Host Overrides doesn't override
-
@sensei-two ah ok..
-
@sensei-two did you solved?
I'm trying now with pfsense 23.05.1 but looking at host-overrides
Warning Do not use DNS override functionality as the only means of blocking access to sites.With DNS Forward (deprecated package) this feature was working fine, with DNS Resolver(unbound) seems to run fine too.
gig@robot:~# nslookup acciaio.internal Server: PFSENSELAN Address: PFSENSELAN#53 Name: acciaio.internal Address: 192.168.22.3Now my question is I can safely use this or should expect some side effect?
i.e. over OPENVPN I cannot resolve acciaio.internal, even if with on server Custom option: push "dhcp-option DNS LAN.LAN.LAN.DNS"
-
@Summer said in Host Overrides doesn't override:
Warning
There is a warning because dns overrides only work if the client is using pfsense as its dns, what if using other dns, what if using doh in their browser. etc...
dns filtering of any kind is only good if the client can not use any other form of dns. Even then - maybe they will just go to the IP directly.
It states the reason why it might not work - right there in the article

-
@johnpoz thanks for clarification, that's ok.
I'm trying from a OVPN client:
checked on ovpnconnect log the DNS is pfsense but:gig@robot:~# nslookup acciaio.internal Server: 8.8.8.8 Address: 8.8.8.8#53 Name: acciaio.internal ** server can't find note.tb: NXDOMAINcould it be Android issue that goes to google instead to pfsenseDNS?
gig@robot:~# nslookup PFSENSEDNS - acciaio.internal Server: PFSENSEDNS Address: PFSENSEDNS#53 Name: acciaio.internal Address: 192.168.22.3 -
@Summer said in Host Overrides doesn't override:
could it be Android issue that goes to google instead to pfsenseDNS?
If your openvpn client isn't asking pfsense dns - then no its not going to be able to resolve stuff that is in pfsense dns only.
If your client is trying to use some other dns, make sure all traffic flows through the vpn, and do dns redirection.
-
@Summer said in Host Overrides doesn't override:
could it be Android issue that goes to google instead to pfsenseDNS?
You've created a host override @pfsensation
Then an android comes into play - and now, you tell me : you did't know that android always phones to home = uses 8.8.8.8 ?
Anyway, this android uses 8.8.8.8 as it DNS source.
With other words : this android connects to 8.8.8.8 and does the DNS requests.
This means that pfSense will never see/smell/be aware of this DNS request.
So you can place whatever host override on pfSense what you want, it doesn't matter.For host overrides to work in such a situation, make a list of them, call Google (8.8.8.8) and give them your host override list.
This is a joke of course.edit :
Let me rephrase the subject :Host Overrides (registred on pfSense) doesn't override (when the LAN device uses another DNS like 8.8.8.8
Get it ?
-
@Gertjan said in Host Overrides doesn't override:
Host Overrides (registred on pfSense) doesn't override (when the LAN device uses another DNS
That's fine but how can it be changed that DNS?
