Problem to port forwarding - Wireguard and PfSense
-
Greetings,
I'm trying to solve a problem urgently. I have a virtualized cloud server where a VM with PFSENSE on board has been installed. This instance is connected to the external network via public IP (from now on identified as 1.1.1.1) issued by the provider connected to an interface called WAN and generates an internal network 192.168.1.0/24 connected to an interface called LAN with various connected client.
I therefore installed Wireguard on the machine as the purpose is to map external ports on the WAN IP (1.1.1.1) (e.g. 10203) and nat on another port (e.g. 1880) but this mapping must not be carried out on a ip of the local network (192.168.1.0/24) but made to a connected Wireguard client (e.g. 172.16.16.3/32).
The goal therefore is to create a Wireguard server with several clients where these clients host HTTP servers on board which are then reached from the server's WAN under mapped ports.I have therefore made many attempts but I have reached the point of:
- the VPN is a split tunnel so the client must navigate with its own IP address
- the peer's allowed IP is set to the server's Wireguard network (e.g. 172.16.16.0/24) so that all VPN clients can communicate with each other
- the peer (client) reaches the pfsense
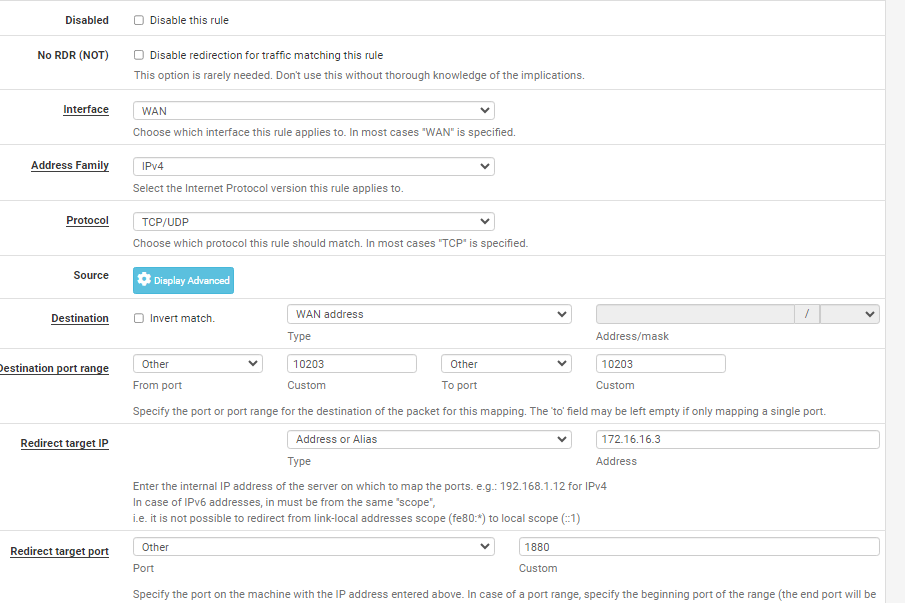
- there is a NAT rule (as in the photo)
- if set to allowedips 0.0.0.0/0 the peer navigates under the server's internet network and in turn the port is mapped correctly
Can you help me solve the problem?
-
@meletechlab what is the problem?
-
The problem is that when the VPN is used as a split tunnel, the port is not mapped to the VPN client
-
@meletechlab
The clients might not be able to handle this properly. They will send responses to their default gateway.You can only workaround this by masquerading the forwarded traffic with the wg interface IP on pfSense. But then you loose the information of the origin source IP.
-
There is an online service called PortMap that performs the same services I wanted. Obviously, since I cannot rely on external services due to the sensitivity of the data that passes through the tunnel, I need to replicate this condition. Consider that I am not interested in the source of the call but only that the traffic to that specific port is established with the client. Each client has a different port
-
@meletechlab said in Problem to port forwarding - Wireguard and PfSense:
There is an online service called PortMap that performs the same services I wanted.
You mean this one in conjunction with VPN, I assume.
