Simple FW rule not being matched
-
I have a pfSense 23.05.1 VM with attached vSphere distributed port group interface set to "VLAN" mode with the appropriate VLAN ID.
In pfSense this is configured as a interface and the static IP is assigned to it. I created a simple rule on the interface allowing any IPv4 traffic from the "_net" to "_net":
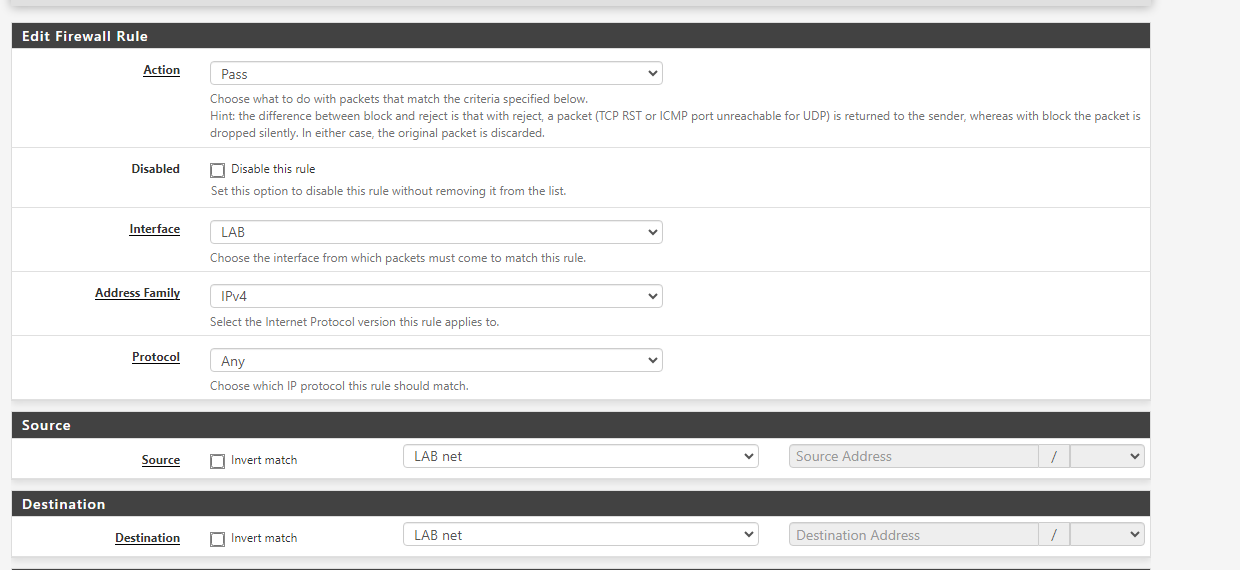
yet if I do a test connection from one VM to another VM both using the same distributed port group obviously for port 445 I can see it hits the default deny rule:
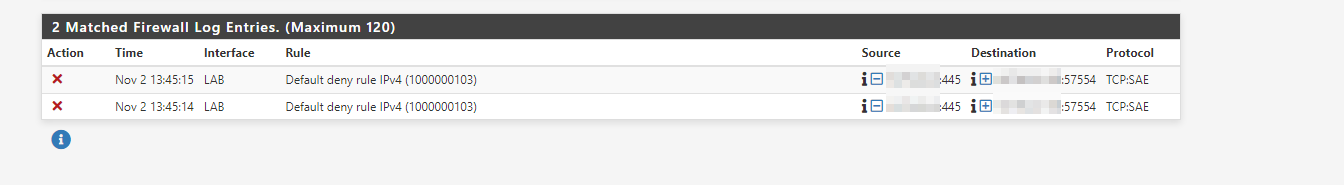
Anyone have any ideas why it's not matching? both IPs are within the subnet assigned to the interface and part of the aliased default _net group.
-
@Justin53
Most probably because of thisboth IPs are within the subnet assigned to the interface
Traffic between devices in the same network segment doesn't pass the router as long as they are not connected to different bridged network ports.
Not clear, why this traffic should even pass pfSense in either direction, but the blocks in the log concerns reply packets. So obviously pfSense has no state for it, because it didn't see the initial SYN packet.
Seems there is something wrong in your network setup. But need more info to get closer. -
@viragomann Good point strange why the response traffic was picked up but the initial connection was not. It's very basic setup here just a distributed port group with VLAN ID attached to it with the interface mapped in pfSense. Both machines have the default gateway set to the static IP in pfSense.
-
@Justin53 why pfsense is only seeing the return, ie SA screams asymmetrical traffic...
-
Yup one of those hosts probably has the wrong subnet mask set so is sending replies to it's gateway (pfSense) incorrectly.
-
@stephenw10 this was exactly it thank you! one of the VMs was not on /24 immediately fixed after correcting it