If client get in it's log:
[dhcp-option][DOMAIN][internal] [register-dns] [redirect-gateway][def1]And on server:
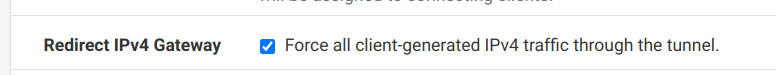
-
I have :
[Aug 25, 2023, 15:45:55] OPTIONS: 0 [dhcp-option] [DOMAIN] [bhf.net] 1 [dhcp-option] [DNS] [192.168.3.1] 2 [block-outside-dns] 3 [register-dns] 4 [redirect-gateway] [def1] 5 [route-gateway] [192.168.3.1] 6 [topology] [subnet] 7 [ping] [10] 8 [ping-restart] [60] 9 [ifconfig] [192.168.3.2] [255.255.255.0] 10 [peer-id] [0] 11 [cipher] [AES-256-GCM] 12 [key-derivation] [tls-ekm]Server side :
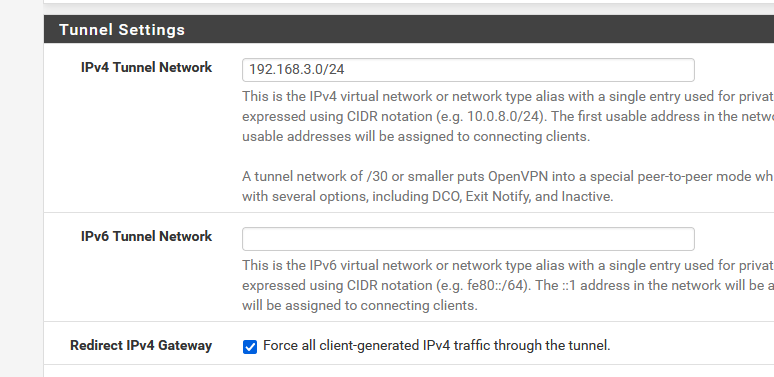
and I've set the DNS as :
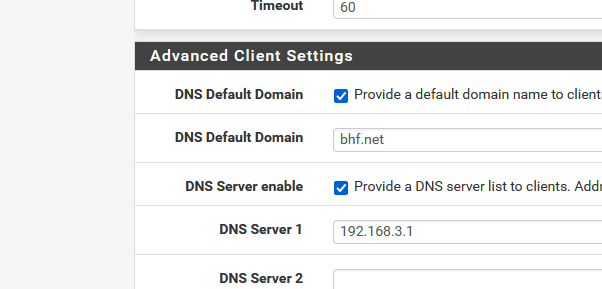
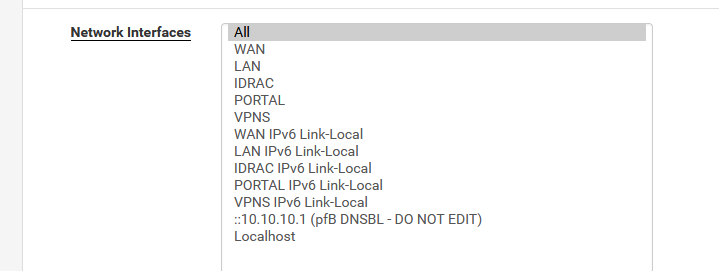
and, unbound listens on "All" interface, which includes my "OPENVPN" interface (which uses 192.168.3.1/24 - which is the tunnel) :
A test on my Phone, connected uing the OpenVPN Client app :
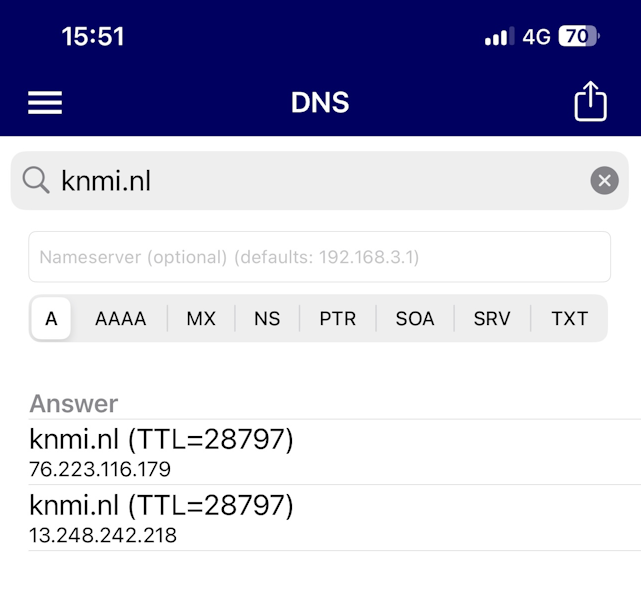
as you can see, it uses 192.168.3.1 as it's DNS. That unbound. And unbound knows about my host overrides.
