Port Forwarding w/ OpenVPN Tunnel - What am I doing wrong?
-
Hi - Did some research here, and everything I am seeing makes me this this should work, but alas.. It does not.
Scenario:
- OpenVPN Tunnel to a new VPN Provider (AirVPN)
- Oubound Traffic works, connection successful & stable.
- Client's are part of an alias group & clients in the alias group connect to problem to the outside.
- Inbound traffic on a specified port, to a machine in the alias group, via VPN interface appears to be blocked. Nothing in the firewall logs. I do see traffic in the Packet Capture attempting to send traffic to me.
Thank you in advance for any insight! I suspect that I may have a conflict with my general drop rule, but also not sure on what specifics I could be missing.
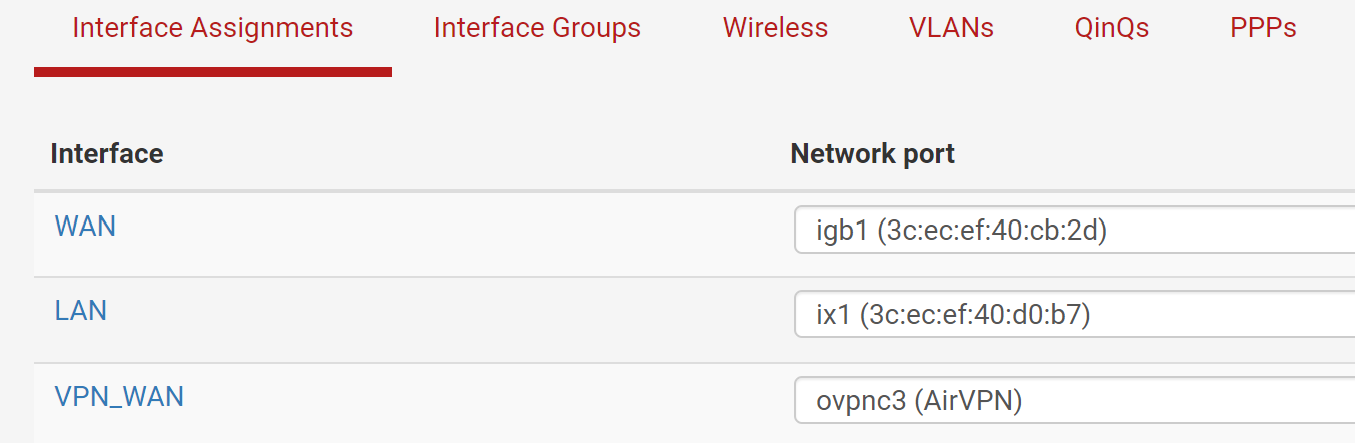
Interfaces:
Aliases:
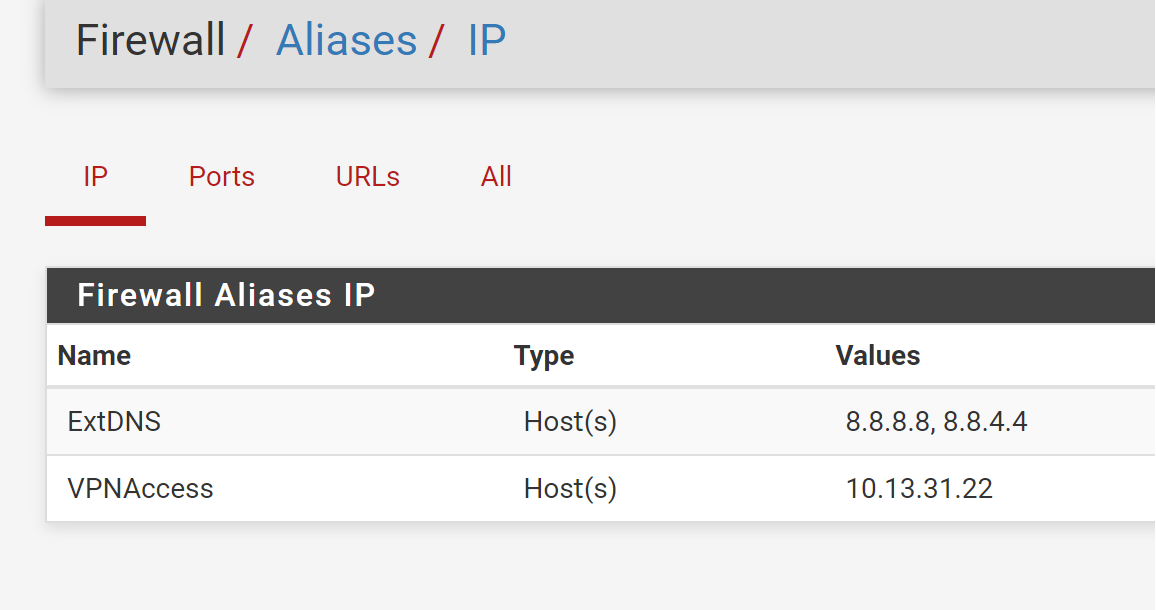
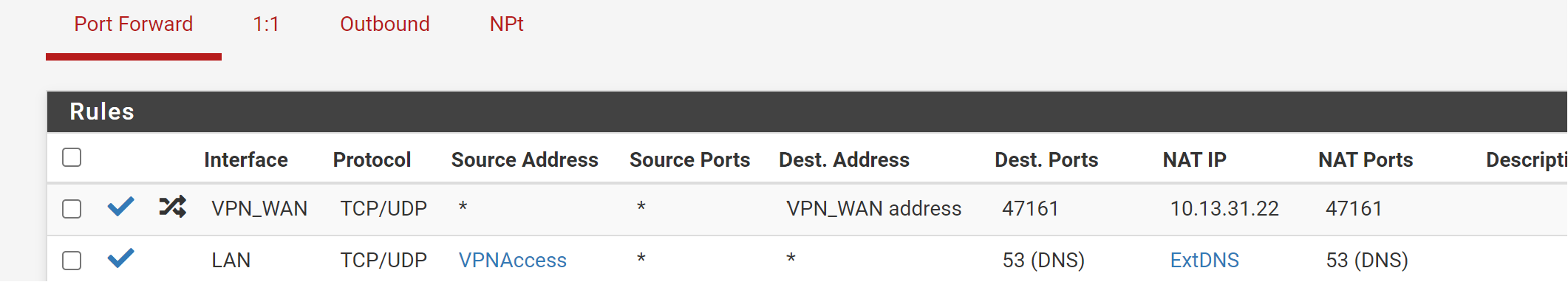
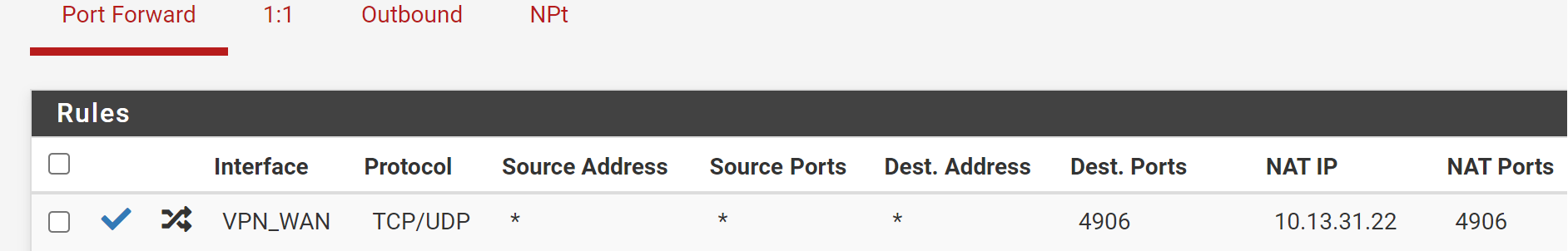
Firewall -> NAT -> Port Forward:
