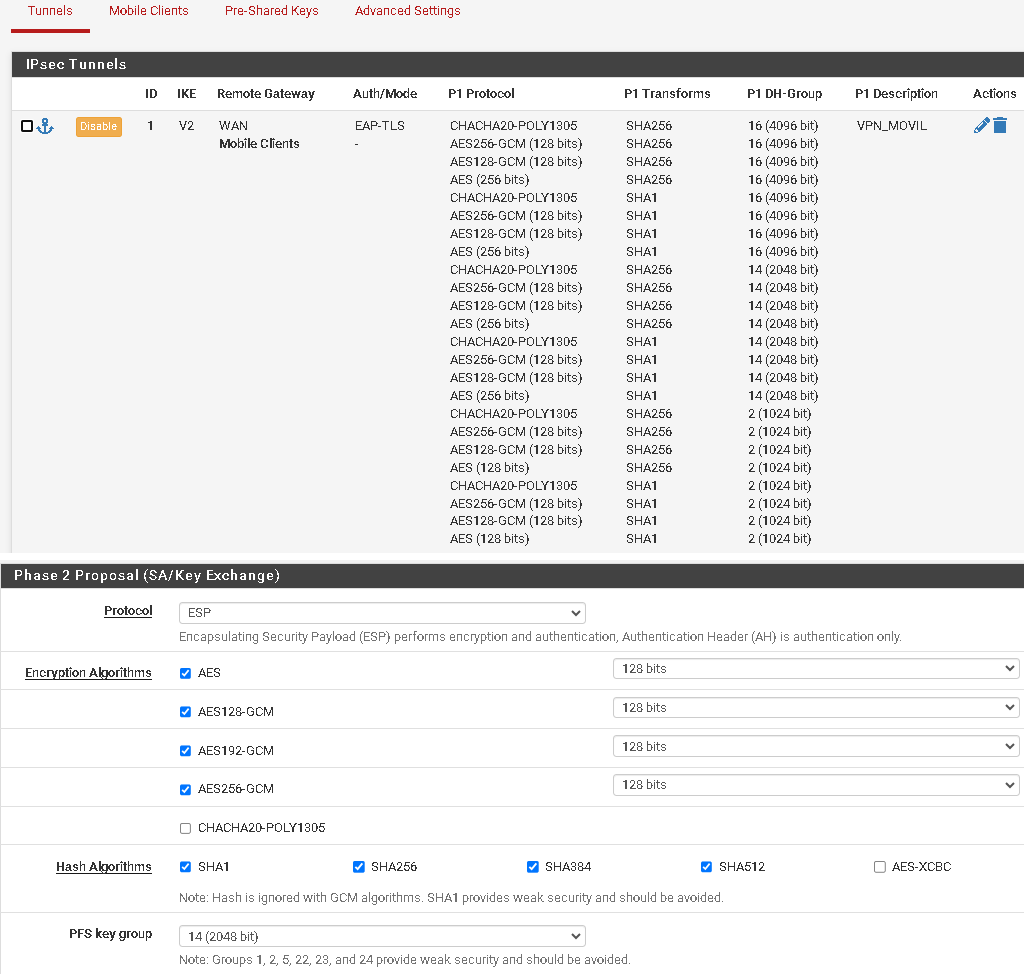
IPSEC S2S VPN failing with no IKE config found for x.x.x.x...x.x.x.x.x, sending NO_PROPOSAL_CHOSEN
-
Hello,
I'm trying to connect to PFSense routers with an IPSEC S2S but am getting this error.
Nov 24 13:10:34 charon 59062 06[IKE] <2> no IKE config found for x.x.x.x...x.x.x.x, sending NO_PROPOSAL_CHOSEN. I have set them up as follows:
Both routers are internet facing, not behind NAT.
