Got Crowdsec 0.0.4 installed on my pfSense (now upgraded to V0.1
-
I've just installed crowdsec 0.0.4 from packages at this link
https://github.com/crowdsecurity/pfSense-pkg-crowdsec/releases/tag/v0.0.4
Here is how I installed it:
ssh to pfSense
create crowdsec folder (optional step)
download and install all 4 packages by fetch and install commands
fetch -a -r https://github.com/crowdsecurity/pfSense-pkg-crowdsec/releases/download/v0.0.4/crowdsec-1.5.4.pkg
fetch ....other 3 packages
install all 4 packages, starting with the re2_2023....pkg by (still in ssh session)
pkg install re2_20230301.pkg
pkg install ..... other 3 packages
You are done. Reload pfSense webui, you will then see Crowdsec service under Services tab. Click to it, read its first tab carefully, click the Settings tab and press Save to start running crowdsec .
You can then tweak the Settings whether you want a full service or just for log parser ... and let your existing LAPI on other local/remote server handle the decision.ec service. Read its instruction carefully in the first crowdsec tab because during installing some package, you will see some extra commands to do, e.g. sysrc command, creating pf.cong....Don't do it!
After running crowdsec, it will download IP blocking lists from its Central API and you will see two new Aliases created under Firewall/Aliases, i.e, crowdsec_blacklists and crowdsec6_blacklists. In my understanding, if not wrong, I need to create two firewall blocking rules based on these two aliases, in order to enable blocking those IPs (Firewall/Rules/WAN).
I later added haproxy and syslog collections into it (by cscli command line). I'm still new to crowdsec and if someone has more experience in setting it up on pfSense, please share.
Thank you
note: here is the metrics output after installation
Acquisition Metrics:╭───────────────────────────┬────────────┬──────────────┬────────────────┬────────────────────────╮ │ Source │ Lines read │ Lines parsed │ Lines unparsed │ Lines poured to bucket │ ├───────────────────────────┼────────────┼──────────────┼────────────────┼────────────────────────┤ │ file:/var/log/auth.log │ 21 │ - │ 21 │ - │ │ file:/var/log/filter.log │ 5.12k │ 3.77k │ 1.35k │ 968 │ │ file:/var/log/haproxy.log │ 1.19k │ - │ 1.19k │ - │ │ file:/var/log/system.log │ 48 │ - │ 48 │ - │ ╰───────────────────────────┴────────────┴──────────────┴────────────────┴────────────────────────╯ Bucket Metrics: ╭──────────────────────────────────────┬───────────────┬───────────┬──────────────┬────────┬─────────╮ │ Bucket │ Current Count │ Overflows │ Instantiated │ Poured │ Expired │ ├──────────────────────────────────────┼───────────────┼───────────┼──────────────┼────────┼─────────┤ │ firewallservices/pf-scan-multi_ports │ 47 │ - │ 887 │ 968 │ 840 │ ╰──────────────────────────────────────┴───────────────┴───────────┴──────────────┴────────┴─────────╯ Parser