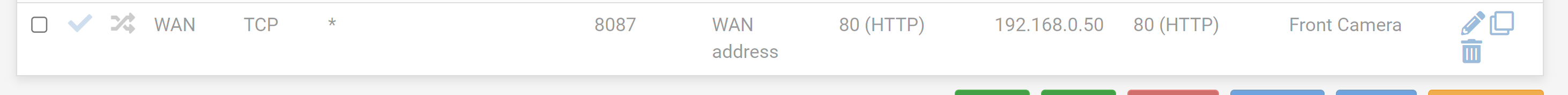
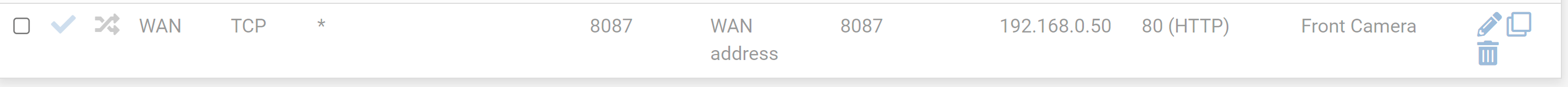
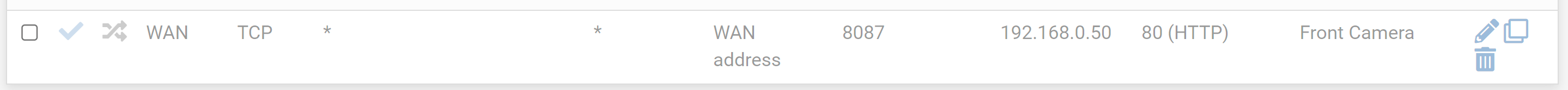
Port Forwarding From Port to Different Port, i.e. port 8087 to port 80
-
I am new to pfSense and I am used to the simple adding port forwarding rules from ANY, Port 8087 to Internal IP, Port 80.
It might be the semantics, or verbiage or I am just not grasping all port forwarding to an internal LAN address, like 192.168.0.50 which uses as a destination WAN which seems to be the default for all port forwards. The docs rarely show anything different and trying to find examples always seem to show a WAN destination, and ultimately the redirect destination and port. This WAN destination also asks for a port and I do not know if it is the port coming in, in this case 8087 or the destination port of my camera which is port 80.
I have attached three images and regardless of verbiage or whatever I don't understand, if I knew which was correct, I would be happy to know which port forward rule is correct.
I am on the latest version, 27.X and this firewall is not online yet. I am trying to get everything set up in advance to change out my old ClearOS box with something well supported.
To be clear, I come in on Port 8087 and the camera is on port 80. I have multiple cameras and each comes in on a different port to port 80 which is set for every camera.Option 1
Option 2
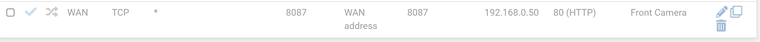
Option 3

Thanks for any help!
John
-
@johnjces
The third one might be what you need.
However, the camera might block access from outside of it's subnet by default.You can run a packet capture on the interface, which the cam is connected to, to see if the packets are forwarded properly and if the device is responding.
-
@johnjces 1 and 2 would be wrong.. You almost never want or need to set the source port of the traffic. Since this would almost always be something random that the client chooses above 1024. There are some rare exceptions.
I change the port for my plex to its 32400 port, but I limit what IPs using a pfblocker alias to limit to specific IPs based on geoip info, and some lists of known plex IPs and monitoring IPs, etc
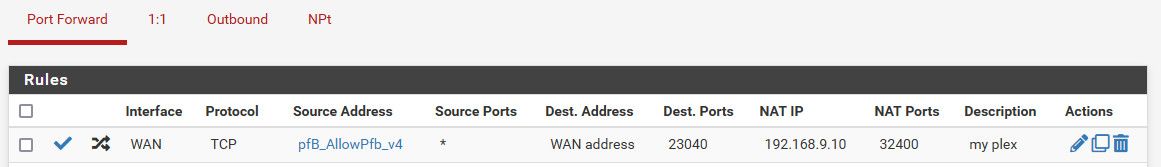
Honestly - I would not suggest you open up cameras to the public internet. It would be much better solution to vpn into your network when you want to view your cameras remotely.
As @viragomann mentions - its possible your cameras do not allow access from a remote network, many of them don't have a gateway for example. So you have to be on the local network to view them, or you have to source nat the traffic so looks like its coming from pfsense IP on the camera network.
Also many cameras don't even require a port forward - I have couple I have played with, currently have a wyze online - and no port forward is required to view its feed. Since they phone home to the mothership if you will, and the connection is made that way. Just open the app on the phone and there you go, etc.
More advice I would suggest, is I would put such devices on their own separate vlan and isolate them from the rest of your network - cameras are notoriously lacking in security.
-
Thank-you both for the replies! I might be on the right track now.
I like the idea of limiting IPs by pfblocker. Someday I will understand all of that!
All of my outdoor cameras have been used successfully for years in this manner. They have full IP settings and gateways. I would not put an indoor camera 'out there' for someone to try and hack and get an inside view. All outside. I trust this arrangement more than cameras that use cloud access, i.e. 'phone home'. Anyway, my cameras have decent usernames and strong passwords but still they are generally easy to hack into. I understand that and accept the risk
I do specifically, through my viewing software, set a port and in this instance it is 8087. I do not believe that my client viewing software randomizes ports when they are specifically set and expected.
