WAN requiring root CA to be installed for internet access
-
@reqman said in WAN requiring root CA to be installed for internet access:
For better or worse, a decision has been made to automatically inspect https traffic (security / DLP reasons have been cited). The end result is that a government provided root cert should be installed on all internet facing (gov) systems.
You'll be needing what's discussed here : Forum > Home pfSense Packages > Cache/Proxy - it's called Squid (I guess).
For starters, read some posts in that part of the forum.
Read also Deprecation of Squid Add-On Package For pfSense Software
-
@Gertjan I don't has anything to do with proxy.. he wants pfsense to trust the cert signed by his gov CA when pfsense checks to see if there is an upgrade at https://upgrade.netgate.com - I know thats the not the right url ;)
Because its not going to be the actual cert from netgate.. His gov is doing mitm.
You should be able to add the CA to the trusted certs that freebsd trusts.
-
@reqman said in WAN requiring root CA to be installed for internet access:
automatically inspect https traffic
He want to inspect (TLS) packets.
-
@Gertjan said in WAN requiring root CA to be installed for internet access:
He want to inspect (TLS) packets.
Yeah but not on his end - upstream in the network the gov is doing it.
-
@johnpoz you're da man!
@johnpoz said in WAN requiring root CA to be installed for internet access:
You should be able to add the CA to the trusted certs that freebsd trusts.
Can it be done from the GUI? Any info will be appreciated.
-
@reqman should be yeah, not sure if available on 2.6?? But on my 23.09 here, this checkbox should do what your asking. You would import your gov CA, and since added to the os trust, when pfsense checks for packages, updates this would accept your gov mitm cert they issue for the fqdn used.
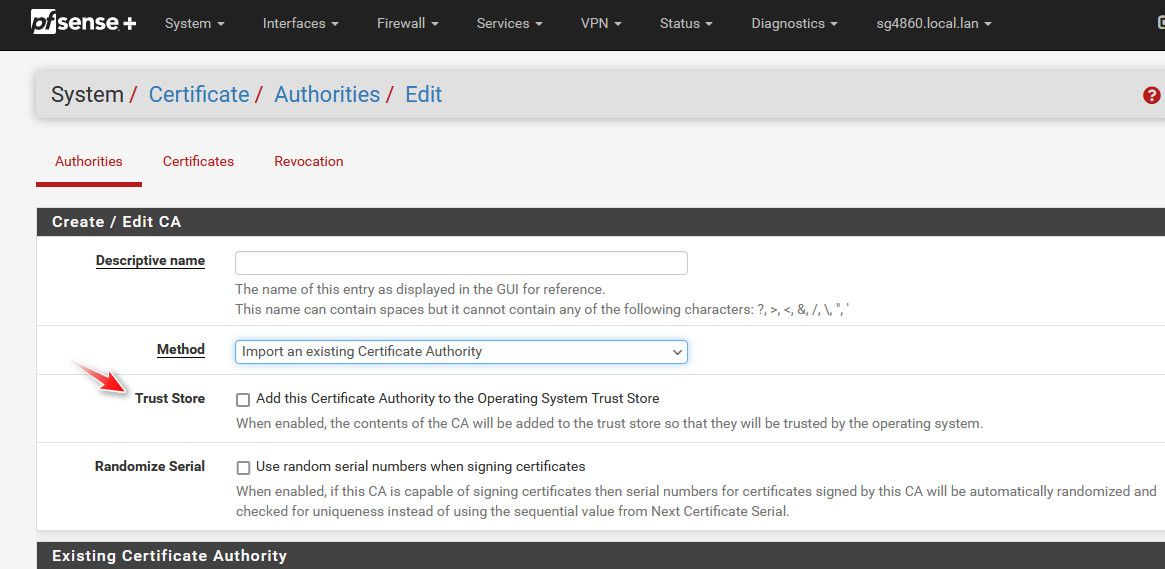
-
You can just set the check box when you import the CA cert:
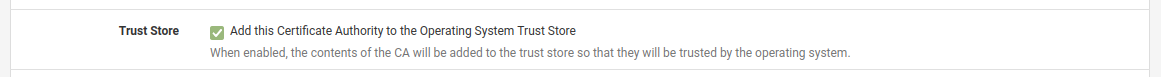
Edit: Ooops took too long to reply. What he said.

Also, yes, that option is in 2.6. But you should still upgrade.
