Both WAN interfaces are in the master state
-
Re: Re - Compatibility between VRRP and CARP
After disabling IGMP and storm control on the Dell EMC Networking N1524 switch where the appliances are configured, my HA configuration partially worked. The WAN still remains in the master state on both nodes.
In pfSense, I use igb0 for the WAN, 4 interfaces in a LAGG for VLANs, and pfsync is on igb5.
Running pfSense 2.7 on both nodes.
I'm considering packet capturing in pfSense. What do I need to check in the packets?
-
EDIT:
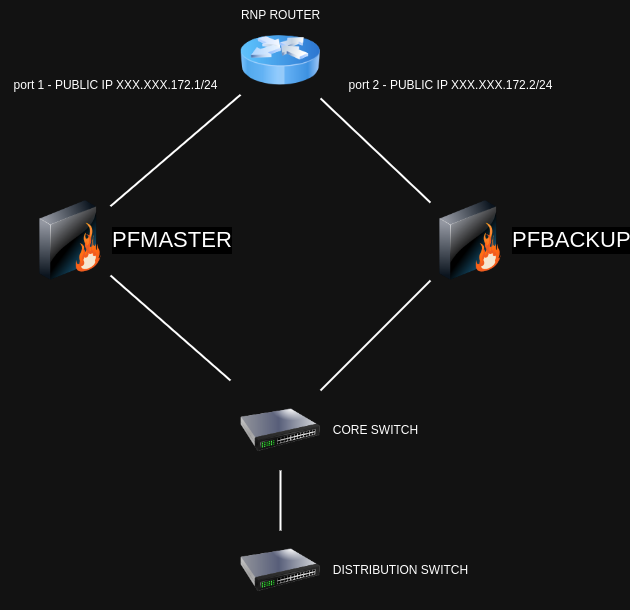
In RNP's router, their technicians configured it using public IPs from our range to set up each port with one gateway.
Wouldn't this be like having HA with Multi-WAN?
-
@empbilly re: master, did you find https://docs.netgate.com/pfsense/en/latest/troubleshooting/high-availability.html#both-nodes-appear-as-master ?
re: the ports, not sure I understand. The .1 and .2 there are on the RNP router? A normal HA setup has either 3 public IPs, or in edge cases 1 public IP and two IPs that can get to the Internet (so pfSense can update itself).
It would not be normal to use two different interfaces on an ISP router and it would not be normal to have the same /24 subnet on two different interfaces because that router won't know where to send packets for the /24. Unless the RNP router is a switch?
https://docs.netgate.com/pfsense/en/latest/highavailability/index.html#ip-address-requirements-for-carp
-
@SteveITS said in Both WAN interfaces are in the master state:
re: the ports, not sure I understand. The .1 and .2 there are on the RNP router?
Yes.
@SteveITS said in Both WAN interfaces are in the master state:
A normal HA setup has either 3 public IPs, or in edge cases 1 public IP and two IPs that can get to the Internet (so pfSense can update itself).
It would not be normal to use two different interfaces on an ISP router and it would not be normal to have the same /24 subnet on two different interfaces because that router won't know where to send packets for the /24. Unless the RNP router is a switch?
To avoid using it this way, we would need to have a switch hierarchically below the RNP router. I believe it's not the ideal solution, but if it's the only option, we'll have to go with it.
I know it's not within the scope of forum questions, and if you can answer, what would be the port configurations for this switch between the RNP router and the appliances?
-
@empbilly Some switch notes are here:
https://docs.netgate.com/pfsense/en/latest/highavailability/index.html#switch-layer-2-concernsA dumb switch should "just work." :)
With the HA the point is the upstream router doesn't know the shared IP moved so all sessions stay open.
If that RNP router really does have the same /24 subnet configured on two interfaces I'd expect it to have a lot of trouble routing. If it's smart (dumb?) enough it might ignore the second if that interface is down/disconnected.
-
@SteveITS said in Both WAN interfaces are in the master state:
A dumb switch should "just work." :)
Exactly!! We took a gigabit dumb switch that was sitting idle and placed it between the RNP router and the appliances, and voila!!! It worked!!!
Anyway, if we were to add a managed switch, could you tell me how the port configurations would look? Would a LAG work? Port mirroring?
-
Jumping in here, and going to be honest didn't read the entire thread but tried to skim it.
Generally with an HA setup you want a switch for the WAN side as well, otherwise the nodes can't communicate to one another about who is up/down.
Easy setup is to just plug the router from the ISP into a switch and then plug both HA nodes into that same switch, and then configure the switch to do the VLAN tagging for you (so you basically have a WAN VLAN) so it's only those 3 things on that VLAN.
I have a similar setup with HA in a prod environment and it works as expected with this setup.
-
@empbilly I don't think you need or want to do anything on a managed switch. The two routers just need to talk to each other, and the ISP router. Port mirroring is not used.
-
@SteveITS Yeah this is correct, no need for a managed switch, personally though I usually use an existing switch, setup the VLAN with tags at the port level, this way I don't need a different switch for WAN. So that's why I suggested that, but only works if you have available ports on an existing managed switch, otherwise an unmanaged one makes more sense.