VPN IPSec iOS 13 VPN on Demand from App
-
Hi,
i switched to a new SG-3100 and all Site 2 Site Connections are working fine.The last thing doesn´t work is the VPN on Demand IPSec Tunnel from my iPhone ( iOS13) pocketControl App.
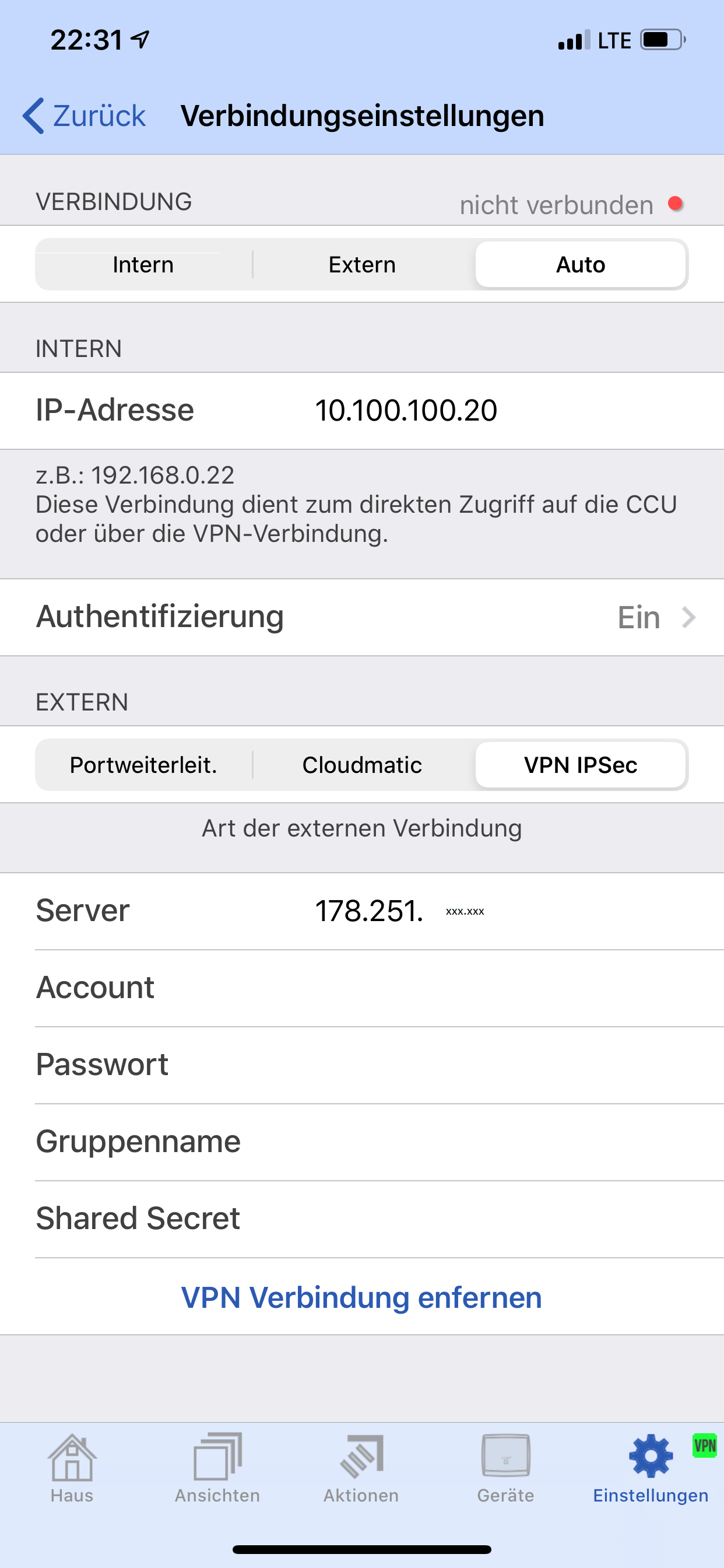
On the iPhone i can´t see what settings are necessary to connect to the pfsense.
