What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?
-
You cant trust anyone.
-
@johnpoz said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
Which they all say, so why should I trust any of them, when I can just do my own resolving thank you very much..
Yet you 'trust' everyone in the chain that links you to all the different upstream domain registries and you do so with all queries unencrypted at every stage. It works for you and you are comfortable with but it is an odd position to be in and question the level of trust with services such a Quad9.
As we understand it, you doubt that Quad9 is secure and may in fact be insecure. Ok, we can see your logic or at least acknowledge your opinion. But as a countermeasure to that potential risk you knowingly chose to run all your external DNS queries as insecure traffic, to all the various upstream root nameservers and below, wherever they reside in the world, under whatever government and by whatever route needed.
My point is that you made a choice; it does not mean those who choose differently are either wrong or fail to understand your point of view. We have simply made a different choice to you.

 ️
️ -
@RobbieTT said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
et you 'trust' everyone in the chain that links you to all the different upstream domain registries
Those are all root and gtlds. That guess what who you forward too uses as well.. ;) the internet doesn't work if those are not there..
Domain registries? Do you not actually understand how dns works?
Sure I register domain.tld, that registar that I use to register that places the NS I will use for that domain, in the gltd NS pointing to NS for my domain, etc.
Kind of hard not to trust ICANN and IANA, since for one they are the only game in town..
Lets just agree you can do what you want, and I can do what I want.. You don't have to agree with mine, and I don't have to agree with yours.. But when it comes to trusting, you are the one that are laying all your trust in some company that says, hey trust us with all your dns.. I am not..
Your wanting billys phone number, but instead of asking billy, your asking sam.. I feel better asking billy directly ;)
-
@johnpoz said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
Your wanting billys phone number, but instead of asking billy, your asking sam.. I feel better asking billy directly ;)
Exactly, I discreetly ask Sam and Sam discreetly answers my question.
You shout across everyone to someone who knows a bit about Billy but not everything and on you go shouting down the line to get the final detailed answer you seek.
Everyone now knows that you want Billy's number, they also all get yours and Billy's number along the way.
 ️
️ -
I just did the following: I use forwarding in the resolver via DoT. I use two "independent" DoT Server (not google or cloudflare) in General Setup via VPN-gateways. I also forced Unbound to only use the VPNs for outgoing and blocked DNS and DoT on WAN.
I think this will be as good as it gets. -
@johnpoz said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
Which brings up a point, when you resolve you always get the full ttl of whatever you resolved.. When you forward, it will return what it has in its cache with the ttl of what is left on its cached
That seems like a valid point for DNS Resolver, the longer the TTL, the fewer the DNS queries. I had no idea TTLs were so short. My hosting provider's DNS management interface always defaults to a 24 hour TTL for new records, and I usually just accept this, though I do drop that to 1 hour for records I know might change e.g. MX, SPF etc. Shorter than hour makes no sense to me, but seconds!?
@johnpoz said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
Another possible advantage to resolving vs forwarding. Is you should always get back from the authoritative NS the best geographically IP for where your query came from.
Another valid, if somewhat surprising point. Considering that most websites these day are served from a CDN (even my own hosting provider enables CDN distribution by default), I figured every query would be resolved to the most local IP, I mean that is literally the CDNs primary purpose, to be served from cache defeats the purpose. Definitely a plus for local recursive resolution if true, though.
@JKnott said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
One reason is for accessing my local devices that have private addresses, either RFC1918 on IPv4 or Unique Local on IPv6. No point on having those on a public DNS.
A good point but already covered - using pfSense DNS Resolver host/domain overrides, or a local hosts file, or AD Guard DNS Rewrites seem to be equally valid solutions for local device DNS resolution.
@JKnott said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
However, when at home, I want to use my own NTP server, so I use my DNS to send NTP to my own server.
Another good point, though not strictly a benefit of pfSense DNS Resolver when other comparable services exist.
@johnpoz said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
Which they all say, so why should I trust any of them, when I can just do my own resolving thank you very much..
