NetGate 4100 + No IPv6 on WAN :(
-
Thank you stephen for your reply.
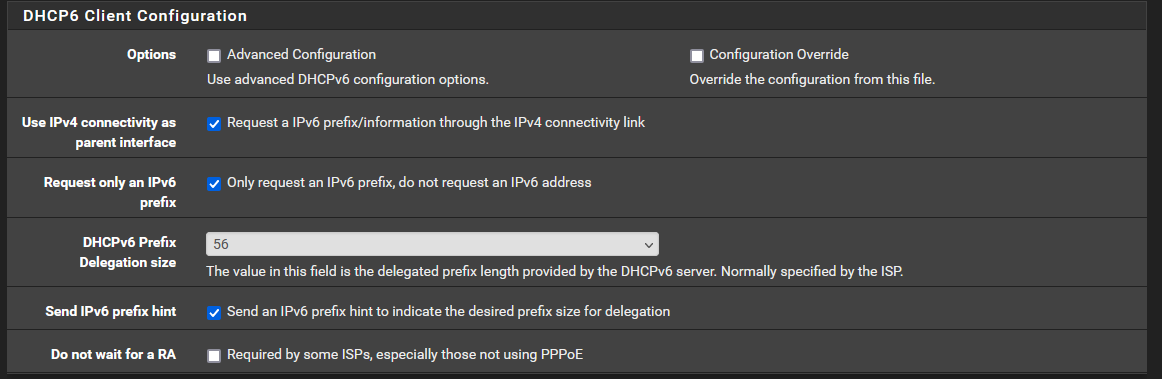
Ok, i understand, that makes sense of course. I thought by setting up prefix delegation my wan interface would get an ipv6 regardless.
With that being said, i tried it with disabling "Request only an IPv6 prefix" also and i won`t get an IPv6 address that way either
but i guess thats to be expected, given the fact that my isp specifically mentioned dhcp-pd for how they assign ipv6.
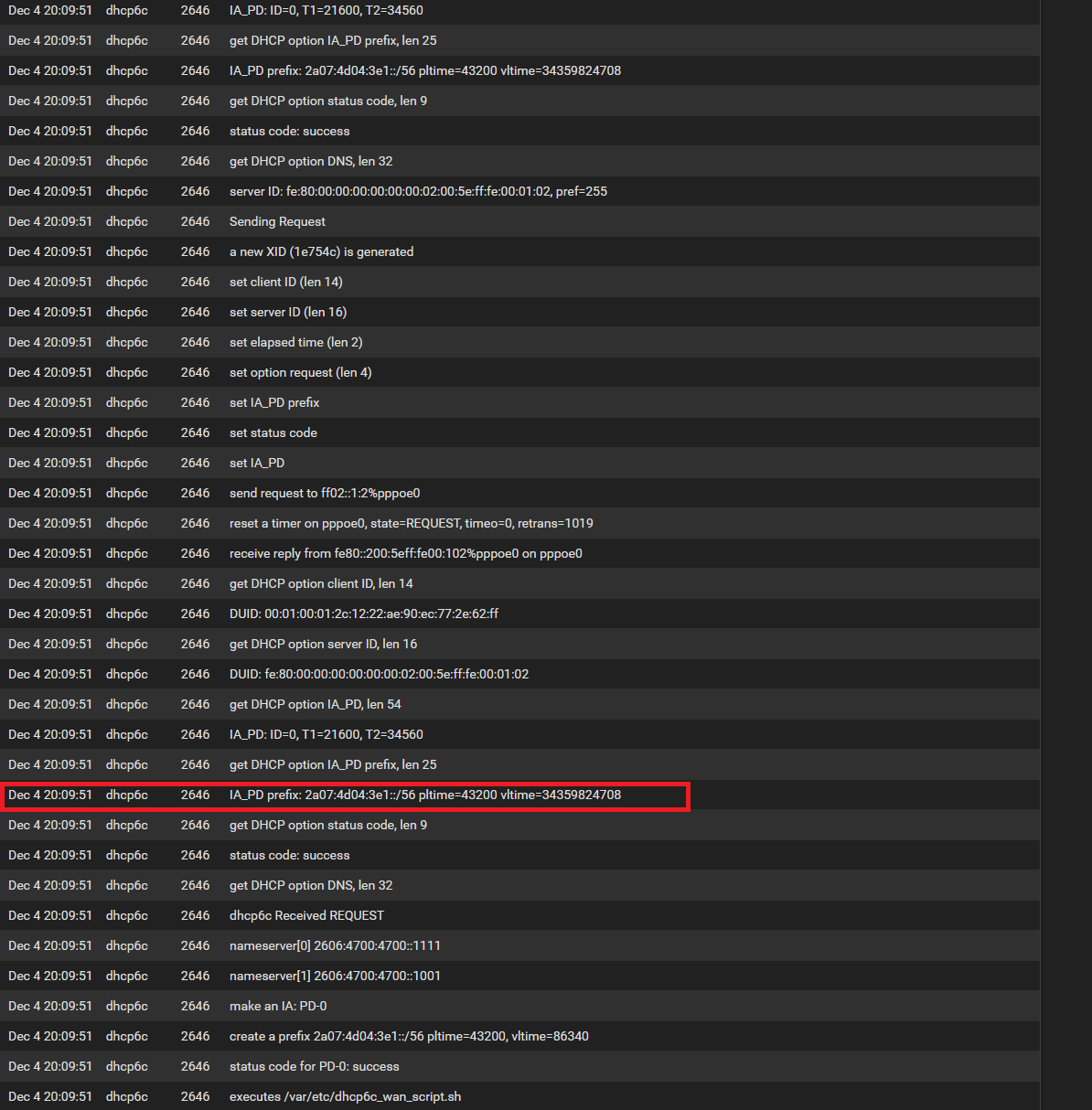
So from the logfiles it seems to work fine then, but tracking wan on one of lan interfaces doesn't do anything.edit:
I was able to get it to work.
What was the solution? Well, just setting up "track interface" on one of my lan interfaces really didn't change anything and no lan interface got any ipv6 assigned to it. But when i re-applied the configuration to my wan interface or in other words re-dial the pppoe connection all my lan interfaces received an ipv6 address. Thank you guys for all your help, that pointed me in the right direction for sure :)Is it common practice that my ISP wont assign any IPv6 to my WAN interface directly, so i bascially just have a CGN IPv4 now on the interface or can this be considered a little bit of an oddity? (So far i always have seen IPv6 addresses being assigned to WAN as well)
-
Yup prefix delegation only is quite common. My ISP here in the UK does exactly that.
-