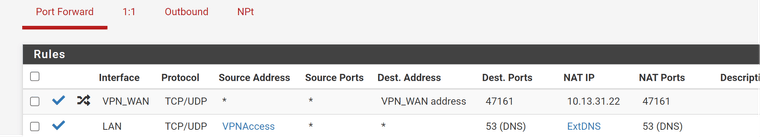
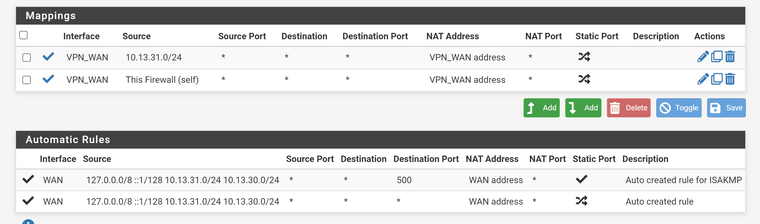
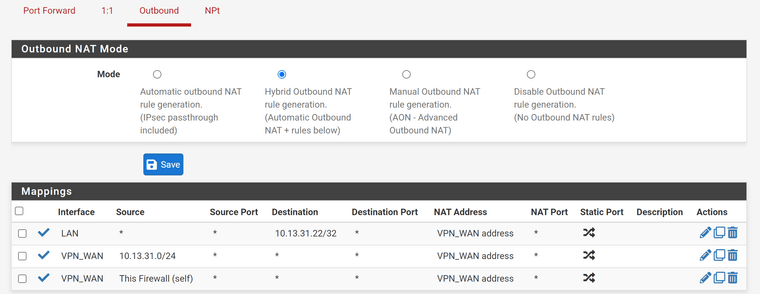
Firewall -> NAT -> Outbound:
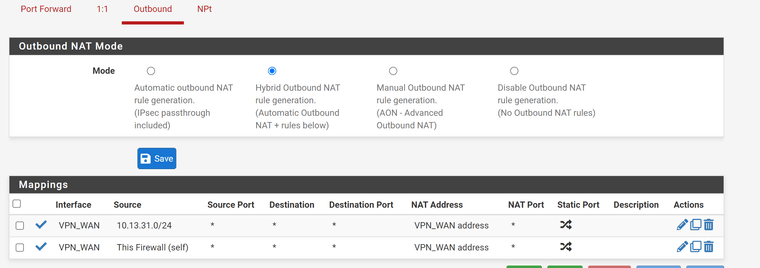
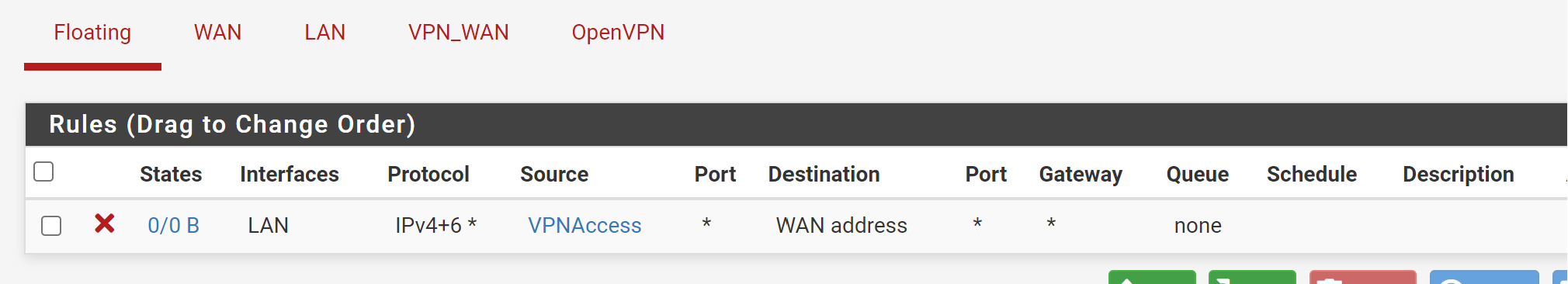
Firewall -> Rules -> Floating (To block VPN Addresses from using WAN IP directly)
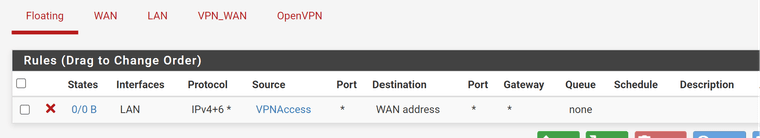
Firewall -> Rules -> LAN (Ignore the gateway names, I updated the interfaces etc. switching to this new VPN provider.)
