"aws s3 cp" crashes the firewall when using squid web proxy
-
This post is deleted! -
@stephenw10 he does show some 1 Jumbo in the list above, but no denied, would MTU on the Amazon side cause this?
-
I would not expect it to. Unless I've misunderstood this the Squid instance is local and AWS here is remote. So the MTU of the link between them is very unlikely to be more than 1500B, probably less.
The problem seems more likely to be that it's trying to cache the full file and then stops accepting traffic.
Do you see the same thing if you try to upload that file to somewhere else? Or any file >500MB to anywhere?
-
To recap:
Squid is local and runs on our LAN firewall / gateway.
AWS S3 bucket is obviously remote.
"Aws s3 cp" tries to copy from a LAN Debian machine to that bucket.
Transfer goes through fine if it bypasses Squid.
When it's told to use web proxy it crashes the firewall after uploading 0.5 / 8 GB.I've just successfully uploaded a 8 GB file to Google Drive involving Squid.
The transfer took several minutes. CPU usage remained at 50-60%.
MBUF Usage reached 30% (3036/10035) and stayed there.
No crash or any noticeable impact on other services and connectivity. -
@adamw What port is used? You need to add that to safe ports in Squid.. I had issues with the college ports needed to be marked safe in Squid that was in use without them it failed any connections
-
@JonathanLee
TCP 443 in both cases (aws s3 cp and Google Drive upload). -
Is Squid set as Custom SSL MITM or Transparent or both??
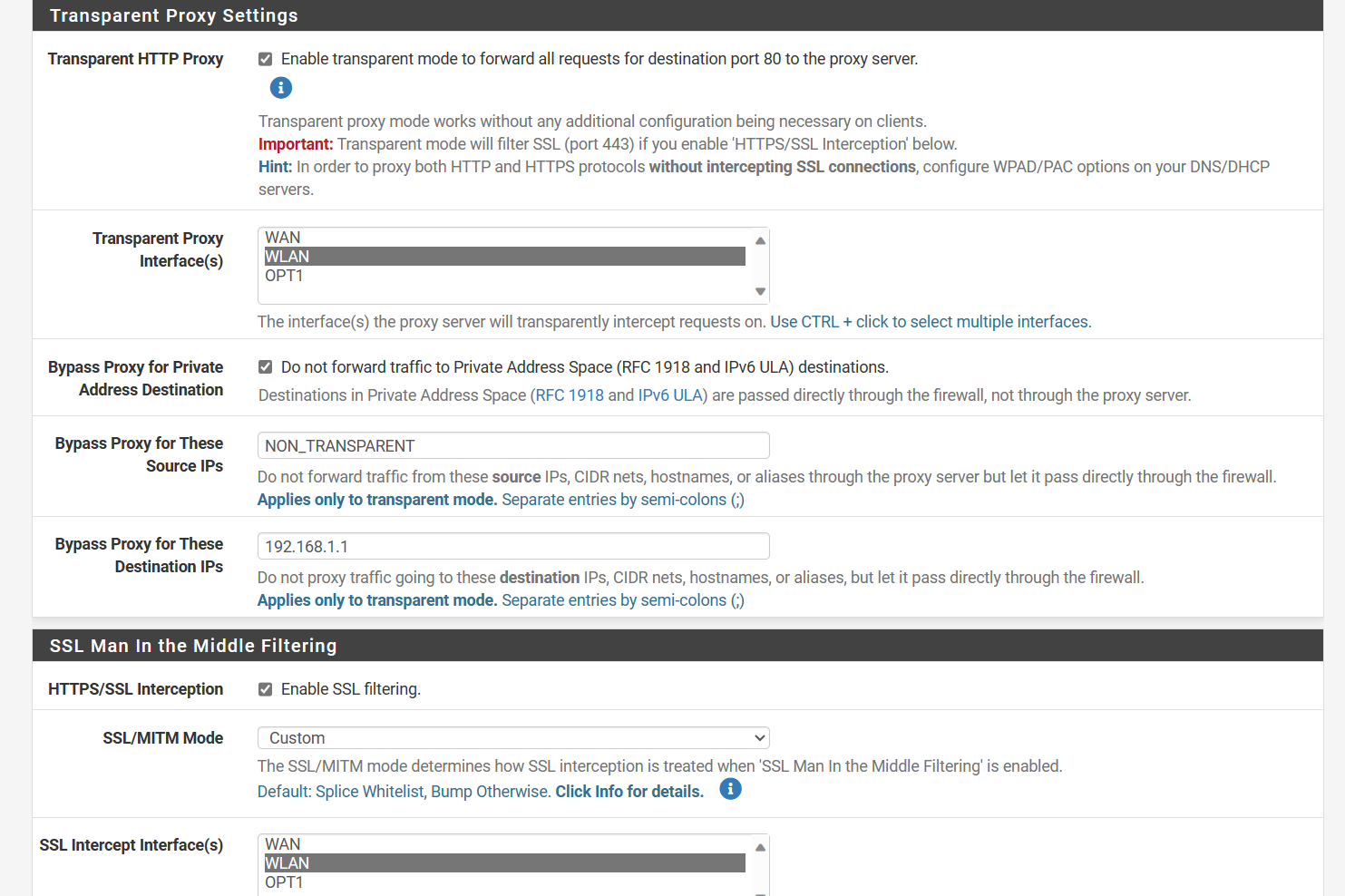
Some sites need to be splice only add this as a splice only
I do this with advanced
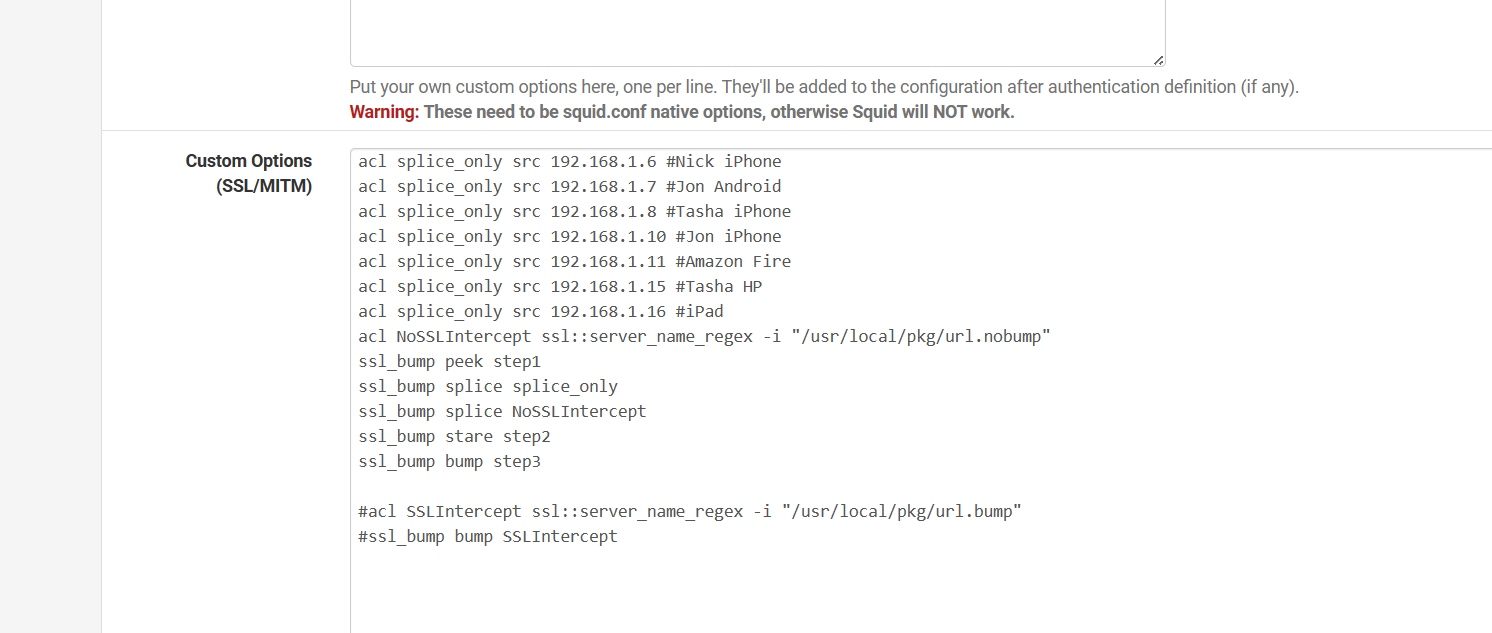
I have a regex splice file that has sites always set to splice
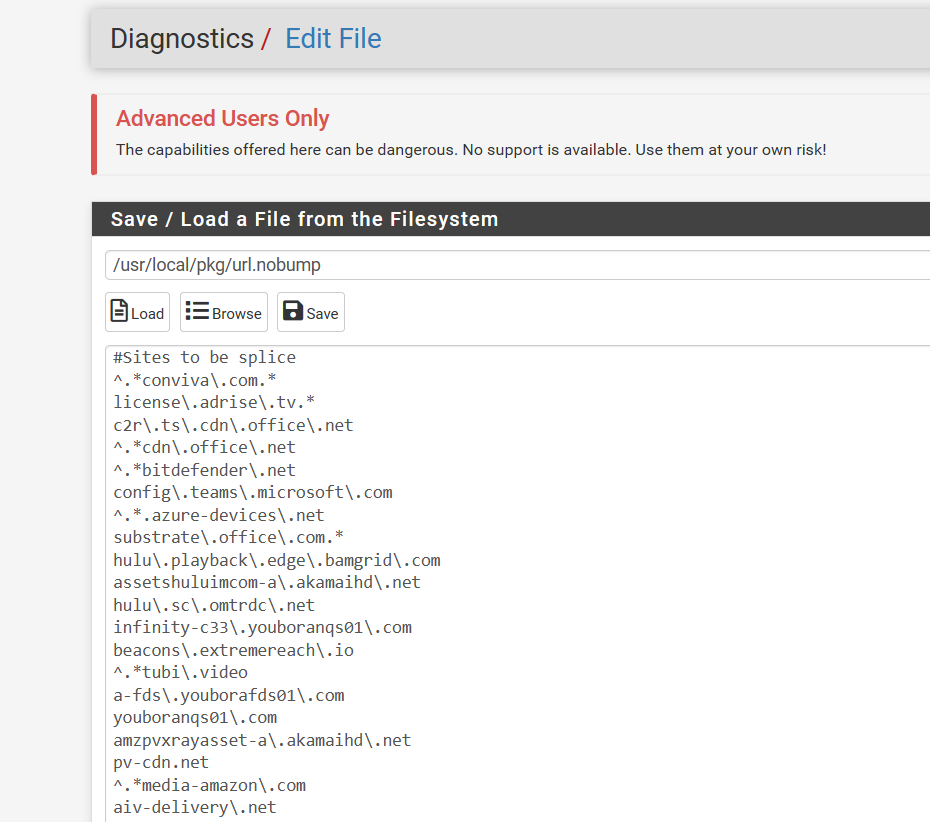
-
My settings:
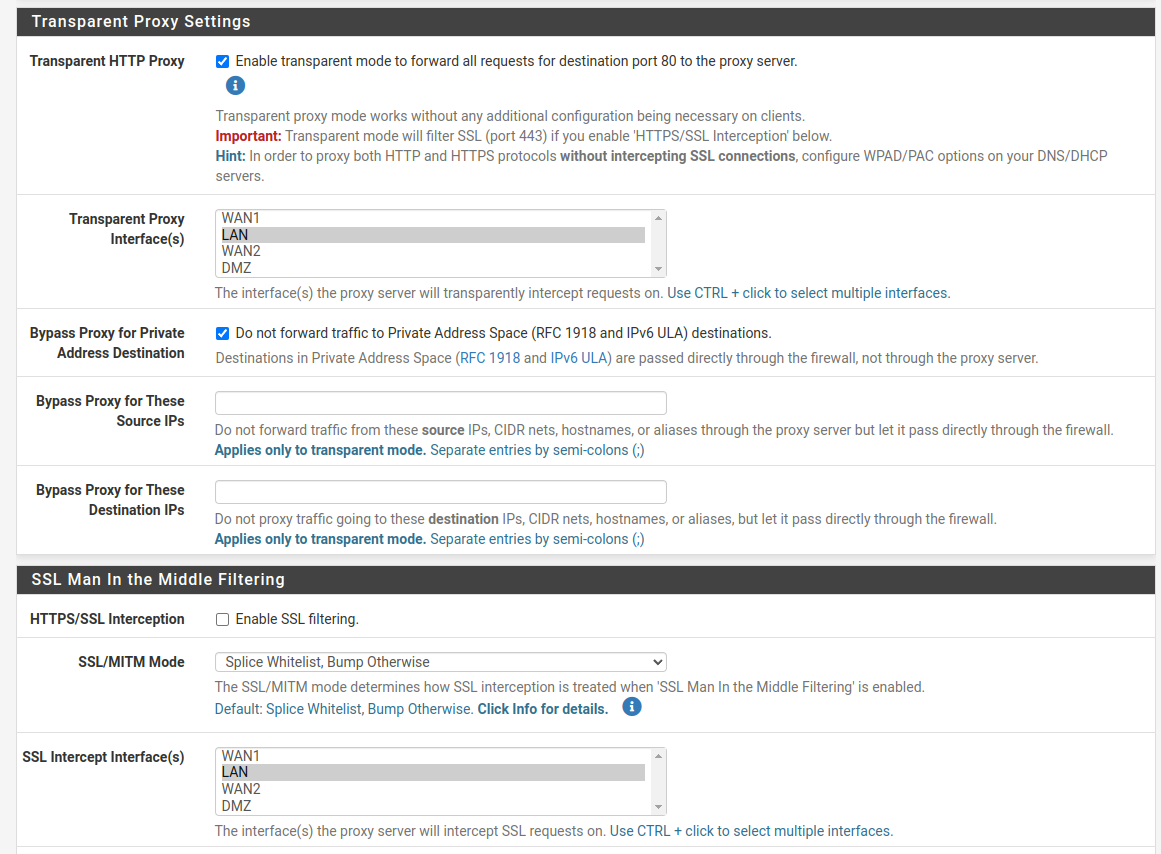
Making it bypass proxy has basically solved my problem but thanks for the suggestions.
-
-