If the above is the case, my client is set to specifically use port 8087, would Option 2 in the images be correct?
And how is it that you still set 'Dest Address' as 'Wan address', and 'Dest ports' as the incoming port, 8087, (that middle part), when the destination is inside my LAN and living on port 80. I am explicitly setting a different port in 8087 to the standard HTTP port 80 of the camera(s).
Thank-you VERY much!!
John
-
@johnjces said in Port Forwarding From Port to Different Port, i.e. port 8087 to port 80:
client viewing software randomizes ports when they are specifically set and expected.
yeah it does - not taking destination port, talking source port..
Users new to networking, never seem to understand a source port.. This is the port that the answer would be sent too..
If I want to talk to port X from my device... The connection to 1.2.3.4:x would be made from my IP, lets say 192.168.1.100, this would also have a port, the source port. This is "almost" ALWAYS some random port above 1024..
Look at your pc and look at the connections.
for example here are some of mine..
TCP 192.168.9.100:5665 52.159.127.243:443 ESTABLISHED TCP 192.168.9.100:6353 192.168.9.10:445 ESTABLISHED TCP 192.168.9.100:22738 192.168.9.10:22 ESTABLISHED TCP 192.168.9.100:24545 192.168.9.10:32400 ESTABLISHED TCP 192.168.9.100:24549 172.104.211.98:443 ESTABLISHED TCP 192.168.9.100:24604 52.204.182.160:443 ESTABLISHED TCP 192.168.9.100:24658 34.117.65.55:443 ESTABLISHED TCP 192.168.9.100:24739 192.168.9.253:22 ESTABLISHED TCP 192.168.9.100:24777 208.123.73.83:443 ESTABLISHED TCP 192.168.9.100:24778 89.149.219.103:443 ESTABLISHEDnotice the port used by 192.168.9.100 which is my machine, and the ports its talking to on the other IPs.. Those are the destination ports..
Then the device your talking to sends its answer, that answer will have a destination port of the source port you used to talk to your destination.. This is going to be something above 1024, and the client chooses this.. When it makes the connection attempt to your destination. You don't really have a say to what this port is going to be, its "random" if you will..
-
@johnjces said in Port Forwarding From Port to Different Port, i.e. port 8087 to port 80:
I do specifically, through my viewing software, set a port and in this instance it is 8087. I do not believe that my client viewing software randomizes ports when they are specifically set and expected.
It will random source port though.
Each IP packet has a source and destination, both have an address and a port.
And how is it that you still set 'Dest Address' as 'Wan address', and 'Dest ports' as the incoming port, 8087,
The client sends its packets to the destination address and port (e.g. WAN addresss, 8087). You can forward it to your LAN target devices IP and port 80.
-
Lightbulb came on!!!
Ya know, I've been playing with this stuff for many many years and wouldn't say I am a newbie, (new to pfsense), but I sure misunderstood the flow back and forth for like... forever!

Thank-you!
John
-
@johnjces glad to hear - now do you understand why you wouldn't set a source port in your firewalls? You would never really know what port the client device wanting to talk to your service on port X would use.. Now there are some rare sorts of applications or scenarios where the source port would be something specific.. dns zone transfers come to mind where its ports 53 to port 53..
But when creating a port forward through your firewall, you would almost never set this source port.. This is a common misconfiguration seen when users are having issues with port forwarding.
-
It does become clear! But when you really think about it, it is a bit odd. My remote viewing software comes into the firewall on 8087 forwarded to port 80 to IP 192.168.0.50 Replies going back from the camera can come back on any random port to the remote client software. The verbiage in the pfsense setup like destination (WAN addess) and port 8087 is a bit confusing to a newbie to pfsense.
But it does somehow make sense.
Thanks you again!
John
-
@johnjces the return traffic is allowed back through the firewall via the state..
Look at your state table - for example here is a connection into my plex server..
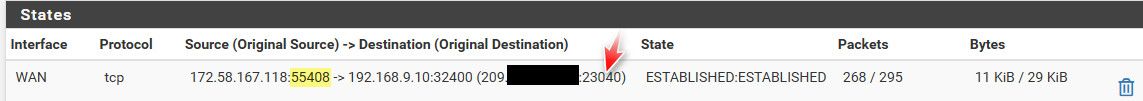
So the traffic hit my wan IP on port 23040, which was sent to my plex server on port 32400.. You can see the clients source port was 55408..
Now if you want something to think about more.. When you go to say netgate.com on port 443.. The source port is changed by pfsense when it does the nat..
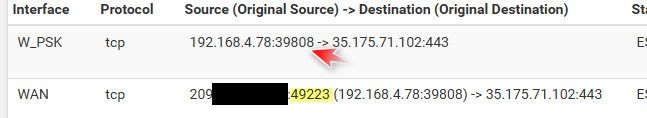
So my client wanting to talk to that 35.x address on port 443.. Used a source port of 39808, but when pfsense changed that to my public 209.x address it used a different source port 49223.. This is typical napt (network address port translation) which is how pretty much every router used that does your typical home natting for users getting a public IP from their ISP and then using rfc1918 space behind. That is how you can have multiple devices on your network all sharing 1 public IP.
The answer back from that 35.x address would come from source port 443, but its destination port would be 49223, which pfsense would then send on to that 4.78 address on port 39808
-
Yep!
I've got a headache!! But I am understanding a LOT more.
Again, thank-you!! You sir are awesome!
John