Netgate 6100 PfSense to Edgerouter Lite - IPSEC site-to-site - works with PSK but NOT with PKI / X509
-
Hello,
I'm trying to configure my IPSEC site-to-site tunnel to use PKI certificates.
This same process works perfectly with PSK (pre-shared-key), but when I switch to PKI, I cannot get IKE started.The CA cert and router certs were created in OpenSSL and imported into both routers. (FYI, these same certs are working fine with the OpenVPN configuration, so I know there's no issue with the actual certs).
Netgate IKE config (screenshots):
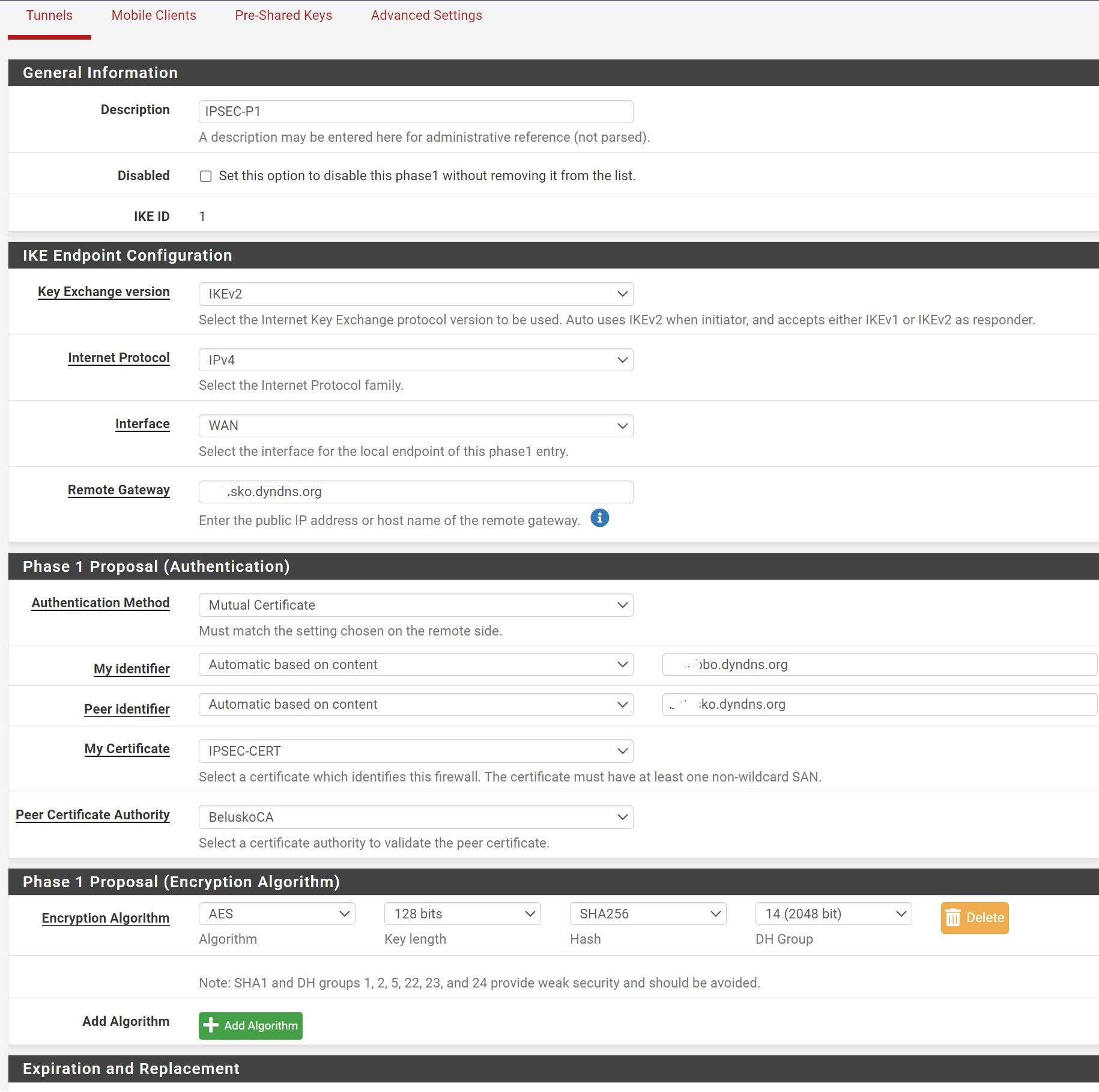
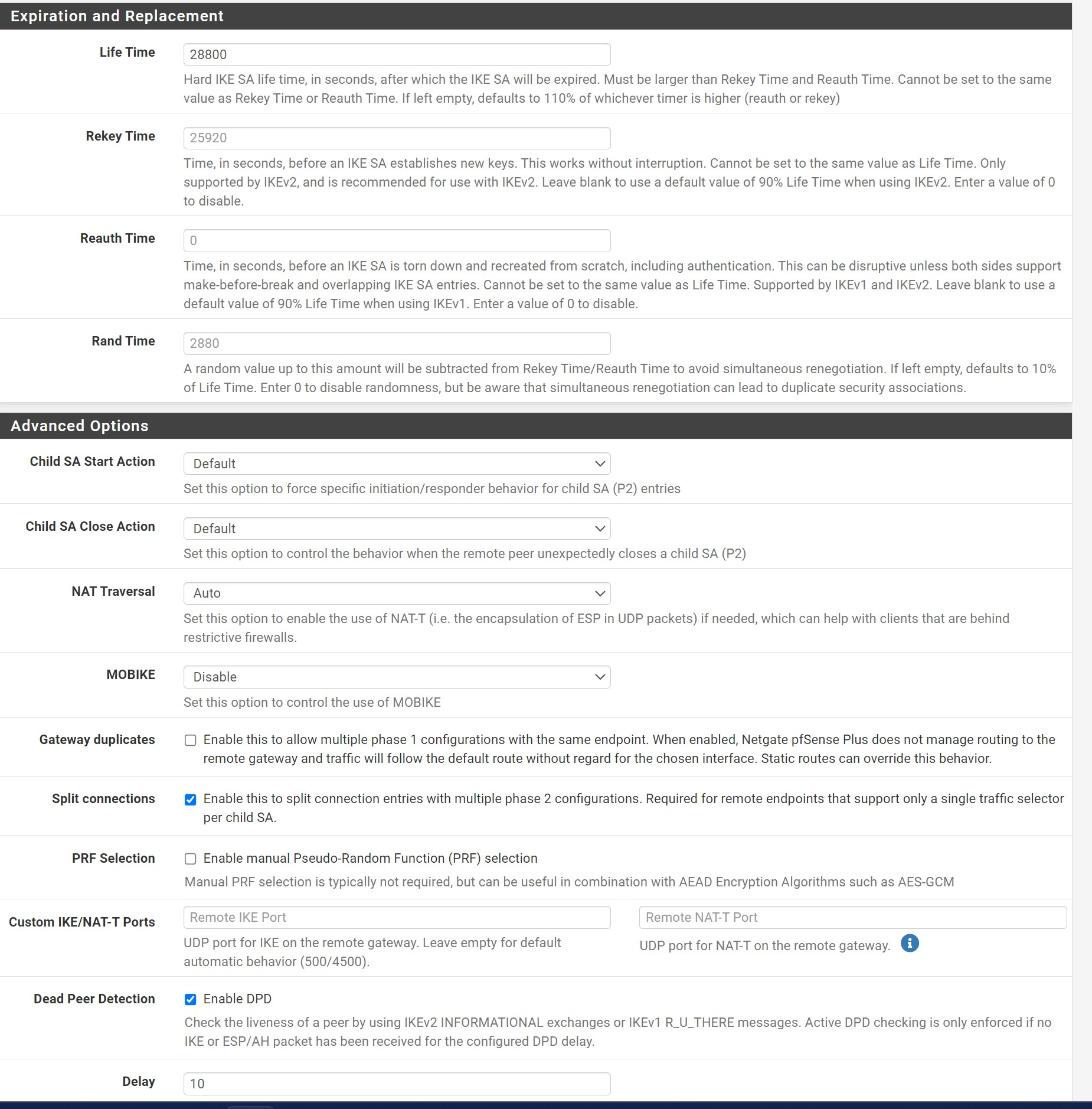
EDGEROUTER code:
Bob@XXXXXXRouter02# show vpn ipsec allow-access-to-local-interface disable auto-firewall-nat-exclude enable esp-group FOO0 { compression disable lifetime 3600 mode tunnel pfs enable proposal 1 { encryption aes128 hash sha256 } proposal 2 { encryption aes128 hash sha256 } } ike-group FOO0 { ikev2-reauth no key-exchange ikev2 lifetime 28800 proposal 1 { dh-group 14 encryption aes128 hash sha256 } proposal 2 { dh-group 14 encryption aes128 hash sha256 } } site-to-site { peer <LOCAL-ENDPOINT-FQDN> { authentication { mode x509 x509 { ca-cert-file /config/auth/cacert.pem cert-file /config/auth/openvpn.pem key { file /config/auth/openvpn.key } } } connection-type initiate description pfsense ike-group FOO0 ikev2-reauth inherit local-address <REMOTE-ENDPOINT-FQDN> tunnel 1 { allow-nat-networks disable allow-public-networks disable esp-group FOO0 local { prefix 192.168.2.0/24 } remote { prefix 192.168.9.0/24 } } tunnel 2 { allow-nat-networks disable allow-public-networks disable esp-group FOO0 local { prefix 192.168.20.0/24 } remote { prefix 192.168.9.0/24 } } tunnel 3 { allow-nat-networks disable allow-public-networks disable esp-group FOO0 local { prefix 192.168.2.0/24 } remote { prefix 192.168.50.0/24 } } tunnel 4 { allow-nat-networks disable allow-public-networks disable esp-group FOO0 local { prefix 192.168.20.0/24 } remote { prefix 192.168.50.0/24 } } tunnel 5 { allow-nat-networks disable allow-public-networks disable esp-group FOO0 local { prefix 192.168.2.0/24 } remote { prefix 10.255.12.0/24 } } tunnel 6 { allow-nat-networks disable allow-public-networks disable esp-group FOO0 local { prefix 192.168.20.0/24 } remote { prefix 10.255.12.0/24 } } tunnel 7 { allow-nat-networks disable allow-public-networks disable esp-group FOO0 local { prefix 192.168.98.0/24 } remote { prefix 192.168.9.0/24 } } tunnel 8 { allow-nat-networks disable allow-public-networks disable esp-group FOO0 local { prefix 192.168.98.0/24 } remote { prefix 192.168.50.0/24 } } } }PfSense LOGS:
Oct 2 12:54:38 charon 19906 14[IKE] <con1|3> IKE_SA con1[3] state change: CONNECTING => DESTROYING
Oct 2 12:54:38 charon 19906 14[CFG] <con1|3> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Oct 2 12:54:38 charon 19906 14[IKE] <con1|3> received NO_PROPOSAL_CHOSEN notify error
Oct 2 12:54:38 charon 19906 14[ENC] <con1|3> parsed IKE_SA_INIT response 0 [ N(NO_PROP) ]