The only thing i can enter in the App are:
Server
Account
Passwort
Groupname
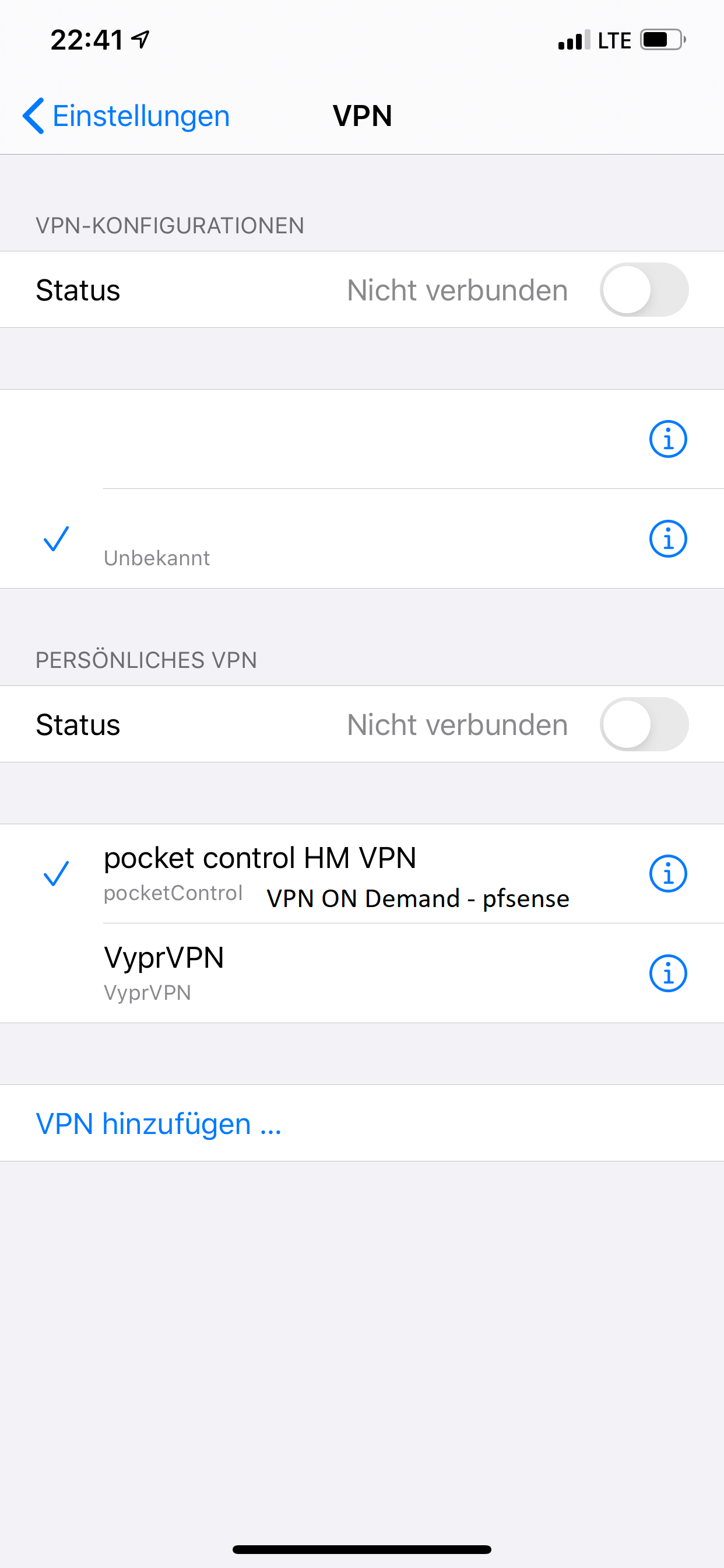
and Shared Secretthe App creates its own VPN Connection under Settings -> VPN -> Personal VPN.
Mar 1 22:53:11 charon 11[CFG] vici client 178 disconnected Mar 1 22:53:11 charon 10[CFG] vici client 178 requests: list-sas Mar 1 22:53:11 charon 10[CFG] vici client 178 registered for: list-sa Mar 1 22:53:11 charon 16[CFG] vici client 178 connected Mar 1 22:53:06 charon 07[IKE] <52> IKE_SA (unnamed)[52] state change: CONNECTING => DESTROYING Mar 1 22:53:06 charon 07[NET] <52> sending packet: from 178.251.xx.xx[500] to 92.248.xx.xxx[500] (56 bytes) Mar 1 22:53:06 charon 07[ENC] <52> generating INFORMATIONAL_V1 request 3435498570 [ N(NO_PROP) ] Mar 1 22:53:06 charon 07[IKE] <52> activating INFORMATIONAL task Mar 1 22:53:06 charon 07[IKE] <52> activating new tasks Mar 1 22:53:06 charon 07[IKE] <52> queueing INFORMATIONAL task Mar 1 22:53:06 charon 07[IKE] <52> no proposal found Mar 1 22:53:06 charon 07[CFG] <52> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Mar 1 22:53:06 charon 07[CFG] <52> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_128/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024 Mar 1 22:53:06 charon 07[CFG] <52> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:53:06 charon 07[CFG] <52> selecting proposal: Mar 1 22:53:06 charon 07[CFG] <52> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:53:06 charon 07[CFG] <52> selecting proposal: Mar 1 22:53:06 charon 07[CFG] <52> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:53:06 charon 07[CFG] <52> selecting proposal: Mar 1 22:53:06 charon 07[CFG] <52> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:53:06 charon 07[CFG] <52> selecting proposal: Mar 1 22:53:06 charon 07[CFG] <52> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:53:06 charon 07[CFG] <52> selecting proposal: Mar 1 22:53:06 charon 07[CFG] <52> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:53:06 charon 07[CFG] <52> selecting proposal: Mar 1 22:53:06 charon 07[CFG] <52> no acceptable INTEGRITY_ALGORITHM