It's weird! How can I take umbrage at the fact that a DNS service provider might sinkhole an IP based on some arbitrary decision (per your Quad9 example) - I'm being censored!!! - whilst at the same time purposefully installing Ad Guard that blocks thousands of IPs, none of which I know anything about or have any control over!! I think you either have to either accept DNS censorship and get on with your 'ad/malware-free' day, or be the Internet purist and suffer ads/malware/phishing. Anyway, for the weird shit, there's always ToR.
@Bob-Dig said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
I think this will be as good as it gets.
This thread is about the benefits of the pfSense DNS Resolver over traditional forwarding so, whilst your config suggestion certainly has value, particularly from a privacy/security perspective, by forwarding, you are also having to compromise on some of the benefits described within this thread. I'm not saying that's a bad thing, only that it is a thing.
Does anybody know why DoT is only supported in DNS Resolver Forwarding Mode? I mean, if it can do it at all (pfSense), why can't it recursively resolve using DoT? I am assuming that DoT is simply a standard DNS request encapsulated inside a TLS encrypted packet, technologies it clearly supports.
-
@tictag said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
Does anybody know why DoT is only supported in DNS Resolver Forwarding Mode? I mean, if it can do it at all (pfSense), why can't it recursively resolve using DoT? I am assuming that DoT is simply a standard DNS request encapsulated inside a TLS encrypted packet, technologies it clearly supports.
DoT & DoH are not supported by the root servers as using them in this way was never anticipated. Indeed, individual use of the root servers is discouraged as they were designed on the premiss that DNS providers would provide the service to users.
I've no idea why pfSense does not support DoH as well as DoT though.
 ️
️ -
@tictag said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
why can't it recursively resolve using DoT?
Because for that to work every single NS on the planet would have to be setup for dot, and you would have to create new tls connections whenever you wanted to talk to a different NS during the resolve process.
Not saying something like that couldn't happen.. Maybe someday that will be a thing where something like quic is used to talk to NSers as you resolve. But its been what 20 some years trying to get IPv6.. And look how slow of an adoption that has been.
Look at how slow it is moving to tls 1.3 from 1.0, 1.1 or 1.2. or even just https for all sites.. When moving to 1.3 from 1.2 should be a simple thing.
Look at dnssec, another option that you would think should be on everything.. And overall has a very low deployment % for how long its been around. Not even every tld has it.. And some registrars don't even support it, even though its been a requirement to be an accredited registrar for years and years. And some registrars that say they support it, either it doesn't work or is pure PITA to get working.. I moved some of my domains to different registrar because of this years ago..
And many domains that do have it deployed are broken in when you look at the rfcs to how it should be deployed. You see warnings like this
RRSIG cdc.gov/A alg 7, id 22544: DNSSEC specification recommends not signing with DNSSEC algorithm 7 (RSASHA1NSEC3SHA1).
That is on a gov site..
Change is slow when it comes to the internet.
-
@tictag said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
whilst at the same time purposefully installing Ad Guard that blocks thousands of IPs, none of which I know anything about or have any control over!!
You blocking stuff on your own local dns - you do have control over. You can determine which lists you use to block, you can view everything in that list that is blocked if you want. You can edit that list as you see fit, etc.
-
@RobbieTT said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
DoT & DoH are not supported by the root servers as using them in this way was never anticipated.
Ahh, of course. And I guess that they are in no hurry to implement it because it would significantly reduce the information they are able to acquire by providing such global services (assuming this information has value to them). This would be akin to end-to-end encryption employed by Telegram, WhatsApp etc - the bane of national security efforts globally.
@johnpoz said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
Because for that to work every single NS on the planet would have to be setup for dot, and you would have to create new tls connections whenever you wanted to talk to a different NS during the resolve process.
Yeah, I guess that would be terribly inefficient resulting in perhaps hundreds of individual transport layer connections per query, mind you, DNS caching would drastically reduce that and we already use encrypted transports for web browsing where any single page might have hundreds of individual [SSL encrypted] GET requests. Not beyond the realms of possibility.
-
@tictag said in What Are The Benefits Of Using pfSense DNS Resolver/Forwarder Services?:
why can't it recursively resolve using DoT?
Another one :
Creating a TLS connection needs a boatload of cpu cycles, compared to plain UDP.
Afaik : TLS means : TCP, not UDP, so already an overhead.Also : DNS requests are small; short lived connections.