But couldn't that become an issue? With the CGNAT IPv4, i bascially cannot reach the IPv4 directly from the outside (well, i could by using a VPN gateway, i guess but you know what i mean) IPv6 would come in handy then, cause those addresses are not behind a carrier grade nat, but with the prefix delegation from my ISP that isn't an option, did i get that right?
-
With IPv6 every IP in the PD is publicly routable. You will have a public v6 IP on every interface to set to trackv6 and could access any of them externally as long as firewall rules on WAN allow it.
-
i am sorry to follow up on that and maybe i just don't get it but in the case of PD, my WAN interface itself won't get an IPv6 address for an ISP, that just hands out the prefix delegation and no IPv6 addresses directly, right?
Isn't that kind of a downside compared to an ISP that assigns the IPv6 directly and maybe also assigns PD? How else can i get a public routable IPv6 on WAN when constraint with a CGN IPv4 address? -
@FreeYourMind said in NetGate 4100 + No IPv6 on WAN :(:
How else can i get a public routable IPv6 on WAN when constraint with a CGN IPv4 address?
You don't need one. With IPv6 there is no NAT. Every IPv6 address in the /56 prefix assigned to you by your ISP is a public routable address.
The ISP has registered that prefix range as belonging to them, so all other routers on the Internet know to send traffic destined for an IPv6 address in your prefix delegation to your ISP's gateway. Your ISP then internally routes that traffic to you because they have your specific connection information (your modem ID and any addressing information they assigned to your account).