found Mar 1 22:53:06 charon 07[CFG] <52> selecting proposal: Mar 1 22:53:06 charon 07[CFG] <52> no acceptable INTEGRITY_ALGORITHM found Mar 1 22:53:06 charon 07[CFG] <52> selecting proposal: Mar 1 22:53:06 charon 07[IKE] <52> IKE_SA (unnamed)[52] state change: CREATED => CONNECTING Mar 1 22:53:06 charon 07[IKE] <52> 92.248.xx.xxx is initiating a Aggressive Mode IKE_SA Mar 1 22:53:06 charon 07[IKE] <52> received DPD vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received Cisco Unity vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received XAuth vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received draft-ietf-ipsec-nat-t-ike-02 vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received draft-ietf-ipsec-nat-t-ike-03 vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received draft-ietf-ipsec-nat-t-ike-04 vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received draft-ietf-ipsec-nat-t-ike-05 vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received draft-ietf-ipsec-nat-t-ike-06 vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received draft-ietf-ipsec-nat-t-ike-07 vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received draft-ietf-ipsec-nat-t-ike-08 vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received draft-ietf-ipsec-nat-t-ike vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received NAT-T (RFC 3947) vendor ID Mar 1 22:53:06 charon 07[IKE] <52> received FRAGMENTATION vendor ID Mar 1 22:53:06 charon 07[CFG] <52> found matching ike config: 178.251.xx.xx...%any with prio 1052 Mar 1 22:53:06 charon 07[CFG] <52> candidate: 178.251.xx.xx...%any, prio 1052 Mar 1 22:53:06 charon 07[CFG] <52> looking for an IKEv1 config for 178.251.xx.xx...92.248.xx.xxx Mar 1 22:53:06 charon 07[ENC] <52> parsed AGGRESSIVE request 0 [ SA KE No ID V V V V V V V V V V V V V V ] Mar 1 22:53:06 charon 07[NET] <52> received packet: from 92.248.xx.xxx[500] to 178.251.xx.xx[500] (766 bytes) Mar 1 22:53:06 charon 07[IKE] <51> IKE_SA (unnamed)[51] state change: CONNECTING => DESTROYING Mar 1 22:53:06 charon 07[NET] <51> sending