forticlient - dtls
-
@NollipfSense dtls, tls using udp
I can get the logs from the client later today.
I have created a case with fortinet
10/7/2023 11:01:12 AM info sslvpn FortiSslvpn: 5384: PreferDtlsTunnel=1
10/7/2023 11:01:17 AM error sslvpn FortiSslvpn: 5384: error: SslBlockingRead() timeout. (tm=5000, n=-1)
10/7/2023 11:01:17 AM info sslvpn FortiSslvpn: 5384: PreferDtlsTunnel=1
10/7/2023 11:01:23 AM error sslvpn FortiSslvpn: 5384: error: SslBlockingRead() timeout. (tm=5000, n=-1)
10/7/2023 11:01:23 AM info sslvpn FortiSslvpn: 5384: PreferDtlsTunnel=1
10/7/2023 11:01:28 AM error sslvpn FortiSslvpn: 5384: error: SslBlockingRead() timeout. (tm=5000, n=-1)
10/7/2023 11:01:28 AM info sslvpn FortiSslvpn: 5384: PreferDtlsTunnel=1
10/7/2023 11:01:34 AM error sslvpn FortiSslvpn: 5384: error: SslBlockingRead() timeout. (tm=5000, n=-1)
10/7/2023 11:01:36 AM info sslvpn FortiSslvpn: 5384: PreferDtlsTunnel=1
10/7/2023 11:01:41 AM error sslvpn FortiSslvpn: 5384: error: SslBlockingRead() timeout. (tm=5000, n=-1) -
@eoyen Are you using dtls 1.2 or 1.3?
-
set ssl-max-proto-ver tls1-3
set ssl-min-proto-ver tls1-2set dtls-max-proto-ver dtls1-2
set dtls-min-proto-ver dtls1-0so 1.2
-
Hi, did you have any ideas to what the problem could be?
-
If this is just an SSL VPN using UDP encapsulation or similar pfSense should just pass it. It doesn't care what's in the packets.
Try running a pcap for that traffic on the LAN and then the WAN. Make sure you see two way traffic on both interfaces.
About the only thing I could imagine breaking it might be some MTU issue. But even then most connections would simply reduce their packet size to allow for it. UDP can fail in that situation where TCP would not.
Steve
-
@stephenw10 thank you
looks like it could be related to mtu, i have also tried to set mtu manully on the interfaces but that did not change anything
UDP, bad length 1774 > 1472
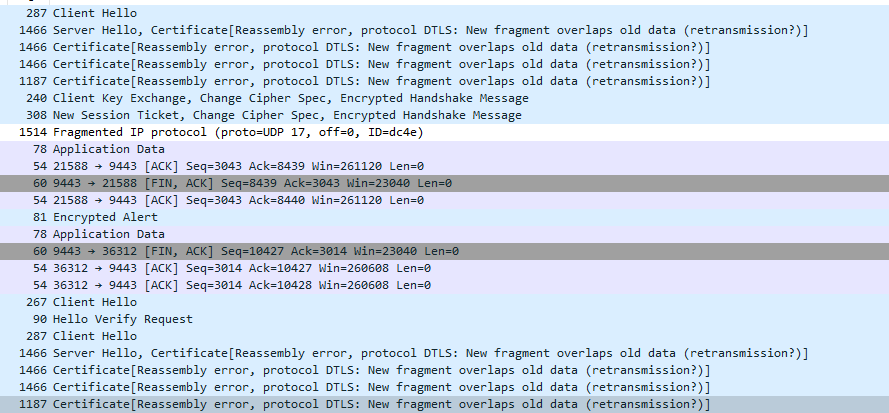
also found this as known issue for the latest version of forticlient
954004 DTLS tunnel cannot establish when handshake packet has a large MTU.
downgraded forticlient to version FortiClientVPNSetup_7.0.9.0493_x64
did not help. -
This post is deleted! -
What are the MTUs of the interfaces involved here? Where are you seeing that bad length error? Are you running the client on MacOS?
-
hi so after some more testing bypassing the pfsense box it turned out that the FortiClient version running on my laptop was older and handled automatically fallback to tcp better then the newer clients.
so using a new client on the laptop directly on the modem in bridge mode still doesn't work, so pfsense is not the problem.so the issue is either the modem provided by the isp or a problem somewhere in their infrastructure
UDP, bad length is displayed in the status window on pfsense when doing packet capture for the udp connection.
client on windows only.
mtu is not configured to any specific value. -
Well you might be able to force it by setting the interface MTU sufficiently small on the interface closest to the laptop. Or on the laptop itself.
There are a lot of reports of it being broken in the Fortinet client though.