@adamw IP addresses that are set to already use the proxy don’t need to be transparent also because they know the proxy addresses already. That is what my bypass is so it doesn’t double them.
-
@JonathanLee said in "aws s3 cp" crashes the firewall when using squid web proxy:
@adamw @mcury I also bypass destination of my firewall IP that helped me with weird firewall logs showing up. I have my 192.168.1.1 as go to firewall rules
If you are going to use transparent proxy for some users and explicit proxy for others, as I used to do back in my Squid days, the best way I found was :
Bypass Proxy for These Source IPs: Include all IPs that are going to use explicit proxy.
Bypass Proxy for These Destination IPs: Inlucde here all the local networks, advice would be to add 10.0.0.0/8;172.16.0.0/12;192.168.0.0/16For users using explicit mode, do the same bypass but in the client settings (Browser and/or OS, or through the .pac file directly).
-
Just a quick reminder that the thread is not about bypassing squid but about a sensible https request crashing the firewall requiring a power cycle :)
-
@adamw said in "aws s3 cp" crashes the firewall when using squid web proxy:
Just a quick reminder that the thread is not about bypassing squid but about a sensible https request crashing the firewall requiring a power cycle :)
Hm, unfortunately I can't help you with that.. I was a SG-3100 owner for almost 6 years, used Squid for a long long time and no crashes for me.
I would suggest you to try to a clean squid install, then go configuring little by little to find what is the trigger for the crash.good luck!
-
Is config exported from Netgate 3100 expected to work with Netgate 4100 out of the box?
I might be ok with exchanging one of our 3100 devices for 4100 and use the latter for further testing. -
You'd have to reassign the interfaces but otherwise yes. If you have any complex VLAN/switch port setup in the 3100 that wouldn't apply in a 4100 of course.
-
 A adamw referenced this topic on
A adamw referenced this topic on