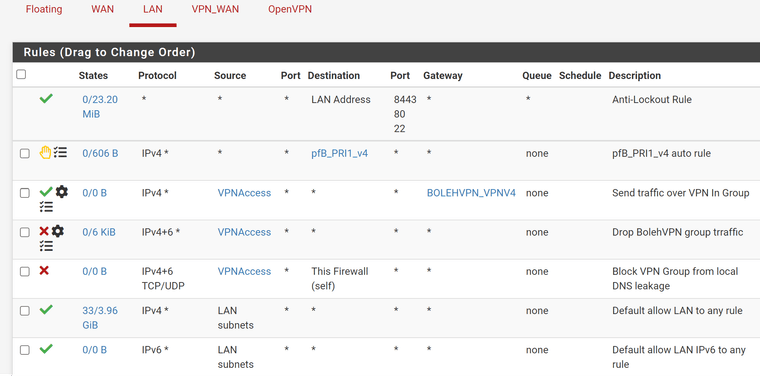
Firewall -> Rules -> VPN_WAN
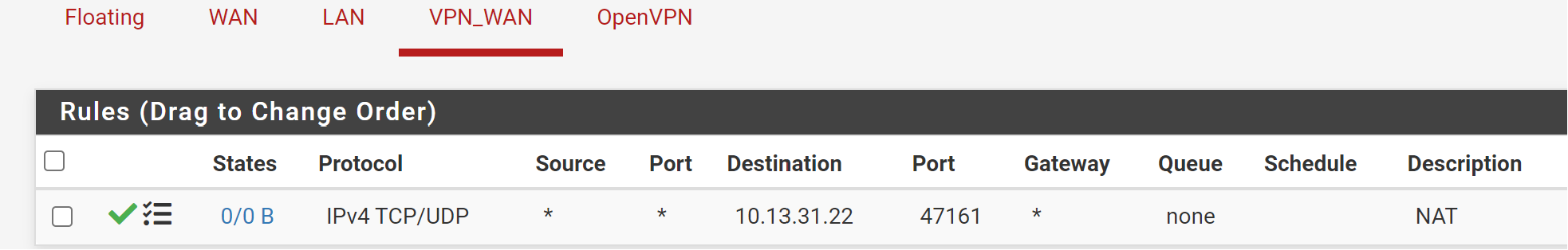
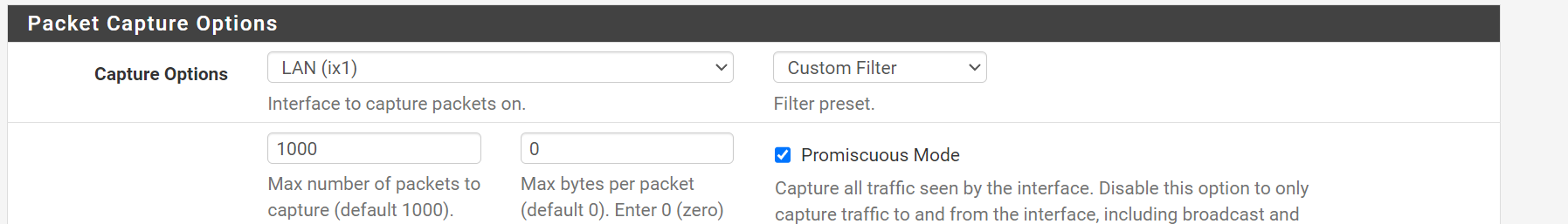
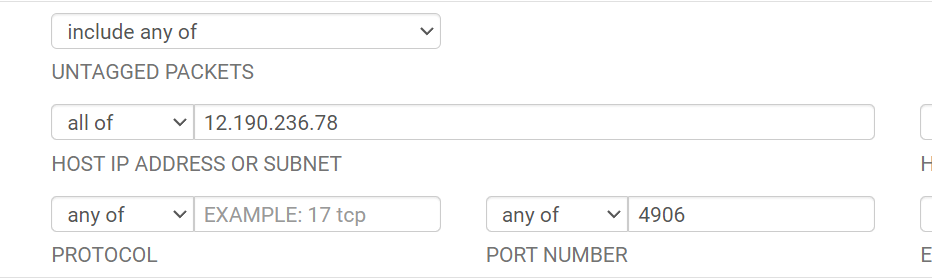
Packet Capture:
-
@techbooties said in Port Forwarding w/ OpenVPN Tunnel - What am I doing wrong?:
Client's are part of an alias group & clients in the alias group connect to problem to the outside.

