Mapping public IP to internal host IP for outbound traffic
-
I have a /29 block of IPs and I'd like to map an IP to each device specifically for outbound traffic.
I've seen a bunch of guides for dealing with traffic going inbound, but I haven't found anything that works for outbound traffic.My current setup is pfSense on IP *.35, and I'd like to use *.36, 37, and 38 for my 3 internal hosts.
On a fresh config of pfSense how would I accomplish this?
Previously in IPFire we made virtual IP addresses and mapped those to each host. -
@fuckwit_mcbumcrumble Outbound NAT:
https://docs.netgate.com/pfsense/en/latest/nat/outbound.html
You can change to Hybrid and add rules for your special devices.The IPs can be added as VIPs/IP Alias:
https://docs.netgate.com/pfsense/en/latest/firewall/virtual-ip-addresses.html -
@SteveITS
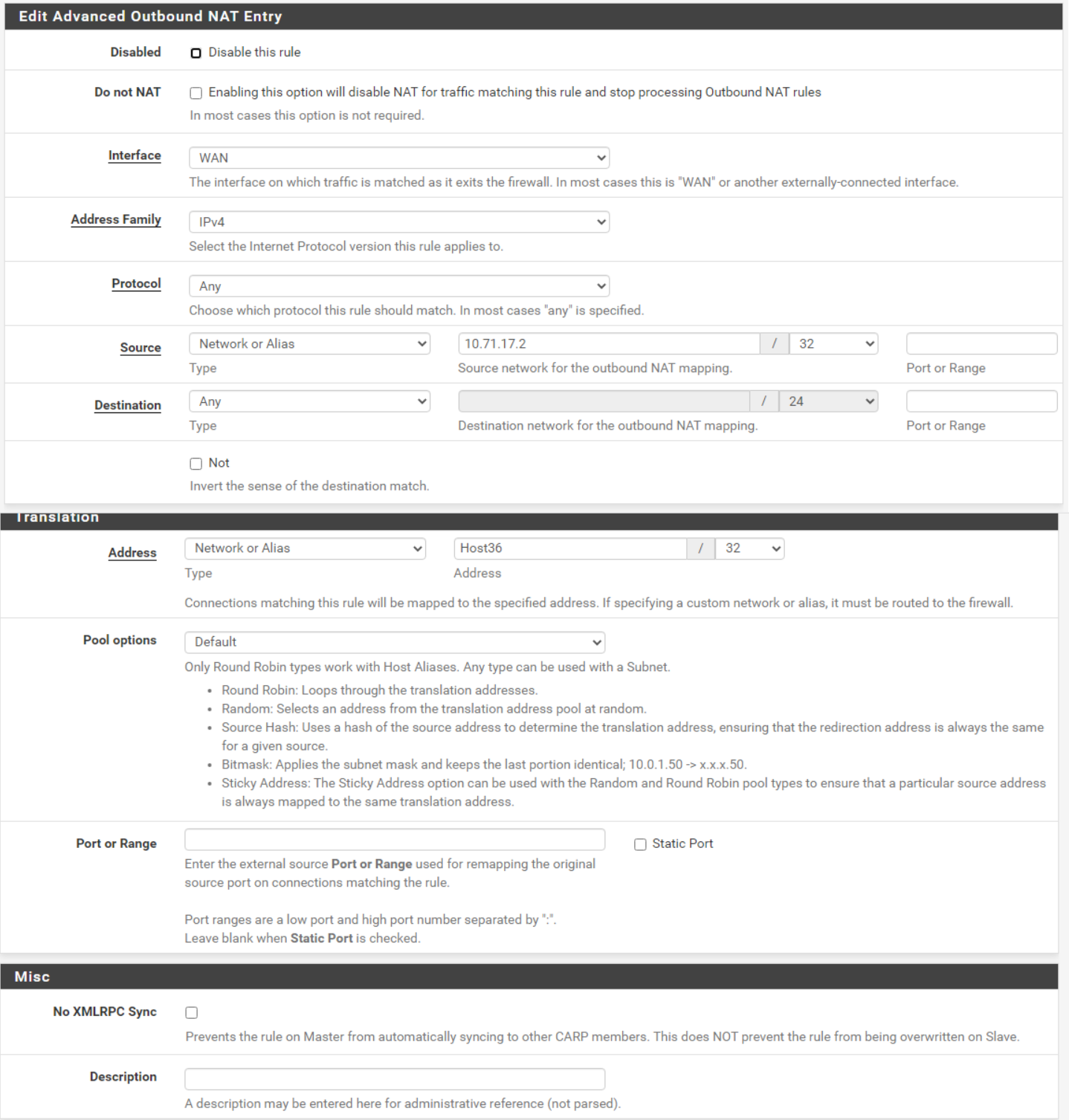
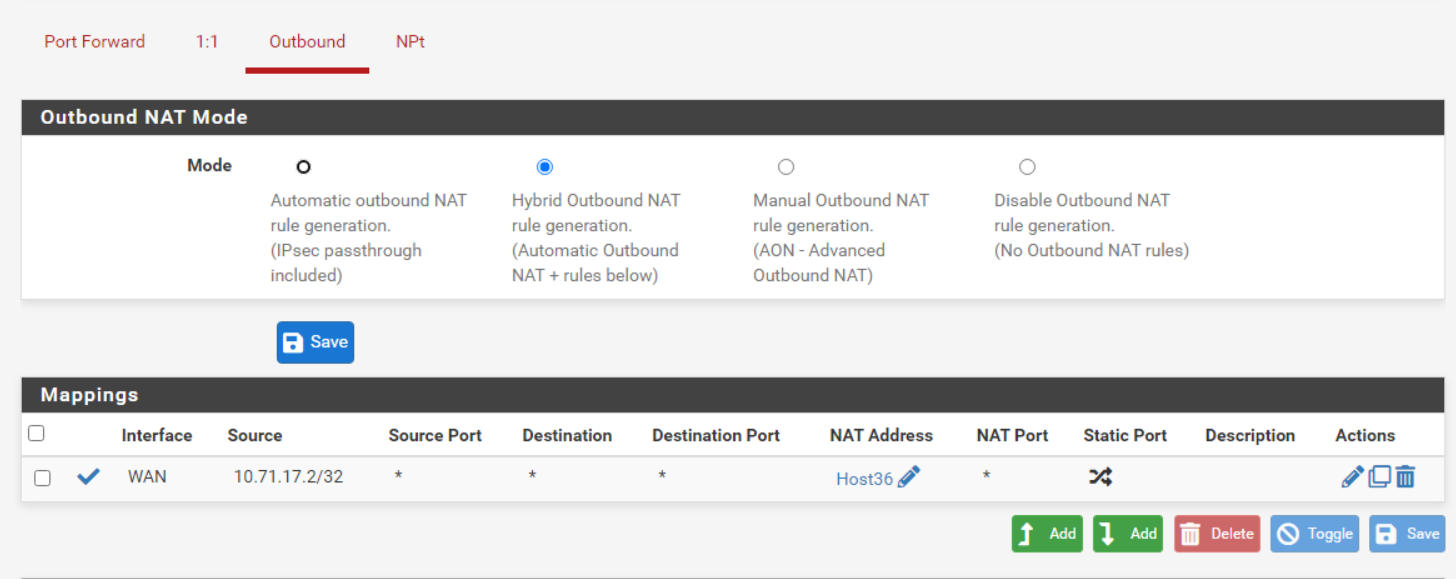
Attached is my current config. As far as I can tell from those guides I have it set up correctly based on those docs.
However as soon as I enable the outbound nat rule the device is not able to communicate outside of the network.
Inside it works just fine, but as soon as it tries to leave the network all connectivity is lost.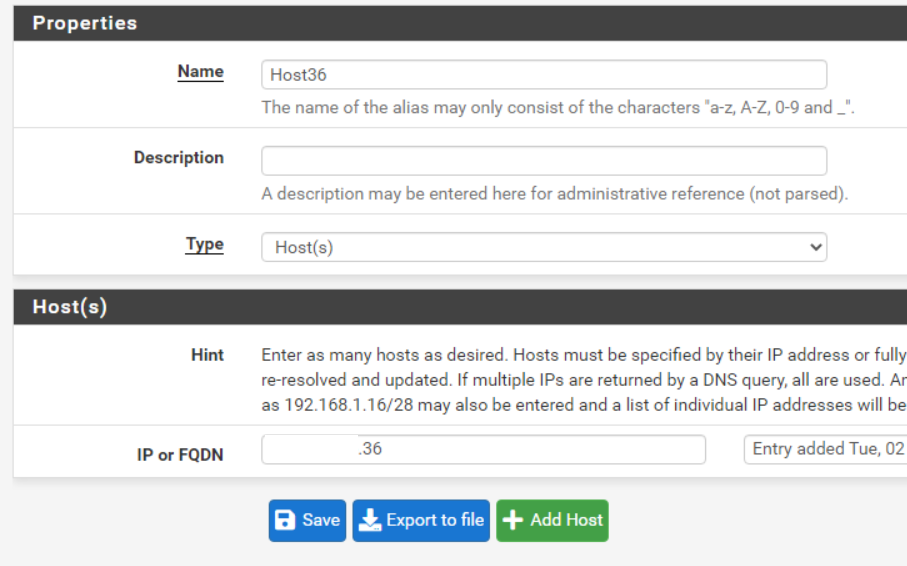
-
@fuckwit_mcbumcrumble
You need to add the public IPs to the WAN first. Firewall > Virtual IPs
Use type "IP Alias", select WAN interface and state the desired IP with the correct /29 mask.Then in the outbound NAT rule at translation address you can select this IP from the drop-down. But it should also work with the alias you've already created.