Oct 2 12:54:38 charon 19906 14[NET] <con1|3> received packet: from <REMOTE-IP>4[500] to <LOCAL-ENDPOINT_IP>[500] (36 bytes)
Oct 2 12:54:38 charon 19906 12[NET] <con1|3> sending packet: from <LOCAL-ENDPOINT_IP>[500] to <REMOTE-IP>4[500] (508 bytes)
Oct 2 12:54:38 charon 19906 12[ENC] <con1|3> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Oct 2 12:54:38 charon 19906 12[CFG] <con1|3> sending supported signature hash algorithms: sha256 sha384 sha512 identity
Oct 2 12:54:38 charon 19906 12[CFG] <con1|3> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> IKE_SA con1[3] state change: CREATED => CONNECTING
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> initiating IKE_SA con1[3] to <REMOTE-IP>4
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating CHILD_CREATE task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating IKE_ESTABLISH task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating IKE_AUTH_LIFETIME task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating IKE_CONFIG task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating IKE_CERT_POST task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating IKE_AUTH task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating IKE_CERT_PRE task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating IKE_NATD task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating IKE_INIT task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating IKE_VENDOR task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> activating new tasks
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> queueing CHILD_CREATE task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> queueing IKE_ESTABLISH task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> queueing IKE_AUTH_LIFETIME task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> queueing IKE_CONFIG task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> queueing IKE_CERT_POST task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> queueing IKE_AUTH task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> queueing IKE_CERT_PRE task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> queueing IKE_NATD task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> queueing IKE_INIT task
Oct 2 12:54:38 charon 19906 12[IKE] <con1|3> queueing IKE_VENDOR task
Oct 2 12:54:38 charon 19906 12[KNL] creating acquire job for policy <LOCAL-ENDPOINT_IP>/32|/0 === <REMOTE-IP>4/32|/0 with reqid {1} -
If anyone comes across this, I was able to resolve it. The Edgerouter/EdgeOS software is picky about the names.
On the PfSense side, the "My Identifier" field needs to be set as "FQDN", and must contain the SAN in the certificate. If no SAN, most likely the CN (common name) will work, as it did in another test.
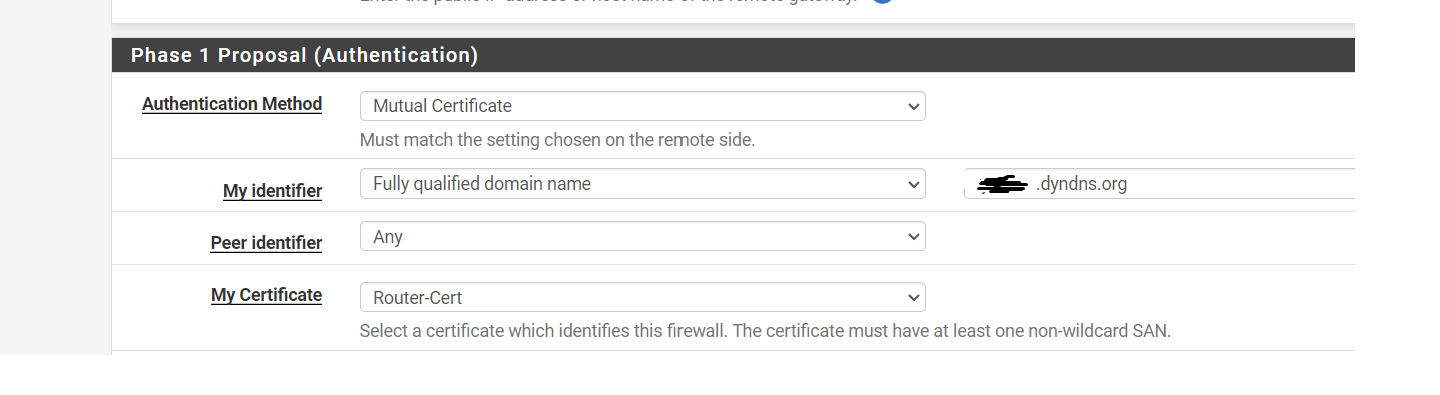
Note that in my attached picture, the SAN (subject alternative name) LOOKS like a FQDN, but it is actually just a name.
I hope this saves someone else 4 days of troubleshooting : )