To do 23.09 or not? That's the question.
-
@chudak no the new 23.09 I have 23.05 I can roll back to if worse comes to worse.. But whenever new version comes out, I like to have the install media for it just in case.
To be honest I don't recall ever having to use it, but have done clean installs sometimes - back when zfs came out I did a clean, etc.
I am on a netgate appliance.. So that is an option..
edit:
Look at that link already in my inbox - those tac guys are normally always johnny on the spot ;)edit2: I would prob just pull the trigger on the upgrade, after taking a backup config for sure. But my new gig is full remote, so prob not a good thing if things went south to be offline for any length of time ;)
-
@chudak said in To do 23.09 or not? That's the question.:
I am personally interested in how the OpenVPN server is faring after the 23.09 migration to OpenSSL 3.
If you are using modern ciphers/hashes on the OpenVPN instance and certs you'd never notice the difference in a lot of cases.
Where you run into problems is with setups that had certs made a decade ago and that also use former OpenVPN default encryption and so on trying to deal with old/legacy clients. Thankfully less and less common these days.
-
@johnpoz said in To do 23.09 or not? That's the question.:
Sending a ticket to tac now to get a image, better to be prepared than sorry ;)
Im living life on the edge...Updating now.
-
@michmoor yeah - that can be fun, normally works without issue.. But I have meeting starting in like 4 mintues..
-
Running smoothly here on the (discontinued) Home/Lab-Version.

-
@johnpoz said in To do 23.09 or not? That's the question.:
@michmoor yeah - that can be fun, normally works without issue.. But I have meeting starting in like 4 mintues..
Cancel your meeting and tell them you have something more important to do

-
@johnpoz said in To do 23.09 or not? That's the question.:
But I have meeting starting in like 4 mintues..
I think my update from 23.05.1 to 23.09 took less than 10 minutes, I would guess something around 7 minutes..
Edit:
It seems that this version is using less RAM in comparison to 23.05.1 ?
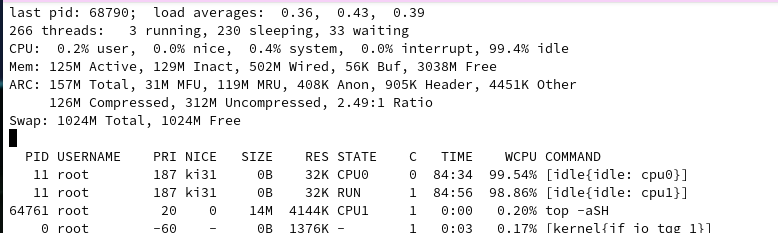
-
Worked fine for me apart from Suricata not starting @bmeeks
-
OS upgrade went through without an issue.
Got to say I'm really feeling the lease utilization screen.......
Let me keep clicking around to see new things. haha
-
@NogBadTheBad https://forum.netgate.com/topic/183878/after-upgrade-to-pf-23-09-surricata-says-it-s-starting-but/
-
@NogBadTheBad said in To do 23.09 or not? That's the question.:
@NogBadTheBad https://forum.netgate.com/topic/183878/after-upgrade-to-pf-23-09-surricata-says-it-s-starting-but/
No issues on my side with pfSense+ 23.09, also Suricata is running without issue on a white box with Intel
 Atom
Atom C3558 same as the Netgate 6100.
C3558 same as the Netgate 6100. -
@johnpoz said in To do 23.09 or not? That's the question.:
@chudak I will be moving to it, prob this weekend.. Or after work hours.. Sending a ticket to tac now to get a image, better to be prepared than sorry ;)
JP, as you pointed out years ago, support is quick. From ticket submission to message with download link was 6 minutes (and I even told them they could sit on the ticket if they were busy with upgrade issues). Image built on thumb drive, update done from a console (still use the RPi as console you helped with).
All went smooth on the old SG-4860. Ever since that issue a while back where the screens filled with errors on boot, I've been a bit gun shy, but pulled the trigger anyway. All my VLANs and interfaces are as built. Snort/pfBlockerNG are happy too. Some higher memory usage after update, but it's coming back down.
