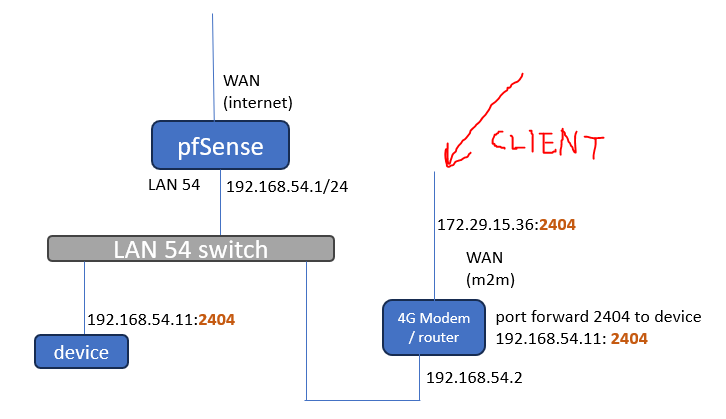
Create gateway from router attached to LAN
-
@viragomann does this configuration can work in theory ?
do i need to set extra gateway on the pfsense ? -
@Bambos there are a few ways to skin that cat..
Is the source IP always going to be that specific IP, or atleast in that network? if so host route on your 54.11 box pointing to that IP or network to the 54.2 address would work.
or if that 4g/router allows for natting so the traffic looks like it came from 54.2 vs 15.36 would also be a solution.
Placing some route on pfsense would just lead to asymmetrical routing. And would be very problematic at best.
Other option is to connect this other router via transit network to pfsense.. So now pfsense knows they if one of its clients wants to go to some 172.29 address send it to that router.
-
@johnpoz Hello Jon, yes, the IP's are static.
what do you mean by transit network ? ? connect the 4G modem / router on a pfSense interface (not on LAN) ? (Static Route i guess... ?)
-
@Bambos yes a transit network is a network that connects routers together - it does not have hosts on it..
Here is a drawing showing how you would use a transit network with another router.
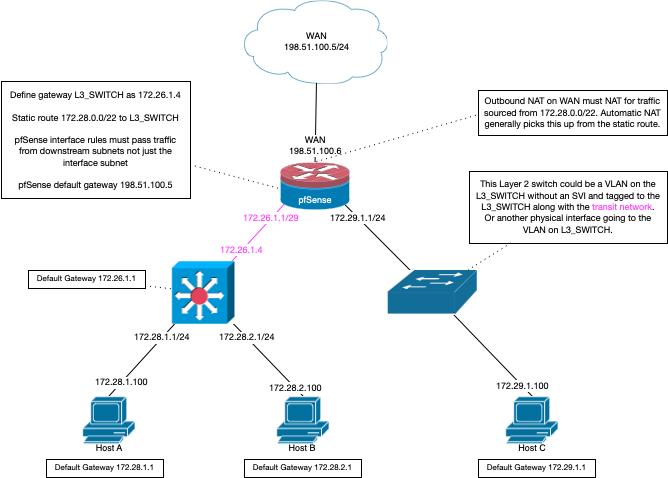
This shows a actual downstream router in your own network, where its default route is pfsense.. But that doesn't have to be the case.. It could just have routes to the networks on pfsense, and some other default route.
But if this the only host that needs to be able to talk to the other network, a route on that specific host would be an easier solution.
-
@johnpoz ok clear ! so in order to implement a transit network between routers (as this example) practically is connect the 4G modem/router to a dedicated interface on pfsense. I have tried that in the past and is working. But now i'm checking a simpler method for implementing this, and also using one interface less on the main pfsense router.
Assuming that 4G/router doing NAT (because of the port forward), in theory would be ok and the traffic will not pass through the pfsense. the device 54.11 will see that packets coming from 54.2 and reply back to it.
-
@Bambos said in Create gateway from router attached to LAN:
he device 54.11 will see that packets coming from 54.2 and reply back to it.
Exactly that is another way to skin the cat, and would be very simple solution. But depends if that router would do that.. If the 54 network was its "wan" then you wouldn't need port forwards even..
But if you can get that 4g router to do a outbound/source nat so 54.11 thinks the traffic is coming from 54.2 address then yeah that is a clean simple solution.