So, consider a client on your LAN with an IPv6 address from the routable /56 assigned to you. That client connects out to some IPv6 site. pfSense routes that from your LAN to your WAN. The WAN interface sees that the destination is "not a local network", so it sends it to the next-hop default gateway. It does this using the link-local IPv6 address on your WAN interface and talking directly to the link-local IPv6 address on your ISP's default gateway assigned to you. Thus outbound traffic is automatically routed without your WAN needing a public IP.
Now consider unsolicited inbound traffic such as your remote laptop attempting to connect back home over a VPN. You will need to know the IPv6 address of your intended target on your LAN. You either put in that IPv6 address as the destination, or you configure some type of IPv6 dynamic DNS client so you can use a hostname from the public internet. Your client sends a packet to the IPv6 client address on your LAN. The Internet routers recognize the IPv6 address is part of a /56 prefix delegated by your ISP and your ISP is the routing authority for that prefix, so they route the request to your ISP's Internet gateway. Your ISP then routes the request internally on their network to your connection because they know what prefix they assigned to you. If your WAN firewall rules allow the inbound traffic, then it connects.
What makes this possible with IPv6 is the removal of NAT. Your local LAN clients can talk directly out to Internet hosts using their native IPv6 address (no NAT needed). Your IPv4 connection is totally out of the picture. It does not matter about the CGNAT for IPv6 traffic only. That last bold point is key. You cannot make any kind of IPv4 connection from the Internet because the CGNAT is in the way. You would need to use IPv6, and that means any Wi-Fi or other remote network you were using to connect back home would need to be IPv6 capable. Unfortunately, very few are these days (at least in the US). I suspect there are very few public Wi-Fi hotspots with full IPv6 connectivity.
-
thanks you bmeeks, for giving a bit more background information about this.
But lets stick with your example for a moment and lets say the VPN is not running behind your pfsense, but instead running on the firewall itself, which is a common configuration, right?So lets assume i wanna connect with my remote laptop to OpenVPN running on pfsense, how would i do that, if we stick with the example you were talking about? I might overlook something but i obviously can't connect to the CGNAT IPv4 from the outside and given the fact that WAN doesn't have its own IPv6 address, i can't do that either.
So instead of binding OpenVPN to my WAN address which is usually something you would do with NAT in IPv4, you would now just bind OpenVPN to one of your lan interfaces instead?
-
You could connect to any IPv6 address on the firewall because they are all publicly routable. So you could run a VPN server on the LAN address for example and connect to that from some remote location. You would only need firewall rules on WAN to allow access to it.
-
Yeah, i was confused about that part a bit i guess. I am still trapped in that NAT mindset of having one public available address on the firewall itself, usually bound to WAN and i never came across a configuration where WAN only has a link local IPv6 instead of a public routable IPv6.
Thank you guys for your patience and for taking the time to shed some light on my issue. We live and learn. :)
-
@FreeYourMind said in NetGate 4100 + No IPv6 on WAN :(:
thanks you bmeeks, for giving a bit more background information about this.
But lets stick with your example for a moment and lets say the VPN is not running behind your pfsense, but instead running on the firewall itself, which is a common configuration, right?So lets assume i wanna connect with my remote laptop to OpenVPN running on pfsense, how would i do that, if we stick with the example you were talking about? I might overlook something but i obviously can't connect to the CGNAT IPv4 from the outside and given the fact that WAN doesn't have its own IPv6 address, i can't do that either.
So instead of binding OpenVPN to my WAN address which is usually something you would do with NAT in IPv4, you would now just bind OpenVPN to one of your lan interfaces instead?
"Yes" is the short answer as @stephenw10 has already described. Your "destination address" for the outside client attempting to connect back in would be the LAN interface's IPv6 address on your firewall. But you would still need the correct rules on your WAN to allow that traffic to pass through, because it will be coming in from your default gateway's link-local IPv6 address to the link-local IPv6 address on your WAN interface. Your WAN link-local address is just a "transit network" between your delegated /56 prefix and the ISP's network core.