-
Well, on 2.6.0 the screen is a bit different:
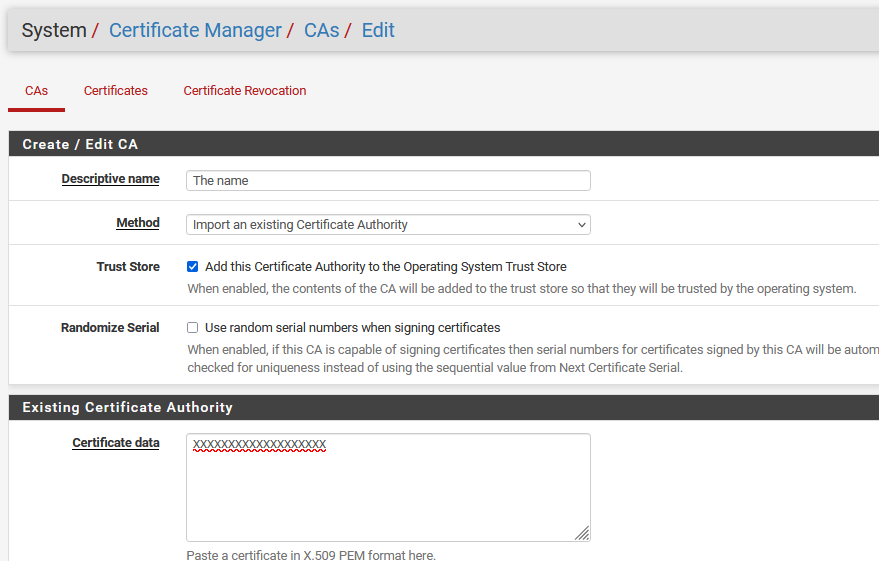
The upload went just fine:
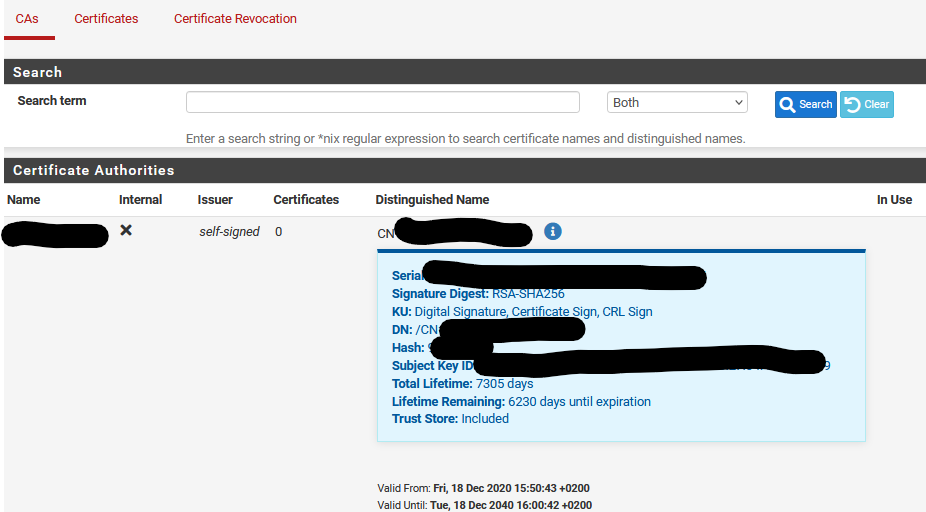
However, trying to even check for updates fails, with a reference to the cert:
>>> Updating repositories metadata... Updating pfSense-core repository catalogue... Certificate verification failed for /DC=local/DC=gov/DC=xxx/CN=xxx-SPECIAL-SubCA 34372419584:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_0-main/sources/FreeBSD-src-RELENG_2_7_0/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /DC=local/DC=gov/DC=xxx/CN=xxx-SPECIAL-SubCA 34372419584:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_0-main/sources/FreeBSD-src-RELENG_2_7_0/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /DC=local/DC=gov/DC=xxx/CN=xxx-SPECIAL-SubCA 34372419584:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_0-main/sources/FreeBSD-src-RELENG_2_7_0/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /DC=local/DC=gov/DC=xxx/CN=xxx-SPECIAL-SubCA 34372419584:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_0-main/sources/FreeBSD-src-RELENG_2_7_0/crypto/openssl/ssl/statem/statem_clnt.c:1921: pkg-static: https://pkg01-atx.netgate.com/pfSense_v2_7_0_amd64-core/meta.txz: Authentication error -
You may have to add the proxy explicitly to allow that to work:
https://docs.netgate.com/pfsense/en/latest/config/advanced-misc.html#proxy-supportTry running
pkg-static -d updateto get more error output though. -
@stephenw10 said in WAN requiring root CA to be installed for internet access:
You may have to add the proxy explicitly to allow that to work:
https://docs.netgate.com/pfsense/en/latest/config/advanced-misc.html#proxy-supportHmm, use it to support the normal update mechanism I suppose, right? I could try that I suppose, but I'd rather do the update manually via ISO, if that is possible.