packet: from 178.251.xx.xx[500] to 92.248.xx.xxx[500] (56 bytes) Mar 1 22:53:06 charon 07[ENC] <51> generating INFORMATIONAL_V1 request 2473055166 [ N(AUTH_FAILED) ] Mar 1 22:53:06 charon 07[IKE] <51> activating INFORMATIONAL task Mar 1 22:53:06 charon 07[IKE] <51> activating new tasks Mar 1 22:53:06 charon 07[IKE] <51> queueing INFORMATIONAL task Mar 1 22:53:06 charon 07[IKE] <51> found 1 matching config, but none allows XAuthInitPSK authentication using Aggressive Mode Mar 1 22:53:06 charon 07[CFG] <51> candidate "con-mobile", match: 1/1/1052 (me/other/ike) Mar 1 22:53:06 charon 07[CFG] <51> looking for XAuthInitPSK peer configs matching 178.251.xx.xx...92.248.xx.xxx[maximilian] Mar 1 22:53:06 charon 07[CFG] <51> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Mar 1 22:53:06 charon 07[CFG] <51> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Mar 1 22:53:06 charon 07[CFG] <51> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_256/HMAC_MD5_96/PRF_HMAC_MD5/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_2048 Mar 1 22:53:06 charon 07[CFG] <51> proposal matches Mar 1 22:53:06 charon 07[CFG] <51> selecting proposal: Mar 1 22:53:06 charon 07[IKE] <51> IKE_SA (unnamed)[51] state change: CREATED => CONNECTING Mar 1 22:53:06 charon 07[IKE] <51> 92.248.xx.xxx is initiating a Aggressive Mode IKE_SA Mar 1 22:53:06 charon 07[IKE] <51> received DPD vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received Cisco Unity vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received XAuth vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received draft-ietf-ipsec-nat-t-ike-02 vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received draft-ietf-ipsec-nat-t-ike-03 vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received draft-ietf-ipsec-nat-t-ike-04 vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received draft-ietf-ipsec-nat-t-ike-05 vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received draft-ietf-ipsec-nat-t-ike-06 vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received draft-ietf-ipsec-nat-t-ike-07 vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received draft-ietf-ipsec-nat-t-ike-08 vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received draft-ietf-ipsec-nat-t-ike vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received NAT-T (RFC 3947) vendor ID Mar 1 22:53:06 charon 07[IKE] <51> received FRAGMENTATION vendor ID Mar 1 22:53:06 charon 07[CFG] <51> found matching ike config: 178.251.xx.xx...%any with prio 1052 Mar 1 22:53:06 charon 07[CFG] <51> candidate: 178.251.xx.xx...%any, prio 1052 Mar 1 22:53:06 charon 07[CFG] <51> looking for an IKEv1 config for 178.251.xx.xx...92.248.xx.xxx Mar 1 22:53:06 charon 07[ENC] <51> parsed AGGRESSIVE request 0 [ SA KE No ID V V V V V V V V V V V V V V ] Mar 1 22:53:06 charon 07[NET] <51> received packet: from 92.248.xx.xxx[500] to 178.251.xx.xx[500] (766 bytes) Mar 1 22:53:05 charon 09[CFG] vici client 177 disconnected Mar 1 22:53:05 charon 13[CFG] vici client 177 requests: list-sas Mar 1 22:53:05 charon 13[CFG] vici client 177 registered for: list-sa Mar 1 22:53:05 charon 09[CFG] vici client 177 connected Mar 1 22:52:59 charon 08[CFG] vici client 176 disconnected Mar 1 22:52:59 charon 05[CFG] vici client 176 requests: list-sas Mar 1 22:52:59 charon 08[CFG] vici client 176 registered for: list-sa Mar 1 22:52:59 charon 05[CFG] vici client 176 connected Mar 1 22:52:56 charon 05[IKE] <50> IKE_SA (unnamed)[50] state change: CONNECTING => DESTROYING Mar 1 22:52:56 charon 05[NET] <50> sending packet: from 178.251.xx.xx[500] to 92.248.xx.xxx[500] (56 bytes) Mar 1 22:52:56 charon 05[ENC] <50> generating INFORMATIONAL_V1 request 1405839326 [ N(NO_PROP) ] Mar 1 22:52:56 charon 05[IKE] <50> activating INFORMATIONAL task Mar 1 22:52:56 charon 05[IKE] <50> activating new tasks Mar 1 22:52:56 charon 05[IKE] <50> queueing INFORMATIONAL task Mar 1 22:52:56 charon 05[IKE] <50> no proposal found Mar 1 22:52:56 charon 05[CFG] <50> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Mar 1 22:52:56 charon 05[CFG] <50> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_128/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024 Mar 1 22:52:56 charon 