-
@johnpoz
I am using asymmetrical routing with my layer 3 switch. It works fine for me. I used a transit network last time with pfsense, due to your recommendation years ago. This time when I setup pfsense I used asymmetrical routing like I did in my old Cisco days. I see no real difference using my Cisco small business switch in L3 mode at my home. My L3 switch knows all the vlans and pfsense has no vlans defined and knows nothing of them. My L3 switch has all the vlans defined on the switch and DHCP. pfsense only has 1 static LAN IP defined which connects to my L3 switch. All my traffic routes from my L3 switch to pfsense. -
@coxhaus said in Create gateway from router attached to LAN:
I am using asymmetrical routing with my layer 3 switch
Well that is not a very good thing to do, and yeah can cause all kinds of problems. This can be a real problem with a stateful firewall.
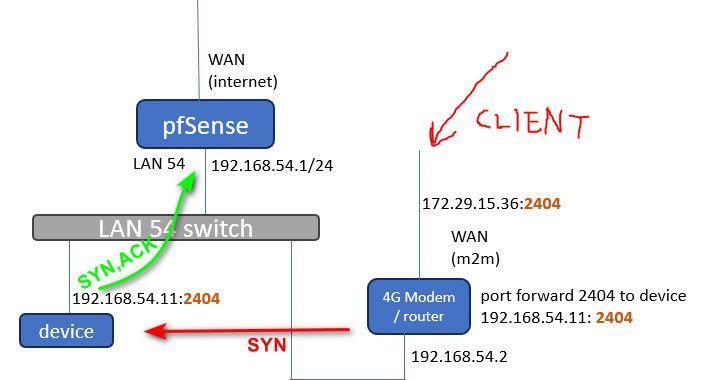
When your 54.11 tries to send an answer to 15.36 the syn,ack it sends to pfsense would be denied.. Since pfsense never saw the syn to open the state..
edit: if your going to route on your L3 switch.. Then setup a route on it to send traffic to that 172.29 back to your 4g.. This way pfsense never sees the traffic and wouldn't block the syn,ack when it never saw the syn.. But wouldn't work if your gateway on your device is not the svi on the switch.
Off the top there are 3 ways to skin this cat, using routing via actual transit network on pfsense. A host route on the device for that 172.29 network or host IP that is sending the traffic. Or nat the traffic..
-
@johnpoz Hello John,
this is very interesting , so following a test environment for your third suggested option, i used a second pfSense box to simulated nated traffic coming from WAN through port forward. the setup is the following:
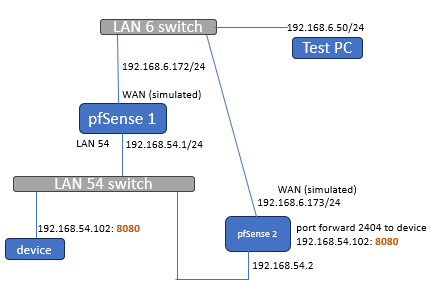
There is a device 54.102 : 8080 running a web server on 8080 port. prove that is working... :
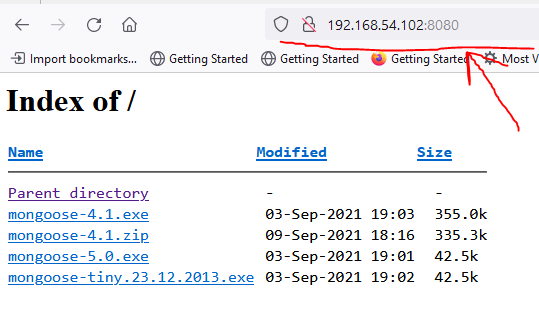
on the secondary pfSense to simulated the nated traffic (54.2) i made a port forward from WAN to 54.102: 8080
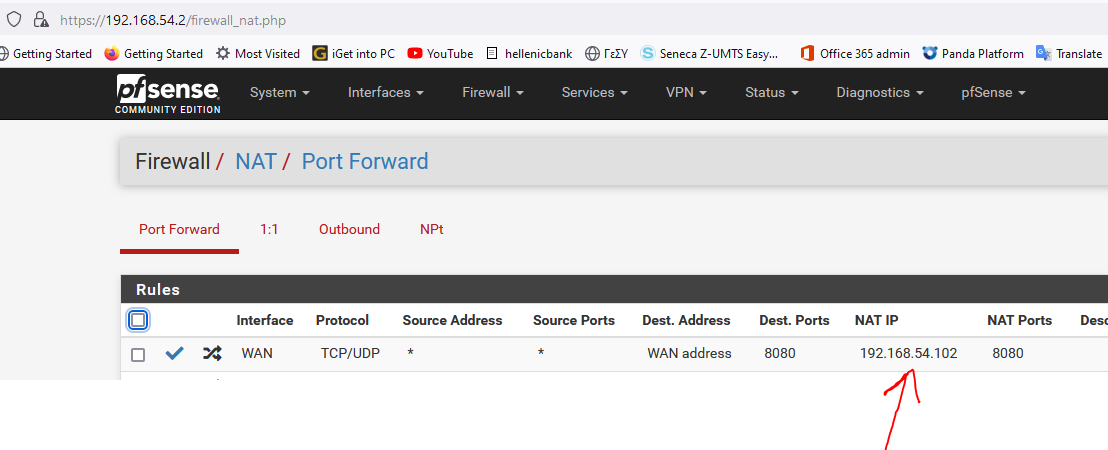
BUT , when requesting from the test pc (6.50) the 6.173:8080 is NOT! working. That's why i stated from first post that maybe extra rules or settings are needed.
I'm open to make more test on this setup. (both pfsense boxes are CE2.6) -
@Bambos if your pfsense wan is rfc and per what make of your drawing you would need to make sure you disable the rfc1918 rule.. Because your source IP.. 192.168.6.50 would be blocked no matter if you created a port forward or not.