Don't miss the manual change to Kea DHCP if you do an update.
I'll build the backup SG-4860 from the thumb drive tomorrow.
I say gopher it.
Rick
-
I upgraded to 23.09 and started having problems with my VPN clients that were connected. I run three VPN clients as I pass traffic to various locations based on geography. That said I recreated them all, each would work as I created them, but as I would create the next the one before would stop working. It didn't appear to be a rule failure as I modified a rule to pass the traffic to the newly created known gateway and it would function. Rather than dig a deeper hole I ended up reverting back to 23.05.1. I still have to decide if I'm continuing on with pfSense or not with the latest licensing issues - so I'll stick at 23.05.1 at the moment until I decide how I want to proceed.
-
@mdthibodeau said in To do 23.09 or not? That's the question.:
I upgraded to 23.09 and started having problems with my VPN clients that were connected.
Have you read through the release notes for 23.09? There are some specific sections on the new OpenSSL regarding changes to algorithms and ciphers that are no longer supported. You may need to change or rebuild your VPN clients to get them to work. I would imagine the OpenSSL 3.0x upgrade will be in the CE version as well due to security issues.
-
@Ramosel
@mdthibodeau said in To do 23.09 or not? That's the question.:That said I recreated them all, each would work as I created them, but as I would create the next the one before would stop working. It didn't appear to be a rule failure as I modified a rule to pass the traffic to the newly created known gateway and it would function.
Yes, I recreated all three. And like I said, as I would build them they would work until the next was built as I have a total of three. I run Plus and not CE, not sure how that would apply.
-
This post is deleted! -
@mdthibodeau said in To do 23.09 or not? That's the question.:
I run Plus and not CE, not sure how that would apply.
You had mentioned in your post that you were having thoughts about the licensing issues.
@mdthibodeau said in To do 23.09 or not? That's the question.:
I still have to decide if I'm continuing on with pfSense or not with the latest licensing issues.
I was just saying that if one of your choices (rather than paying license fees) was to drop back to CE, you'd still have to rebuild your VPN clients as I believe it is inevitable they will include OpenSSL 3.x in that version as well.
-
@Ramosel I understand now. My decision will only be pfSense+ or something non-pfSense. I love the product and trust the product, but I can't say that I trust the leadership decisions. That said, I have no issue paying for a Plus license - however Netgate has continued to be poor at giving all the information (as if they are making decisions on the fly - which in my opinion is pretty bad). They still haven't addressed white box users and the transferability of a TAC Lite license. I've been told they would allow for a "one time courtesy" transfer or if there is hardware failure. The problem is those are simply things I've read that are hearsay and not direct from Netgate. Once I can get some answers to the outstanding questions I have from Netgate then I can make a better informed decision on the direction I'm going to go, however CE will not be it.
To the original issue I had - as I stated - after upgrading I did rebuild my VPN clients. The issue wasn't that they didn't function after I rebuilt them. Again, I have three. I would rebuild #1 and #1 would work. I would then rebuild #2 and #2 would work, but #1 would fail. Continuing, I would rebuild #3 and #3 would work, but #1 and #2 would not work. I can test this as I have rules that direct certain traffic through each of these VPNs. When all three were built out any rules that would direct traffic through #1 and #2 would obviously fail. However, if I modified any of those rules to instead direct traffic out #3 they would work. So, the rules themselves are not failing. Also, after all three were rebuilt - all showed as connected and gateways up. So, I'm not really sure what the issue there is.
-
Kind of moot for a lot of folks I suspect. I was one of the fools who upgraded to pfSense+ a year ago. I would have been happy to support the project for $129/year. Then after the debacle last week, I downgraded to CE. Now I don't need to worry about more Netgate nonsense or TAC Lite pricing going up & down like an elevator.
-
@KOM That's fair. I just hope Netgate realizes that they broke a lot of trust with a lot of people and at some point will either have to openly come out and actually apologize or lose user base. Without trust, you may have a person that continues to use your product - but they are always looking at other options while never recommending your product vs being invested in and backing your product. That's just my two cents though.