Traffic Graph and trunk links
-
Is it graphing the parent interface or a VLAN on it?
If it's the parent you might expect to see traffic on VLANs on it.
-
@stephenw10 Just a VLAN
So if you see the below screen shot, the interface which is a vlan on a trunk has over 10Mb of traffic but there is no talker that comes up that shows that.
But if i go on my Wireless IoT vlan, those spikes makse more sense and i see the top talker pulling down 10Mbp of traffic.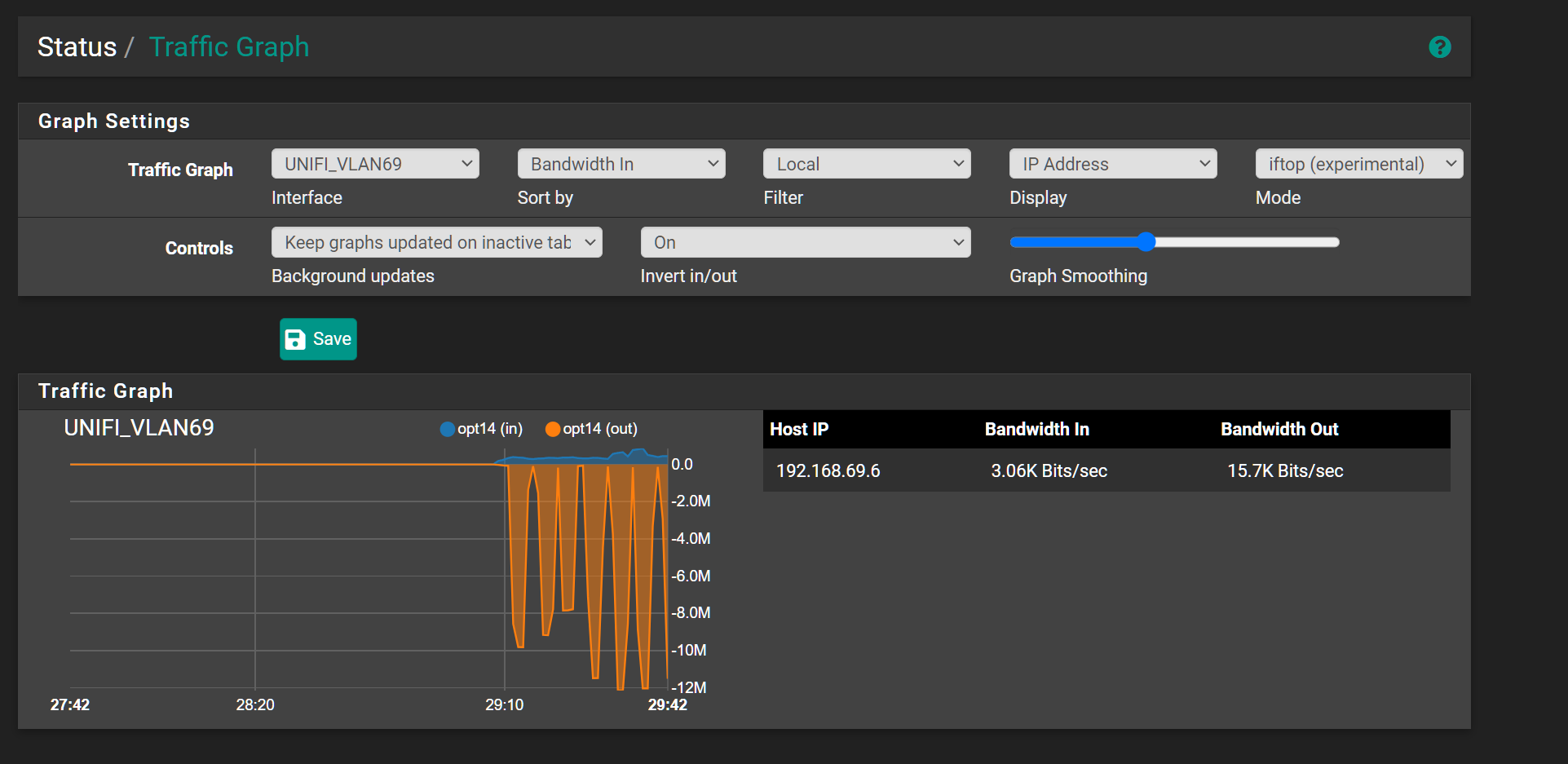
-
That's on the 6100? 7100? What is the parent interface for it? I assume in 23.05.1?
-
@stephenw10 This is on a 6100 on 23.05.1 Release. igc2 interface
-
This test box is running 23.09, so this might have been fixed already, but do you see that on the dash graphs too?
