unable to upgrade
-
route -n get 8.8.8.8
route to: 8.8.8.8
destination: 0.0.0.0
mask: 0.0.0.0
gateway: 27.33.208.13
fib: 0
interface: vmx1
flags: <UP,GATEWAY,DONE,STATIC>
recvpipe sendpipe ssthresh rtt,msec mtu weight expire
0 0 0 0 1500 1 0 -
Try running:
pkg-static -d4 update -
@stephenw10 DBG(1)[64467]> Request to fetch pkg+https://pfsense-plus-pkg.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/meta.txz
DBG(1)[64467]> opening libfetch fetcher
DBG(1)[64467]> Fetch > libfetch: connecting
DBG(1)[64467]> Fetch: fetching from: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/meta.txz with opts "i4"
DBG(1)[64467]> Fetch: fetching from: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/meta.txz with opts "i4"
DBG(1)[64467]> Fetch: fetching from: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/meta.txz with opts "i4"
pkg-static: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/meta.txz: No route to host
repository pfSense has no meta file, using default settings
DBG(1)[64467]> Request to fetch pkg+https://pfsense-plus-pkg.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/packagesite.pkg
DBG(1)[64467]> opening libfetch fetcher
DBG(1)[64467]> Fetch > libfetch: connecting
DBG(1)[64467]> Fetch: fetching from: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/packagesite.pkg with opts "i4"
DBG(1)[64467]> Fetch: fetching from: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/packagesite.pkg with opts "i4"
DBG(1)[64467]> Fetch: fetching from: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/packagesite.pkg with opts "i4"
pkg-static: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/packagesite.pkg: No route to host
DBG(1)[64467]> Request to fetch pkg+https://pfsense-plus-pkg.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/packagesite.txz
DBG(1)[64467]> opening libfetch fetcher
DBG(1)[64467]> Fetch > libfetch: connecting
DBG(1)[64467]> Fetch: fetching from: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/packagesite.txz with opts "i4"
DBG(1)[64467]> Fetch: fetching from: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/packagesite.txz with opts "i4"
DBG(1)[64467]> Fetch: fetching from: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/packagesite.txz with opts "i4"
pkg-static: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v23_05_1_amd64-pfSense_plus_v23_05_1/packagesite.txz: No route to host
Unable to update repository pfSense
Error updating repositories! -
@stephenw10 Had to cut the top bit as the whole thing was being flagged as spam sorry
-
Hmm, I note that when you ran the traceroute above it only worked when you sourced it from the LAN IP.
Is that still true? Or for ping, does it also work only when sourcing from some address other than WAN?
Do you have any manual outbound NAT rules that are breaking traffic from the WAN address?
Unfortunately you can't set a source address for pkg to test it that way.
-
@stephenw10 said in unable to upgrade:
Hmm, I note that when you ran the traceroute above it only worked when you sourced it from the LAN IP.
Is that still true? Or for ping, does it also work only when sourcing from some address other than WAN?
Do you have any manual outbound NAT rules that are breaking traffic from the WAN address?
