How do you design tagged and untagged networks?
-
When designing a network, what is the best method to use untagged and tagged interfaces?
- Is it best to use eg. the 'LAN' interface as the untagged management network and all other networks as tagged VLANs?
- Or do you use the 'LAN' interface untagged as the network for all the clients and do you tag all other networks?
- Or do you tag just all networks and don't you give the 'LAN" interface an IP address?
I know there is no golden rule and no best answer. But I would like to know your ideas and best practices. Thanks!
-
@Krisbe if there is going to be only 1 network on an interface, then I leave it untagged. If I am going to put more than 1 network on an interface - I personally leave 1 network native (untagged) and tag the other vlans I put on that physical interface.
Other people might tag all the vlans on an interface, and have no untagged (native) network.
The only "golden" rule if you will is you don't run more than 1 untagged network on the same physical interface. And even then - you can still do that - there is just no isolation at layer 2. So its going to be problematic.
So for me - these interfaces are all untagged network, that connect to a port on my switch that is in a specific vlan. Other than vlan 4 and 6 that are tagged because they are also on igb2, but igb2 has a native (untagged) network on it as well.
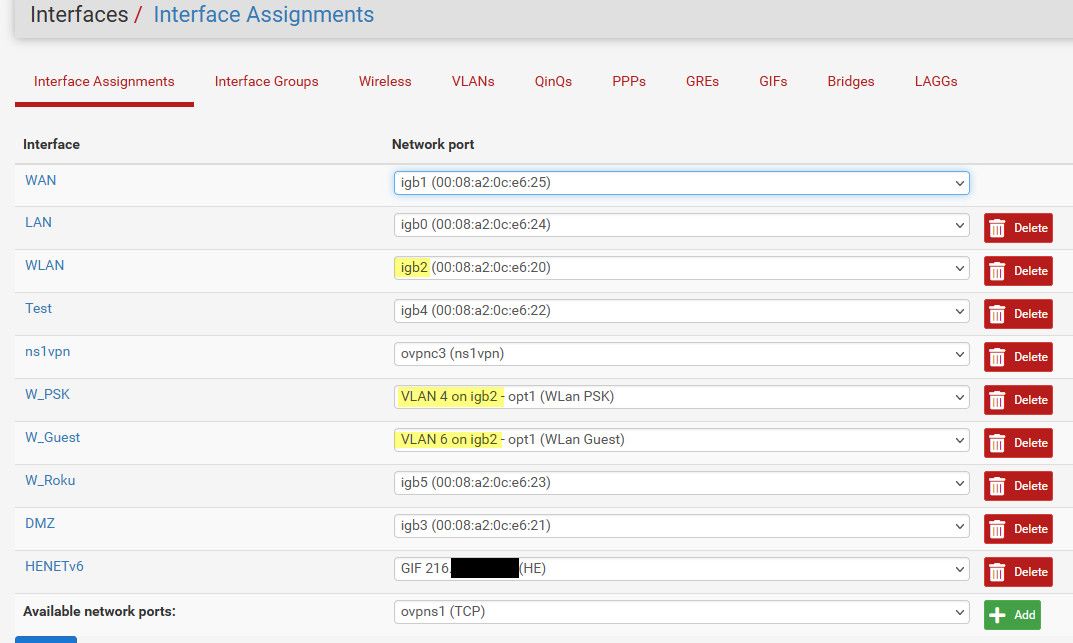
So the switch port igb2 is connected to, there is a untagged vlan and then there 2 tagged vlans (4&6)
-
Not having any real experiences with VLAN, as I prefer running 'more networks / cables' (for now).
But, when you think about VLANs, add to your to-do list : check out the VLAN capable switches, "play" with them first. Check out their GUI's, very often .... really bare-bone, not very well designed .... and as usual, their are good the ones ... probably the expensive ones.
A 'normal' switch has no button, no menu, nothing. Just X ports and power inlet. An admin's dream.
VLAN switches have their own IP, have a GUI to administer, and such, open up a whole new device that has to be maintained. Settings have to be back-upped, you'll probably have to make a 'design' how pfSense VLAN settings correlate with the VLAN capable switch(es). loose that paper, and you lost your day.
Cables have to be labeled now because "plug it in and it works" isn't guaranteed at all.Btw : your adding a new 'security' factor right into your network.
-
@johnpoz said in How do you design tagged and untagged networks?:
Other people might tag all the vlans on an interface, and have no untagged (native) network.
Yup I'm one of those people. If possible I avoid having tagged and untagged traffic on the same interface. The reason for that is that VLAN config errors or badly behaved devices are far more likely to strip tags incorrectly that add tags. The results in traffic that should be on a VLAN being untagged and if that link has an untagged interface it will hit that.
-
All my IF's with tags have PVID/"Native vlan" as 999 , and 999 is not used for anything, besides being "native".
Well ... except my Unifi WiFi IF .... I made that back when you couldn't TAG the "Control" stream for the UNiFI's.And i have spread out the vlan load over two interfaces to improve throughput.
Vlan1 is also unused in my networks.
/Bingo