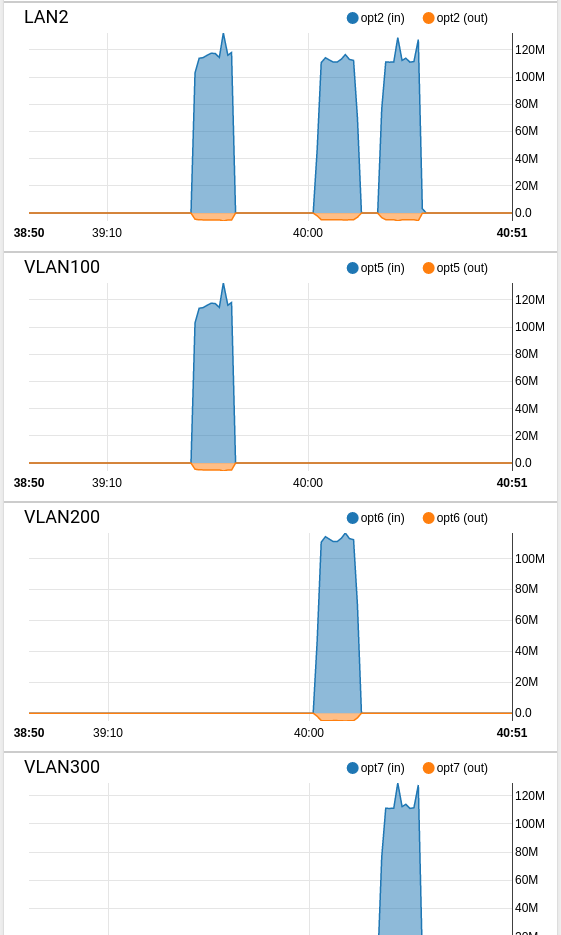
Those 3 VLANs are on LAN2 which I is what I expect.
-
@stephenw10 The dash graphs is how I originally spotted the issue.
I then went into Traffic Graph to identify in the UNIFI VLAN what is talking so much and either no IPs show up or if one does it’s below a meg of traffic as I would expect as it’s only APs and switches in that vlanI just took this off my dashboard now. How is the UNIFI vlan pulling down the same traffic level of Kidszone? Same trunk link but different vlan/subnets? Different firewall rulesets. So in theory its not possible to have the same flows.
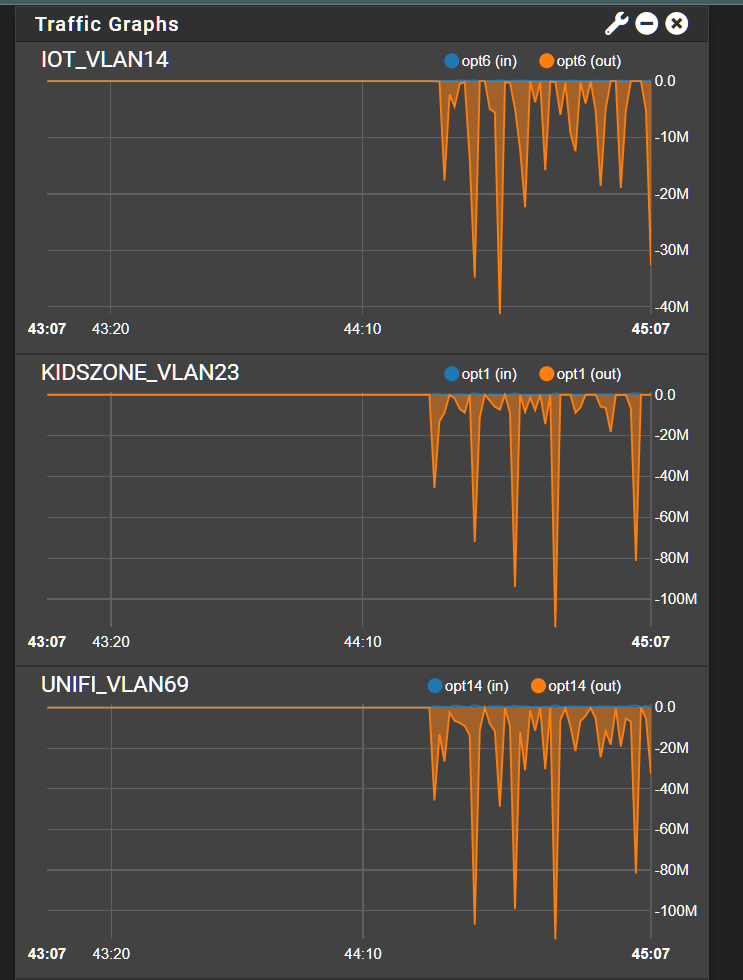
-
Hmm, can you test 23.09? I can't see a bug specifically for this....
If not I'll try to replicate in 23.05.1
-
@stephenw10 Can i use boot environments for this? I got a system that i can throw 23.09 on it but i want to know if its possible to switch back to 23.05.1 if need be and have everything be the way it was once i tested out this issue.
edit: unless there is a soon-to-be release in the next few days i can wait.

-
Yes you can create a 23.05.1 boot environment and then roll back to it from 23.09.
-
- During the update i get the error that it failed..
