Not able to reach P2 Tunnel IPSec VPN From another FW
-
Hi! We have the following topology:
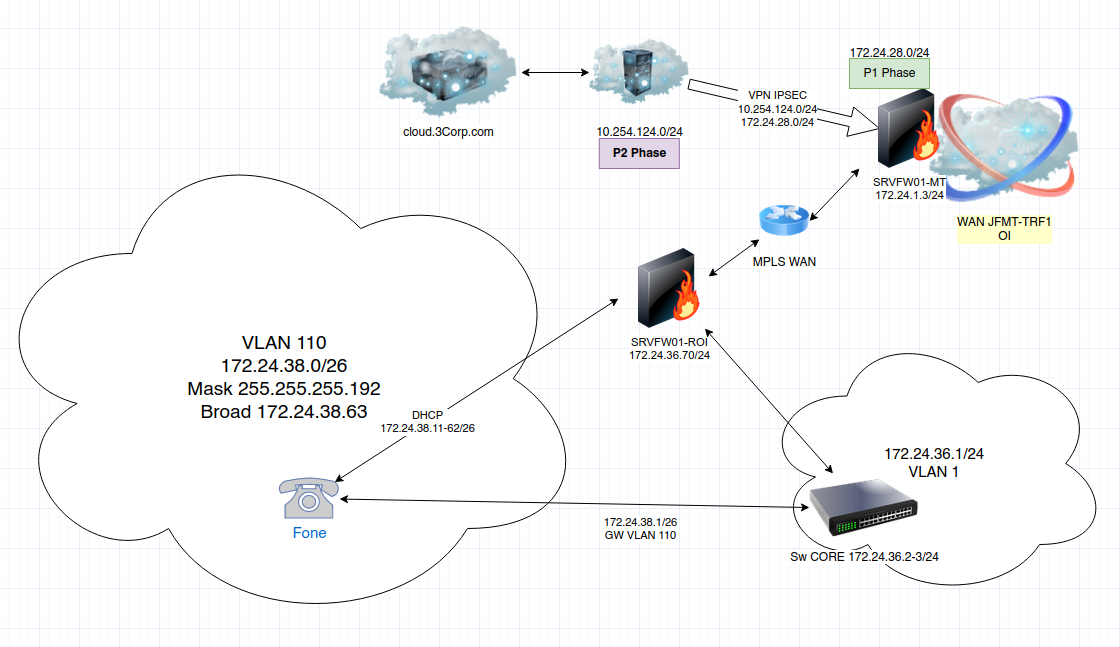
- Each firewall is Pfsense release 2.4.4;
- 172.24.28.0/24 is root VLAN110 and 172.24.38.0/24 is leaf VLAN110;
- They are normally communicating each other;
- VPN IPSec P1 Phase is Tagged VLAN110;
- VPN IPsec is fully functional between P1 and P2 phases;
- 10.254.124.0 is external network from Telecom Provider;
- Telecom could reach 172.24.38.0/26 network due to Firewall IPSec Rules;
My question is:
- How does 174.24.38.0/26 reach to 10.254.124.0? They stuck in 172.24.38.1
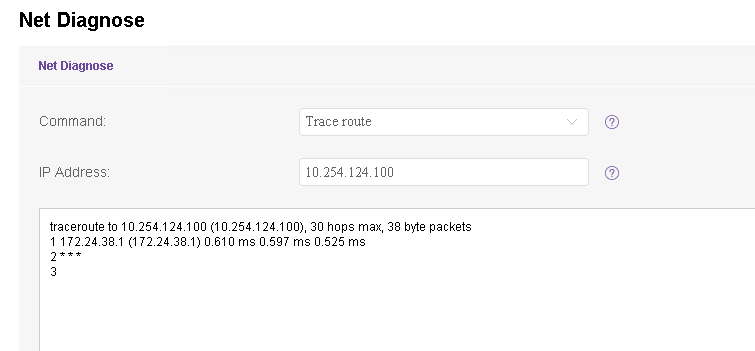
-
@Redbob
Has routing ever worked prior to you posting here? -
@michmoor Routing from 172.24.38.0/26 to 172.24.28.0/24 works fine (IP cliente here is 172.24.38.12):
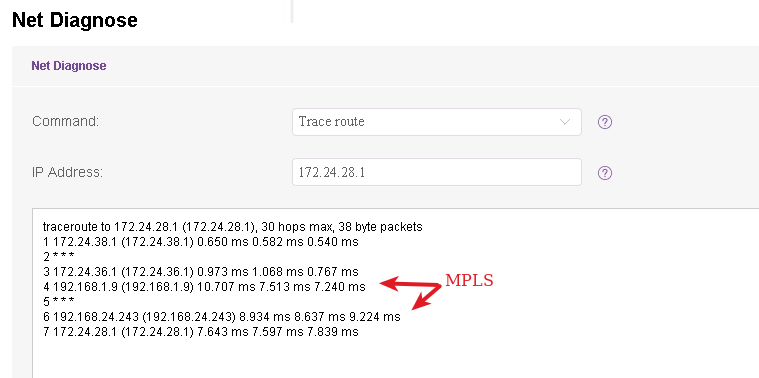
-
@Redbob
To clarify, has it routing through the IPsec tunnel ever worked? Reading the post it feels like it did so im trying to make sure if it was working before so we can figure out what changed.If it never worked, then my question is how will traffic get to the other LAN? Static or Dynamic routing?
