Why do I need TS installed on pfsense router?
-
@johnpozah ok. Looks different to me
-
@michmoor maybe browser setting on my phone? Just using firefox on an iphone.. I think I set it to dark or something - not a big browser on my phone guy anyway.. I mean I look up stuff like anyone and go to the site.. But not a big just surfing about to stuff so have not spent any time trying to make it look pretty or anything ;) heheh
-
I see
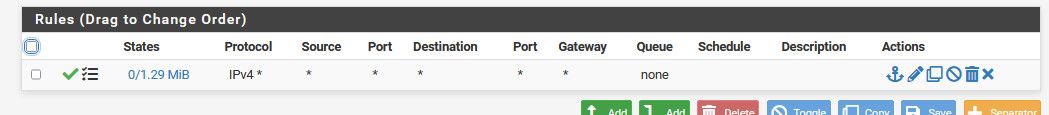
tailscale0 Default deny rule IPv4 (1000000103)Blocking access to my router via TS
I have no WF rules on tailscale0 interfacePuzzled

I do see WG port open.
Do I need to open port for TS too?
-
@chudak you mean on this interface you have no rules?
-
@johnpoz said in Why do I need TS installed on pfsense router?:
@chudak you mean on this interface you have no rules?

I do not.
What’s interesting that except opening pfsense UI everything else is working fine


 ️
️PS: WG interface also has none
-
@chudak so you can get to your other devices though pfsense TS connection.. Or do the clients have their own TS connections?
I could try removing that rule and see if I can still get to the web gui.. There for sure some hits on it - but not very much.. but then all I did was open the webgui page, I didn't log in or anything.
I will set that rule to log as well to see what it actually allows.
-
@johnpoz said in Why do I need TS installed on pfsense router?:
@chudak so you can get to your other devices though pfsense TS connection.. Or do the clients have their own TS connections?
Both work fine
BTW I trued adding this rule and it didn't make any difference
-
@chudak that rule is what seems to allow it - here I set it to log, and made a connection via my phone and you can see it showing a state
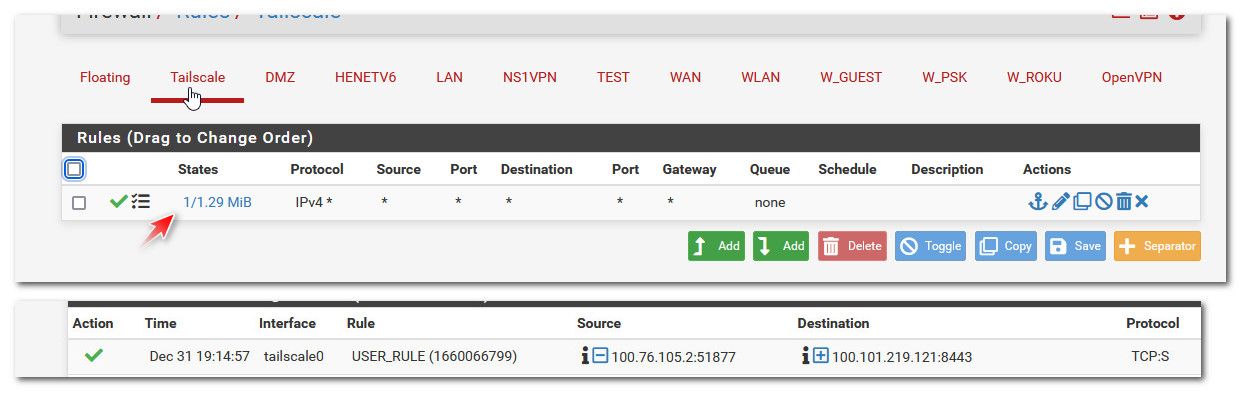
Did you try just access say your webgui on your pfsense lan IP?
-
@johnpoz said in Why do I need TS installed on pfsense router?:
@chudak that rule is what seems to allow it - here I set it to log, and made a connection via my phone and you can see it showing a state

Did you try just access say your webgui on your pfsense lan IP?
I can access via LAN IP
Added this rule and see what you see:
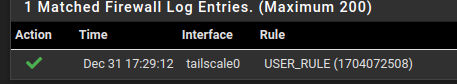
So it passed, buy still no UI
So I am suspecting it's something else on pfsense level
-
@johnpoz said in Why do I need TS installed on pfsense router?:
@chudak that rule is what seems to allow it - here I set it to log, and made a connection via my phone and you can see it showing a state