For every new TLS connection a really rare item needs to be used : random numbers.Dot would work from top to bottom if the root servers would 'speak' DoT.
Right now, they don't.
Most TLD do .... (afiak).
Domain name servers : same thing. Mine do... Others ? -
Another benefit is that you can set your smtp servers so systems only can use approved mail servers. This way no device can try to start using non approved email smtp servers.
What I do with this is I made an alias
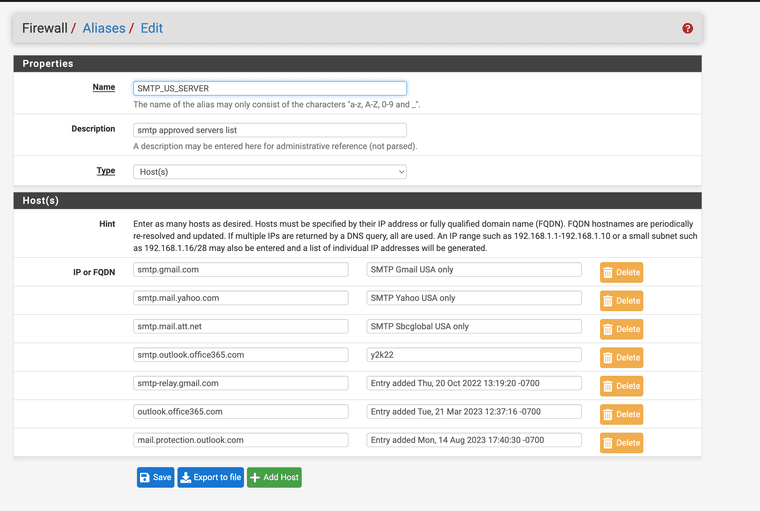
(SMTP US SERVERS)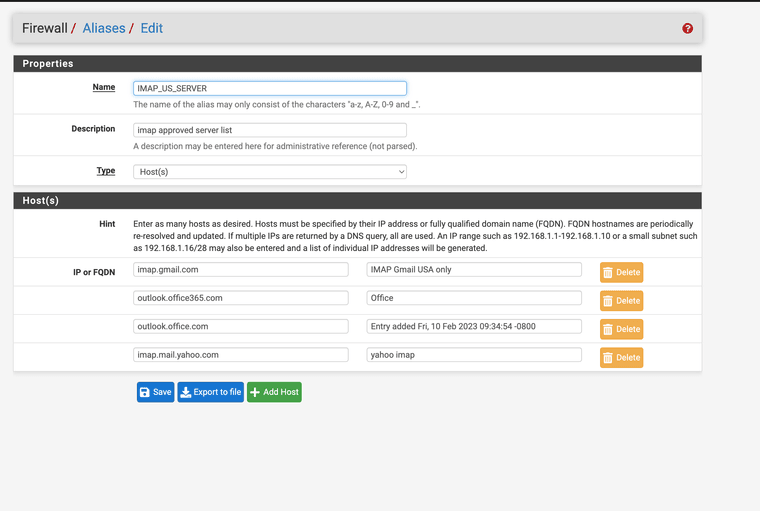
(IMAP US SERVERS)
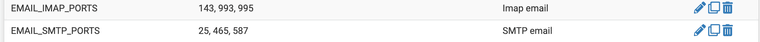
(Alias for ports)After I create a server specific mail ACL (access control list)
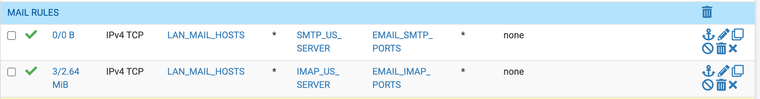
(now my hosts can only access the approved smtp and imap servers)The ports I have for mail can only be used for mail and for specific approved servers.
Once and a while google takes a min to resolve and send only issue.