-
@michmoor The IPSec Tunnel works fine. Look this device:
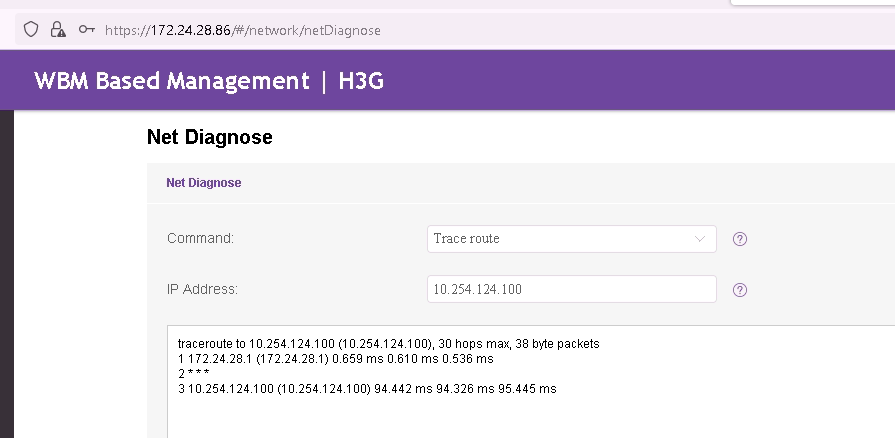
It's on the 172.24.28.0/24 side. The challenge is: how to establish a route between 172.24.38.0/26 and 172.24.28.0/24 till 10.254.124.0/24?
172.24.38.0/26 is not merely a subnet from 172.24.28.0/24 due to tag, because Telecom must not access the entire network (172.24.0.0/16)This is VPN IPsec:
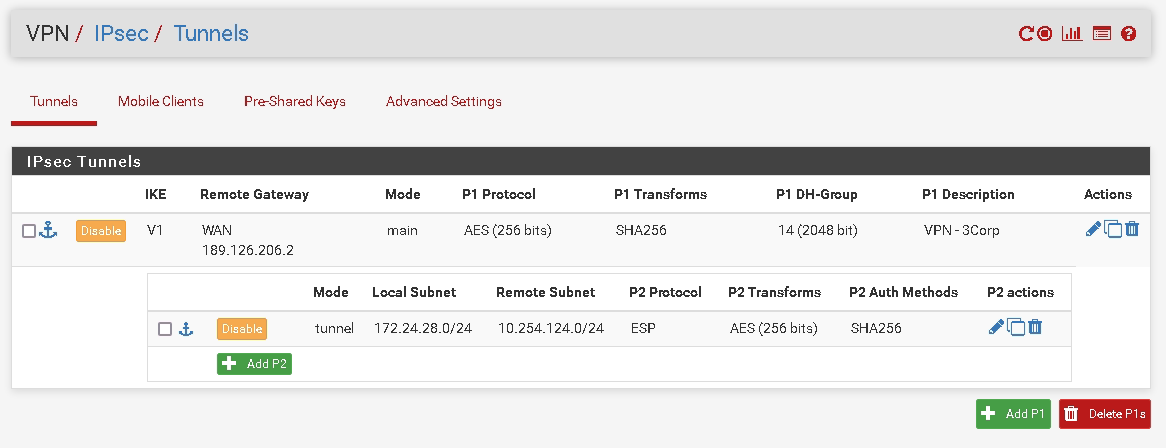
And these are rules:
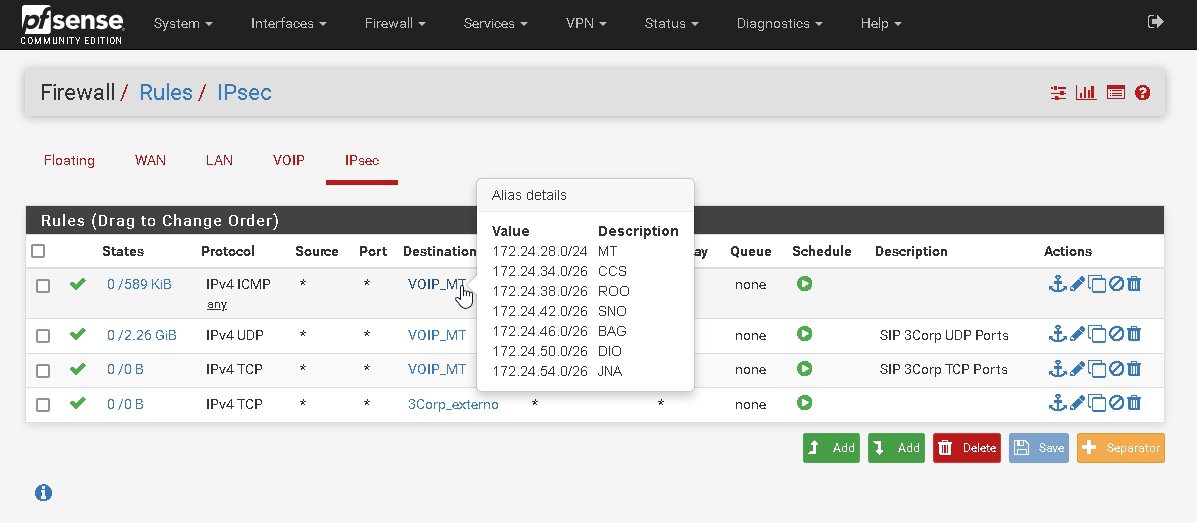
-
172.24.38.1 doesnt have a route to 10.254.124.0/24.
Your options are either to- create static routes on each hop.
- use dynamic routing protocols such as OSPF or BGP.