05[CFG] <50> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:52:56 charon 05[CFG] <50> selecting proposal: Mar 1 22:52:56 charon 05[CFG] <50> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:52:56 charon 05[CFG] <50> selecting proposal: Mar 1 22:52:56 charon 05[CFG] <50> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:52:56 charon 05[CFG] <50> selecting proposal: Mar 1 22:52:56 charon 05[CFG] <50> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:52:56 charon 05[CFG] <50> selecting proposal: Mar 1 22:52:56 charon 05[CFG] <50> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:52:56 charon 05[CFG] <50> selecting proposal: Mar 1 22:52:56 charon 05[CFG] <50> no acceptable ENCRYPTION_ALGORITHM found Mar 1 22:52:56 charon 05[CFG] <50> selecting proposal: Mar 1 22:52:56 charon 05[CFG] <50> no acceptable INTEGRITY_ALGORITHM found Mar 1 22:52:56 charon 05[CFG] <50> selecting proposal: Mar 1 22:52:56 charon 05[CFG] <50> no acceptable INTEGRITY_ALGORITHM found Mar 1 22:52:56 charon 05[CFG] <50> selecting proposal: Mar 1 22:52:56 charon 05[IKE] <50> IKE_SA (unnamed)[50] state change: CREATED => CONNECTING Mar 1 22:52:56 charon 05[IKE] <50> 92.248.xx.xxx is initiating a Aggressive Mode IKE_SA Mar 1 22:52:56 charon 05[IKE] <50> received DPD vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received Cisco Unity vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received XAuth vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received draft-ietf-ipsec-nat-t-ike-02 vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received draft-ietf-ipsec-nat-t-ike-03 vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received draft-ietf-ipsec-nat-t-ike-04 vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received draft-ietf-ipsec-nat-t-ike-05 vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received draft-ietf-ipsec-nat-t-ike-06 vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received draft-ietf-ipsec-nat-t-ike-07 vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received draft-ietf-ipsec-nat-t-ike-08 vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received draft-ietf-ipsec-nat-t-ike vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received NAT-T (RFC 3947) vendor ID Mar 1 22:52:56 charon 05[IKE] <50> received FRAGMENTATION vendor ID Mar 1 22:52:56 charon 05[CFG] <50> found matching ike config: 178.251.xx.xx...