Getting private/local IP on WAN
-
If you copy the file to /conf it will be used in preference to the system generated file.
Also check other config options: https://mpd.sourceforge.net/doc5/mpd.html
-
@stephenw10 ok so I should copy mpd_wan.conf to /conf and edit it there leaving only the line that needs to be overridden in the file correct? just making sure because I tried a couple of things but nothing is enforcing the edit we want. Thank you for all your help Steve.
-
Nope it uses the complete conf file from there so it has to contain everything it did in /var/etc
-
@stephenw10 oh ok thank you, i'll try it out
-
@stephenw10 copied the whole config file and edited it and it is overriding correctly but it's still retrying every 9 seconds after timing out. Might this line be useless for this? if so, what can I edit in it that could override this?
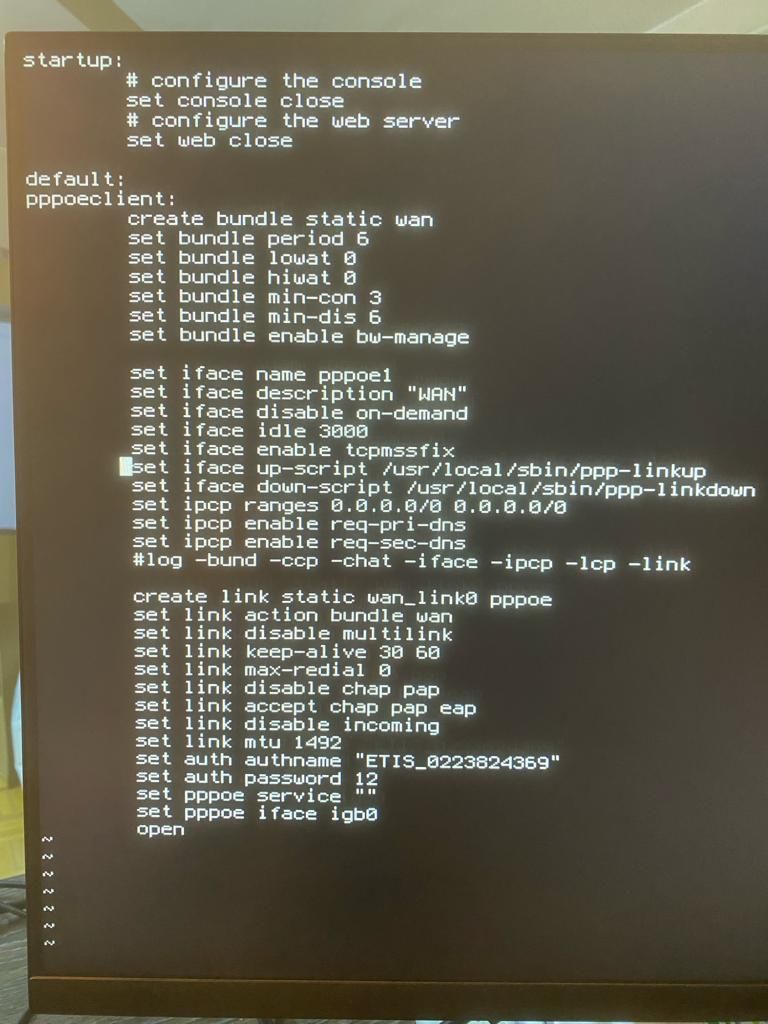
I think this should be available in the GUI as other people might have the same issue too, there are a lot of slow and stupid ISPs.
-
Can anyone help?
-
Yeah, the keep-alive setting probably isn't what you want there, I expect that to apply once the link is up:
This command enables the sending of LCP echo packets on the link. The first echo packet is sent after seconds seconds of quiet time (i.e., no frames received from the peer on that link). After seconds more seconds, another echo request is sent. If after max seconds of doing this no echo reply has been received yet, the link is brought down. -
@stephenw10 what can I do then? there is no way to get PPPoE to work on pfsense then?
-
Well there may be other mpd options there that would help here. I've never tried because I've never seen a PPPoE link that took that long responding.
-
@stephenw10 do you know any other mpd options that might help? it's literally a 3-second difference
-
@aelakkad it connects fine on windows and on the router itself so why does pfsense force 9 seconds when it could be more than that?
