Noob needs help with basic routing
-
Hello,
I run PfSense in Hyper-V. I have 3 networks defined in Hyper-V and have Pfsense with 3 NICs
- WAN 192.168.1.0/24 (pfsense assigned 192.168.1.28)
- Network1 10.1.0.0/24 (pfsense assigned 10.1.0.1)
- Network2 10.2.0.0/24 (pfsense assigned 10.2.0.1)
Pfsense is installed and running. I need Network1 and Network2 to be able to talk to each other and to Internet through pfsense.
What specifically do I need to add into PfSense to make it work? -
@artisticcheese nothing really other then create rules on interfaces that you create, only lan has default rules - if you create new interface you would need to add the rules you want on that interface.
Out of the box pfsense will have routes to any network its directly attached too. Unless you modified the outbound nat from auto, when you create a new interface with a network, it would auto be natted to your wan address.
There is nothing "special" you would have to do with pfsense other than create the network and assign the rules, enable dhcp if you want on that network, etc..
You didn't plug these 2 interfaces into the same dumb switch did you? That would be very problematic - especially with dhcp. You would need 2 different physical dumb switches, or a vlan capable switch you setup to isolate the 2 networks, etc.
-
@johnpoz This is Hyper-V virtual switch, so there is nothing physical about whole setup.
I have no issues routing from either Network1 or Network2 to internet via pfSense but Network1 can not talk to Network2. Firewall feature is disabled on pfsense, so it's not ACL either.