I do happen to have some outbound NAT rules:
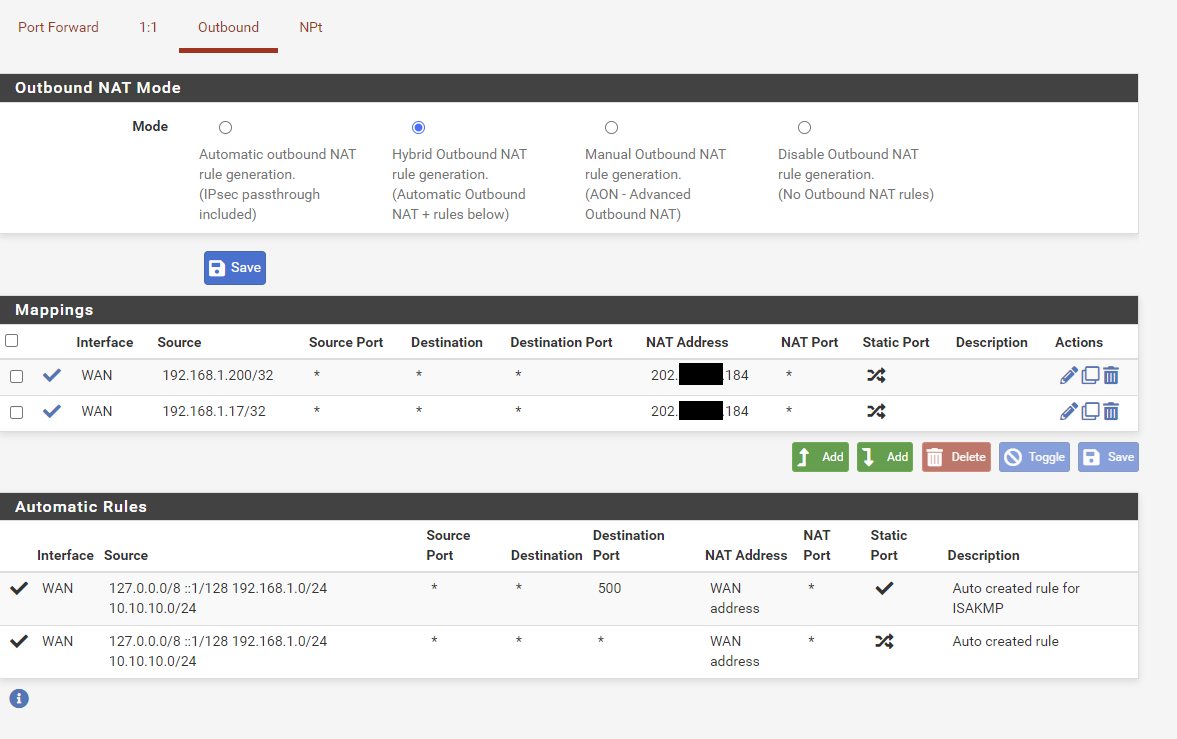
i've got a feeling it could be that automatic rule, but I can't see how to disable it for testing.
pinging from both LAN and WAN addresses looks to work, but if I don't specify a source address it fails:
[23.05-RELEASE][admin@pfSense.domain.com.au]/root: ping -S 192.168.1.1 8.8.8.8
PING 8.8.8.8 (8.8.8.8) from 192.168.1.1: 56 data bytes
64 bytes from 8.8.8.8: icmp_seq=0 ttl=58 time=12.512 ms
64 bytes from 8.8.8.8: icmp_seq=1 ttl=58 time=12.505 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=58 time=12.503 ms
64 bytes from 8.8.8.8: icmp_seq=3 ttl=58 time=12.516 ms
64 bytes from 8.8.8.8: icmp_seq=4 ttl=58 time=12.521 ms
^C
--- 8.8.8.8 ping statistics ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 12.503/12.511/12.521/0.007 ms
[23.05-RELEASE][admin@pfSense.domain.com.au]/root: ping -S 27.xxx.xxx.14 8.8.8.8
PING 8.8.8.8 (8.8.8.8) from 27.33.208.14: 56 data bytes
64 bytes from 8.8.8.8: icmp_seq=0 ttl=58 time=12.565 ms
64 bytes from 8.8.8.8: icmp_seq=1 ttl=58 time=12.653 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=58 time=12.571 ms
64 bytes from 8.8.8.8: icmp_seq=3 ttl=58 time=12.531 ms
^C
--- 8.8.8.8 ping statistics ---
4 packets transmitted, 4 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 12.531/12.580/12.653/0.045 ms
[23.05-RELEASE][admin@pfSense.domain.com.au]/root: ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8): 56 data bytes
^C
--- 8.8.8.8 ping statistics ---
6 packets transmitted, 0 packets received, 100.0% packet loss -
Hmm, that looks fine. The OBN rules look fine too.
Is the traceroute from the WAN IP still failing?Does ping succeed to 208.123.73.207?