-
Without seeing the actual pcap data it's hard to see exactly what the timing is. It look to me like pfSense is sending requests with increasing delays; 2s then 4 s etc. The server sends a response after ~4s nd that restarts pfSense's sequence. So pfSense could be rejecting the response, without logging that for some reason. That could be because it's a response to the first request not the current one.
Try adding:
set debug Xwhere X is 0 by default but can be higher. -
@stephenw10 do I add it in the /conf/mpd_wan.conf file or in the tcpdump commad?
-
Im trying to highlight them below, they look very consistent and keeps going like that the difference is almost exactly 10 seconds
00:54:15.668893 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 00:54:16.358748 PPPoE PADO [Host-Uniq 0x8072780400F8FFFF] [Service-Name] [AC-Name "RMS-BNG-NE40X8A-04"] 00:54:17.397076 IP6 fe80::b2be:76ff:fee1:d6fb > ff02::1: ICMP6, router advertisement, length 32 **00:54:18.540483 PPPoE PADI [Host-Uniq 0x4071780400F8FFFF] [Service-Name]** 00:54:18.674857 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 00:54:20.554203 PPPoE PADI [Host-Uniq 0x4071780400F8FFFF] [Service-Name] 00:54:21.680748 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 00:54:23.659903 ARP, Request who-has 192.168.1.100 (00:1b:21:48:da:98) tell 192.168.1.1, length 46 00:54:24.138309 ARP, Request who-has 192.168.100.101 tell 192.168.100.200, length 46 00:54:24.645205 PPPoE PADI [Host-Uniq 0x4071780400F8FFFF] [Service-Name] 00:54:24.686743 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 00:54:24.798613 ARP, Request who-has 192.168.100.101 tell 192.168.100.200, length 46 00:54:25.158660 ARP, Request who-has 192.168.1.100 (00:1b:21:48:da:98) tell 192.168.1.1, length 46 00:54:25.793111 ARP, Request who-has 192.168.100.101 tell 192.168.100.200, length 46 00:54:26.790738 IP6 fe80::b2be:76ff:fee1:d6fb > ff02::1: ICMP6, router advertisement, length 32 00:54:27.692753 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 00:54:27.930098 IP 192.168.100.200.5353 > 224.0.0.251.5353: UDP, length 36 00:54:27.935885 IP6 fe80::7367:caec:5679:6871.5353 > ff02::fb.5353: UDP, length 36 00:54:27.943973 IP 192.168.100.200.5353 > 224.0.0.251.5353: UDP, length 36 00:54:27.944048 IP6 fe80::7367:caec:5679:6871.5353 > ff02::fb.5353: UDP, length 36 00:54:27.944591 IP 192.168.100.200.5353 > 224.0.0.251.5353: UDP, length 36 00:54:27.944800 IP6 fe80::7367:caec:5679:6871.5353 > ff02::fb.5353: UDP, length 36 00:54:27.945330 IP 192.168.100.200.5353 > 224.0.0.251.5353: UDP, length 36 00:54:27.945618 IP6 fe80::7367:caec:5679:6871.5353 > ff02::fb.5353: UDP, length 36 00:54:27.946011 IP6 fe80::7367:caec:5679:6871.57683 > ff02::1:3.5355: UDP, length 30 00:54:27.946488 IP 192.168.100.200.57683 > 224.0.0.252.5355: UDP, length 30 00:54:27.946890 IP6 fe80::7367:caec:5679:6871.55593 > ff02::1:3.5355: UDP, length 30 00:54:27.947475 IP 192.168.100.200.55593 > 224.0.0.252.5355: UDP, length 30 00:54:28.352433 IP6 fe80::7367:caec:5679:6871.57683 > ff02::1:3.5355: UDP, length 30 00:54:28.354092 IP 192.168.100.200.57683 > 224.0.0.252.5355: UDP, length 30 00:54:28.354704 IP6 fe80::7367:caec:5679:6871.55593 > ff02::1:3.5355: UDP, length 30 00:54:28.355150 IP 