Inbound traffic on a specified port, to a machine in the alias group, via VPN interface appears to be blocked. Nothing in the firewall logs. I do see traffic in the Packet Capture attempting to send traffic to me.
Packet Capture:Sniff the traffic on the LAN interface to verify if it is blocked on pfSense.
If you can see the forwarded packets there, the traffic is probably blocked by the destination host.
Does it even listen on port 47161?Firewall -> Rules -> Floating (To block VPN Addresses from using WAN IP directly)
This rule only blocks the host in the stated alias. But this makes no sense, since any traffic from this alias is directed to the VPN gateway by LAN policy routing rule and if the rule is omitted due to the gateway is down, any traffic is blocked by the next rule.
-
@viragomann - Thx for the response. To clarify your points:
-
I was only saying that there is one IP (10.13.31.22) in the group "VPNAccess" which is an alias, per the guides followed. In my case, this is the only IP that should use the VPN (in the past, I had a few more in there but since consolidated.)
-
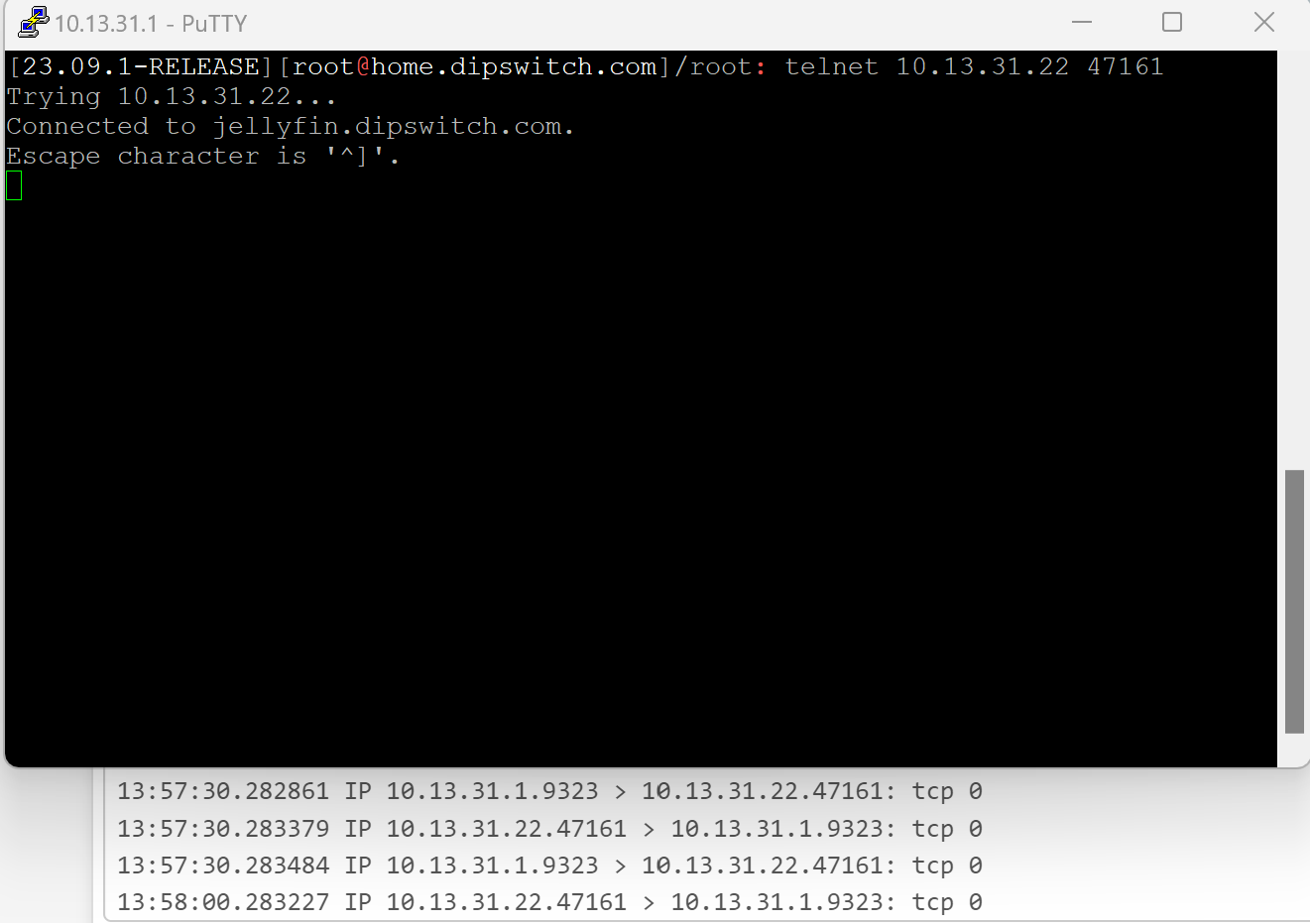
Telnet locally to the client from another local machine works on the port:

-
I sniffed on LAN, from the router to the client, and the ports show up. (When using another local to local host, it won't show up in the sniff, due to never hitting the router.) (Note: Ignore the hostname, it's a local domain, resolved locally at the moment.)