Try running
pkg-static -d updateto get more error output though.Sure:
DBG(1)[27251]> pkg initialized Updating pfSense-core repository catalogue... DBG(1)[27251]> PkgRepo: verifying update for pfSense-core DBG(1)[27251]> PkgRepo: need forced update of pfSense-core DBG(1)[27251]> Pkgrepo, begin update of '/var/db/pkg/repo-pfSense-core.sqlite' DBG(1)[27251]> Request to fetch pkg+https://pkg.pfsense.org/pfSense_v2_7_0_amd64-core/meta.conf DBG(1)[27251]> opening libfetch fetcher DBG(1)[27251]> Fetch > libfetch: connecting DBG(1)[27251]> Fetch: fetching from: https://pkg00-atx.netgate.com/pfSense_v2_7_0_amd64-core/meta.conf with opts "i" Certificate verification failed for /DC=local/DC=gov/DC=xxx/CN=xxx-SPECIAL-SubCA 34372419584:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_0-main/sources/FreeBSD-src-RELENG_2_7_0/crypto/openssl/ssl/statem/statem_clnt.c:1921: DBG(1)[27251]> Fetch: fetching from: https://pkg00-atx.netgate.com/pfSense_v2_7_0_amd64-core/meta.conf with opts "i" Certificate verification failed for /DC=local/DC=gov/DC=xxx/CN=xxx-SPECIAL-SubCA 34372419584:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_0-main/sources/FreeBSD-src-RELENG_2_7_0/crypto/openssl/ssl/statem/statem_clnt.c:1921: DBG(1)[27251]> Fetch: fetching from: https://pkg00-atx.netgate.com/pfSense_v2_7_0_amd64-core/meta.conf with opts "i" Certificate verification failed for /DC=local/DC=gov/DC=xxx/CN=xxx-SPECIAL-SubCA 34372419584:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_0-main/sources/FreeBSD-src-RELENG_2_7_0/crypto/openssl/ssl/statem/statem_clnt.c:1921: DBG(1)[27251]> Request to fetch pkg+https://pkg.pfsense.org/pfSense_v2_7_0_amd64-core/meta.txz DBG(1)[27251]> opening libfetch fetcher DBG(1)[27251]> Fetch > libfetch: connecting DBG(1)[27251]> Fetch: fetching from: https://pkg00-atx.netgate.com/pfSense_v2_7_0_amd64-core/meta.txz with opts "i" Certificate verification failed for /DC=local/DC=gov/DC=xxx/CN=xxx-SPECIAL-SubCA 34372419584:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_0-main/sources/FreeBSD-src-RELENG_2_7_0/crypto/openssl/ssl/statem/statem_clnt.c:1921: DBG(1)[27251]> Fetch: fetching from: https://pkg00-atx.netgate.com/pfSense_v2_7_0_amd64-core/meta.txz with opts "i" Certificate verification failed for /DC=local/DC=gov/DC=xxx/CN=xxx-SPECIAL-SubCA 34372419584:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_0-main/sources/FreeBSD-src-RELENG_2_7_0/crypto/openssl/ssl/statem/statem_clnt.c:1921: DBG(1)[27251]> Fetch: fetching from: https://pkg00-atx.netgate.com/pfSense_v2_7_0_amd64-core/meta.txz with opts "i" Certificate verification failed for /DC=local/DC=gov/DC=xxx/CN=xxx-SPECIAL-SubCA 34372419584:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_0-main/sources/FreeBSD-src-RELENG_2_7_0/crypto/openssl/ssl/statem/statem_clnt.c:1921: pkg-static: https://pkg00-atx.netgate.com/pfSense_v2_7_0_amd64-core/meta.txz: Authentication error -
Hmm, it would interesting to see what the cert the proxy is sending shows as when pfSense tries to access it.