Office 82.71.x.x:
Phase 1
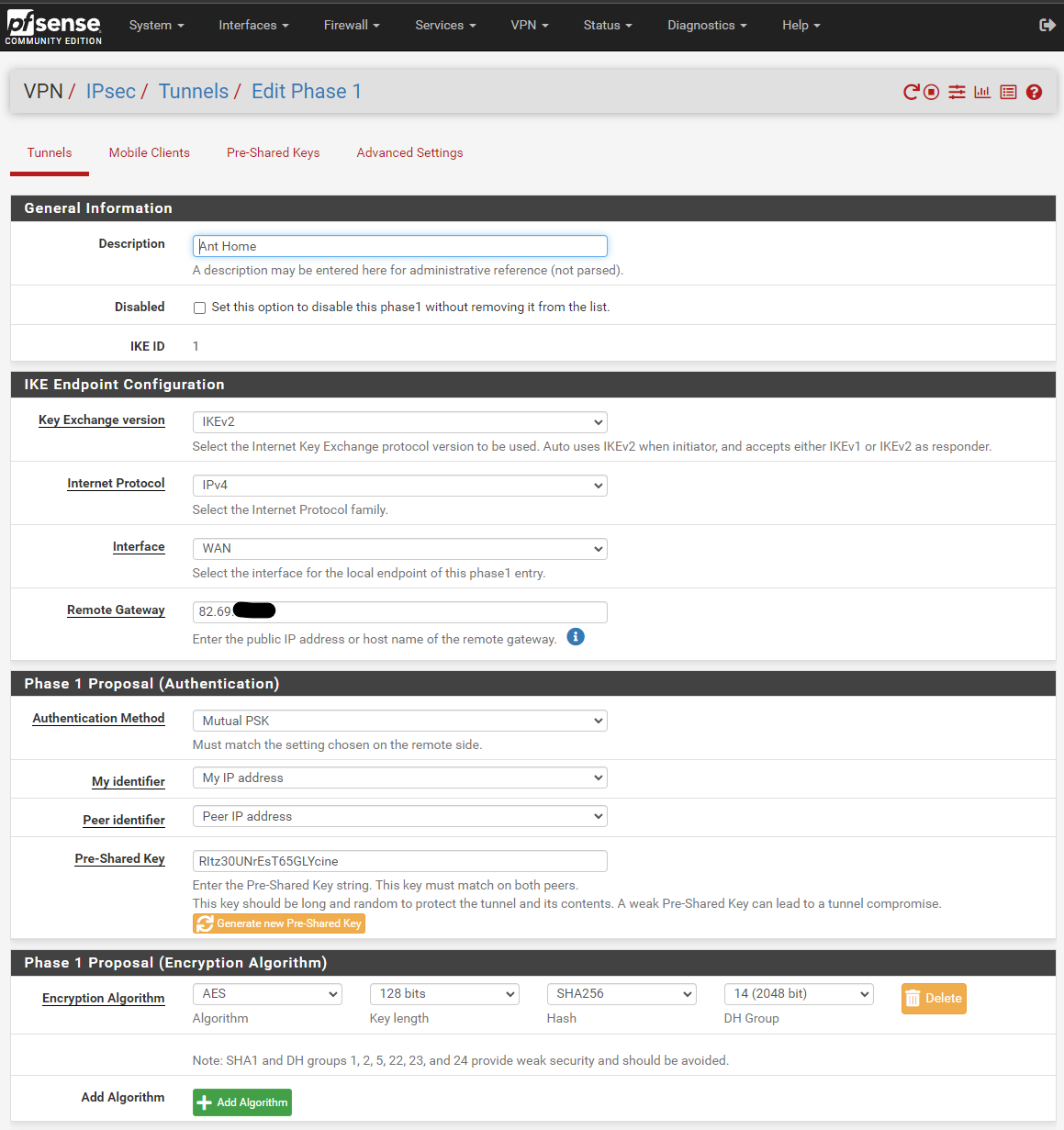
Phase 2
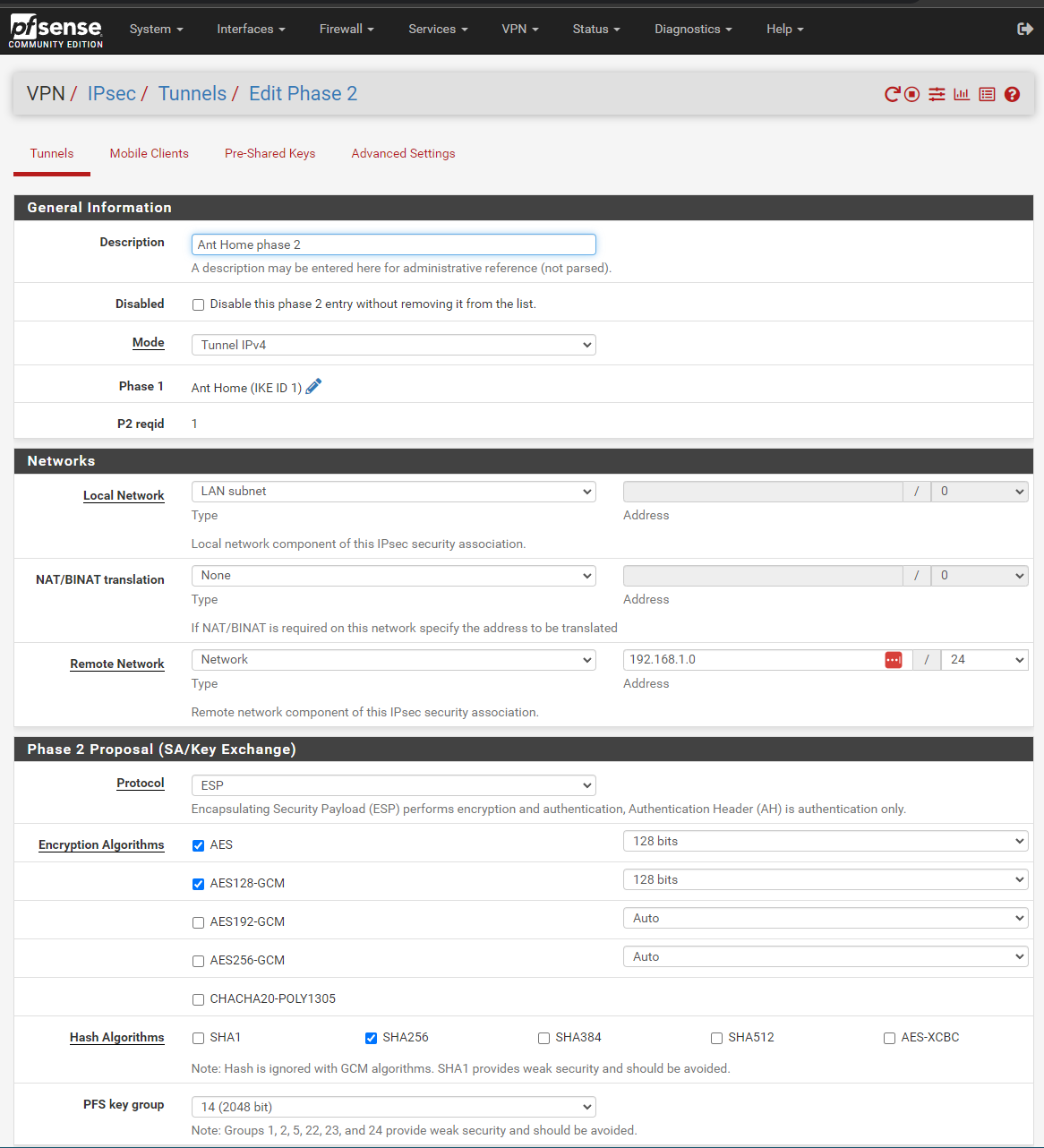
Home 82.69.x.x:
Phase 1
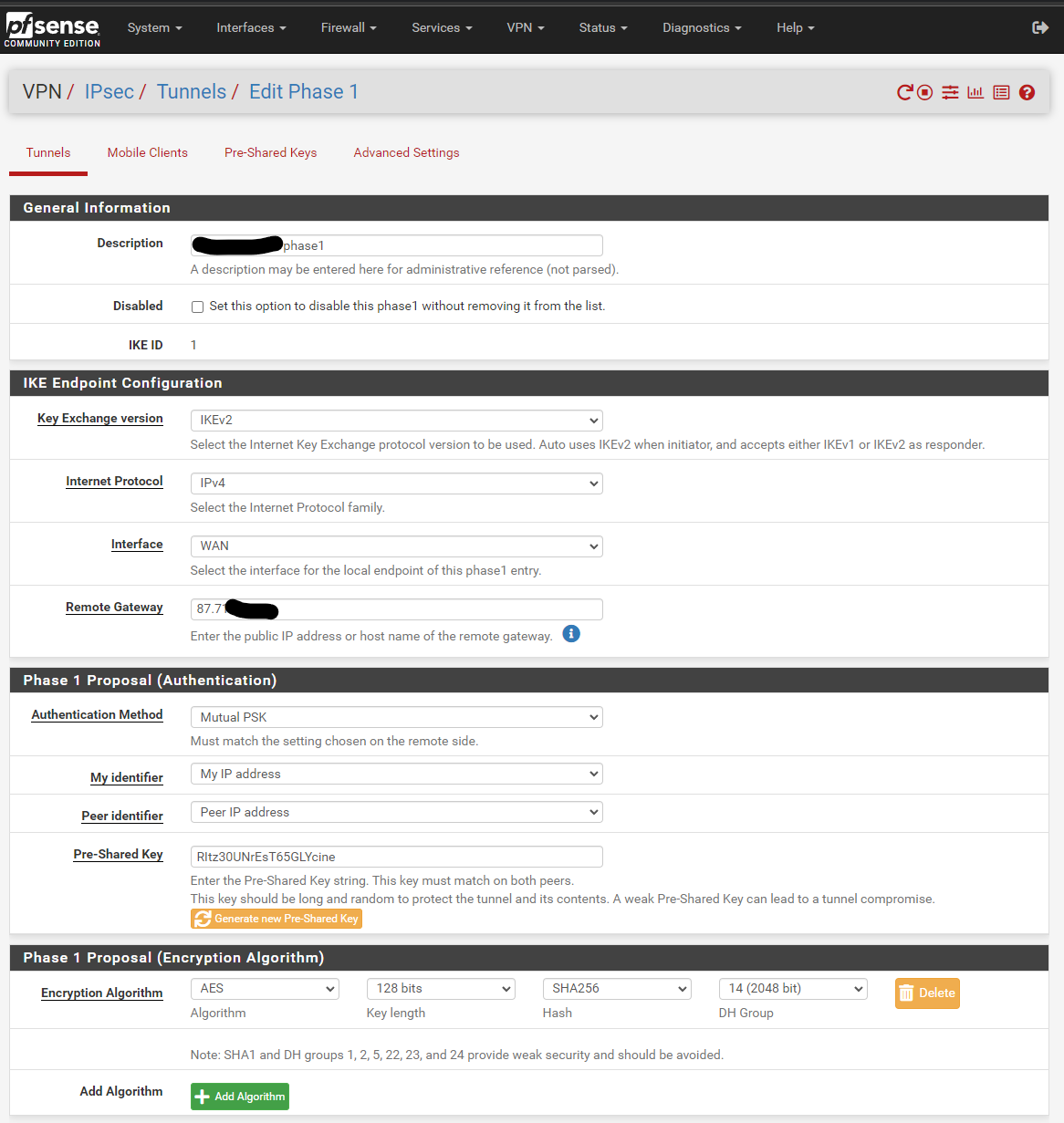
Phase 2:
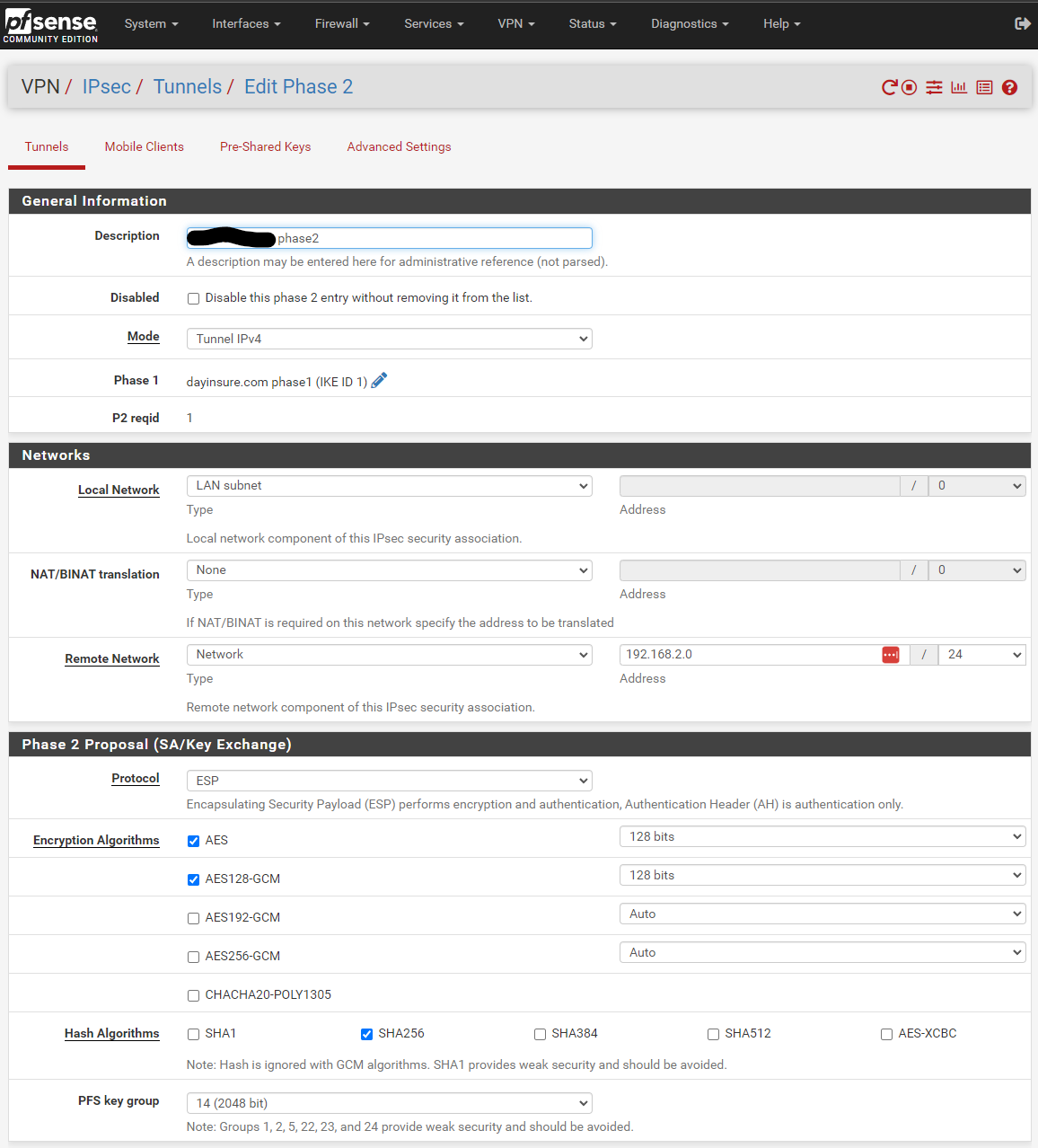
What I noticed was strange was the auto VPN rules didn't work, they were blocking the traffic so I added these:
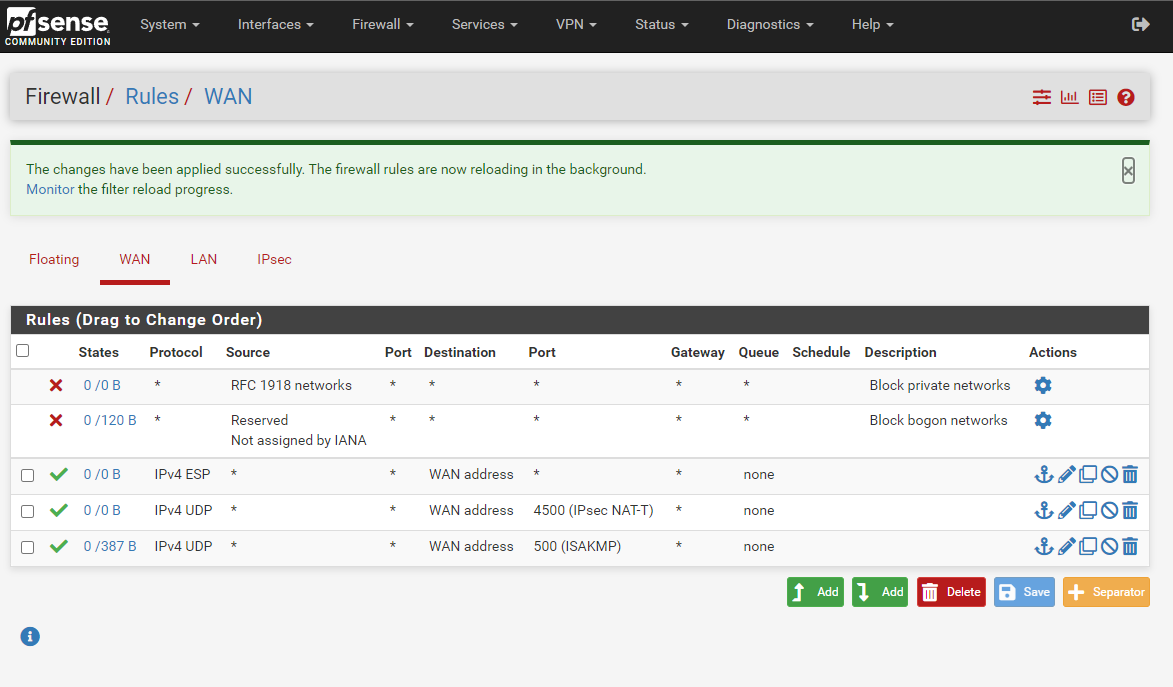
Which then allowed communication, where it previously just timed out. Should it point to the WAN address?Nov 24 14:57:49 charon 26204 11[IKE] <con1|6> activating IKE_AUTH task
Nov 24 14:57:49 charon 26204 11[IKE] <con1|6> activating IKE_CERT_POST task
Nov 24 14:57:49 charon 26204 11[IKE] <con1|6> activating IKE_CONFIG task
Nov 24 14:57:49 charon 26204 11[IKE] <con1|6> activating IKE_AUTH_LIFETIME task