%any with prio 1052 Mar 1 22:52:56 charon 05[CFG] <50> candidate: 178.251.xx.xx...%any, prio 1052 Mar 1 22:52:56 charon 05[CFG] <50> looking for an IKEv1 config for 178.251.xx.xx...92.248.xx.xxx Mar 1 22:52:56 charon 05[ENC] <50> parsed AGGRESSIVE request 0 [ SA KE No ID V V V V V V V V V V V V V V ] Mar 1 22:52:56 charon 05[NET] <50> received packet: from 92.248.xx.xxx[500] to 178.251.xx.xx[500] (766 bytes) Mar 1 22:52:56 charon 05[IKE] <49> IKE_SA (unnamed)[49] state change: CONNECTING => DESTROYING Mar 1 22:52:56 charon 05[NET] <49> sending packet: from 178.251.xx.xx[500] to 92.248.xx.xxx[500] (56 bytes) Mar 1 22:52:56 charon 05[ENC] <49> generating INFORMATIONAL_V1 request 683185568 [ N(AUTH_FAILED) ] Mar 1 22:52:56 charon 05[IKE] <49> activating INFORMATIONAL task Mar 1 22:52:56 charon 05[IKE] <49> activating new tasks Mar 1 22:52:56 charon 05[IKE] <49> queueing INFORMATIONAL task Mar 1 22:52:56 charon 05[IKE] <49> found 1 matching config, but none allows XAuthInitPSK authentication using Aggressive Mode Mar 1 22:52:56 charon 05[CFG] <49> candidate "con-mobile", match: 1/1/1052 (me/other/ike) Mar 1 22:52:56 charon 05[CFG] <49> looking for XAuthInitPSK peer configs matching 178.251.xx.xx...92.248.xx.xxx[maximilian] Mar 1 22:52:56 charon 05[CFG] <49> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Mar 1 22:52:56 charon 05[CFG] <49> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Mar 1 22:52:56 charon 05[CFG] <49> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_256/HMAC_MD5_96/PRF_HMAC_MD5/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_2048 Mar 1 22:52:56 charon 05[CFG] <49> proposal matches Mar 1 22:52:56 charon 05[CFG] <49> selecting proposal: Mar 1 22:52:56 charon 05[IKE] <49> IKE_SA (unnamed)[49] state change: CREATED => CONNECTING Mar 1 22:52:56 charon 