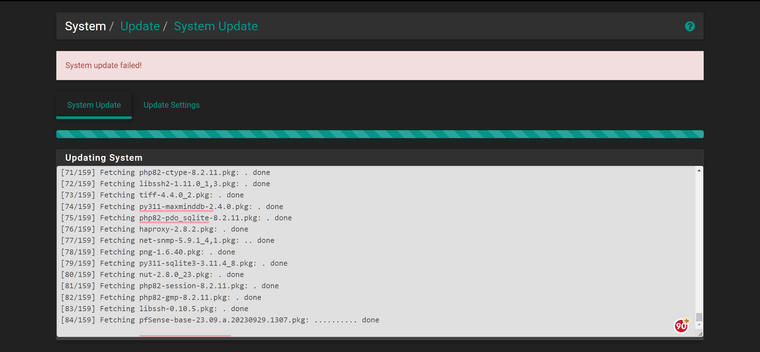
After a few minutes i get the email that the Boot UP is complete but the graphing is still broken.
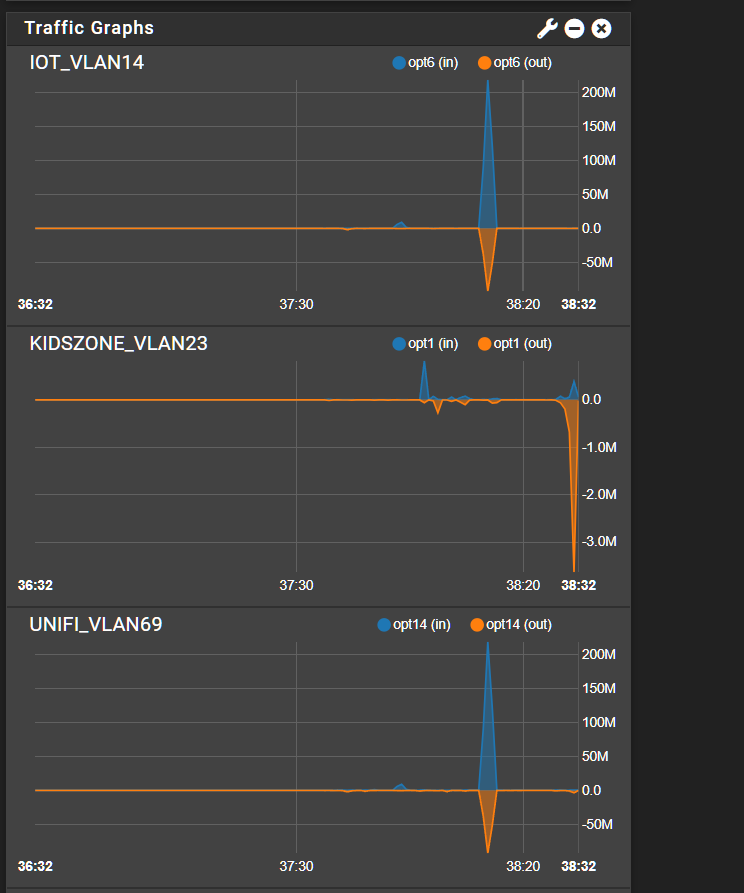
There is absolutely no way there is 200M of traffic on the Unifi VLAN. Impossible but it matches the spikes of a different VLAN (IoT). Somehow the graphing of the trunk is wrong.
I will be switching back to 23.05 now.
-
Hmm. Do you have the parent igc NIC assigned? Does that also show the same traffic?
-
@stephenw10
hmmm....
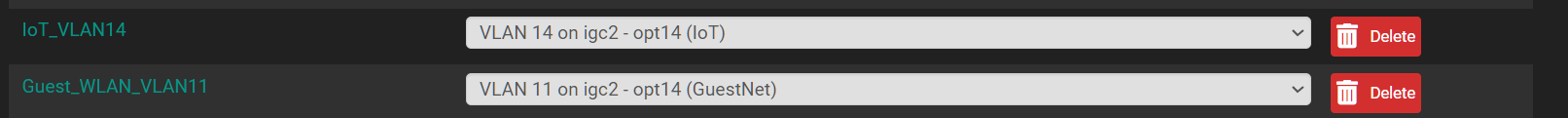
igc2 is assigned to the trunk - UNIFI vlan
Because Unifi needs to operate on the native vlan i assigned igc2 but it has no vlan assignments.
igc2.14 is the IoT vlanMaybe we're on to something here.......

-
Ah, yes, then that's expected. The parent NIC sees the traffic from all VLANs on it. That's exactly what I see above on the graphs here. And why that's the first thing I asked.

You should still be able to put client traffic on a VLAN in Unifi and just have the management traffic untagged. Or potentially untag it at a switch in between pfSense and the AP.
Steve
-
@stephenw10 You did ask i must have misunderstood, my bad on that. But good to know its expected behavior.
Thank you so much for the assist here. Appreciate it!!