Internally route devices to WAN
-
No that would have only 9.100 resolving that.. Pretty sure I gave pretty good instructions and examples of it working in that post.
local.lan wouldn't be a vlan, that is the domain..
if a 192.168.9.100 IP did the query it would get back that 10.10.10.10 address
your access control would be the IP range of your devices, say 192.168.9.0/24 now any device coming back 192.168.9.x and asking for test.local.lan would get back 10.10.10.10
You prob want to change local-zone to domain.com
and your local-data would be the IP you want mail.domain.com to resolve to say 1.2.3.4 - whatever you wan IP is you want to send them too. -
@johnpoz so something like this?
server:
access-control-view: 192.168.20.0/24 IP of Laptop
view:
name: "mail" Name of Server
local-zone: "mail.domain.com"
local-data: "mail.domain..com. 90 IN A 10.10.10.10" IP of wan -
@VioletDragon not quite..
the zone is the domain.. domain.com
the local-data is correct if your wan IP was 10.10.10.10
And its not name of server, that is the name of the view your creating..
If your laptop has say IP address 192.168.20.x then it would resolve mail.domain.com to 10.10.10.10
-
@johnpoz So does this look correct? I have taken some info out.
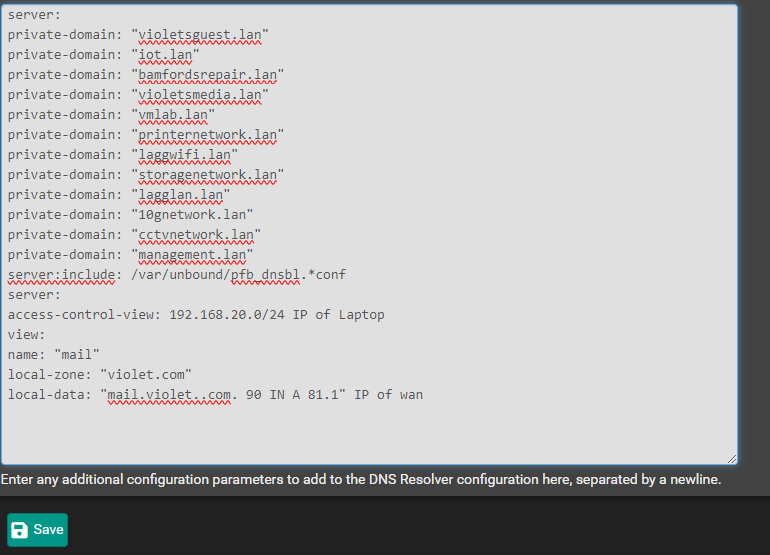
-
@VioletDragon take that 2nd server: out and you have ..com not sure if typo or just taking something out..
And you might want to up the TTL?? Or your going to get a lot of queries - 90 was just something I used in my example.