Here is what HyperV looks like
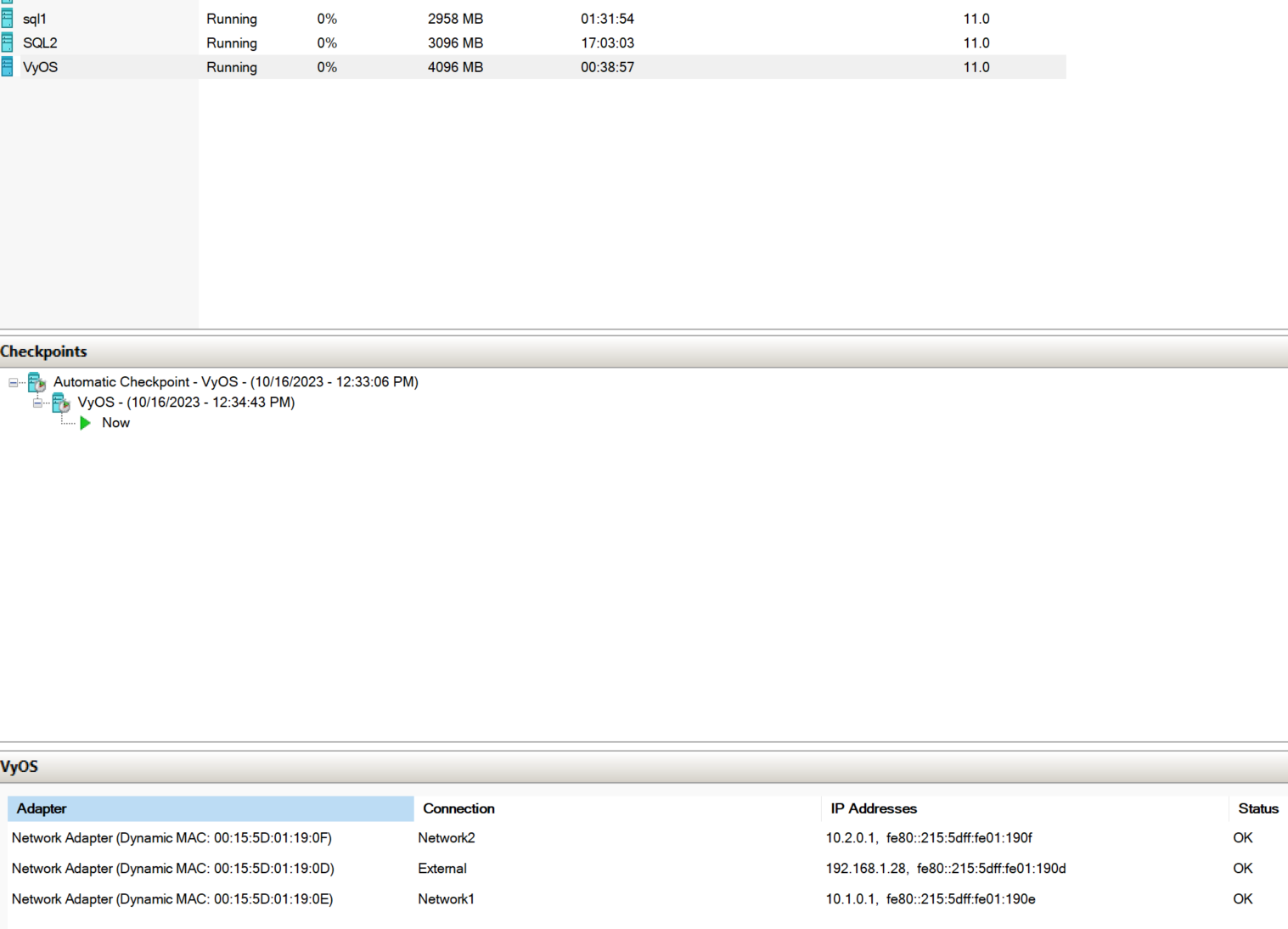
-
@artisticcheese what you do in in hyper-v has nothing to do with pfsense. Pfsense doesn't care if its connected to physical or virtual.. It just routing and firewalling traffic it sees on its interfaces - be they real or virtual.
What you posted doesn't even show pfsense running.. So not sure what that has to do with anything. Your problem is in your virtual setup most likely.. As stated pfsense will know how to route between any network its directly attached to.. Now if that traffic never gets to pfsense in the first place - then its kind of hard for pfsense to "route" it.
-
@johnpoz
Checking and unchecking this checkbox fixed all the issues. There were no other changes other then that. Thanks.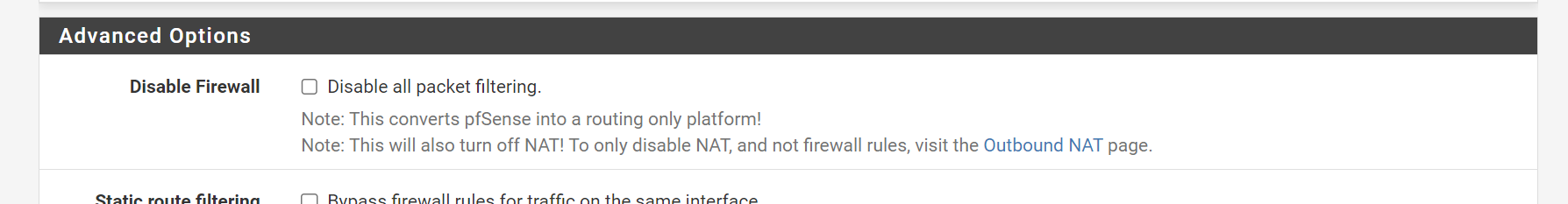
-
@artisticcheese have no idea what why you would of disabled packet filtering.. That for sure is not pfsense out of the box. Did you want want pfsense to only route? If so then it sure wouldn't of been natting any networks attached to its wan IP.
-
@johnpoz Would that apply/read in any saved-but-not-Applied rules? (which a restart should do as well)
-
@SteveITS yeah I would think restarting pf would force the loading of rules.. Which you could just also do with filter reload under status.
Or you would of thought of just reboot pfsense if something wasn't working, etc.
Not sure how they would of gotten that deep into the weeds of disable and then reenable pf?