But just reinstalling 2.7.1 will work fine as long as you don't need to install pkgs.
-
@stephenw10 my apologies for delaying to reply, suffering from the not-having-enough-free-time syndrome.
Which would be the safest way to upgrade my installation to 2.7.1? Fresh install from ISO and import saved config? Have an ISO mounted and launch a script of some sort? Other?
-
@reqman said in WAN requiring root CA to be installed for internet access:
Have an ISO mounted and launch a script of some sort?
If your pfSense is a VM, yes.
Reboot the pfSense VM machine, and is should boot from the ISO? where the pfSense installer takes over.
Another classic one : No VM, so prepare a USB drive. See pfSense documentation about how to create one. Use "etcher" as told.
Boot from the USB drive : the installer takes over etc.If the installer finds an already extiing partion with the (old) 2.6.0) installed, it will use the config for the new setup.
If not, no issue neither, just use your daily backup of the config file.
Just finish the install with a minimal setup like : define LAN and WAN. Now the GUI is available from LAN. Login, and in the GUI, import the config. Have it reboot.
Done. -
M mt_onsemi referenced this topic on
-
@Gertjan took me almost a year to schedule some downtime for this device. Downloaded the compressed ISO of 2.7.2 (iso filename is netgate-installer-v1.0-RC-amd64-20240919-1435), mounted it to my pfsense 2.6 CE VM, enabled booting from the VM CD and fired it up. For a moment I did not understand that 2.7,2 actually booted TBH, until I noticed the "+" next to the pfsense logo :) . Did not know what to select at boot so I just let it take its path.
Unfortunately, a bit later the VM shutted down by itself. Tried the exact same procedure, but no go.
FYI host is a free ESX 5.5 hypervisor on an Xeon E5506 (yes, I know it's old).
Seems I'll be stuck with 2.6.0 :)
-
@reqman said in WAN requiring root CA to be installed for internet access:
FYI host is a free ESX 5.5 hypervisor on an Xeon E5506 (yes, I know it's old).
That 'ESX 5.5' is probably the issue right now.
Check for yourself : install pfSense 2.7.2 on ESX 5.5 hypervisor and you won't find anybody talking about "5.5". It's version 8 or 7 if you have to.Ok to keep old software. But mixing new stuff (pfSense 2.7.2 uses FreeBSD 14) on old stuff, is like installing windows 11 on a PC without a TPM : you can (probably) force it, but it needs uncommon knowledge to do so.
-
You can enable the CE repos in the Net installer and install 2.7.2 from there.
Or you can install 2.7.2 using the legacy ISO image.
But, yes, you may find that ESXi version is too old to support it.
-
@reqman said in WAN requiring root CA to be installed for internet access:
Unfortunately, a bit later the VM shutted down by itself. Tried the exact same procedure, but no go.
The problem is likely the
vmxnet3driver. Change your virtual machine to use thee1000NIC driver and try again. You will take a performance hit using thee1000virtual driver, but that should let the newer pfSense boot and run.I had this problem with a generic FreeBSD VM I had a couple of years ago. The newer FreeBSD versions have an updated
vmxnet3driver that apparently does not play well with older ESXi versions. Changing my VM to use thee1000virtual NIC allowed it to boot and run. If the NIC driver is the problem, the machine crashes and reboots when the NIC driver loads. So, the machine starts booting and looks good, but then crashes when the NIC driver is loaded. -
@Gertjan said in WAN requiring root CA to be installed for internet access:
Ok to keep old software. But mixing new stuff (pfSense 2.7.2 uses FreeBSD 14) on old stuff, is like installing windows 11 on a PC without a TPM : you can (probably) force it, but it needs uncommon knowledge to do so.
I know, but the iron does not support 6.0 and later.
@bmeeks said in WAN requiring root CA to be installed for internet access:
@reqman said in WAN requiring root CA to be installed for internet access:
Unfortunately, a bit later the VM shutted down by itself. Tried the exact same procedure, but no go.
The problem is likely the
vmxnet3driver. Change your virtual machine to use thee1000NIC driver and try again. You will take a performance hit using thee1000virtual driver, but that should let the newer pfSense boot and run.Very useful info, thanks. Will give it a try, when I find some time to reschedule this experiment.