluggish. It's bearable and not that big of a deal, because it's stable so I don't need to do those things often, but it prompted me to have a second look at the SG1100 specs.

Now I'm looking at MikroTik routers and I landed on the RB960PGS: https://mikrotik.com/product/RB960PGS
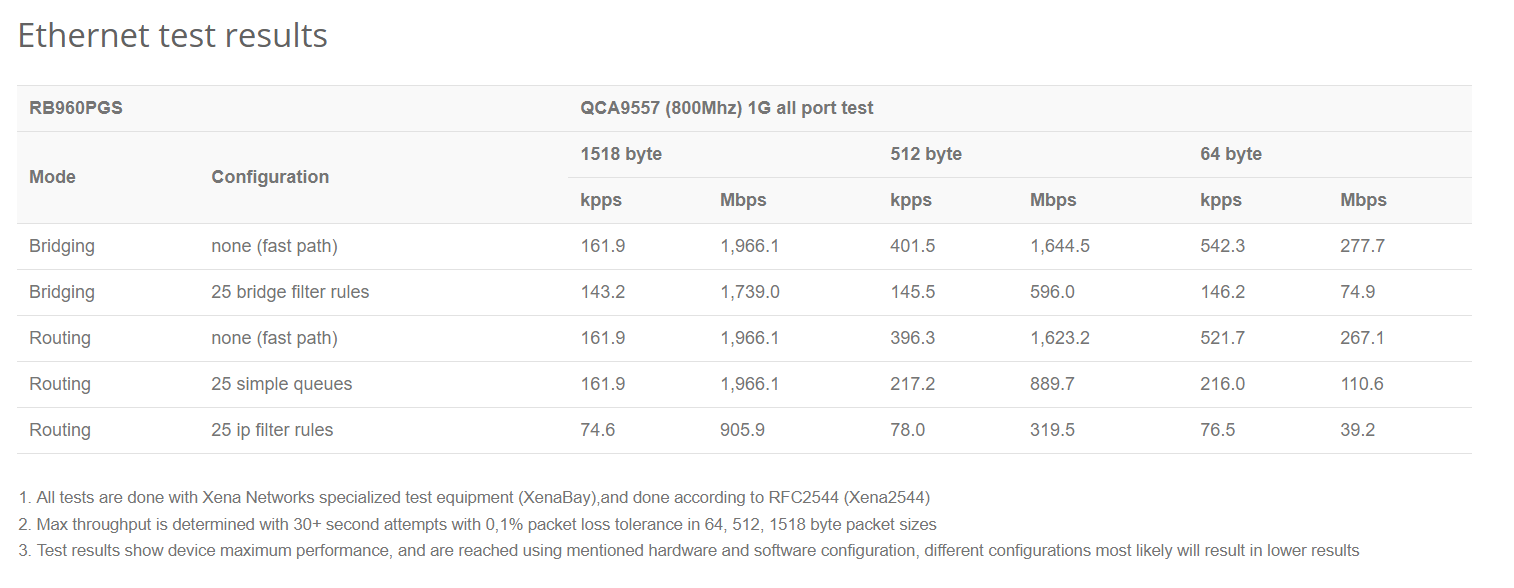
According to the specifications, the RB960PGS has a single core 800MHz processor and only 128MB of RAM, yet the test results page suggests that it out performs the SG1100 that has a 1.2GHz dual core arm processor and 1GB RAM by a lot.
It raises a lot of questions. I'm wondering how can the RB960PGS outperform the SG1100? I'm guessing it's the switch chip can someone confirm? Is that why the SG2100 is quite a bit better than the SG1100 with similar specs? What will I miss out on if I go with the MikroTik router with RouterOS over the Netgate router with PFSense? The MikroTik router takes a hit with having more IP filter rules. Does it still take a hit on the SG1100 with the faster processor?
Most importantly: will I be able to fully utilize my 1Gbps connection with the firewall enabled on my SG1100?
I think the router is just going to be a firewall + router for me. I may setup DNS, but I'll put it on a server if it's a performance hit to the router. Then again, with all that extra processing and RAM, the DNS server should run on the SG1100 like it's not even there, right?
I'm going to pull it out of the box where ever it is sometime soon, but can anyone give me a head start on answering some of those questions or push me in the right direction?
-
@shea said in advice on new home network and curious about SG1100 vs MikroTik's RB960PGS:
It raises a lot of questions. I'm wondering how can the RB960PGS outperform the SG1100?
A few reasons:
- The 1100 has a single ethernet IC that runs at 1Gbps and is shared between the three ports
- They run very different operating systems.
-
@shea said in advice on new home network and curious about SG1100 vs MikroTik's RB960PGS:
Most importantly: will I be able to fully utilize my 1Gbps connection with the firewall enabled on my SG1100?
No. See my previous message.
In a best-case scenario you'll get 600Mbps but without any filtering going on.
-
@rcoleman-netgate said in advice on new home network and curious about SG1100 vs MikroTik's RB960PGS:
- The 1100 has a single ethernet IC that runs at 1Gbps and is shared between the three ports
I think that has to be the bottleneck for the 1100 throughput, because 2100 proves the CPU/OS is capable of more with a better network chip.
@rcoleman-netgate said in advice on new home network and curious about SG1100 vs MikroTik's RB960PGS:
- They run very different operating systems.
Is that to say RouterOS performs well with 800MHz, or is that to say pfSense is inefficient?
Does it seem significant that the RouterOS throughput at 800 million cycles per second, comes very close to the pfSense throughput at 2.4 billion cycles per second?