-
@stephenw10 said in unable to upgrade:
Hmm, that looks fine. The OBN rules look fine too.
Is the traceroute from the WAN IP still failing?Does ping succeed to 208.123.73.207?
Looks like traceroute from WAN and LAN source works:
: traceroute -s 27.xxx.xxx.14 208.123.73.207
traceroute to 208.123.73.207 (208.123.73.207) from 27.33.208.14, 64 hops max, 40 byte packets
1 27-xxx-xxx-13.tpgi.com.au (27.xxx.xxx.13) 1.532 ms 1.479 ms 2.789 ms
2 AU-SA-3016-IPG-01-Eth-Trunk22.tpgi.com.au (203.221.244.9) 1.970 ms 2.038 ms 1.939 ms
3 adl-apt-pir-crt1-be200.tpgi.com.au (203.219.182.65) 23.529 ms
adl-apt-pir-crt1-be100.tpgi.com.au (203.219.182.1) 23.440 ms
adl-apt-pir-crt1-be200.tpgi.com.au (203.219.182.65) 23.463 ms
4 nme-sot-dry-crt1-be70.tpgi.com.au (203.219.107.189) 25.036 ms 24.067 ms
nme-sot-dry-crt1-Be30.tpgi.com.au (203.219.107.221) 24.080 ms
5 203-26-22-117.static.tpgi.com.au (203.26.22.117) 23.954 ms 24.461 ms 24.049 ms
6 203.29.134-68.tpgi.com.au (203.29.134.68) 26.134 ms
syd-apt-ros-int2-be100.tpgi.com.au (203.29.134.4) 28.094 ms
203.29.134-68.tpgi.com.au (203.29.134.68) 24.553 ms
7 hu0-4-0-0.rcr21.b001848-1.sjc01.atlas.cogentco.com (38.32.115.105) 177.766 ms 177.802 ms 177.735 ms
8 be2095.ccr22.sjc01.atlas.cogentco.com (154.54.3.137) 179.053 ms
be2063.ccr21.sjc01.atlas.cogentco.com (154.54.1.161) 178.474 ms 178.575 ms
9 be3144.ccr41.sjc03.atlas.cogentco.com (154.54.5.102) 173.509 ms
be3142.ccr41.sjc03.atlas.cogentco.com (154.54.1.194) 172.368 ms
be3144.ccr41.sjc03.atlas.cogentco.com (154.54.5.102) 173.303 ms
10 ae-18.edge9.SanJose1.Level3.net (4.68.110.125) 174.074 ms 173.508 ms 173.479 ms
11 * * *
12 ZAYO-BANDWI.ear5.Dallas1.Level3.net (4.14.49.2) 212.587 ms 212.477 ms 212.406 ms
13 ae0.aus01-mls-dc-core-a.infr.zcolo.com (64.20.229.158) 213.189 ms 212.638 ms
ae0.aus01-mls-dc-core-b.infr.zcolo.com (64.20.229.166) 212.639 ms
14 net66-219-34-194.static-customer.corenap.com (66.219.34.194) 213.151 ms 212.605 ms
net66-219-34-198.static-customer.corenap.com (66.219.34.198) 212.364 ms
15 fw1-zcolo.netgate.com (208.123.73.4) 214.268 ms 214.108 ms 214.640 ms
16 * * *
17 * * *
18 * * *
19 * * *and
/root: traceroute -s 192.168.1.1 208.123.73.207
traceroute to 208.123.73.207 (208.123.73.207) from 192.168.1.1, 64 hops max, 40 byte packets
1 27-xxx-xxx-13.tpgi.com.au (27.xxx.xxx.13) 1.452 ms 1.359 ms 1.323 ms
2 AU-SA-3016-IPG-01-Eth-Trunk22.tpgi.com.au (203.221.244.9) 2.055 ms 1.893 ms 1.853 ms
3 adl-apt-pir-crt1-be100.tpgi.com.au (203.219.182.1) 23.415 ms
adl-apt-pir-crt2-be200.tpgi.com.au (203.219.182.66) 23.551 ms 23.530 ms
4 nme-sot-dry-crt1-be70.tpgi.com.au (203.219.107.189) 24.018 ms 23.940 ms 24.074 ms