Metrics: ╭─────────────────────────────────┬───────┬────────┬──────────╮ │ Parsers │ Hits │ Parsed │ Unparsed │ ├─────────────────────────────────┼───────┼────────┼──────────┤ │ child-crowdsecurity/sshd-logs │ 176 │ - │ 176 │ │ child-crowdsecurity/syslog-logs │ 5.19k │ 5.19k │ - │ │ crowdsecurity/dateparse-enrich │ 3.77k │ 3.77k │ - │ │ crowdsecurity/geoip-enrich │ 3.77k │ 3.77k │ - │ │ crowdsecurity/haproxy-logs │ 1.19k │ - │ 1.19k │ │ crowdsecurity/non-syslog │ 1.19k │ 1.19k │ - │ │ crowdsecurity/sshd-logs │ 16 │ - │ 16 │ │ crowdsecurity/syslog-logs │ 5.19k │ 5.19k │ - │ │ firewallservices/pf-logs │ 5.12k │ 3.77k │ 1.35k │ │ firewallservices/pf-logs-drop │ 3.77k │ 3.77k │ - │ ╰─────────────────────────────────┴───────┴────────┴──────────╯ Local API Metrics: ╭──────────────────────┬────────┬──────╮ │ Route │ Method │ Hits │ ├──────────────────────┼────────┼──────┤ │ /v1/decisions/stream │ GET │ 268 │ │ /v1/heartbeat │ GET │ 44 │ │ /v1/watchers/login │ POST │ 1 │ ╰──────────────────────┴────────┴──────╯ Local API Machines Metrics: ╭─────────┬───────────────┬────────┬──────╮ │ Machine │ Route │ Method │ Hits │ ├─────────┼───────────────┼────────┼──────┤ │ pfsense │ /v1/heartbeat │ GET │ 44 │ ╰─────────┴───────────────┴────────┴──────╯ Local API Bouncers Metrics: ╭──────────────────┬──────────────────────┬────────┬──────╮ │ Bouncer │ Route │ Method │ Hits │ ├──────────────────┼──────────────────────┼────────┼──────┤ │ pfsense-firewall │ /v1/decisions/stream │ GET │ 268 │ ╰──────────────────┴──────────────────────┴────────┴──────╯ Local API Decisions: ╭────────────────────────────────────────────┬────────┬────────┬───────╮ │ Reason │ Origin │ Action │ Count │ ├────────────────────────────────────────────┼────────┼────────┼───────┤ │ crowdsecurity/ssh-bf │ CAPI │ ban │ 13754 │ │ firewallservices/pf-scan-multi_ports │ CAPI │ ban │ 199 │ │ crowdsecurity/CVE-2019-18935 │ CAPI │ ban │ 24 │ │ crowdsecurity/CVE-2022-37042 │ CAPI │ ban │ 17 │ │ crowdsecurity/http-generic-bf │ CAPI │ ban │ 6 │ │ crowdsecurity/http-open-proxy │ CAPI │ ban │ 251 │ │ crowdsecurity/http-path-traversal-probing │ CAPI │ ban │ 23 │ │ crowdsecurity/http-sensitive-files │ CAPI │ ban │ 6 │ │ crowdsecurity/f5-big-ip-cve-2020-5902 │ CAPI │ ban │ 19 │ │ crowdsecurity/http-bad-user-agent │ CAPI │ ban │ 2796 │ │ crowdsecurity/netgear_rce │ CAPI │ ban │ 20 │ │ crowdsecurity/nginx-req-limit-exceeded │ CAPI │ ban │ 67 │ │ crowdsecurity/http-cve-2021-41773 │ CAPI │ ban │ 17 │ │ crowdsecurity/http-probing │ CAPI │ ban │ 880 │ │ crowdsecurity/CVE-2022-26134 │ CAPI │ ban │ 149 │ │ crowdsecurity/CVE-2022-35914 │ CAPI │ ban │ 43 │ │ crowdsecurity/apache_log4j2_cve-2021-44228 │ CAPI │ ban │ 309 │ │ crowdsecurity/fortinet-cve-2018-13379 │ CAPI │ ban │ 70 │ │ crowdsecurity/grafana-cve-2021-43798 │ CAPI │ ban │ 44 │ │ crowdsecurity/http-backdoors-attempts │ CAPI │ ban │ 307 │ │ crowdsecurity/jira_cve-2021-26086 │ CAPI │ ban │ 10 │ │ crowdsecurity/ssh-slow-bf │ CAPI │ ban │ 28 │ │ crowdsecurity/CVE-2022-41082 │ CAPI │ ban │ 187 │ │ crowdsecurity/CVE-2022-42889 │ CAPI │ ban │ 5 │ │ crowdsecurity/http-crawl-non_statics │ CAPI │ ban │ 206 │ │ crowdsecurity/thinkphp-cve-2018-20062 │ CAPI │ ban │ 17 │ ╰────────────────────────────────────────────┴────────┴────────┴───────╯ -