Nov 24 14:57:49 charon 26204 11[IKE] <con1|6> activating IKE_ESTABLISH task
Nov 24 14:57:49 charon 26204 11[IKE] <con1|6> activating CHILD_CREATE task
Nov 24 14:57:49 charon 26204 11[IKE] <con1|6> initiating IKE_SA con1[6] to 82.69.x.x
Nov 24 14:57:49 charon 26204 11[IKE] <con1|6> IKE_SA con1[6] state change: CREATED => CONNECTING
Nov 24 14:57:49 charon 26204 11[CFG] <con1|6> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Nov 24 14:57:49 charon 26204 11[CFG] <con1|6> sending supported signature hash algorithms: sha256 sha384 sha512 identity
Nov 24 14:57:49 charon 26204 11[ENC] <con1|6> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Nov 24 14:57:49 charon 26204 11[NET] <con1|6> sending packet: from 82.71.x.x[500] to 82.69.x.x[500] (464 bytes)
Nov 24 14:57:49 charon 26204 11[NET] <con1|6> received packet: from 82.69.x.x[500] to 82.71.x.x[500] (36 bytes)
Nov 24 14:57:49 charon 26204 11[ENC] <con1|6> parsed IKE_SA_INIT response 0 [ N(NO_PROP) ]
Nov 24 14:57:49 charon 26204 11[IKE] <con1|6> received NO_PROPOSAL_CHOSEN notify error
Nov 24 14:57:49 charon 26204 11[CFG] <con1|6> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Nov 24 14:57:49 charon 26204 11[IKE] <con1|6> IKE_SA con1[6] state change: CONNECTING => DESTROYINGThey're both on 2.7.1, updated earlier today. Any help, pointers or advice would be greatly appreciated as I'm lost for things to try. They're on the default settings now just to try eliminate any mismatches.
Thanks,
Ant
-
@anthony-breen U don't need to open ports in your WANs for IPSEC, pfsense once u setup the connection, he will open port 500/4500, this case just in necesary for ovpn and wg.
