IPSec NAT IP not working
-
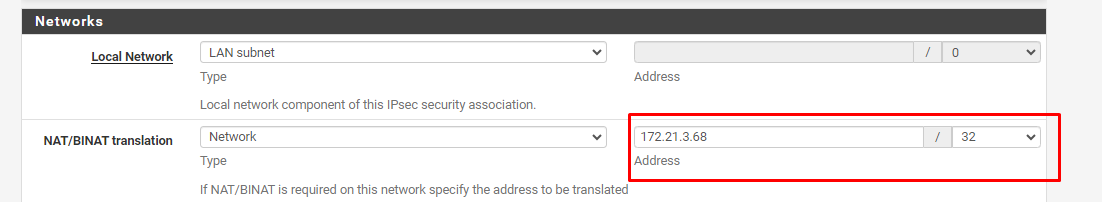
I have a IPSEC Tunnel that is configured to send packages to a NAT / BINAT IP
75134a43-8c6a-4cba-af13-869e35e494e6-image.png
As you can see, the NAT ip is 172.21.3.68
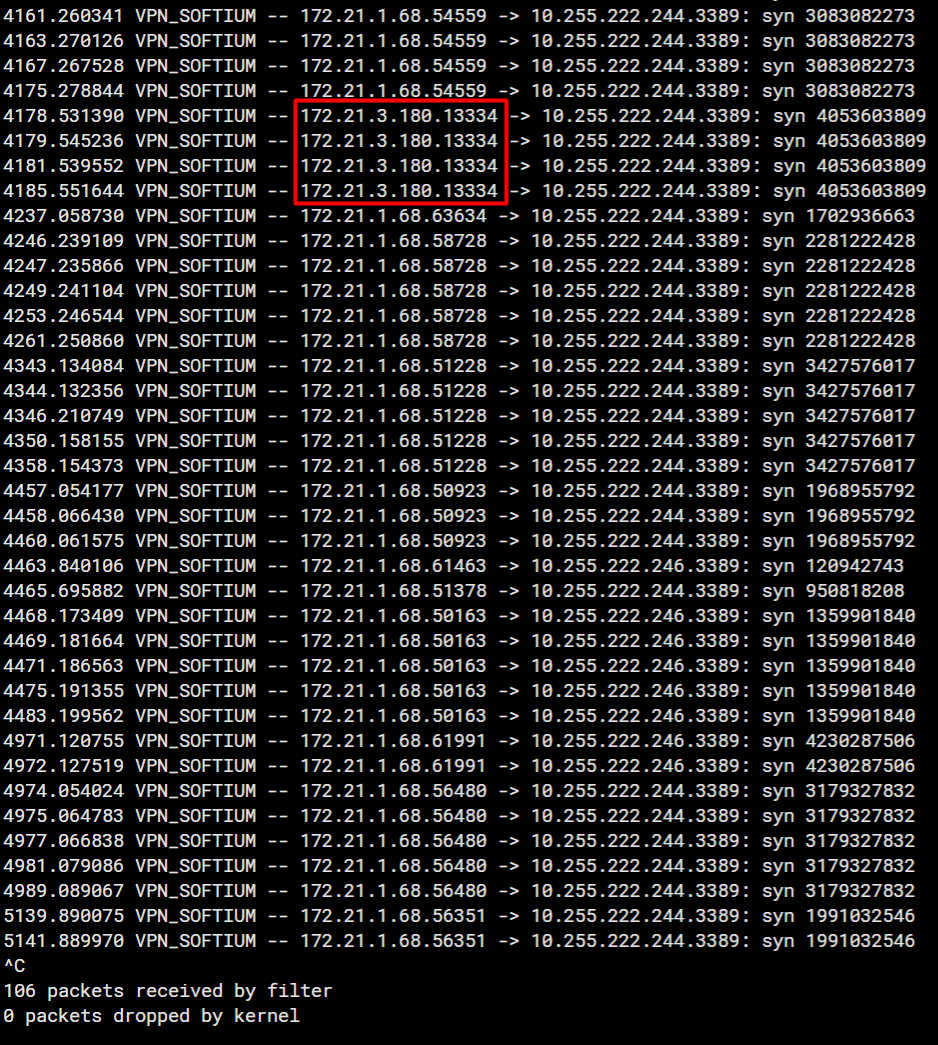
But, the Fortigate log shows that the IP that is sending the package is 172.21.1.68
4a9b5760-386a-4dac-b1be-7a90f5cd6af0-image.png
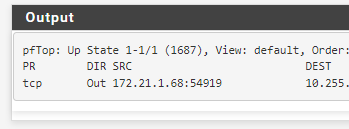
My pfSense logs shows the same thing, the actual IP that is sending the packages is different than the IP configured in the IPSEC
d57d4949-c79d-4fad-be2b-53cde528704d-image.png
Any help is greatly appreciated.
