Clients cant resolve DNS names.
-
Hi everyone,
I just installed my first pfsense systeme ever. I followed several YT videos, included NetworkChuck's and referred to the DNS Resolution Issues website https://docs.netgate.com/pfsense/en/latest/troubleshooting/dns.html .
Following all the steps and going through all the test I've concluded it's a DNS resolution Issue from the PfSense machine to the clients.
So here is my context:
I've installed PfSense as a Virtual machine on Proxmox on a Server with 4 nics.
I've set one of the nics as WAN with a DHCP Ip from my ISP cablemodem/router.
I/ve set another nic as LAN with a 10.x.x.1 IP.
DNS Forwarder and Resolver are disabled.
I've got a Pi-hole and I'm using it as primary server (It works great on any machine not routed through PfSense).
As secondary DNS server I've set 1.1.1.1.
DNS lookup from PfSense works great, Pi-hole resolves even faster than Cloudfare.Clients, get their Ip's from DHCP set on LAN, and can ping all sorts of IPs, DNS Servers, outside servers, WAN, LAN, ISP modem-router, etc. The problem comes the moment I ping a url. The error is pretty clear to me: "Temporary failure in name resolution."
I really need your help here guys, I'm hoping to use PfSense as a Vlan manager to split my IOT devices in a different network for obvious reasons, but I've been banging my head on this issue for the past 3 hours and I still cant get what I've done wrong.
Thank you to all of you in advance for your help.
-
@Kolvert said in Clients cant resolve DNS names.:
DNS Forwarder and Resolver are disabled.
When then how would dns work?
Ask pihole what your doing wrong.. Out of the box the lan rules are any any.. Did you change those? Then pfsense would have zero to do with pihole talking to any dns server it wants.
-
@johnpoz Hi,
As you already know, Resolver was enabled by default, and it didn't help even when dns servers where Cloudfare and Google. I tried enabling Forwarder, and nothing. Firewall rules for LAN are PASS for any to any. I also tried PASS on WAN any to any.
I can tell for sure that once I decided to try Pi-hole PfSense used it for queries successfully, but still didn't pass the url's to the clients.
So basically default settings didn't resolve DNS, and custom neither. So I checked the guide and the forum, tried and tested for hours and after failing on every attempt I asked for help.
-
@Kolvert said in Clients cant resolve DNS names.:
Clients, get their Ip's from DHCP set on LAN, and can ping all sorts of IPs, DNS Servers, outside servers, WAN, LAN, ISP modem-router, etc. The problem comes the moment I ping a url. The error is pretty clear to me: "Temporary failure in name resolution.
Your clients get a LAN IP. But they got more then then that.
Did they got a network (network mask), a gateway IP and most important : a DNS IP.
So, on one of these 'clients', useipconfig /alland check that DNS IP.
Does it 'points' to the IP that is used by your DNS = Pi-Hole.
Also : can it reach the Pi-Hiole ? If the piHome is on the same LAN as the clients, the there will be no problem.
Another LAN, then a firewall rule on the Clienst LAN has to authorize the DNS traffic.You could use the 'nslookup' command to check if the client actually can and uses pi-Hole for its DNS needs.
@Kolvert said in Clients cant resolve DNS names.:
DNS Forwarder and Resolver are disabled.
Better check and be sure that pfSense itself still has a working DNS then.
-
@Kolvert said in Clients cant resolve DNS names.:
Resolver was enabled by default, and it didn't help even when dns servers where Cloudfare and Google
Because setting dns has zero to do with anything when you resolving..
So in the diagnostic menu, dns lookup with unbound enabled.. Can you look up say www.netgate.com ?
This is with default settings of pfsense.
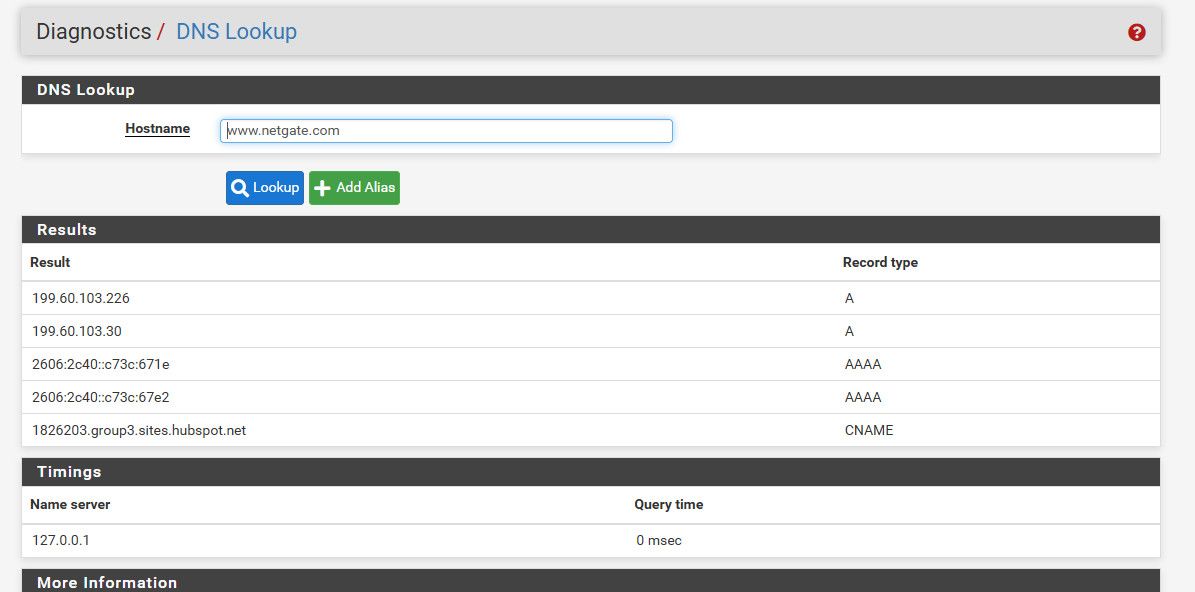
If that fails, from cmd line on pfsense do a trace..