And that test doesn't look valid either because pfsense 2 wouldn't be natting that 6.50 to its 54.2 address if the traffic is coming in its wan. You would need to create an outbound nat on the pfsense2 box lan interface.. So traffic coming into the wan isn't the 6.50 address, but looks like it comes from the pfsense2 54.2 address.
So you would need to disable the block rfc1918 rule on pf2 box, port forward, and create a outbound nat on the pf2 lan interface so it changes that 6.50 to the pfsense 54.2 address. Otherwise your 54.102 is just going to send its answer to 6.50 back to pf1, which would be SA, and pfsense would block.. Without the source nat your still asymmetrical
edit: or you need to have your pf2 box lan be the 192.168.6 address, and then there is no need for port forward or disable rfc1918 rule and it would auto nat any traffic from its "lan" to its wan IP 192.168.54.2.. And would really just work out of the gate.
your 6.50 client on pf2 lan wanting to go to 54.102 would be allowed by the default lan any any rule, and by default be natted to the pf2 wan of 54.2 and be sent direct to the 54.102 box.. The 54.102 box would send its answer back to pf2 and pf2 state would allow the traffic back, even though the source is rfc1918. Pf1 would never be involved in any part of the conversation.
-
@johnpoz Thanks a lot !!! is working with port forward and outbound as you suggested (using pfsense box) .
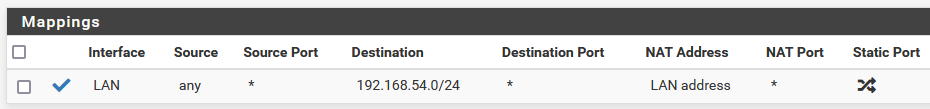
there is no option to make the outbound rule for a single host.
So now is a matter of the 4G router if it can make the same port forward and outbound translation.
-
@Bambos said in Create gateway from router attached to LAN:
there is no option to make the outbound rule for a single host.
select network > state the IP > select /32 mask
-
^ exactly.. But to be honest you could also just put the restriction on your port forward as well. If your source on your port forward only allows single source IP.. Then it doesn't matter if your outbound nat source is any or /24 or /16, etc. since the only one that would be hitting the outbound nat would be the traffic that is allowed via your port forward.
-
@Bambos
Just a thought, If you can use 2 pfsense boxes why can't you use 2 WAN interfaces on 1 pfsense box? -
@coxhaus i guess you didn't follow along the testing.
the 2 pfsense boxes was just for experiment.
the target was to use one network interface LESS, than the previous setup, (and also bypass the traffic from pfsense).
The initial setup was like you say.