-
The images didn't load on the firts post...
Here it goes:
-
@luquinhasdainfra
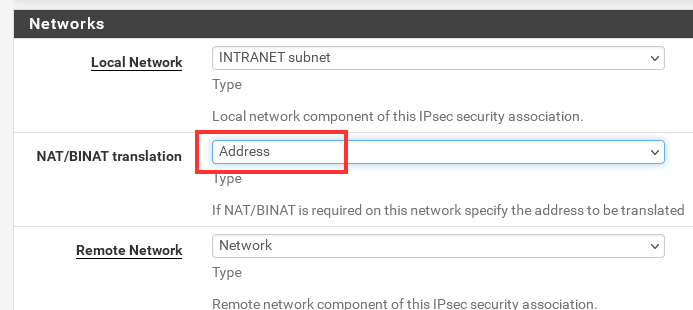
To nat to a single IP, pfSense gives you the type option "Address". So you should change this. However, I don't expect, that this makes a difference.Is this the only one phase 2 for this connection? If there are multiple please post the order.
-
@viragomann This is the only P2 connection,
The address IP is set as the first image shows, it is poiting to 172.21.3.68 but the connections are going through the ip 172.21.1.68
-
@luquinhasdainfra
I was talking about this option:
-
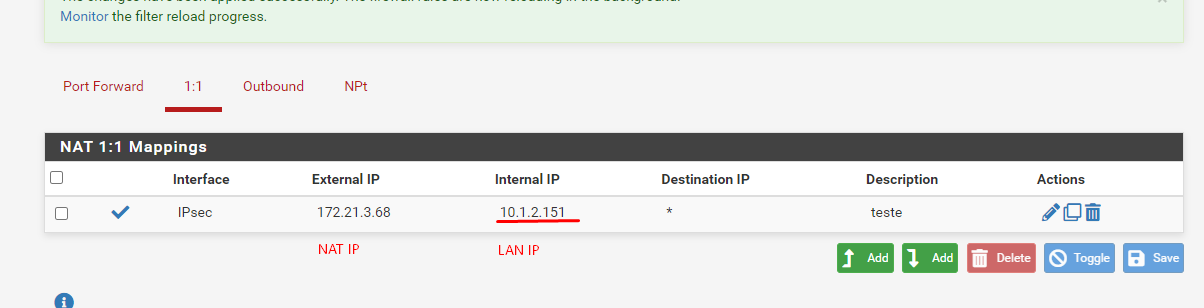
@viragomann I figured out how to configure it...
Actually, it needs a 1:1 NAT to work well. I don't understand why only this tunnel need this configuration.
Thank you for the replies, have a great day.
-
@luquinhasdainfra
Conventional NAT rules do not have any affect on policy-based IPSec traffic at all. You can use it for VTI, however. -
That's really strange, so...
When the 1:1 NAT is createad the IPSEC works fine, but without him it sends it to a wrong NAT IP,
I already checked all my rules and NAT, i never set the IPSEC or any rule / route to send it to the IP 172.21.1.68, instead, i configured the IPSEC to NAT it to 172.21.3.68
-
@luquinhasdainfra
Which device is the shown internal IP in the NAT 1:1 rule? Is it a device in the LAN or the pfSense interface IP?Basically you NAT rule should translate the source address of outbound traffic over IPSec from the stated internal IP to 172.21.3.68. But never heard, that this would work with a policy-based IPSec tunnel.
-
The internal IP in the 1:1NAT it's a computer from our LAN network