I think I just figured it out as I was typing that last sentence: I think pfSense is overall marginally less efficient, but the nic portion is a bottleneck for the 2100 and especially for the 1100. I assume the nic/network/switch chip would stack/grow the more ports you use. I think the 2100 could handle a much higher throughput with more ports, but the CPU is intentionally better than needed to support packages and other additions to pfSense, which is why the dual 1.2GHz seems disproportionate to the single 800MHz. Apparently the firewall throughput isn't directly determined by the CPU speed, and the nic is more involved with the firewall than I had thought, because the firewall throughput on the 1100 is quite bad, despite having a better CPU. I think I would need to learn more about these "IP filter rules" to understand why that is.
@rcoleman-netgate said in advice on new home network and curious about SG1100 vs MikroTik's RB960PGS:
@shea said in advice on new home network and curious about SG1100 vs MikroTik's RB960PGS:
Most importantly: will I be able to fully utilize my 1Gbps connection with the firewall enabled on my SG1100?
No. See my previous message.
In a best-case scenario you'll get 600Mbps but without any filtering going on.
Ultimately I guess everything else is irrelevant and this is what it all comes down to.
-
@shea said in advice on new home network and curious about SG1100 vs MikroTik's RB960PGS:
Is that to say RouterOS performs well with 800MHz, or is that to say pfSense is inefficient?
No, Linux and FreeBSD are very different platforms.
-
Is that to say RouterOS performs well with 800MHz, or is that to say
pfSense is inefficient?No, but the RouterOS is like the name indicates a router and Linux based
that will be a little bit agile, faster acting and more near the hardware coded.pfSense is BSD based an a firewall, that can be turned into a fully UTM
device, with, IDS/IPS, AV scanning, caching proxy (reverse & caching),
Geo blocking and spam filtering.So first a router is routing between one and another or more network(s)
so it is connecting oriented action.A Firewall like pfSense is, is separating and filtering one from another or
more networks.That both devices and/or the OS will be able to use filters and be able to
route, make or place them not in the same device area.Does it seem significant that the RouterOS throughput at 800 million cycles per second, comes very close to the pfSense throughput at 2.4 billion cycles per second?
Again, you need more horse power for pfSense to reach the same goal as
together with the RouterOS.I think I just figured it out as I was typing that last sentence: I think pfSense is overall marginally less efficient, but the nic portion is a bottleneck for the 2100 and especially for the 1100. I assume the nic/network/switch chip would stack/grow the more ports you use. I think the 2100 could handle a much higher throughput with more ports, but the CPU is intentionally better than needed to support packages and other additions to pfSense, which is why the dual 1.2GHz seems disproportionate to the single 800MHz. Apparently the firewall throughput isn't directly determined by the CPU speed, and the nic is more involved with the firewall than I had thought, because the firewall throughput on the 1100 is quite bad, despite having a better CPU. I think I would need to learn more about these "IP filter rules" to understand why that is.
The entire action is a total different pointed to the both OS.
ROS does normally netfilter = SPI and net work address translation NAT
pfSense is filtering with the packet filter PF from FreeBSD and network
address translation is a later part or stage "inside" of the "pf"!So ROS is not allowing any packet to flow into the network and pfSense
will "see" inspect all packets and then it acts based on the given rules.You will need perhaps more "horse power" with pfSense but you will be able
to realize absolutely other or different things with it.Dual or more WAN ports can be handled really good;
- load balancing with failover on top of it
-- policy based routing
-- session based routing
-- service based routing
Caching and filtering
- Squid & SquidGuard
-- Caching proxy for the LAN
-- reverse proxy in front of the DMZ
-- Blacklists and AV scanning support
Blacklists, Antispam and Geo Blocking
- pfBlocker-NG
-- using blacklists of much list servers
-- using much categories
-- able to set up paied lists (Spamhaus, iBlocklist, ect.)
ISD/IPS
- Snort / Suricata
-- Deep packet inspection
Patch system
- pfSense packet system
-- installing recommended and/or your own patches, like you want or need it.
Packed system
- Packed installations to enrich the entire pfSense
- OVPN, WireGuard, IPSec, and so on
WiFi support
- Captive portal with voucher system for WiFi
-- own wifi cards installations like you need
-- WiFi APs from other vendors
If this is more or less something for you, you will be sorted with
pfSense at a glance. - load balancing with failover on top of it
-
I have several MikroTik switches at home and they work great. I also have pfsense installed in an old Dell OptiPlex small form factor PC with a couple of network cards in them.
MikroTiks are great for what they are as "routers" and switching but I wouldn't use them for any serious firewall functions like you would find in pfsense. It doesn't have intrusion detection if you care about that.
Although it does have wireguard VPN and IPSec but no Open VPN.If you don't secure the MikroTik firewall rules properly it can get pretty nasty in terms of break ins from the outside. Several ISPs use MikroTik as routers for their network. Even installed them at customer's site.
pfsense is just dead easy to configure and set up.
-
@shea The 2100 has a similar CPU to the 1100 but has a separate NIC for WAN.
“Working in the GUI” could well be eMMC write speed (which is inherently not fast). Note the 2100 has 4GB/4x the RAM so can better use a RAM disk. The 2100 also has a max version with an m.2 drive.
I don’t see you said what your current bandwidth is..? As alluded to above I suggest figuring out your needs/goals, then choose software, then choose hardware.
-
I'm pretty sure that Mikrotik platform will be using some hardware offloading to pass traffic without having to process each packet. You can see that by how much slower it is with only 25 IP filtering rules. I'm assuming the 'simple rules' that do not slow throughput are handled in the offloaded path but anything more complex cannot be. There are quite a few devices that behave like that. Big numbers until you try to do anything complex when throughput tanks. The 1100, like anything running pfSense, uses pf for all filtering. No hardware ACLs.
Steve
