Streaming services discover using vpn
-
Hi guys.
Need some advice. This is not to be used for geoblocking but simply routing traffic so I was wondering how would you come about this?
Viaplay detects vpn so I you use your companys IP address and there is a VPN attached to that, Viaplay will block the IP used and tell you its a vpn.
Thats kind of annoying so now I cannot watch Formula1 on Viaplay at the office....
How would you obfuscate traffic to circumvent that?
-
Easy. Use your smartphone's Data Plan (not WiFi) and stream Viaplay using the proper app on your phone
 . The IP will be properly "geolocated", and your mobile service provider is not a VPN so Viaplay won't block it.
. The IP will be properly "geolocated", and your mobile service provider is not a VPN so Viaplay won't block it.Bonus points -- your employer will be happy you are not using their network resources to stream Formula 1. However, they might still have an issue with your attention being focused on Formula 1 and not their business requirements
 .
. -
It's usually because DNS is resolving from somewhere completely different. Make sure requests are also using the VPN. That can be easier said than done of course.

-
@stephenw10 All traffic is routed via the VPN and exits as it should. No DNS leaks.
But www.ipscorequality.com reports that its a VPN exiting and the IP is "dirty" when we ask viaplay support.
-
Hmm, not sure then. There is big money being use to develop methods to detect VPNs though so it doesn't surprise me that there are other methods.
I can't reach the site at all to check interestingly. What does it report for you? -
@stephenw10 said in Streaming services discover using vpn:
I can't reach the site at all to check interestingly
I would assume a typo, because that fqdn does not resolve on public internet.
Maybe he meant https://www.ipqualityscore.com/
I wouldn't put much trust in that site - says my IP is proxy.. which clearly it freaking isn't
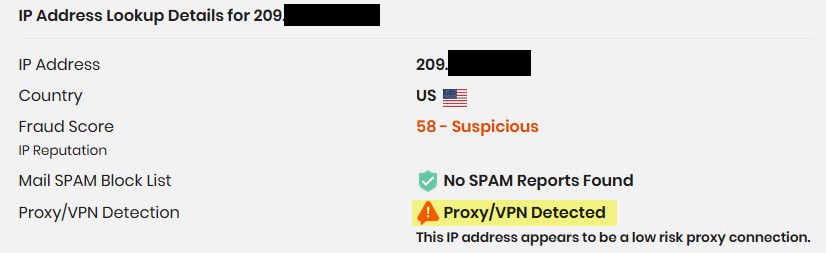
According to that site ns1.netgate.com - is a freaking proxy..
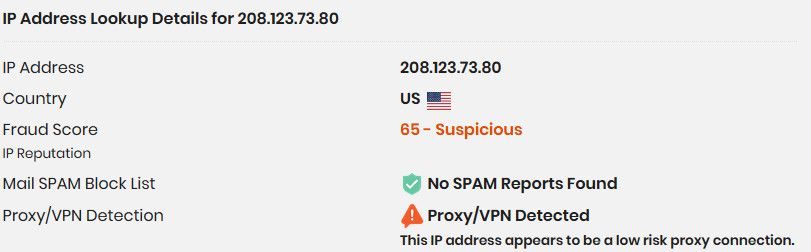
ns1.netgate.com. 1682 IN A 208.123.73.80 ns2.netgate.com. 1682 IN A 208.123.73.90 ns3.netgate.com. 1682 IN A 34.197.184.5All 3 of them are according to that site.
-
Mmm, seems accurate then!
-
@stephenw10 what kind of shenanigans you guys doing with your NSers - your fraud score is higher than my IP hehehe..
You guys hosting a tor exit node from your NSers ;) hehehe
-
Mmm, I was trying to think. I'm not 100% sure how that is setup currently. Pretty sure it's not behind a VPN though.

-
@stephenw10 Its possible those IPs were used before in a shared environment.. But then for that site to be valid, they really should list a date of when this reputation was last figured out, etc.
I mean its quite possible for example that the last guy that had my IP was doing some proxy stuff.. Or other stuff to lower the reputation, etc. Same goes for your NS IPs..
But I have had this IP for quite some time..
These sorts of lists are really only valuable if they are maintained.. Some guy in 2000 using this IP for bad stuff, its now 2023.. And my IP is still listed at bad as example.. Come on.. that data is of little value.. Now a report that hey we are seeing bad stuff from this IP in Feb of 2023 would be way more valuable info. Maybe you have to use their paid service for such info?
-
@johnpoz said in Streaming services discover using vpn:
https://www.ipqualityscore.com/
Just tested my static IP with this service and the score is about the same as yours. Incorrect and pretty much misleading and useless.
Ted
-
@johnpoz It would be interesting to reputation test their site.
Ted
-
@tedquade hahaha - good idea..