Lets that : I create a very special host name :
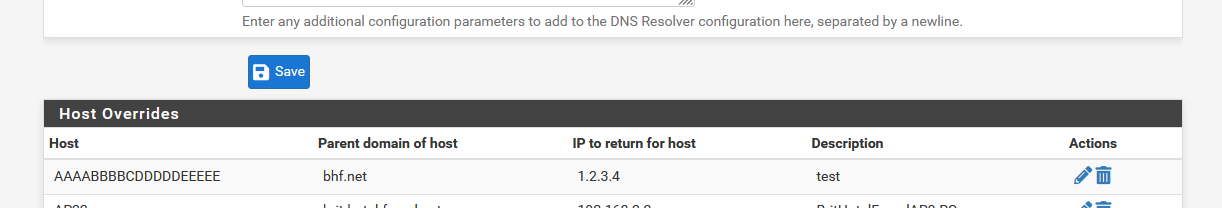
I pre test that AAAABBBBCDDDDDEEEEE.bhf.net on my pfSense LAN connected PC :
Microsoft Windows [version 10.0.22621.2215] (c) Microsoft Corporation. Tous droits réservés. C:\Users\Gauche>nslookup AAAABBBBCDDDDDEEEEE.bhf.net Serveur : pfSense.bhf.net Address: 2a01:cb19:907:a6dc:92ec:77ff:fe29:392c Nom : AAAABBBBCDDDDDEEEEE.bhf.net Address: 1.2.3.4So, that works.
Now my Phone :
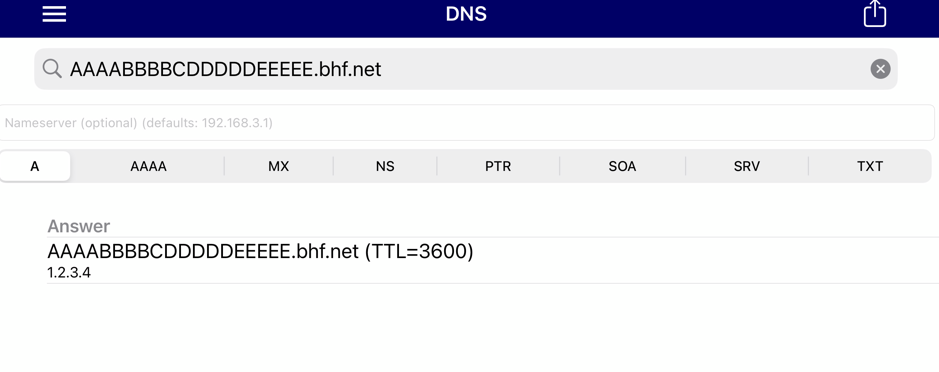
1.2.3.4 also.
Now : your turn.
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
@Summer if you have some app or browser or whatever on your phone that is wanting to use some hard coded dns.. and not doh like in a browser. One way to work around that could be dns redirection.
So if your phone insists on using 8.8.8.8 for example - you could on pfsense do a dns redirection so when it tries to talk to some dns, you redirect it to use unbound on pfsense.
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html
-
Thanks @johnpoz you've made it!
Finally it works!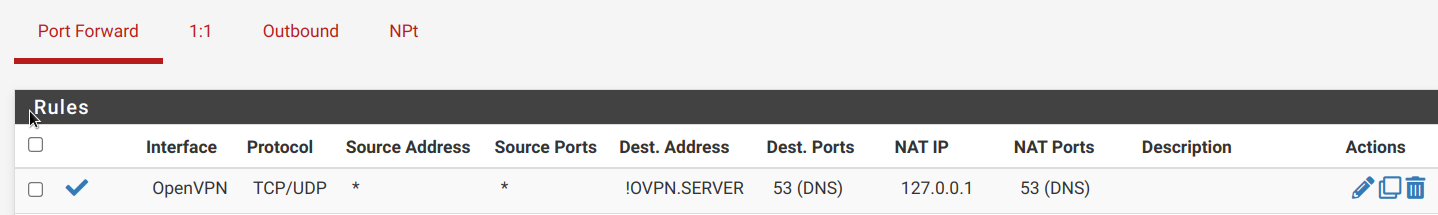
-
@Summer You may also want to block DoH, where (many) browsers bypass DNS to connect out to their DNS over HTTPS service. This page has a pfSense PDF that is very detailed but thorough.
https://github.com/jpgpi250/piholemanual#doh