192.168.100.200.55593 > 224.0.0.252.5355: UDP, length 30 00:54:28.355441 IP 192.168.1.52.137 > 192.168.1.255.137: UDP, length 50 **00:54:28.470082 PPPoE PADO [Host-Uniq 0x4071780400F8FFFF] [Service-Name] [AC-Name "RMS-BNG-NE40X8A-04"]** 00:54:28.935532 IP 192.168.100.200.5353 > 224.0.0.251.5353: UDP, length 36 00:54:28.935968 IP6 fe80::7367:caec:5679:6871.5353 > ff02::fb.5353: UDP, length 36 00:54:28.936780 IP 192.168.100.200.5353 > 224.0.0.251.5353: UDP, length 36 00:54:28.937048 IP6 fe80::7367:caec:5679:6871.5353 > ff02::fb.5353: UDP, length 36 00:54:28.949563 IP 192.168.100.200.5353 > 224.0.0.251.5353: UDP, length 36 00:54:28.950227 IP6 fe80::7367:caec:5679:6871.5353 > ff02::fb.5353: UDP, length 36 00:54:28.960429 IP 192.168.100.200.5353 > 224.0.0.251.5353: UDP, length 36 00:54:28.969292 IP6 fe80::7367:caec:5679:6871.5353 > ff02::fb.5353: UDP, length 36 00:54:29.116704 IP 192.168.1.52.137 > 192.168.1.255.137: UDP, length 50 00:54:29.129630 ARP, Request who-has 192.168.1.100 (00:1b:21:48:da:98) tell 192.168.1.1, length 46 00:54:29.277519 IP 192.168.100.200.60157 > 255.255.255.255.161: UDP, length 124 00:54:29.278496 IP 192.168.100.200.60158 > 255.255.255.255.161: UDP, length 124 00:54:29.882069 IP 192.168.1.52.137 > 192.168.1.255.137: UDP, length 50 00:54:30.567661 IP6 fe80::b2be:76ff:fee1:d6fb > ff02::1: ICMP6, router advertisement, length 32 00:54:30.698656 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 **00:54:31.627479 PPPoE PADI [Host-Uniq 0x00636E0100F8FFFF] [Service-Name]** 00:54:31.926491 ARP, Request who-has 192.168.100.1 tell 192.168.100.200, length 46 00:54:32.795708 ARP, Request who-has 192.168.100.1 tell 192.168.100.200, length 46 00:54:33.662210 PPPoE PADI [Host-Uniq 0x00636E0100F8FFFF] [Service-Name] 00:54:33.704738 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 00:54:33.799981 ARP, Request who-has 192.168.100.1 tell 192.168.100.200, length 46 00:54:34.461711 IP6 fe80::b2be:76ff:fee1:d6fb > ff02::1: ICMP6, router advertisement, length 32 00:54:35.071239 ARP, Request who-has 192.168.1.1 tell 192.168.1.52, length 46 00:54:36.710565 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 00:54:37.581609 IP6 fe80::b2be:76ff:fee1:d6fb > ff02::1: ICMP6, router advertisement, length 32 00:54:37.688202 PPPoE PADI [Host-Uniq 0x00636E0100F8FFFF] [Service-Name] 00:54:39.716545 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 **00:54:41.552605 PPPoE PADO [Host-Uniq 0x00636E0100F8FFFF] [Service-Name] [AC-Name "RMS-BNG-NE40X8A-04"]** **00:54:42.666463 PPPoE PADI [Host-Uniq 0xC0616E0100F8FFFF] [Service-Name]** 00:54:42.722492 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 00:54:44.680206 PPPoE PADI [Host-Uniq 0xC0616E0100F8FFFF] [Service-Name] 00:54:48.680190 PPPoE PADI [Host-Uniq 0xC0616E0100F8FFFF] [Service-Name] 00:54:48.734461 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 00:54:51.740395 IP 192.168.1.1.37316 > 255.255.255.255.7437: UDP, length 173 **00:54:52.592469 PPPoE PADO [Host-Uniq 0xC0616E0100F8FFFF] [Service-Name] [AC-Name "RMS-BNG-NE40X8A-04"]** 00:54:52.859371 IP6 fe80::b2be:76ff:fee1:d6fb > ff02::1: ICMP6, router advertisement, length 32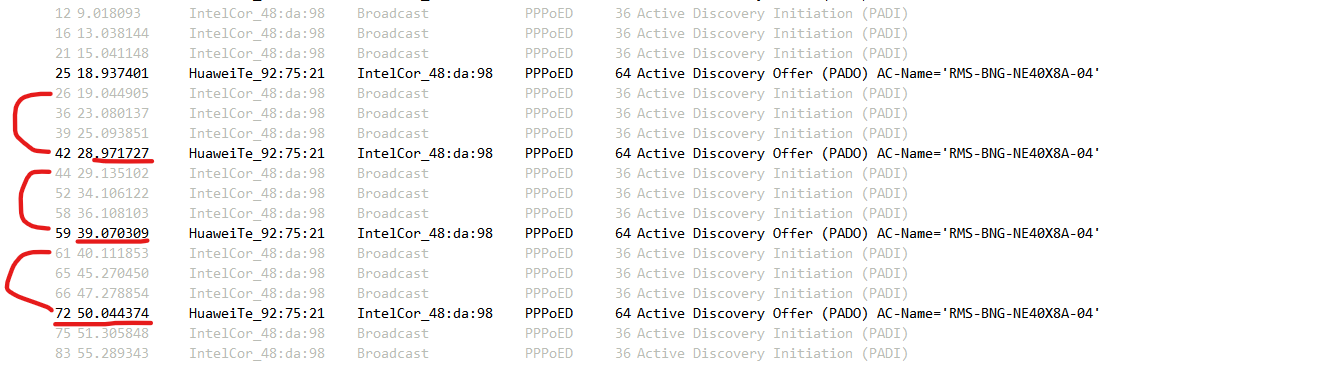
-
The debug line would be in the mpd_wan.conf file.