-
-
Is there anyone else with a similar problem?
-
@techbooties
Again, sniff the traffic on LAN using packet capture, while you try to access the service via VPN.
Post the result, please. -
@viragomann - Thanks for the post. Was what I pasted previously in response to your question initially, not sufficient? I thought that I had done what you suggested?
-
@techboot
You posted a pcap of LAN, while you obviously did a telnet from pfSense itself. And this seems to work.
However, I requested to sniff the traffic on LAN, while you access the server from outside via VPN. -
Thanks -- Just got back to this today.
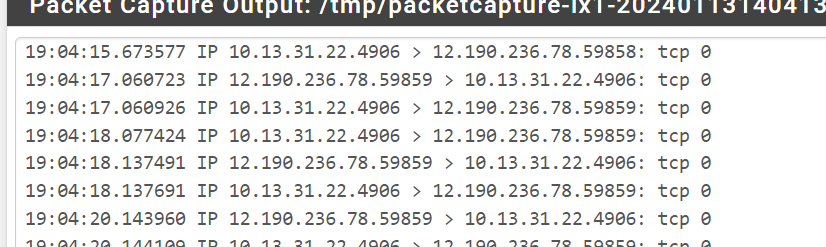
When I try the same telnet as above, I don't get any kind of connection. When using Lan to Lan I get a connection via telnet, so I can't say that the host machine is blocking this?
-
@viragomann -- I wanted to add a detail that the VPN provider is issuing private IP addresses (ie: 10.X.X) but I imagine that is commonplace with every kind of VPN provider at this stage. Is there a rule I am missing?
I tried a block all rule on the VPN interface to see if I could get any kind of logging, and there was nothing even in the firewall block logs.
-
@techboot
You're using a different destination port now, as allowed in the NAT rule?Don't know, what kind of connection this is. It basically looks fine, but not any packet has a payload. So maybe it's just "keep alive" communication.
@techbooties said in Port Forwarding w/ OpenVPN Tunnel - What am I doing wrong?:
I wanted to add a detail that the VPN provider is issuing private IP addresses (ie: 10.X.X) but I imagine that is commonplace with every kind of VPN provider at this stage.
Changed the forum username?
No, it's not normal to masquerade the source IP.
And I was expecting to see a public IP. -
I must have created a second account and didn't realize Google had an account linked and stored the other. Sorry for this confusion. I will clean up the duplicate account, but don't want to delete it mid-thread.
Yes, I changed the port number from the VPN provider... it's a static port, with the option to release and request a new one if needed.
So basically VPN provider (AirVPN) has public IP -> private IP with assigned port to route towards it (mine, when connected with the client) -> pfsense -> local machine
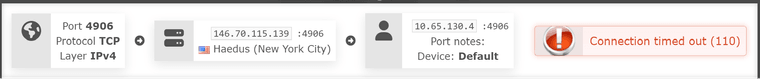
So my running theory now is that since I am being assigned a 10.x IP by the VPN provider upon connection to them, there is something I am missing fundamentally in my config?
-
-
@techboot
This whole thread is already pretty confusing. In the screenshot above on the VPN interface, I can see public source IP. But then you say, the provider replaces it with a private one (masquerading)...To get a step beyond, do a simple test, please:
Add an outbound NAT rule for the incoming traffic:
Interface: LAN
source: any
destination: <server IP>/32
translation: interface addressCheck if you get access from outside.