Did you try just access say your webgui on your pfsense lan IP?
Did you set up any of these?
https://tailscale.com/kb/1146/pfsense/?q=pfsen
https://tailscale.com/kb/1181/firewalls
https://tailscale.com/kb/1082/firewall-portsIn addition to the standard TS install?
-
@chudak those are all about clients behind pfsense making their own TS connections, I have none of those.. I allowed the 41641 port to my wan that is it..
-
@johnpoz said in Why do I need TS installed on pfsense router?:
@chudak those are all about clients behind pfsense making their own TS connections, I have none of those.. I allowed the 41641 port to my wan that is it..
TCP/UDP on 41641 on WAN?
-
-
@chudak mine is set for UDP only - I set it up long time ago.. I must of looked to see what they require.. But Its working.. If I connect my phone from sell it shows direct connection and my rule shows a state.
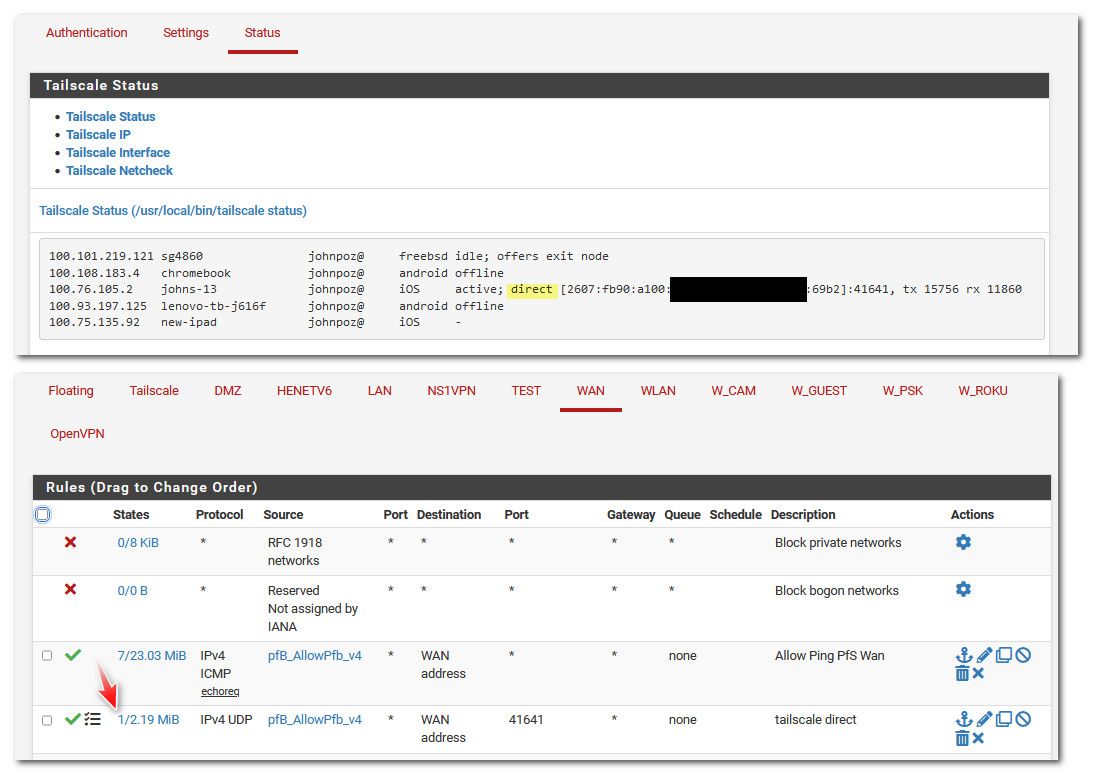
My phone on cell only gets IPv6, but t-mobile converts it to IPv4 when connecting to IPv4 stuff.
-
@johnpoz said in Why do I need TS installed on pfsense router?:
@chudak mine is set for UDP only
Changed my to UDP only and confirmed it still works fine
-
For what its worth i do not have the TS port open on my WAN side and im able to make direction connection and access all LAN resources.
The snippet is from my phone on LTE.