There are the same conditions true for this. Either the VPN server is used as default gateway or the provider masquerades the traffic.Since you don't want to use the VPN as default route and don't care about the source IP, you can go with masquerading.
-
Could you possibly help me with masquerading as I have never used it and I don't want to cause any trouble. How can I apply a rule?
-
I tried to test it but it didn't work. I would like all traffic coming from outside on port 10203 to be forwarded to port 1880 on IP 172.16.16.3/32 (vpn client). Obviously 10203 must also be opened
-
@meletechlab
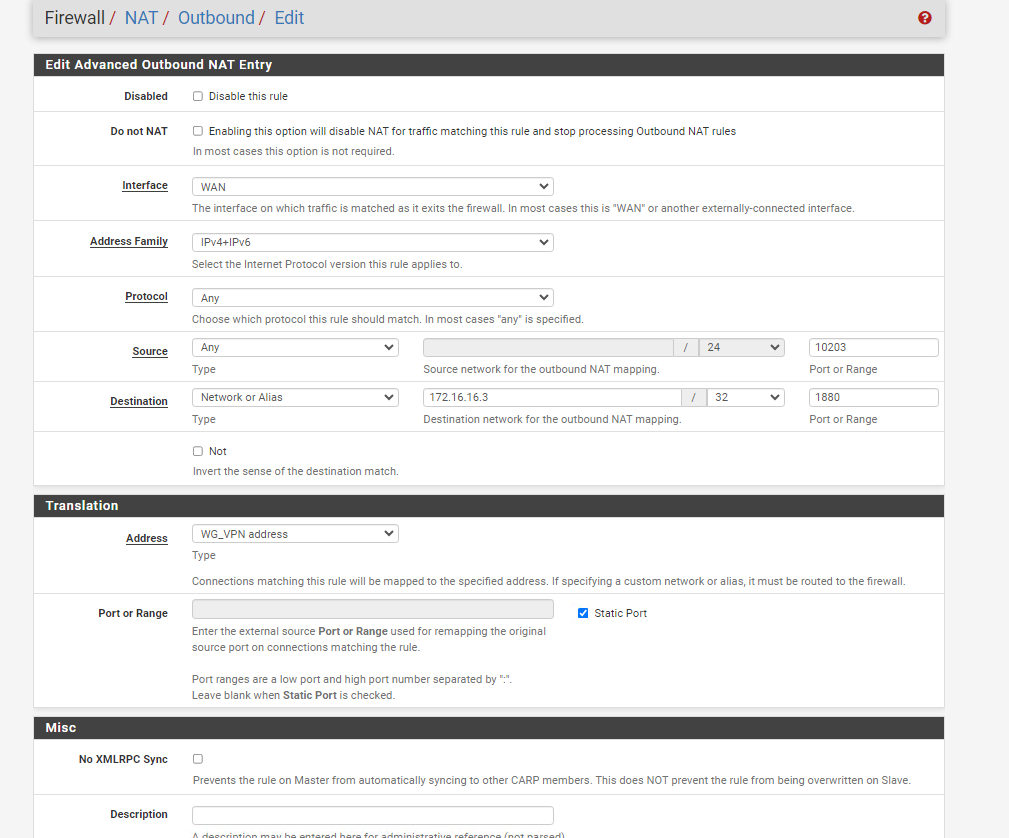
You have to do this on the VPN interface.Assuming you have already assigned an interface to the Wireguard instance, add an outbound NAT rule to this interface
interface: <wg instance interface>
source: any
source port: any (it's most likely dynamic)
destination: 172.16.16.3
dest. port: 1880 (if you want to limit the rule to the needed port)
translation: interface addressEnsure that the outbound NAT is set to hybrid mode.