-
To clarify when you say "server ip" do you want the public ip as seen in the screenshot or the assigned internal IP via Masquerading?
-
@techboot
It's local IP.Edit:
also flush the states after adding the rule. -
No change. To confirm:
NAT:
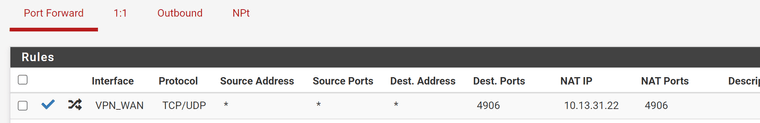
Outbound NAT:
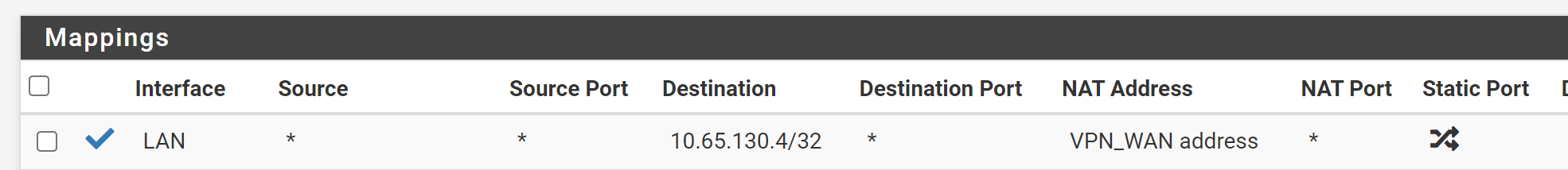
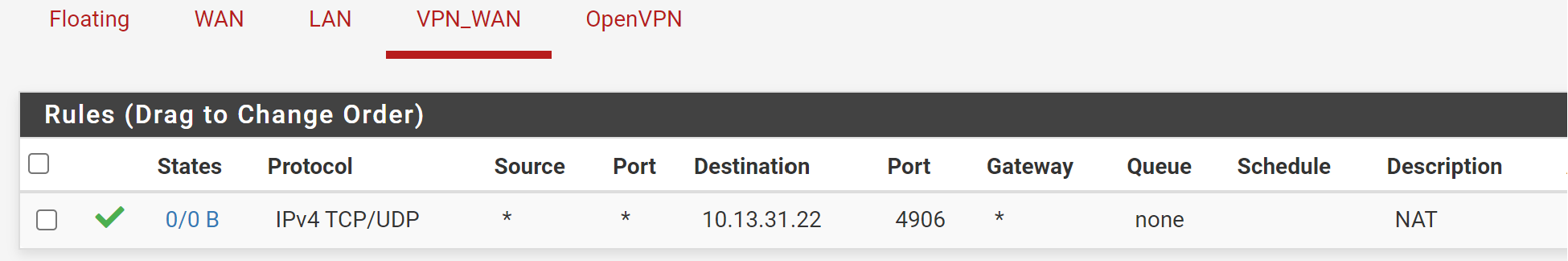
Rules (VPN Interface)
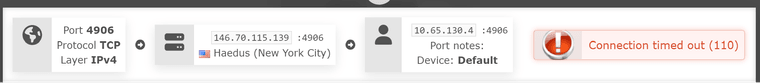
VPN Provider Port Check Tool: (Note, telnet to the public IP from an outside IP (ie: an Azure VPS, yields the same result)
--
In an effort to maybe make this easier, should I delete this thread and re-make it? I will remove all of the rules, NAT, etc.. reboot for good measure and start over with all of the details / information in one post based on your feedback and comments thus far?
-
@techboot said in Port Forwarding w/ OpenVPN Tunnel - What am I doing wrong?:
NAT:
And the mess goes on...
10.13.31.22 is your VPN interface address. The NAT IP has to be your internal server IP!Also you should limit the destination IP. Your may set it to the interface address.
-
-
@techboot
Ah ya. So you need to edit the outbound NAT rule and correct the destination IP. -
Cleared States.
--
--
I am confused what you mean by limit the destination IP and limit to the interface address. I assume you mean on the port forward tab?