5 203-26-22-117.static.tpgi.com.au (203.26.22.117) 24.176 ms 24.164 ms
203-26-22-121.static.tpgi.com.au (203.26.22.121) 23.965 ms
6 203.29.134-68.tpgi.com.au (203.29.134.68) 24.792 ms
syd-apt-ros-int2-be100.tpgi.com.au (203.29.134.4) 26.806 ms 26.629 ms
7 hu0-4-0-0.rcr21.b001848-1.sjc01.atlas.cogentco.com (38.32.115.105) 177.726 ms 177.931 ms 178.168 ms
8 be2095.ccr22.sjc01.atlas.cogentco.com (154.54.3.137) 178.903 ms
be2063.ccr21.sjc01.atlas.cogentco.com (154.54.1.161) 178.512 ms 178.734 ms
9 be3144.ccr41.sjc03.atlas.cogentco.com (154.54.5.102) 173.328 ms 173.400 ms
be3142.ccr41.sjc03.atlas.cogentco.com (154.54.1.194) 172.956 ms
10 ae-18.edge9.SanJose1.Level3.net (4.68.110.125) 186.714 ms 173.819 ms 177.050 ms
^Cbut if I don't select a source address:
traceroute 208.123.73.207
traceroute: findsaddr: failed to connect to peer for src addr selection.ping still failing unless I specifically select a source address:
[23.05-RELEASE][admin@pfSense.domain.com.au]/root: ping -S 192.168.1.1 208.123.73.207
PING 208.123.73.207 (208.123.73.207) from 192.168.1.1: 56 data bytes
64 bytes from 208.123.73.207: icmp_seq=0 ttl=50 time=212.896 ms
64 bytes from 208.123.73.207: icmp_seq=1 ttl=50 time=212.874 ms
64 bytes from 208.123.73.207: icmp_seq=2 ttl=50 time=212.919 ms
64 bytes from 208.123.73.207: icmp_seq=3 ttl=50 time=213.019 ms
^C
--- 208.123.73.207 ping statistics ---
4 packets transmitted, 4 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 212.874/212.927/213.019/0.055 ms
[23.05-RELEASE][admin@pfSense.domain.com.au]/root: ping -S 27.xxx.xxx.14 208.123.73.207
PING 208.123.73.207 (208.123.73.207) from 27.33.208.14: 56 data bytes
64 bytes from 208.123.73.207: icmp_seq=0 ttl=50 time=212.840 ms
64 bytes from 208.123.73.207: icmp_seq=1 ttl=50 time=212.865 ms
64 bytes from 208.123.73.207: icmp_seq=2 ttl=50 time=212.848 ms
64 bytes from 208.123.73.207: icmp_seq=3 ttl=50 time=213.043 ms
^C
--- 208.123.73.207 ping statistics ---
4 packets transmitted, 4 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 212.840/212.899/213.043/0.084 ms
[23.05-RELEASE][admin@pfSense.domain.com.au]/root: ping 208.123.73.207
PING 208.123.73.207 (208.123.73.207): 56 data bytes
^C
--- 208.123.73.207 ping statistics ---
6 packets transmitted, 0 packets received, 100.0% packet loss -
Hmm, so what address is it trying to use by default there then? Are there any addresses on the system you can set as source that fail?
-
@stephenw10 said in unable to upgrade:
Hmm, so what address is it trying to use by default there then? Are there any addresses on the system you can set as source that fail?