WAN rules
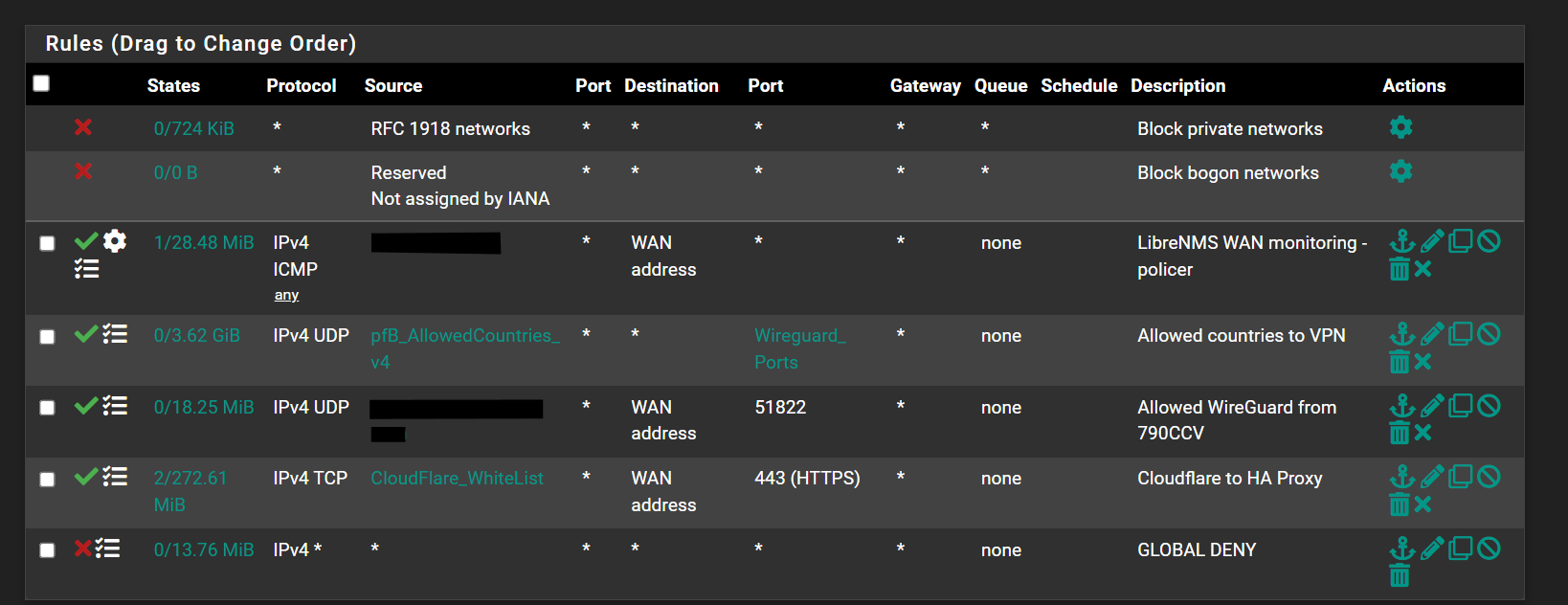
-
@michmoor said in Why do I need TS installed on pfsense router?:
For what its worth i do not have the TS port open on my WAN side and im able to make direction connection and access all LAN resources.
The snippet is from my phone on LTE.

WAN rules

Also confirmed
I disabled the open port 41461 rule and still see everything working fine.But you do have a rule on the TS interface, don't you? As here:
that seem like a must to have
-
@chudak I am pretty sure it uses stun to get through the nat. But its better to on purpose open it so you can view it, etc.
-
@chudak
TS rules are not required if accessing resources on your LAN. The reason is all in how TS and FreeBSD work out the routing. Essentially the most direct interface out to your LAN will be your source IP.
For example, if your LAN gateway IP is 192.168.1.1 then when you access a server on that LAN from TS, the server will see incoming requests from 192.168.1.1.
IMO, i do not like the implementation of TS on the firewall for this very reason. ACLs must be done on the TS controller but require you to write it in JSON. Its not difficult to write but its cumbersome. The default ACL on Tailsale is 'any-any' which is why communication works out of the box so to speak.
If this is for remote access to your home then no biggie but i would highly advise not to use this for any business deployment.Here are my ACL rules which work in my limited environment i am using this.
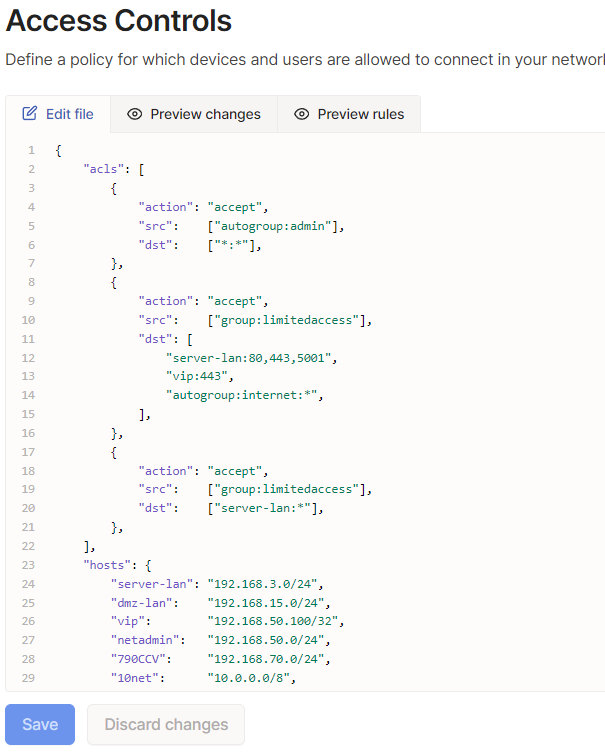
-
@michmoor I by any means not a tailscale expert or even user.. I have it up and running, it works - but I don't normally use it. if I need to remote in I use openvpn as my go too.
But if rules are not needed on the interface - why is showing traffic when was testing if could access pfsense web gui, doing some pings, etc..