HAProxy 502 error when using POST method
-
Hi there
I have setup HAProxy to offload my internal domains. The SSL offloading works fine, except that as soon as a POST method is being used, I get a 502 Bad gateway error.
My setup:
I have an internal wildcard certificate through let's encrypt and cloudflare which goes on my top level domain. e.g. *.home.mydomain.com
Then I have my backends setup without ssl.
The frontend terminates on 2 virtual IPs, 1 for each VLAN I have backends in. They are configured separately.
Then I have the action which routes this to the backends.DNS resolves are there. Those work.
This all works fine, except for the POST methods. The weird thing is, it is only for the second virtual IP, it seems the first works fine, although they are both setup the same way.
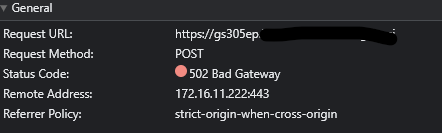
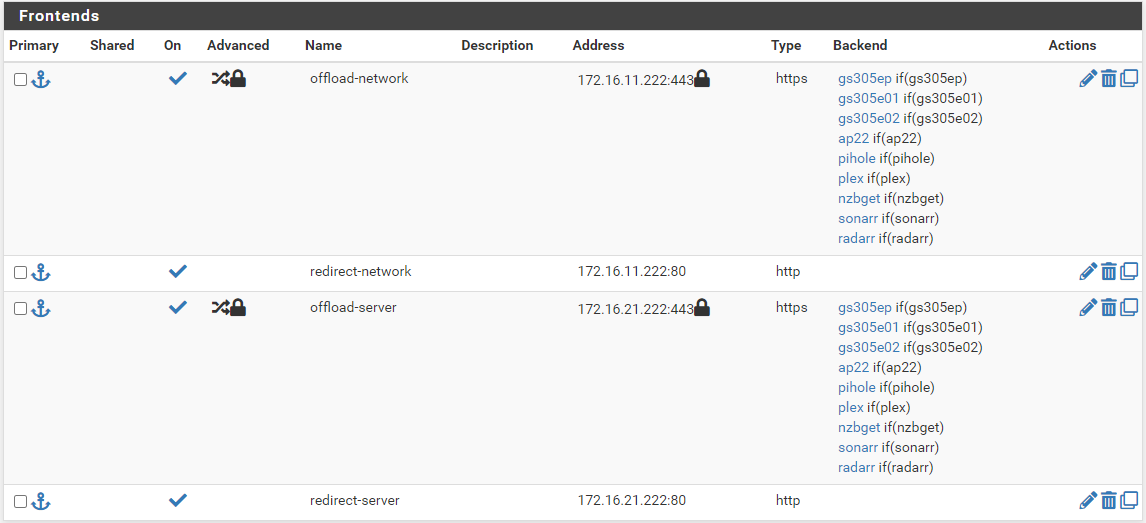
Anyone got an idea why?
-
@Berick
Did you redirect non-SSL request to HTTPS. If yes, how did you do that? -
@viragomann I did, as you can see with a frontend redirect rule.
-
@Berick
All I can see there, are frontend names beginning with "redirect", the listening IPs and the types.