Oh and this line is wrong
access-control-view: 192.168.9.100/32 testview
In your above where you have IP of laptop, it would be mail which is the name of your view
Here
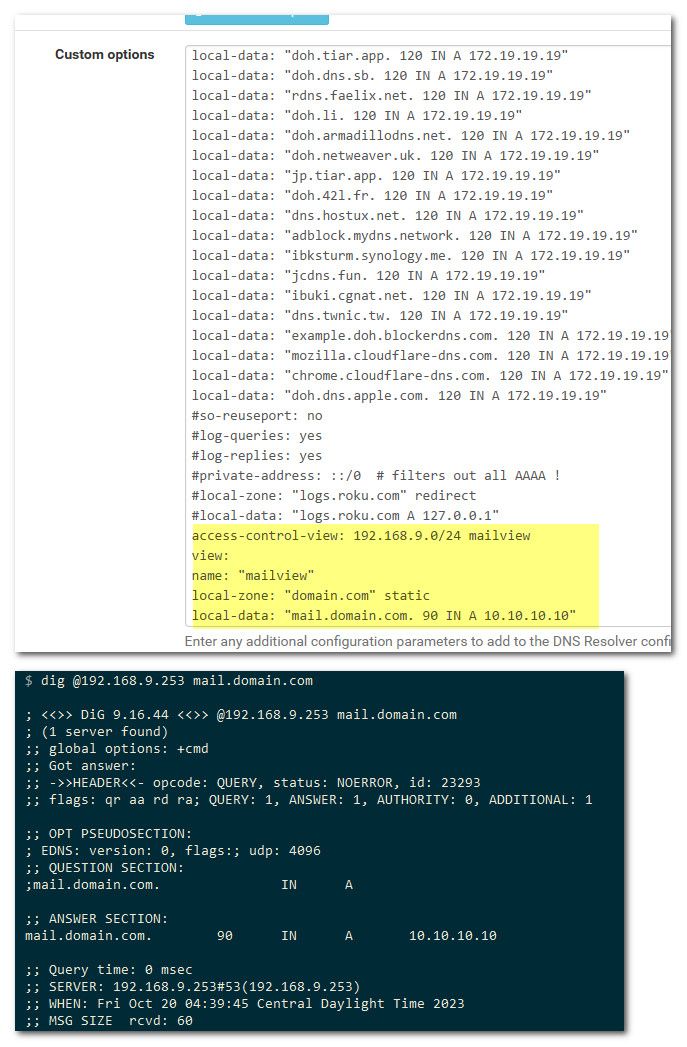
You forgot the zone type as well, do you look up anything else in domain.com - from external? If so then that would be transparent zone vs static zone, etc. But with a view don't think it matters.. But you have to set the zone type.
Here I moved it to the top of my custom options
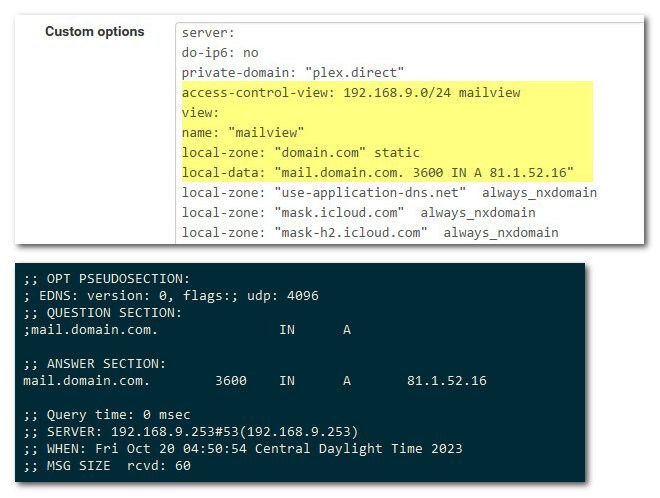
Set a different longer ttl and changed it what looks more like a public IP
-
@johnpoz I will give this ago and report back to you.
192.168.20.0/24 is the IP Range of the VLAN.
Regards
-
Right so if you want only the laptop to see that view you'd set a single IP there rather than the subnet.
-
@stephenw10 yeah that was my first example with the /32 - but pretty sure he has multiple mobile devices, etc. Vs handing out specific IPs to devices and listing all the ips that you want to use the view, using a cidr is simpler.. Unless of course you have IPs in that range that you don't want to see the view.
-
@stephenw10 I want multiple VLANs to see this, i.e Guest Network, LAN and WIFI network.
Regards
-
@johnpoz Just a quick question, how can you do this for multiple VLANs?
-
@VioletDragon just set the view for whatever source IPs you want be that a /24 or a /20 etc.. you can also create multiple views, etc. if you want some range of IPs to get this result, and some other range of IPs to get a different one, etc.
-
@johnpoz Yeah I have two VLANs one for Guest WI-FI and Private WI-FI. I am trying to figure out how to add those two into the views.
Regards
-
@VioletDragon well if your networks are next to each other or even if they are not just use a cidr that covers it..
For example if your networks were say 192.168.2.0/24 and 192.168.3.0/24 you could just a 192.168.2.0/23 which would include both of those networks.