Live block by crowdsec: sample
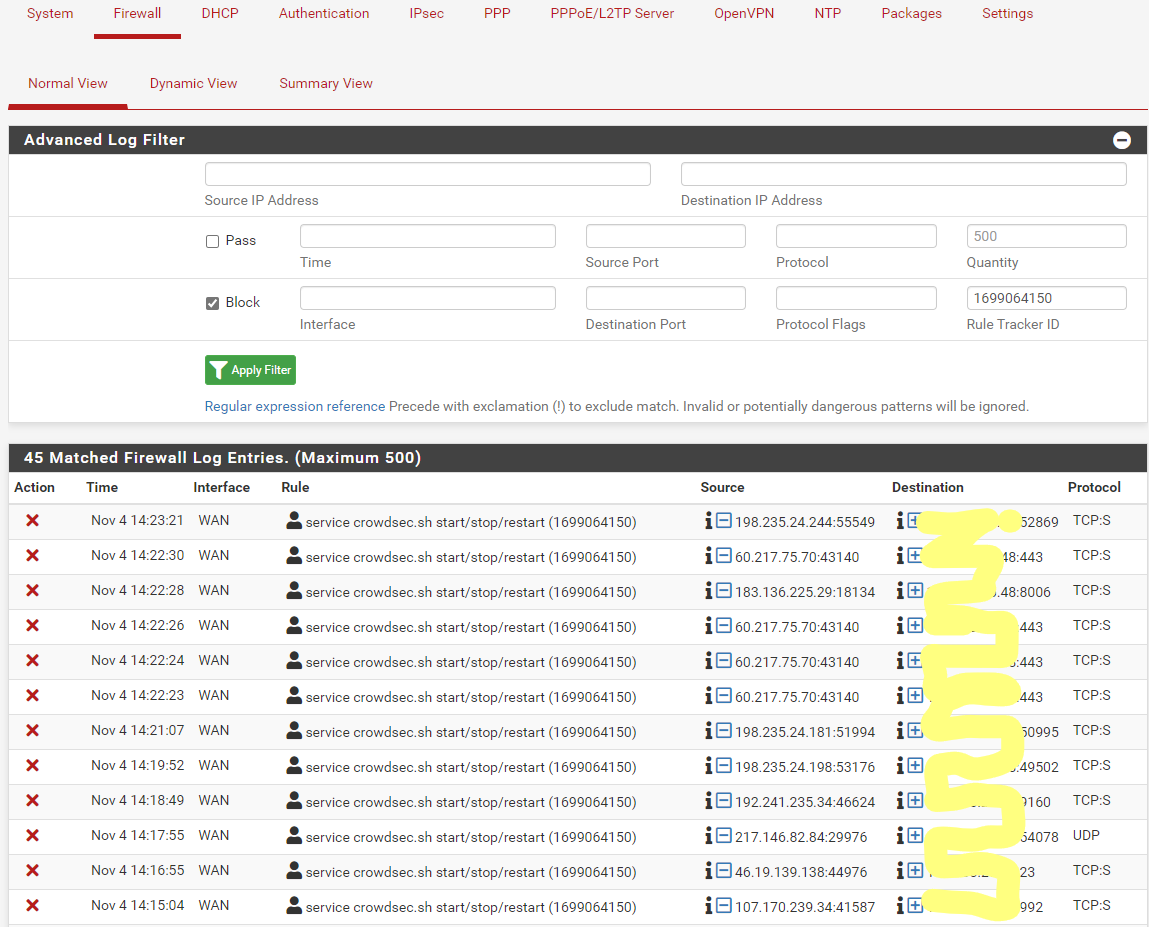
port scan block: sample
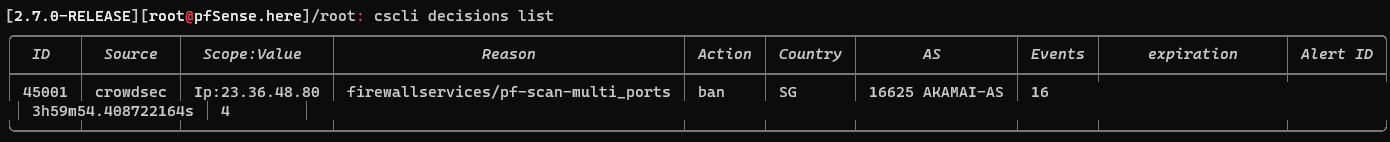
corresponding log entries in crowdsec log file
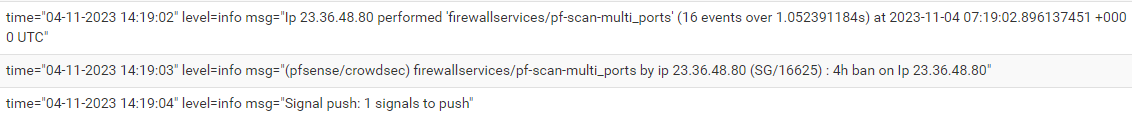
-
Just update to the latest version v0.1
All the additional collections and blocklists I installed in v.0.0.4 are still there and were automatically upgraded during installing the new version.Here is my upgrading steps
remove old version
service crowdsec.sh stop pkg remove pfSense-pkg-crowdsec crowdsec crowdsec-firewall-bouncer re2installing v0.1
setenv IGNORE_OSVERSION yes pkg add https://github.com/crowdsecurity/pfSense-pkg-crowdsec/releases/download/v0.1/abseil-20230125.3.pkg pkg add https://github.com/crowdsecurity/pfSense-pkg-crowdsec/releases/download/v0.1/re2-20230901.pkg pkg add https://github.com/crowdsecurity/pfSense-pkg-crowdsec/releases/download/v0.1/crowdsec-firewall-bouncer-0.0.28_1.pkg pkg add https://github.com/crowdsecurity/pfSense-pkg-crowdsec/releases/download/v0.1/crowdsec-1.5.5.pkg pkg add https://github.com/crowdsecurity/pfSense-pkg-crowdsec/releases/download/v0.1/pfSense-pkg-crowdsec-0.1.pkgCrowdsec starts running by itself after the upgrade.
-
@bthoven
Areyou the maintainer of this package? -
@michmoor No. I'm just a user. The reason I posted was that I'm not familiar with freebsd command lines and thought it might help others who have struggled to do it, and no mention in the official instruction on how to upgrade the package, especially now it is still not in the package list GUI on pfSense.
-
@michmoor I've seen a couple posts on Reddit but have not used this package. Crowdsec is the dev: https://www.crowdsec.net/product/crowdsec-security-engine, https://docs.crowdsec.net/docs/next/intro
A post I read a month or so ago said it wasn't available for Plus, only CE, I think because it was being installed outside of the pfSense repos? But https://docs.crowdsec.net/docs/next/getting_started/install_crowdsec_pfsense does not mention that, however it does say "We have submitted the package to the pfSense developers for review and inclusion in the official repositories."
It's an interesting approach. Basically a real time block list. Functionally though, seems similar to pfBlocker downloading block lists.
-
@SteveITS
I agree in terms of the function. It seems to work with other tools like Suricata or pfBlocker but with similar functionality.
I'm willing to give it a shot once its available officially tho. Could be interesting.