05[IKE] <49> 92.248.xx.xxx is initiating a Aggressive Mode IKE_SA Mar 1 22:52:56 charon 05[IKE] <49> received DPD vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received Cisco Unity vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received XAuth vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received draft-ietf-ipsec-nat-t-ike-02 vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received draft-ietf-ipsec-nat-t-ike-03 vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received draft-ietf-ipsec-nat-t-ike-04 vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received draft-ietf-ipsec-nat-t-ike-05 vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received draft-ietf-ipsec-nat-t-ike-06 vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received draft-ietf-ipsec-nat-t-ike-07 vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received draft-ietf-ipsec-nat-t-ike-08 vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received draft-ietf-ipsec-nat-t-ike vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received NAT-T (RFC 3947) vendor ID Mar 1 22:52:56 charon 05[IKE] <49> received FRAGMENTATION vendor ID Mar 1 22:52:56 charon 05[CFG] <49> found matching ike config: 178.251.xx.xx...%any with prio 1052 Mar 1 22:52:56 charon 05[CFG] <49> candidate: 178.251.xx.xx...%any, prio 1052 Mar 1 22:52:56 charon 05[CFG] <49> looking for an IKEv1 config for 178.251.xx.xx...92.248.xx.xxx Mar 1 22:52:56 charon 05[ENC] <49> parsed AGGRESSIVE request 0 [ SA KE No ID V V V V V V V V V V V V V V ] Mar 1 22:52:56 charon 05[NET] <49> received packet: from 92.248.xx.xxx[500] to 178.251.xx.xx[500] (766 bytes)Can you help me and tell me what i have to reconfig?
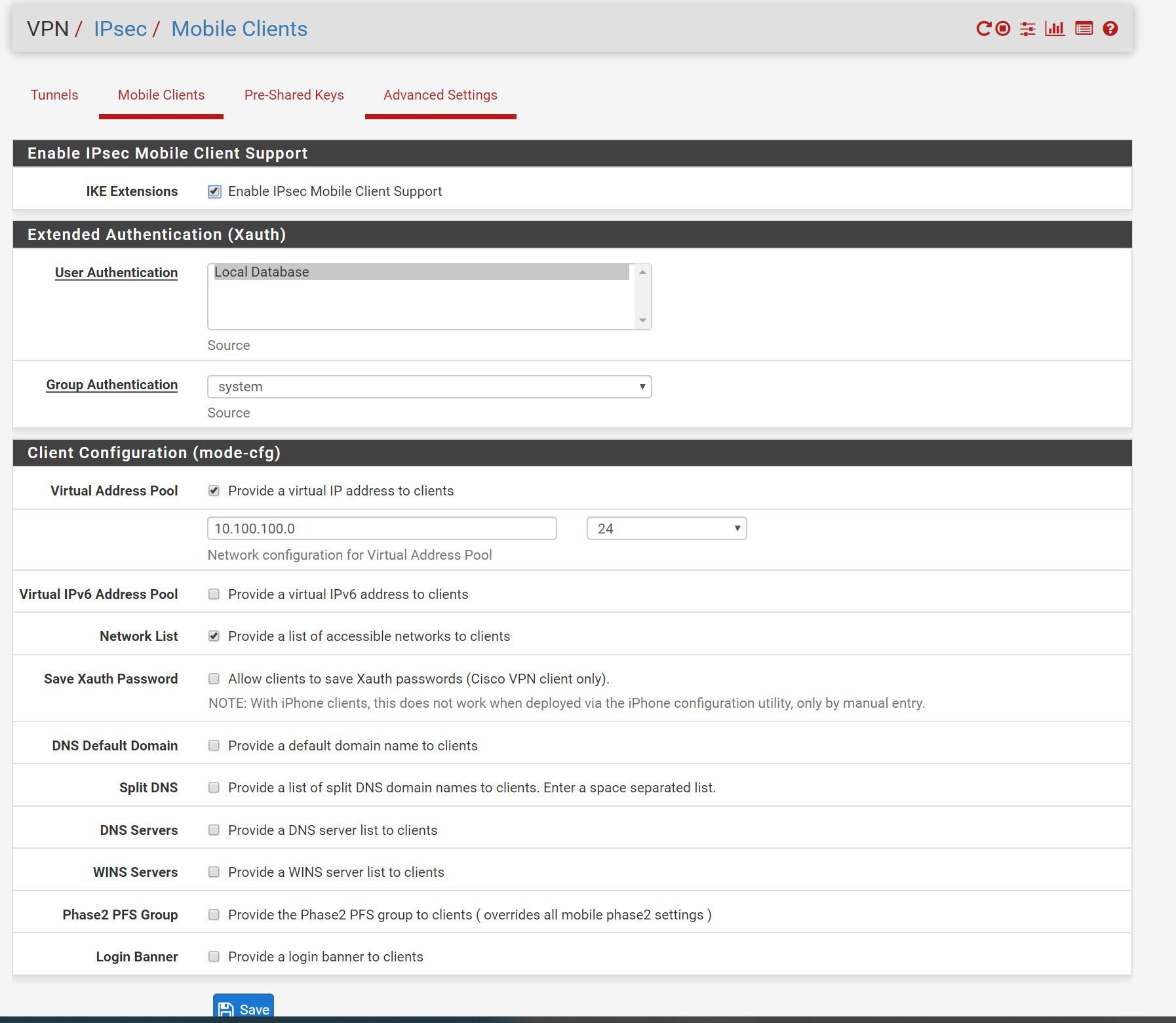
-
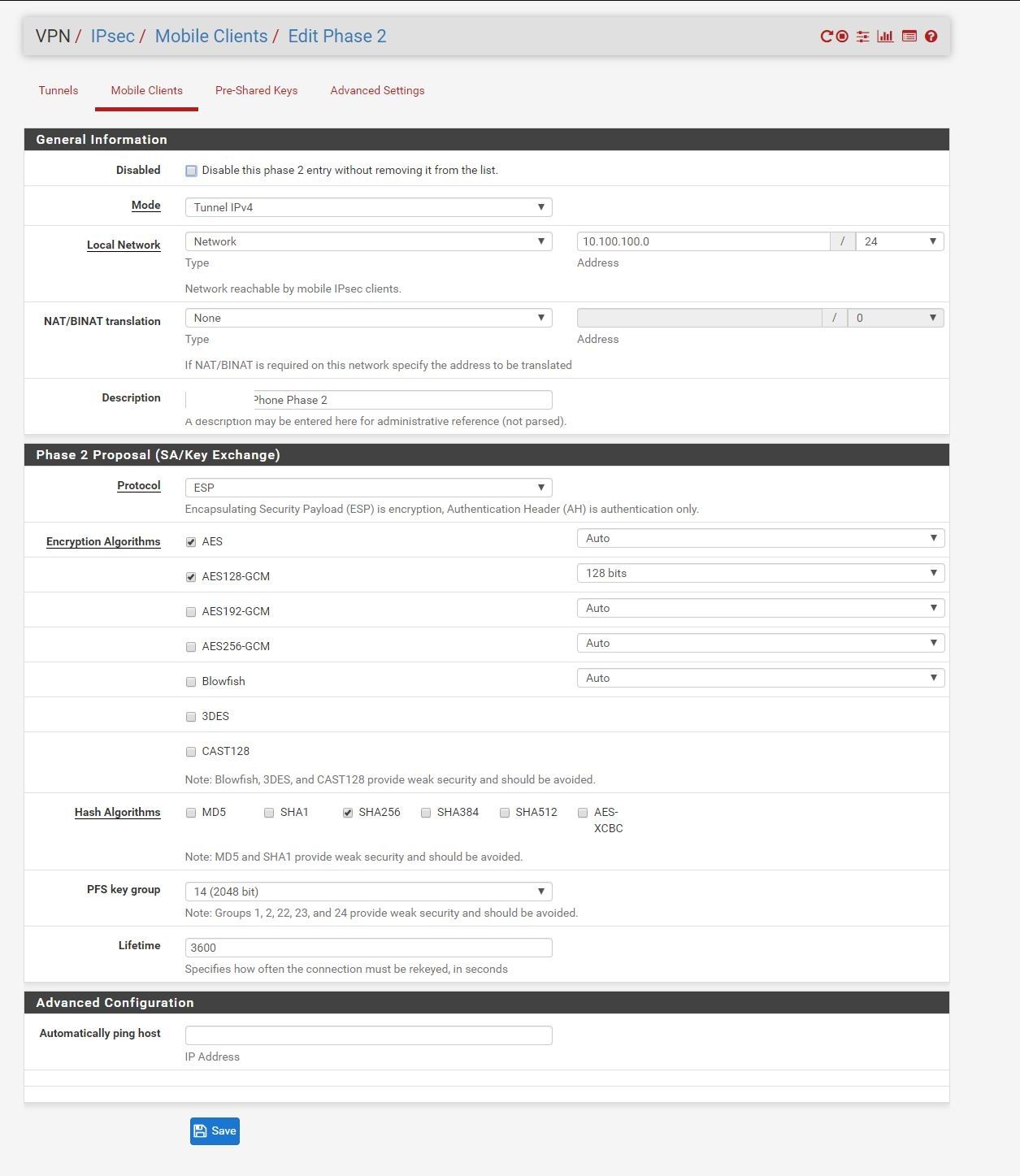
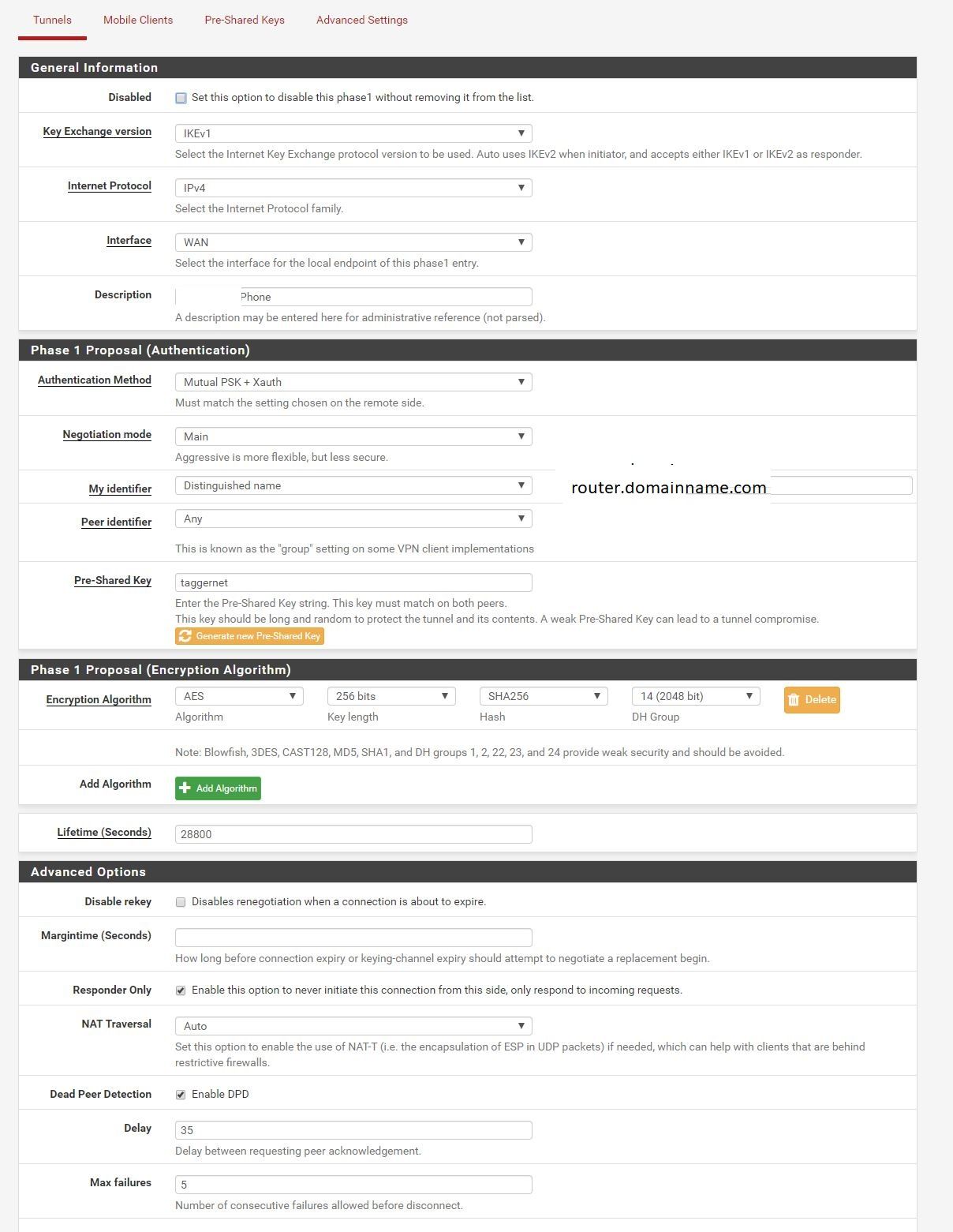
Tutorial: https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev1-xauth.html
but i had to change some options:
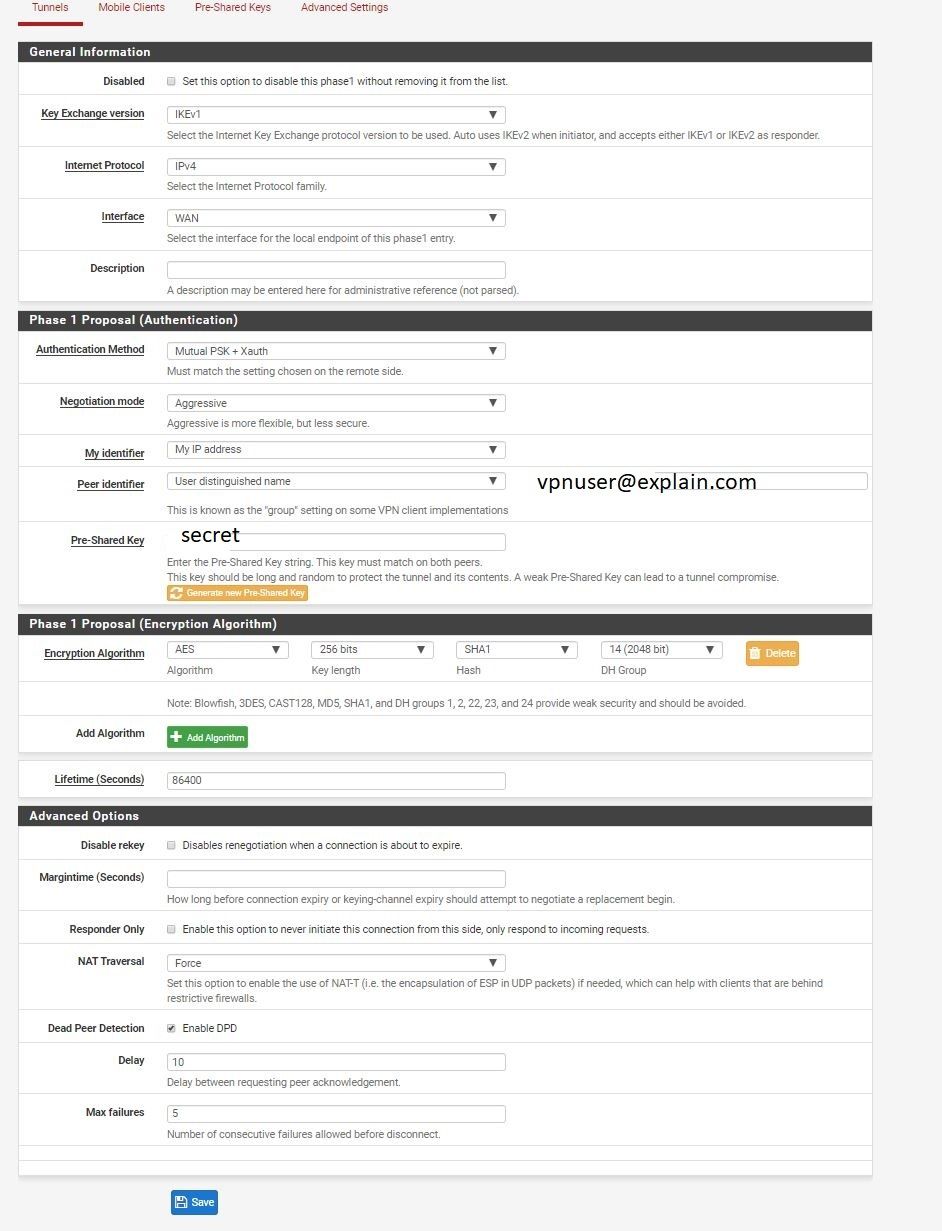
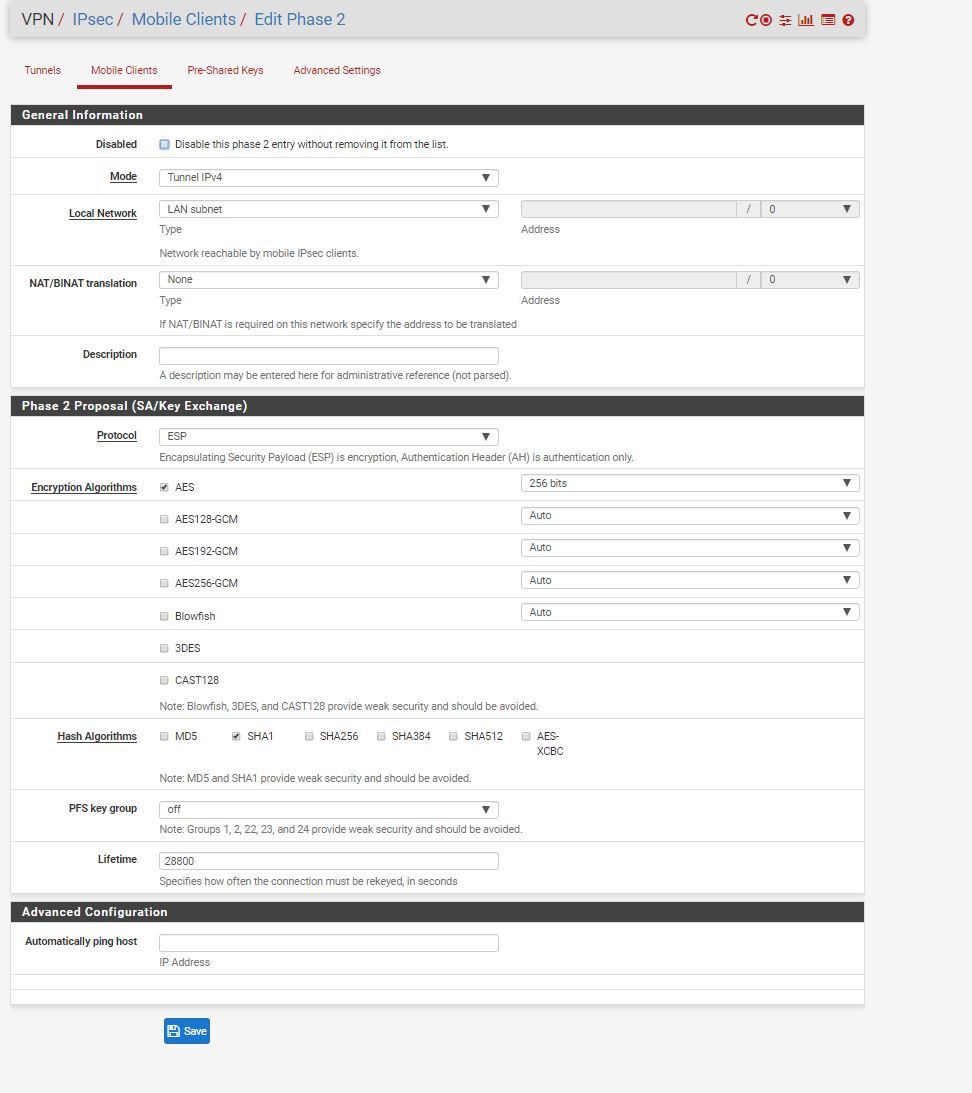
-
This post is deleted!
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.