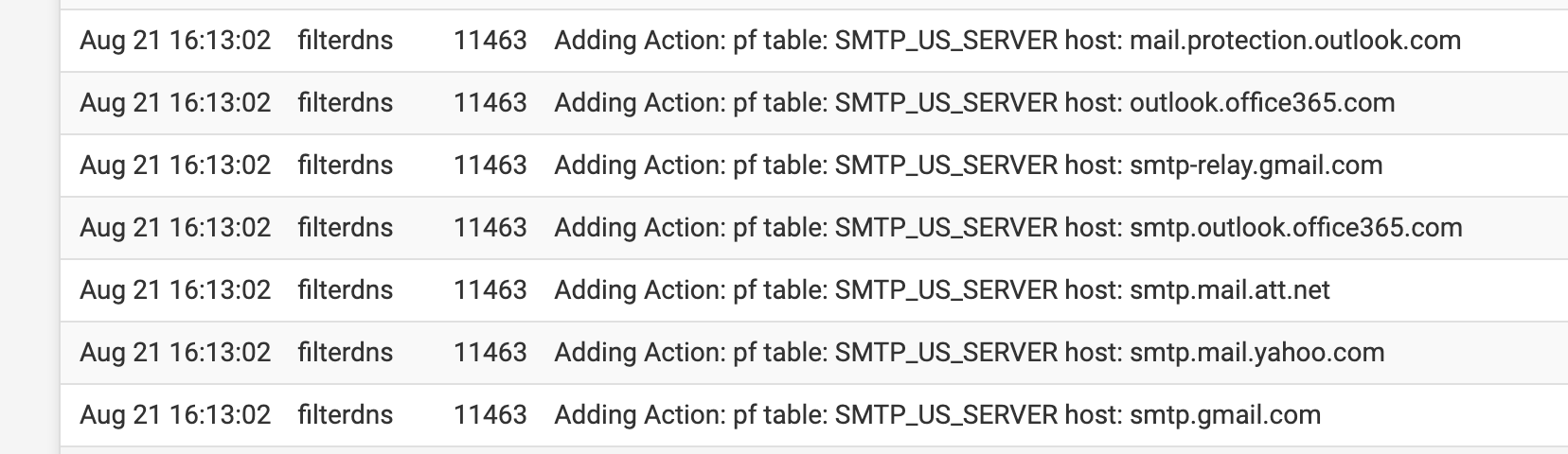
(resolved automatically when they change every 5 or so mins)Your system now will only use the approved USA servers. A couple years ago this was a big issue for some offices as the email being sent out was going to non approved servers.
You can also use "DNS over SSL" with port 853 and get some extra security.
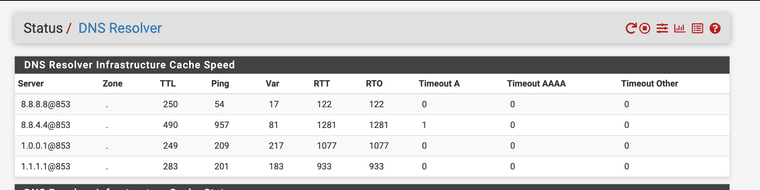 (DNS OVER 853)
(DNS OVER 853)Everything for my system uses DNS over SSL/TLS. The firewall does the SSL/TLS DNS requests for me.
You can also create access control lists on who can send DNS requests to the firewall.
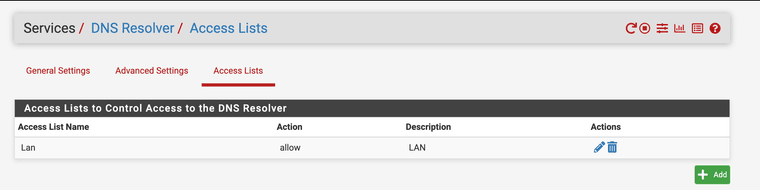
Keep in mind devices will try to use DoH and all sorts of other ways to quarry an IP address if pfSense does it you have some more control over just opening up port 53 with a any any * * rule.
Of course you need a good NAT rule.
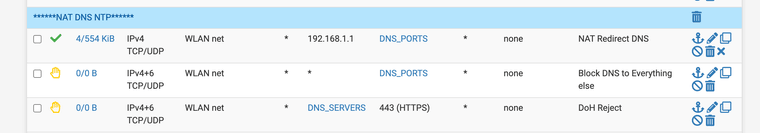
And you need a good DoH block list to really get good control
combineddohlist.txtThe firewall can make better use of IPS/IDS if it knows what it is resolving to.