Starlink DHCP Overriding Default Route
-
Issue
I am connecting a remote site with OpenVPN, using FRR OSPF for my routing. Everything works great until I use Starlink as an internet connection. A default static route is being added into the pfsense routing table to route everything to the Starlink router and I am not sure why. I have intentionally configured no default route on the pfsense as I am using OSPF to distribute, so this static route is causing issues. I think this might have something to do with this post, which I think suggests that it is receiving a static route through DHCP option 121, and putting it into the routing table. I have no static routes configured on the remote pfsense. I'm still getting the default router and the pfsense is creating the WAN gateway, so assuming that if it is an issue with option 121, I just want to tell pfsense to ignore it?
This is not something I have experienced when testing in my lab or with other internet connections. If I manually delete the route with the route delete shell command, it just comes back again.
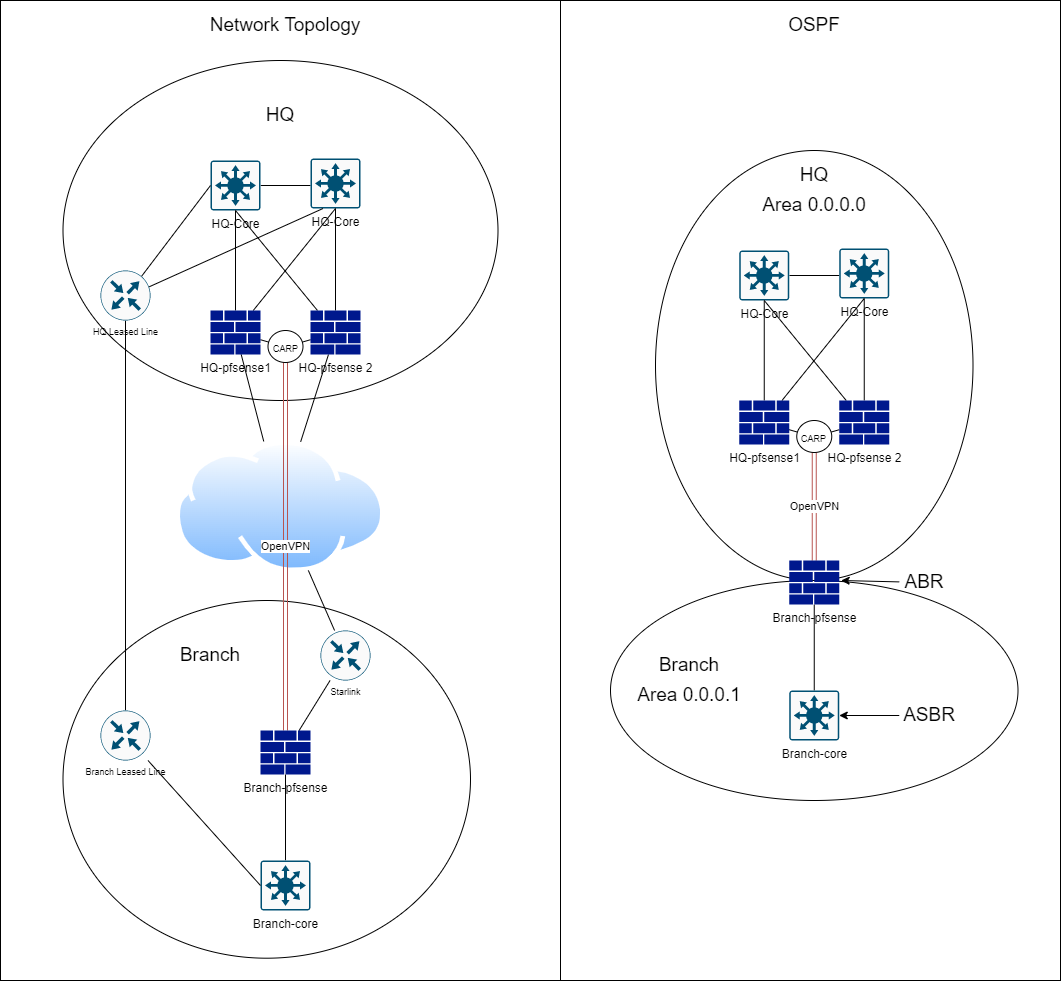
Network Overview
I'm not sure this is entirely needed, but I thought I would cover in case any questions arise. I'm trying to add a VPN connection to remote sites using OpenVPN. The remote sites have an existing leased line to my HQ, which has very limited bandwidth. The service provider is performing bandwidth management for us over this leased line, so traffic cannot be encapsulated in a tunnel or VPN.
My core aim is to be able to route traffic over the VPN tunnel when up, and then automatically route traffic over the leased line when the VPN is down. I have used FRR OSPF to share routing over the VPN, and from my ASBR at the remote site. My HQ-pfsense advertise themselves as a default gateway to the banch-pfsense. The remote site ASBR also advertises itself as a default route but with a higher cost, so the branch pfsense ignores it until it looses the neighborship over the VPN. Similarly the ASBR has a static route to the leased line with a higher cost than that being shared over the VPN, so again prefers the OSPF route shared over the VPN.
OpenVPN server instances are running on my HQ cluster, bound to the CARP VIP. FRR monitors the CARP status. I'm using net30 tunnels for each site running as its own OpenVPN server instance.
This all works nicely, routing fails over, no changes or tunnels required on the leased line.
-
Starlink uses CGNAT which causes all kinds of issues with remote connectivity.
I'm kind of in a similar boat trying to connect to a remote site with an IPSec connection, but it's virtually impossible, thanks to Starlink.
More or less tagging this to follow if there ever comes a solution.