Linux IPTables NAT to pfSense NAT
-
@viragomann
Your explanation is same as my understanding.
here is the topology:pfSense LAN 172.16.0.1 with Virtual IP 192.168.0.1 | Switch | +--------------+------------+ | | Laptop 192.168.0.100 Device 172.16.0.100What I want is, when I try to access 1.2.3.4 from my laptop, pfSense can do DNAT and SNAT, which make it looks like this:
192.168.0.100 -> 1.2.3.4
Apply DNAT rule => 192.168.0.100 -> 172.16.0.100
If no DNAT, then the package will route to WAN (default gateway), but now, it should route to LAN interface.
Apply SNAT rule. => 172.16.0.1 -> 172.16.0.100 -
Tried packet capture.
Seems the issue is the DNAT not working as I expected.
When I ping 1.2.3.4 from 192.168.0.100, the DNAT rule should change the destination to 172.16.0.100, but it actually goes to WAN.
I captured the ICMP on WAN interface, and the source ip has been changed to external IP, and the target didn't change. -
@thomasyuan So you're trying to capture traffic from laptop 192.168.0.100 intended for the external IP 1.2.3.4 and send it to 172.16.0.100?
This may help, it's describing capturing and redirecting DNS requests on port 53:
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html"invert LAN Address" would be "any other DNS server" but in your case the destination would be 1.2.3.4.
-
@thomasyuan said in Linux IPTables NAT to pfSense NAT:
192.168.0.100 -> 1.2.3.4
Apply DNAT rule => 192.168.0.100 -> 172.16.0.100
If no DNAT, then the package will route to WAN (default gateway), but now, it should route to LAN interface.
Apply SNAT rule. => 172.16.0.1 -> 172.16.0.100So if you call 1.2.3.4 on the laptop it should go to 172.16.0.100, as I understood.
This would need a simple port forwarding rule on the LAN.
Select the LAN interface, at source state 192.168.0.100, at destination enter 1.2.3.4 and at redirect target 172.16.0.100.An outbound NAT rule (SNAT) is only necessary if the destination device has no default gateway settings or even use another default gateway than pfSense.
In this case switch the outbound NAT into hybrid mode and add a rule:
interface: LAN
source: *
destination: 172.16.0.100
translation: interface address (as I got it, this is 172.16.0.1) -
@viragomann
yes, I need the SNAT because I can NOT change anything on the device, the devices only has fixed IP, and no default gateway.And I believe your suggestion for the SNAT rule is exactly what I did. (did spend sometime to figure out why the SNAT is grayed out)
-
@SteveITS
Thanks for the reference link. I wasn’t sure what’s NAT reflection before as I mentioned I an newbie to pfSense. After reviewing some explanations, I feel maybe I don’t need the SNAT, just need to set the NAT reflection to Proxy? Will try and update later.one comment from reddit
DutchOfBurdock • 4 yr. ago It's a facility of NAT to allow LAN hosts to make connections to forwarded ports on WAN. In most circumstances, LAN hosts will access LAN hosts via LAN. However, in some cases, you need to access the services via the WAN (TLS certificate in a public facing web server, for example) IP. NAT would normally drop these connections. Reflection changes that behaviour and will forward the connections to the forwarded IP. There are two modes for this, Proxy and Pure. Pure is generally better; especially for game servers or services requiring large port ranges and UDP. Proxy is useful for TCP only servers, but has the benefit of making the connection appear to come from the Firewall (LAN) IP. -
@thomasyuan
And you say, even though you added these two NAT rule correctly, the packets to 1.2.3.4 is directed out to the WAN gateway?When I ping 1.2.3.4 from 192.168.0.100, the DNAT rule should change the destination to 172.16.0.100, but it actually goes to WAN.
I captured the ICMP on WAN interface, and the source ip has been changed to external IP, and the target didn't change.So I'd assume, that your LAN interface network mask is wrong.
Can you post some screenshot, please, so that we can see your setting rather then stepping in the dark:
Status > interfaces
NAT Port forward
NAT outbound@thomasyuan said in Linux IPTables NAT to pfSense NAT:
I feel maybe I don’t need the SNAT, just need to set the NAT reflection to Proxy?