About your issue, if u have 2 pfsense for the p2p, try add more algo in phase1.
Regards.
-
@periko Hello,
Thanks for the reply, I have tried adding additional P1 alog's but I still get the same error
Nov 27 10:04:46 charon 59062 09[NET] <48> received packet: from 82.71.x.x[500] to 82.69.x.x[500] (508 bytes)
Nov 27 10:04:46 charon 59062 09[ENC] <48> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Nov 27 10:04:46 charon 59062 09[CFG] <48> looking for an IKEv2 config for 82.69.x,x...82.71.x.x
Nov 27 10:04:46 charon 59062 09[CFG] <48> ike config match: 0 (%any...127.0.0.1 IKEv1/2)
Nov 27 10:04:46 charon 59062 09[CFG] <48> ike config match: 0 (82.69.x.x...87.71.x.x IKEv2)
Nov 27 10:04:46 charon 59062 09[IKE] <48> no IKE config found for 82.69.x.x...82.71.x.x, sending NO_PROPOSAL_CHOSEN
Nov 27 10:04:46 charon 59062 09[ENC] <48> generating IKE_SA_INIT response 0 [ N(NO_PROP) ]
Nov 27 10:04:46 charon 59062 09[NET] <48> sending packet: from 82.69.x.x[500] to 82.71.x.x[500] (36 bytes)
Nov 27 10:04:46 charon 59062 09[IKE] <48> IKE_SA (unnamed)[48] state change: CREATED => DESTROYINGI thought the same about the auto rules, will disable the manual ones I've created & try again...




Thanks,
Ant
-
@anthony-breen If are trying to work with other brand, add more algo in phase 1 and phase 2, if u don't have the doc where u can see what algo he need u need to do reverse eng. Add more, maybe he is searching for less secure algorithms.
The only issue is that if u are in pfsense 2.7.x and they request less secure algorithms, U will be not be able to make work.