If your networks are not adjacent you could still use a cidr to include them both.. Say you had
192.168.4.0/24 and 192.168.7.0/24 you could use a 192.168.0.0/21 to cover both of those - as long as you were not using any other network that falls under that cidr that you don't want to use the view.
I think you might be able to add multiple
access-control-view: 192.168.3.0/24 mailview
access-control-view: 192.168.7.0/24 mailview
access-control-view: 192.168.22.0/24 mailviewetc.. but I have not tested that specifically..
But I believe you can do that.. You could also just duplicate your view for your different network, call one mailviewA and the other mailviewB or something and then use your different access-control for each one, etc.
-
@johnpoz Is this what I have done correct ? 10.10.10.20/24 is the VLAN for the Private WIFI connection.
Sorry I had to put this project on halt due to work and Christmas. Hope you had a great Christmas.
Regards
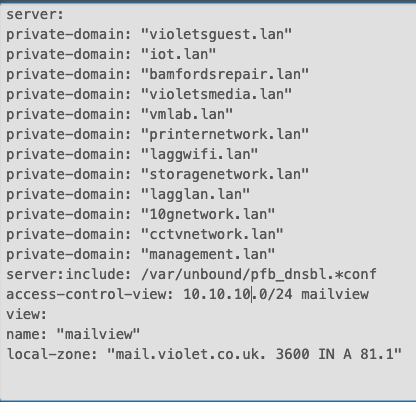
-
@VioletDragon if your client is on 10.10.10.0/24 then yeah any client would see that view 10.10.10.x or .y etc..
But your address is wrong a 81.1 is not a valid IP address you need 4 octets and see you have a " there at then end, did you just leave the rest of the IP off to post?
-
@johnpoz Yes I removed the rest of the WAN IP for security purposeses. Is this correct though?
-
@VioletDragon but you have your full IP posted in a image above in the thread? Or did I just make up that IP?
I don't see your local zone for the domain and local data for the actual record.
Just scroll up - I posted a very explicit example of how to do it.
-
@johnpoz That IP in the screenshot above isn't my IP.
-
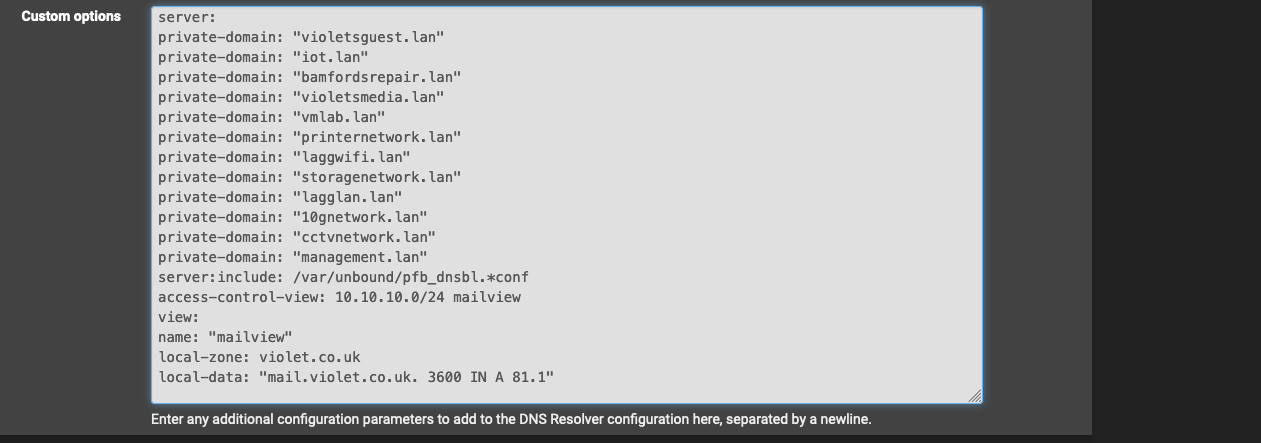
@johnpoz How does it look now?
-
@VioletDragon yeah that should work other than the invalid IP