NAT reflection mirrors NAT rules from WAN to the internal interfaces.So internal devices are enabled to access other internal destinations with the public IP.
I don't expect, that this does anything in your setup. -
@viragomann
I didn't use the real ip address when I describe the issue.
You can replace 192.168.0.x to 192.168.66.x, 1.2.3.4 to 50.112.4.100, and 172.16.0.x to 172.16.4.x.
Here is the screenshot of the NAT.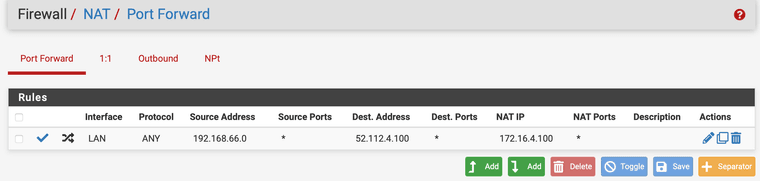
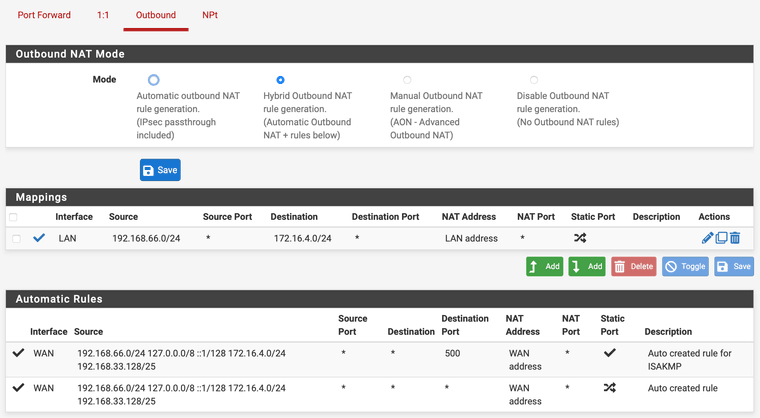
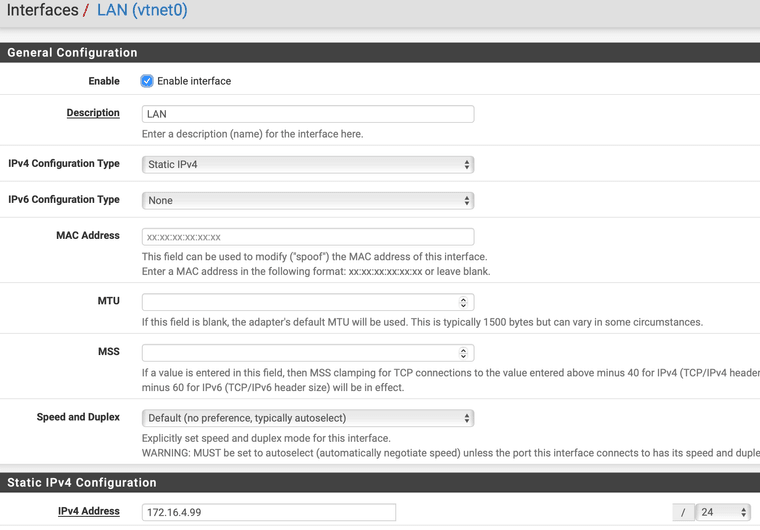
I think right now, the major issue is, seems the port forwarding is not applied for some reason.
-
When I ping 52.112.4.100 from my laptop, I can see below packet from LAN
03:19:05.100249 IP 192.168.66.210 > 52.112.4.100: ICMP echo request, id 1, seq 2471, length 40And below packet from WAN (192.168.99.99 is WAN IP address)
03:21:08.179184 IP 192.168.99.99 > 52.112.4.100: ICMP echo request, id 36355, seq 2472, length 40I feel the Port Forward is not working, so the destination didn't change to 172.16.4.100, so the packet will route to WAN instead of LAN, which then cause the Outbound rule can't match because it was applied on LAN interface.
-
I am stupid.
The Port Forward rule was wrong.
It should be 192.168.66.0/24 network, but I selected single host and give the ip address as 192.168.66.0.
Thanks @viragomann and @SteveITS !