-
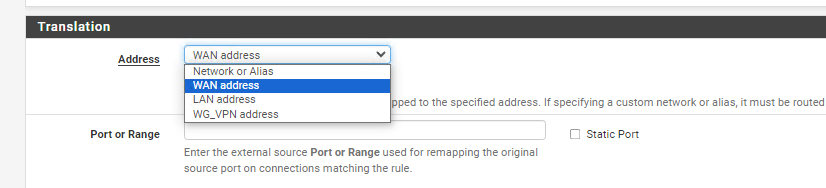
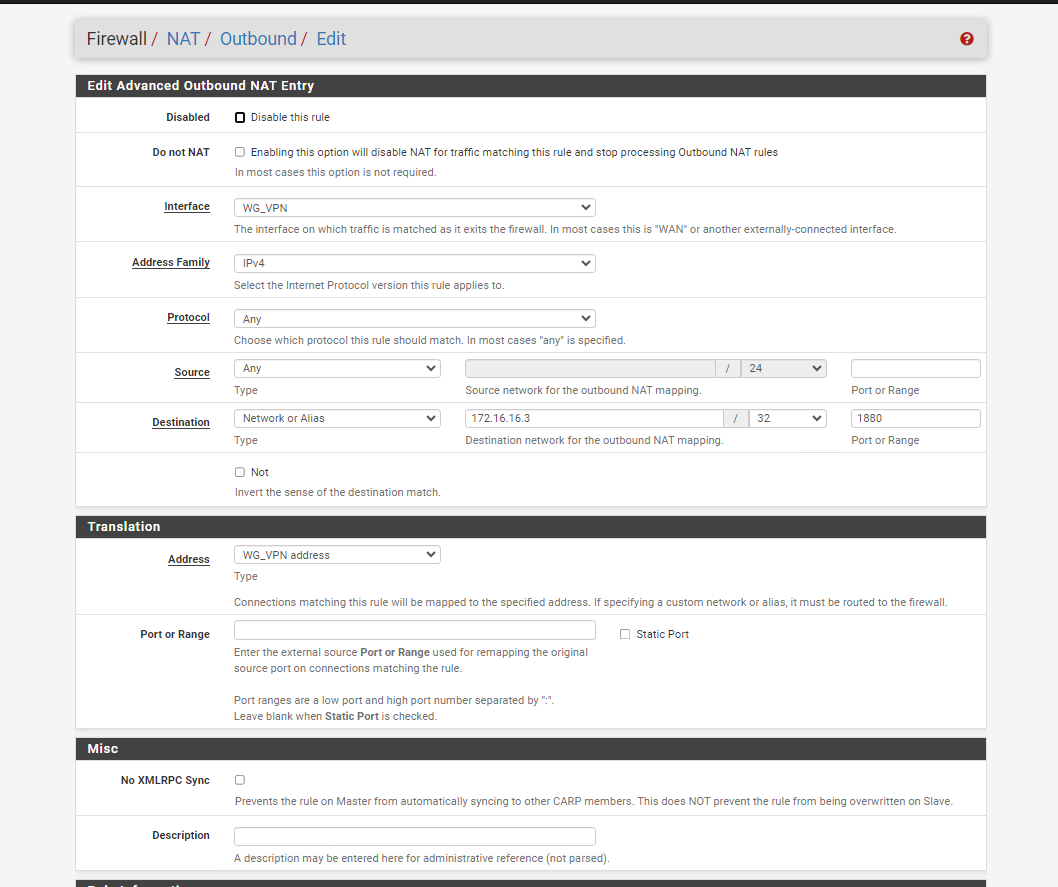
@viragomann Into translation section "interface address" it is not present, I only find the ones you see in the photo where WG_VPN is the VPN interface
-
I first created a port forwarding from the WAN network (therefore public) to the IP of the wireguard client from the external 10203 to the internal 1880
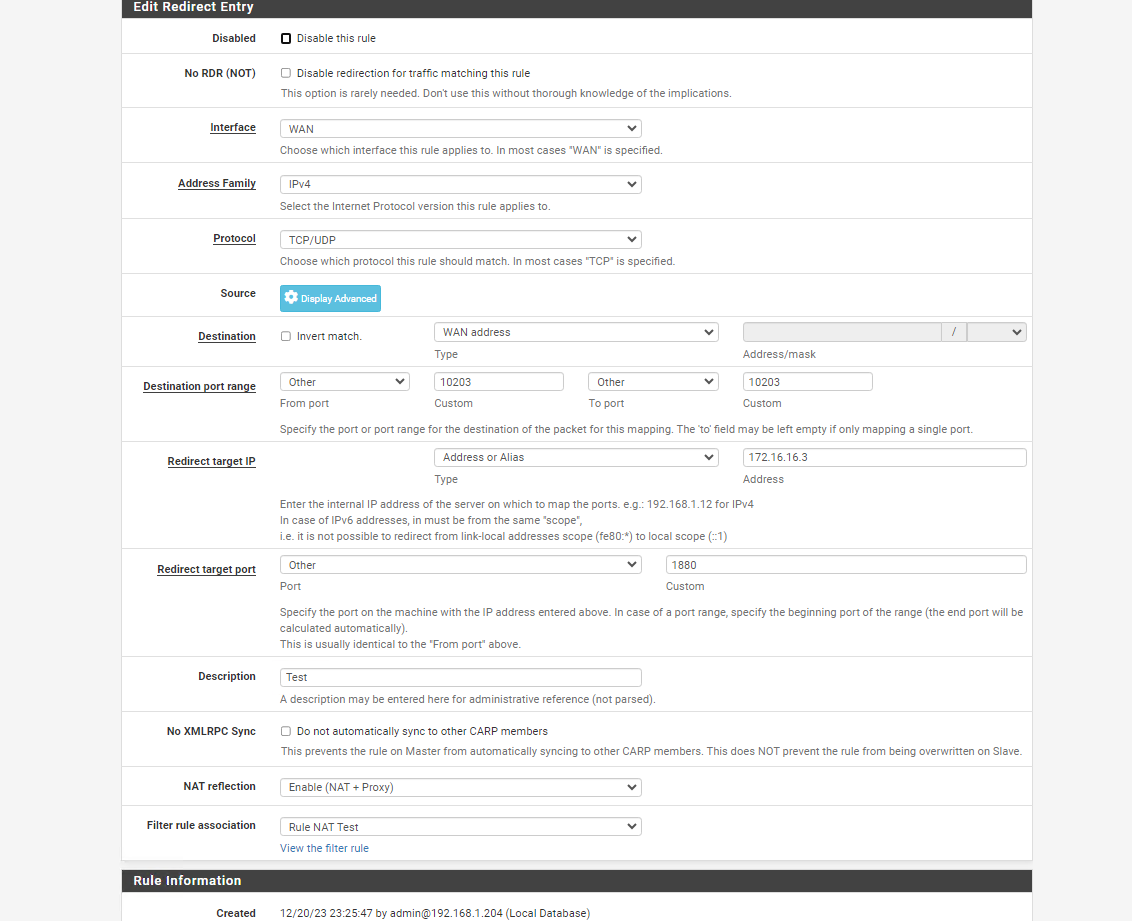
Then I created the rule according to your directions
-
@meletechlab said in Problem to port forwarding - Wireguard and PfSense:
Into translation section "interface address" it is not present, I only find the ones you see in the photo where WG_VPN is the VPN interface
Okay, that's new to me. So select the WG_VPN address then.
I first created a port forwarding from the WAN network (therefore public) to the IP of the wireguard client from the external 10203 to the internal 1880
Then I created the rule according to your directions
Seems all correct.
But no success? -
@viragomann Nothing, I also tried changing the translation address to various addresses but no results. the VPN client is correctly connected to the Wireguard and from there I reach the PFSense interface
-
@meletechlab
Sniff the traffic to find out where it Stücks.
On pfSense use Diagnostic > Packet capture to sniff the traffic on the VPN interface. If there is nothing check the WAN.