Ok, so we can see the unique id of the request is sent 3 times then the server replies. But it could be replying to any of those three requests.
The fact that the reply triggers pfSense to start with a new request though seems indicate it's refusing the offer.
-
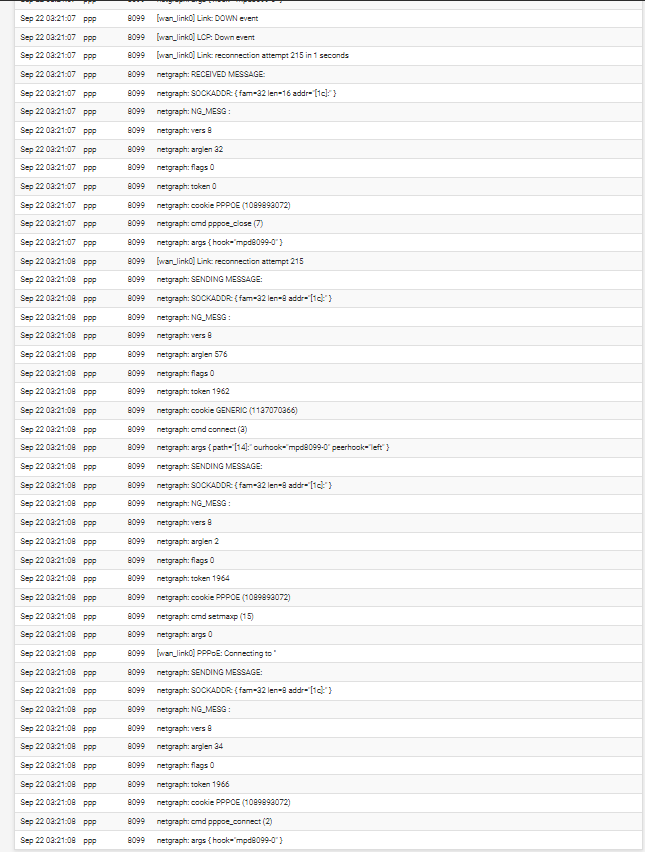
@stephenw10 what would make it refuse the offer? I set debug 10 and did another pcap
packetcapture-igb0-20230922022327.pcap
is there a way to stop it from rejecting the PADO?
-
I'm still not 100% sure it is actually seeing the replies. It could be that it only ever tries the same ID 3 times whether or not it sees a reply for example.
With the debugging logs do you see 3 sent messages for each 1 received message?
This really seems like the solution is going to be something simple like it needs an identifier set. But I assume you didn't set anything like that in the Windows client?
-
@stephenw10 how can I export a better debug log, I've set it to 10, should I set it to more for example? And is there a way to download/export the system log from the GUI so it could be more helpful to us?
Is there some way to implement the identifier set? I did not set one in windows, only username and pass, nothing else at all.
-
We're off the map at this point.

I've never had to set debug logging to get PPPoE connected so I can't tell you. Try it and see. You can download the full system log file from /var/log/system.logYou can set a service name in the PPPoE client. It's almost never required though.
-
@stephenw10 yea I asked the ISP and no service name required. I just don't understand why pfsense wouldn't just wait a couple of seconds, the router and pc do wait. Like it's literally a couple of seconds and we cant override it and it's rendering the whole this useless it's very frustrating.