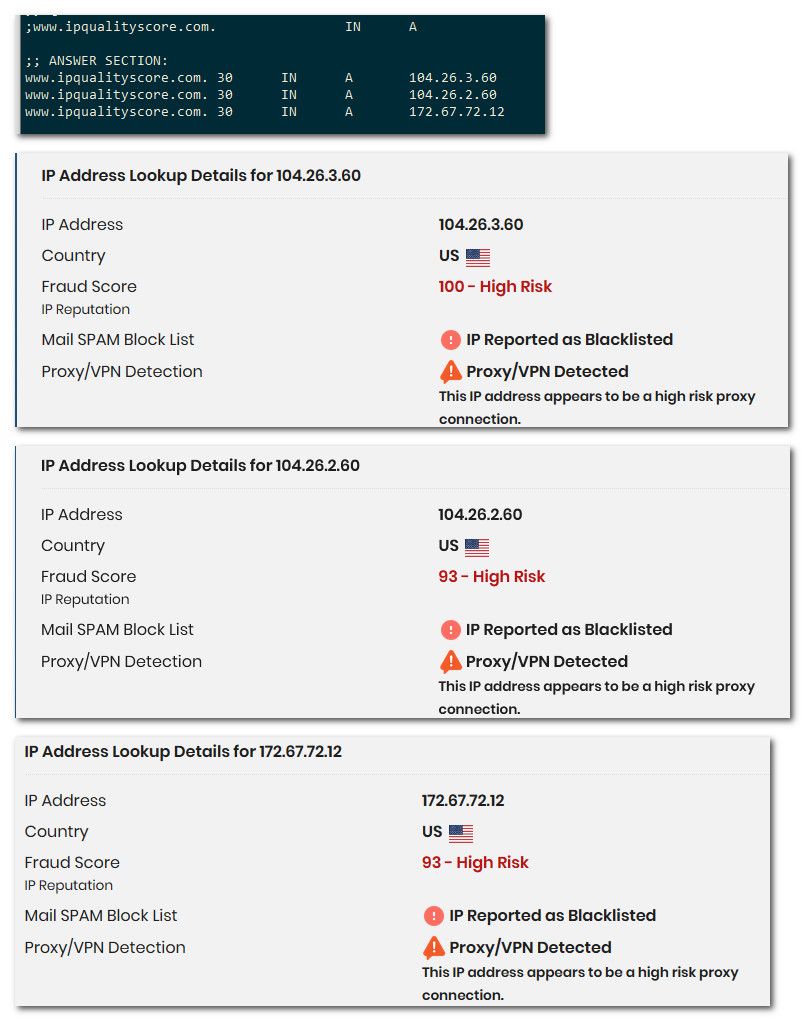
All their IPs are also on some blacklist ;)
So yeah this sure seems like a great site for IP reputations - where I do I sign up for their "pro" service.. <rolleyes>
-
@johnpoz I think this one can be put to rest now.
Ted
-
@tedquade yeah - this site is one of many that you can look up if an IP is a vpn, many of them might not have the best data.. But it doesn't matter if an IP gets listed.. Then yeah other companies using these lists can block you from a vpn.
Whatever this site is he is trying to stream from is blocking his company IP, there isn't much you can do about it. Watch on your phone, or tablet using hotspot off your phone even if need be.
But these streaming services have gotten better, and more concerned with if you connecting via something that could obfuscate your geo location. I know some of them block HE ipv6 tunnels, which are not really true "vpns" but they can be used to change what part of the world you look like your coming from.. The "tunnel" is just a gre tunnel, which isn't encrypted, etc. But you can use one of their pops that are in a different part of the world than you actually are from.
Love to work in the company IT shop if someone asked if could get off some blacklist because can not access some streaming site to watch tv shows ;)
We had an issue once where we had an exit point in FL, but for some freaking reason maxmind was saying it was in Vietnam.. Made no freaking sense, but was causing users issues with accessing their bank sites, etc. I tried for months to try and get maxmind to fix it - which I don't think they ever did.. But we just stop using that network as our exit point for users.. And it was our IP.. we had owned that /16 space for years and years and years.. And it was correctly registered in arin for what location that network was coming from, etc.
It wasn't blacklist or on any bad lists - but some banks were not letting their users access when you tried to login from an IP that from their geoip stuff was saying was vietnam, and not the us, etc.
-
-
@stephenw10 https://forum.netgate.com/topic/182866/universal-procedure-pointers-upp-mzstatic-com-s-mode-of-access-redirector-question
I agree yes they are, Apple Music now does this. As the domain mzstatic no longer needs to be on an approved "splice" list. It uses UPP to force the splice over the established connection. This would bypass even Palo Alto firewalls.
-
@johnpoz I had a huge TB sized container hidden inside the ".Trashes" folder on my NAS this week. Unreal, I had to disable system integrity to even remove it. This invasive actor used all of the hidden spotlight index folders like v-100 this invasive actor had full snapshots and everything. There is no way that the index and .trashes folder would ever be over a TB in size. There is lots of invasive actors right now out there. I wonder the main mode of use, maybe it is some type of invasive UPP being abused.
-
@JonathanLee and what does that have to do with streaming services marking an IP as bad and not letting you connect? If your exposing your nas to the public internet - yeah its going to be a target..
As to your .trashes folder being a specific size.. That would depend on what you deleted, and what size you set for your trash.. Because you found a large trash file - how is this an indication that you were hacked?
-
@johnpoz it had sandbox folders in it like snapshots of something. I never deleted that. It was really weird. Both V-100 spotlight folders and .trashes had that. I don't expose the NAS it's protected behind the firewall. Could have been a timebomb bug and it never got implemented because I blocked it. I thought maybe someone else has that bug and they don't know what is making the IP show as high risk. I don't even think OS x uses sandbox Microsoft does. Someone has to have seen this weird HDD resources consumption issue too. One can say it's the perfect place to hide. Some hidden folders that no one really looks at on any USB drive that is plugged into a apple OS. An invasive actor might use it for a container to do proxy chains with, or an exit node. The normal users would not think to look at it, they just use the NAS and the NAS uses their Internet without them knowing. That could cause a bad IP reputation without them knowing. I was flat out confused, thinking why is the folders all the sudden so massive in size. Just a weird situation. It's like a scary Halloween Pumpkin bug. Hey, that reminds me of the Metasploit's pumpkin I saw during a lab in October.