Enter an option: 8 [23.09-RELEASE][admin@sg4860.local.lan]/root: dig www.netgate.com +trace ; <<>> DiG 9.18.16 <<>> www.netgate.com +trace ;; global options: +cmd . 82332 IN NS f.root-servers.net. . 82332 IN NS e.root-servers.net. . 82332 IN NS d.root-servers.net. . 82332 IN NS a.root-servers.net. . 82332 IN NS b.root-servers.net. . 82332 IN NS j.root-servers.net. . 82332 IN NS c.root-servers.net. . 82332 IN NS i.root-servers.net. . 82332 IN NS g.root-servers.net. . 82332 IN NS h.root-servers.net. . 82332 IN NS k.root-servers.net. . 82332 IN NS m.root-servers.net. . 82332 IN NS l.root-servers.net. . 82332 IN RRSIG NS 8 0 518400 20231126050000 20231113040000 46780 . eDfXq+KZzto5xFLKorHYdE1QL6Sia8J0MiBn6f4jba2Ti8dOxLIylTzE f4UaLMMPM+PVml2jgjgL0dcCFhU4/9yO/kKNtQWW5XzGFm7yQoYbkl5u +DEJ4IUqb/UfU35v6rklV7DuLdARv2+hoPw5nX6ncLMa6F5IXnTFJoW6 KwDrYVvh/wNTHCLbbecMg2OcrCgJ+GvYxt1nkbKrWC7LiAohnpwyg4Wc LkT+o+8ogK3CtTbPs72vnqOqEuUn9oB/I0RCOvg1qkdjuVvzh+R4gN4G fOcn4j9phCYwdF8XBDpJG/w8Z4rT78N8J28wSx37nZbMucHvU687+fvI 0fodKQ== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766 com. 86400 IN RRSIG DS 8 1 86400 20231126050000 20231113040000 46780 . JaEUR+R7peut6yFM1LbPkXRSFAIyU0RR88Qgj24mIos4woIP2xZ+vVC/ mVK775YUIf9laz9F2OcDHq6RpJNp4IwKxEGw+Dd33DQgWi+zzSFiZoK9 KvI27vAsuSuK33J2lUAdTR68HjG7CBX7XtDtHqTmM/guLusd07r9rrzp /HrgSncZ6gVblrooUTadoIO8wGV4875c2rof4G2WeUA3Fpg13iydgM4f oZrLZKfnbbEhhOzq6FKHKBeGOWfdOXYIAGePGcr954eUtLIJE8M9KQMY IPhNPyVLgSr/VsAFfxEoPA5GHfuSrF3I2EEXDOF99id4OOr26H4pxSG1 N1DOrg== ;; Received 1175 bytes from 198.41.0.4#53(a.root-servers.net) in 9 ms netgate.com. 172800 IN NS ns1.netgate.com. netgate.com. 172800 IN NS ns2.netgate.com. netgate.com. 172800 IN NS ns3.netgate.com. CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q2D6NI4I7EQH8NA30NS61O48UL8G5 NS SOA RRSIG DNSKEY NSEC3PARAM CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20231118052525 20231111041525 63246 com. HHilTlIgM2bBSkNCrfIYydeweb7FpcSd/HCPjoMq9cDoI45LnU1trxYf GtncYfSgPxd01lt7BuBdTBRjFX2kHEWQNAjqKR+wj9ohk9mqvk3naenD eWVPwSEZjYdV+LPjL7rXvMWq6GRZXFG2OC0oR37mS4PCPT/pWYTARo7m 66PiR/ixIP8UPkUbxjZTHFuDsR+lywg8Od0OsTopTj5+rw== 2U53SUOKS8OJJV178M90A8BMNI9USDVJ.com. 86400 IN NSEC3 1 1 0 - 2U546JK1TS9KBOQUQCUA3NNLO26FTDRN NS DS RRSIG 2U53SUOKS8OJJV178M90A8BMNI9USDVJ.com. 86400 IN RRSIG NSEC3 8 2 86400 20231119051632 20231112040632 63246 com. OacVZDM5N9+s5oGr+dXi0mHEWEjsnkEvnLh/D7JRl0SeqOGl8DT4Gw4t XGfhVZ2qp3fbe3mFtSrpk8ptK76sw3gCvohniFT9+Wn4Er/7n/qEpAKX jCqdKGGFiwYWl/Ivav3UntPJGHGRZhMRdPfFReewNRhOjAMKKI1zCx5V SByKJiUTTfEaC5MEp8BXEzVAt/iQrk229m8KZf2O5RPVeg== ;; Received 779 bytes from 192.5.6.30#53(a.gtld-servers.net) in 42 ms www.netgate.com. 60 IN CNAME 1826203.group3.sites.hubspot.net. ;; Received 118 bytes from 208.123.73.90#53(ns2.netgate.com) in 33 ms [23.09-RELEASE][admin@sg4860.local.lan]/root:This is how resolver would resolve..
-
Hi, sorry everyone for the delay, I really thought I posted here that I found the solution to this problem.
The problem was, on Proxmox, I had set static IP on the NIC and it was way out of the one I was using into PfSense.
As said I'm just dipping my toes on network management and on virtualization, so please excuse my ignorance.Thank you everyone for your help.