Not sure... I do have a /29 assigned to my service too which is in virtual IPs, but when I try and ping from one of them I get:
ping -S 202.xxx.xxx.185 8.8.8.8
ping: bind: Can't assign requested address -
I even just tried doing an outbound NAT for the firewall and it didn't seem to help
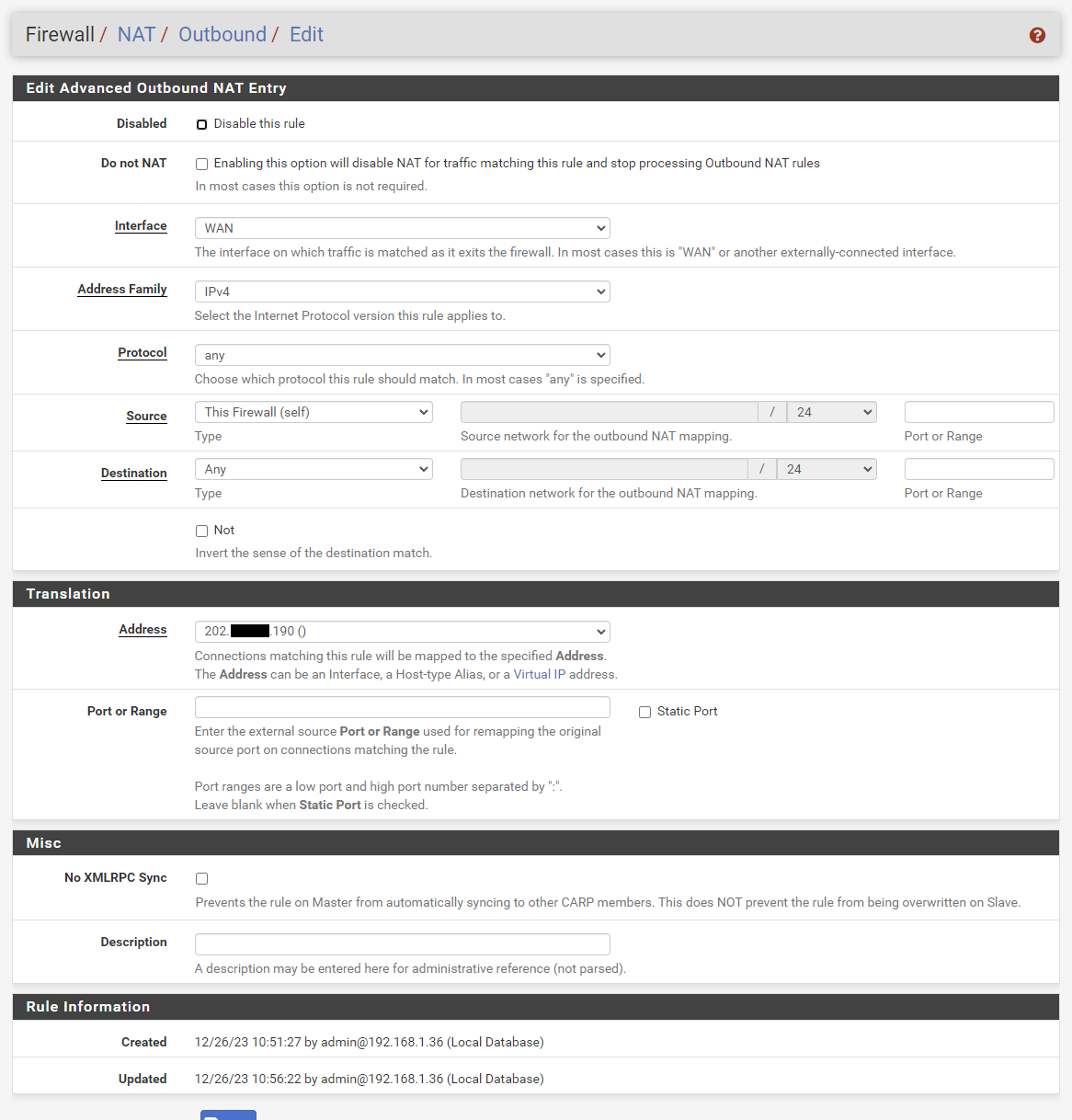
same thing when I try and ping out from it, 100% packet loss.