Setting up CARP Master and Backup on a per VLAN basis (Like VRRP): is it possible?
-
Hello!
I am a computer novice who is currently working on his CCNA. I have a question about CARP which can probably be answered with either yes or no, but I have not found a clear answer looking through the forums myself.Some background (probably not required to answer the question):
I have recently learned about VRRP and am fortunate enough to be able to create a home setup with 2 pfsense boxes that each have their own ISP connection.
So I intend to make a setup, where if one of the ISP connections is down, the Backup will assume Master role and provide internet from its connected ISP.
I noticed that, in VRRP, there is a per-VLAN construction that could make it so that a Router can be a Master node in one VLAN and a Backup in another. This seems ideal for my current living situation allowing each party to still use its own ISP on their own VLAN while still being able to fall back on each other.
From what I read about CARP on the wikipedia and the netgate documentation, it seems to be very similar to VRRP from protocol numbers to functionality, but my knowledge is very surface level.The question:
Can CARP Routers take the role of Master in one VLAN and Backup in another VLAN?
Additional visuals
I made a diagram to better illustrate the setup (maybe ignore the vlan100 block in the middle, since I realized the devices in it may not make complete sense)
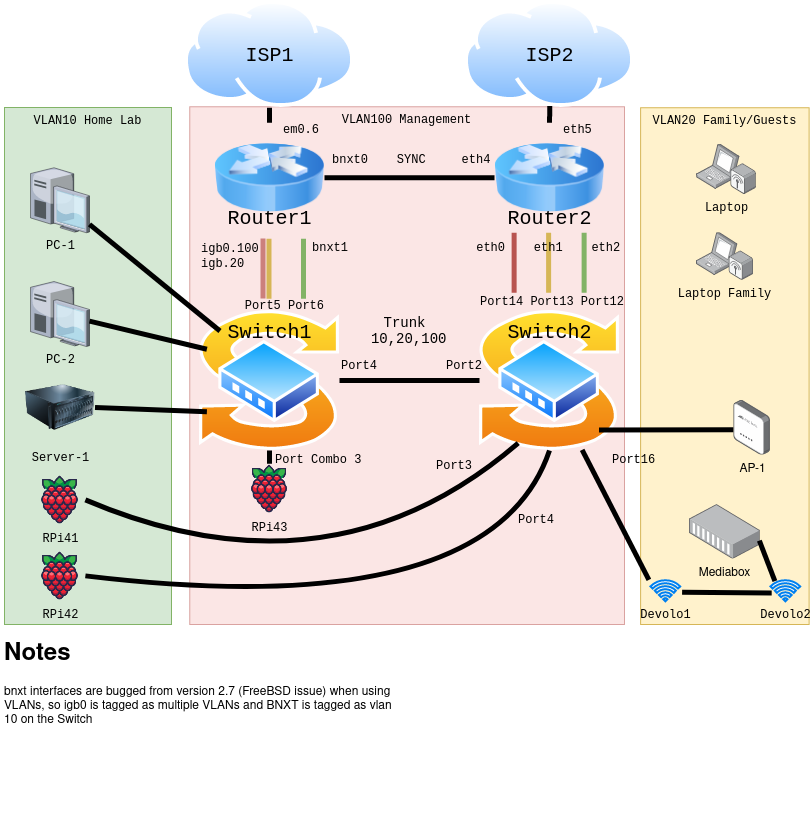
-
@Delegator5042 said in Setting up CARP Master and Backup on a per VLAN basis (Like VRRP): is it possible?:
I have recently learned about VRRP and am fortunate enough to be able to create a home setup with 2 pfsense boxes that each have their own ISP connection.
First lesson to learn: CARP <> VRRP
These protocols are just similar.So I intend to make a setup, where if one of the ISP connections is down, the Backup will assume Master role and provide internet from its connected ISP.
So why want to use CARP for this.
This can be done better by connecting both ISP cables to a single pfSense and configure a gateway failover group.You can use CARP additionally for hardware redundancy if you want.
-
@viragomann said in Setting up CARP Master and Backup on a per VLAN basis (Like VRRP): is it possible?:
So why want to use CARP for this.
This can be done better by connecting both ISP cables to a single pfSense and configure a gateway failover group.I can understand that the setup is not optimal and after reading about gateway groups I think I will follow your advice if I can setup both ISP connections on each router. I've read that you can use a switch on the ISP Ethernet connection so it could be shared with multiple routers, but I haven't tried this.
EDIT: seems like I can't share them for my specific ISPs. Each expects only one connection to one routerI would still like to know if I could force a vlan (or subnet) to use a specific gateway and only when that gateway is down to send the traffic over to designated backup connection.
I imagine if I make a firewall rule that allows all traffic from the VLAN network with the caveat that it goes to a specific gateway, when that gateway is down, won't I have to manually edit the rule each time that gateway is down?
-
@Delegator5042 said in Setting up CARP Master and Backup on a per VLAN basis (Like VRRP): is it possible?:
I've read that you can use a switch on the ISP Ethernet connection so it could be shared with multiple routers, but I haven't tried this.
Yes, put a small switch into each line or even a VLAN capable switch and split it into two virtual switches.
Consider that for CARP, you need an IP on each pfSense and a third as VIP. So you should have 3 IPs on each.
If you haven't there is also a way to configure private IPs on the boxes, but this has some drawbacks.I would still like to know if I could force a vlan (or subnet) to use a specific gateway and only when that gateway is down to send the traffic over to designated backup connection.
You can configure a gateway group and set this as default gateway.
For routing traffic other than according the default gateway you can do policy routing by stating a gateway in the firewall pass rule.You your purposes you can configure an additional gateway group, say with inverted priorities, and use this in the policy routing rule.