But the question was, how you did the redirects. This is sadly not explained by that screenshot. -
@viragomann sorry, sure thing here it is:
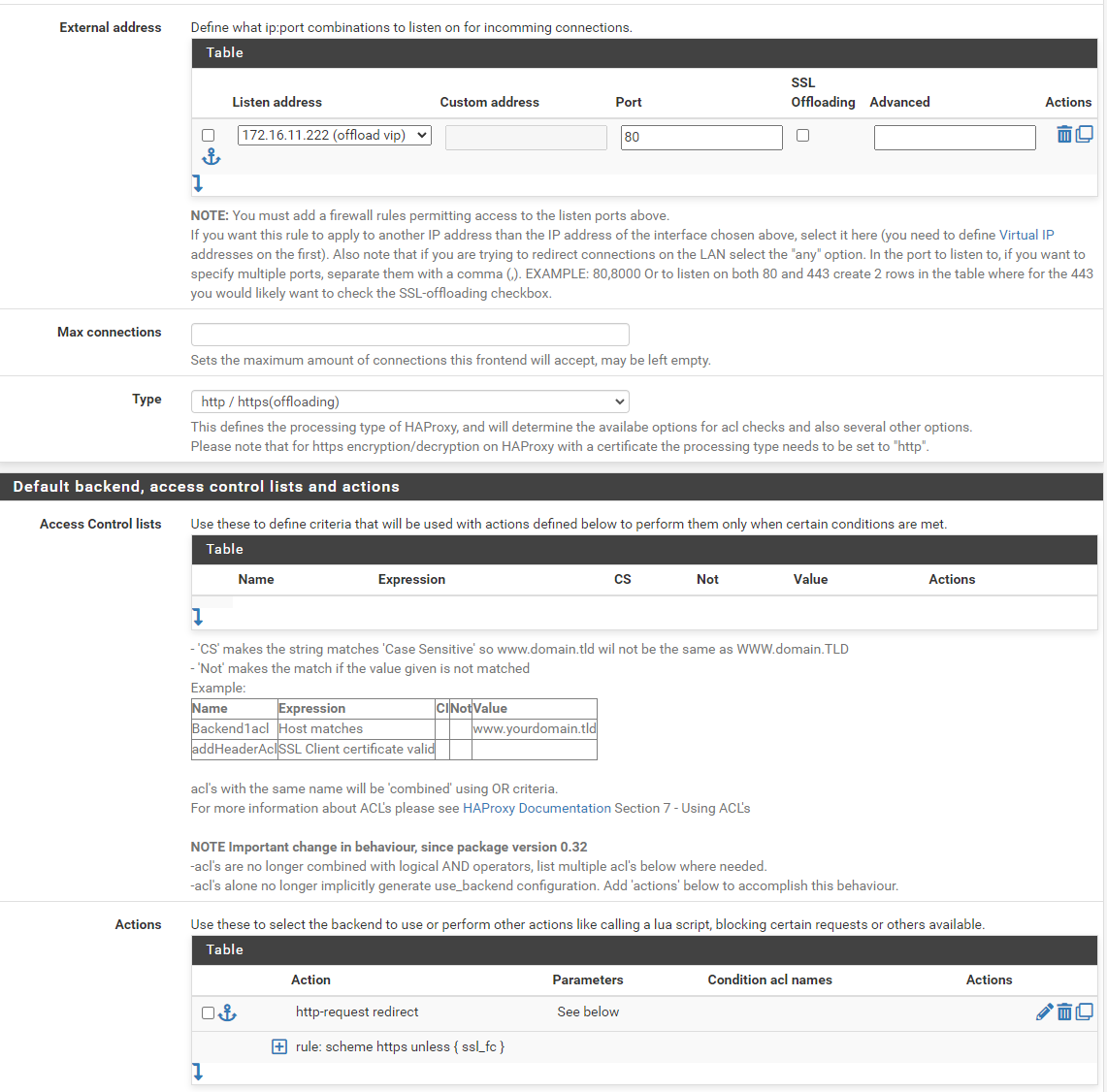
-
@Berick
Your're missing an ACL for this action.
Is that even accepted by the GUI this way, with the 'unless' directly in the rule?In my settings I have this ACL

(note that 'not' is checked)
and this action
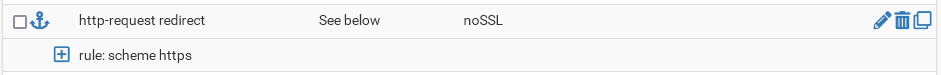
to achieve https redirect. -
@viragomann changed it to your config, but unfortunately, no improvement, still bad gateway error.
-
@Berick
Maybe you get more details on the issue from the HAproxy log after enabling logging. -
@viragomann This is what I have in the logs even on debugging level:
Sep 19 22:25:01 pfSense haproxy[99796]: 172.16.10.11:65470 [19/Sep/2023:22:25:01.856] offload-network~ gs305ep_ipvANY/gs305ep 0/0/5/-1/66 502 209 - - SH-- 1/1/0/0/0 0/0 "POST /login.cgi HTTP/1.1" -
@Berick
That's not really much.
Maybe you can find more details, when running the browser debugging mode.I got a similar problem solved by adding this response header:
http-response header set > name: content-security-policy, fmt: upgrade-insecure-requestsYou can try, but not sure if this helps.