OpenVPN does not work on bridged PFsense router
-
It sees the connection at the firewall and shows TLS error, it's got to be the certificate negotiation. This is an issue with the certificates. If you look at your firewall logs now on that tab under system and look for that time stamp see if a port is blocked. Most often VPN rules are created automatically, are you running auto outbound nat? or manual?
-
I am running auto outband NAT. I haven't noticed any entry in the firewall logs to suggest that the port is blocked. If it's able to work on my mobile network but not on my other network I would assume it isn't blocked by the firewall.
-
@george1116 Is your mobile network going into pfsense?
Have you also created a user profile on pfsense? Are you removing pfsense from the equation?
-
I have considered my ISP, but I am using the same provider on my mobile so that shouldn't be the problem.
I have a user profile which I use to log into pfsense. The only way I can use pfsense OpenVPN right now is to create a hotspot from my mobile phone, connect my PC to that network and then the VPN works, it just doesn't make sense to me, if there are issues with tls handshake then I shouldn't be able to use my mobile as well hotspot no?
-
@george1116 said in OpenVPN does not work on bridged PFsense router:
Tunnelblick
This is a different vpn client here....
When you are using pfSense to authenticate you are going to use the login profile you created to log on to the firewall (vpn server) after that you need to direct traffic with the OpenVPN tab on the firewall rules.
I think what you did , correct me if I am wrong is created or set a VPN with the "Tunnelblick" software first and connected without pfsense in the equation after that you wanted it to be secure so you installed OpenVPN on pfsense following a guide like this??
https://www.wundertech.net/how-to-set-up-openvpn-on-pfsense/
However when you created a username and profile on the firewall locally you are going to be authenticating to that with that username and password so the client on the mac running Tunnelblick is not needed here. It would only need to direct traffic to that client as your VPN tunnel goes to the firewall and stops and traffic flows out of it as if your sitting on the lan.
Without pfsense your vpn goes directly to the client and that's what it is authenticating to meaning you are not using pfsense at all your wifi is connected to your hotspot? That is why I think this is the issue your using your Tunnelblick login and expecting that same login to work with pfSense however that is specific to Tunnelblick and that is why it has certificate issues as it says hey tunnelblick let me log in and pfsense says no way I want the pfsense version of software (OpenVPN)
For you to use only pfSense you need to use the username and password you created on the firewall for use with OpenVPN after use remote desktop locally with that private ip you want to access.
-
@george1116 Try this
follow this guide https://www.wundertech.net/how-to-set-up-openvpn-on-pfsense/
after use OpenVPN download make sure it is the specific OpenVPN application on a windows pc or mac or iphone, it looks like a orange keyhole.
use the remote username and login for pfsense created in the guide see if you can connect, nothing else do not use Tunnelblick do not delete it do not try to connect to it just use the firewall info, once you do that see if you get a connection, if you do we can create a lan rule so you can work without Tunnelblick software running.
https://openvpn.net/client/
Use this client to test it, for this test you are removing use of tunnelblick so just shut that pc off when you run this test set it up as if you are logging on to the pfSense as the openvpn server
-
pfSense should be the server, I think tunnelblick is being used as a server and that is causing the issues, as this is the device you are connecting to and that is the issue
-
Not at all, I am not using Tunnelblick as a server, also, I followed that exact blog/video you shared to set up my VPN.
I downloaded the config from the VPN exporter and installed it correctly on both tunnelblick and viscosity, both output the same error.
-
@george1116 Can you connect to just the firewall without using Tunnelblick?
Can you use just OpenVPN software
Using
openvpn.net/client/ -
@JonathanLee said in OpenVPN does not work on bridged PFsense router:
openvpn.net/client/
Same thing here.
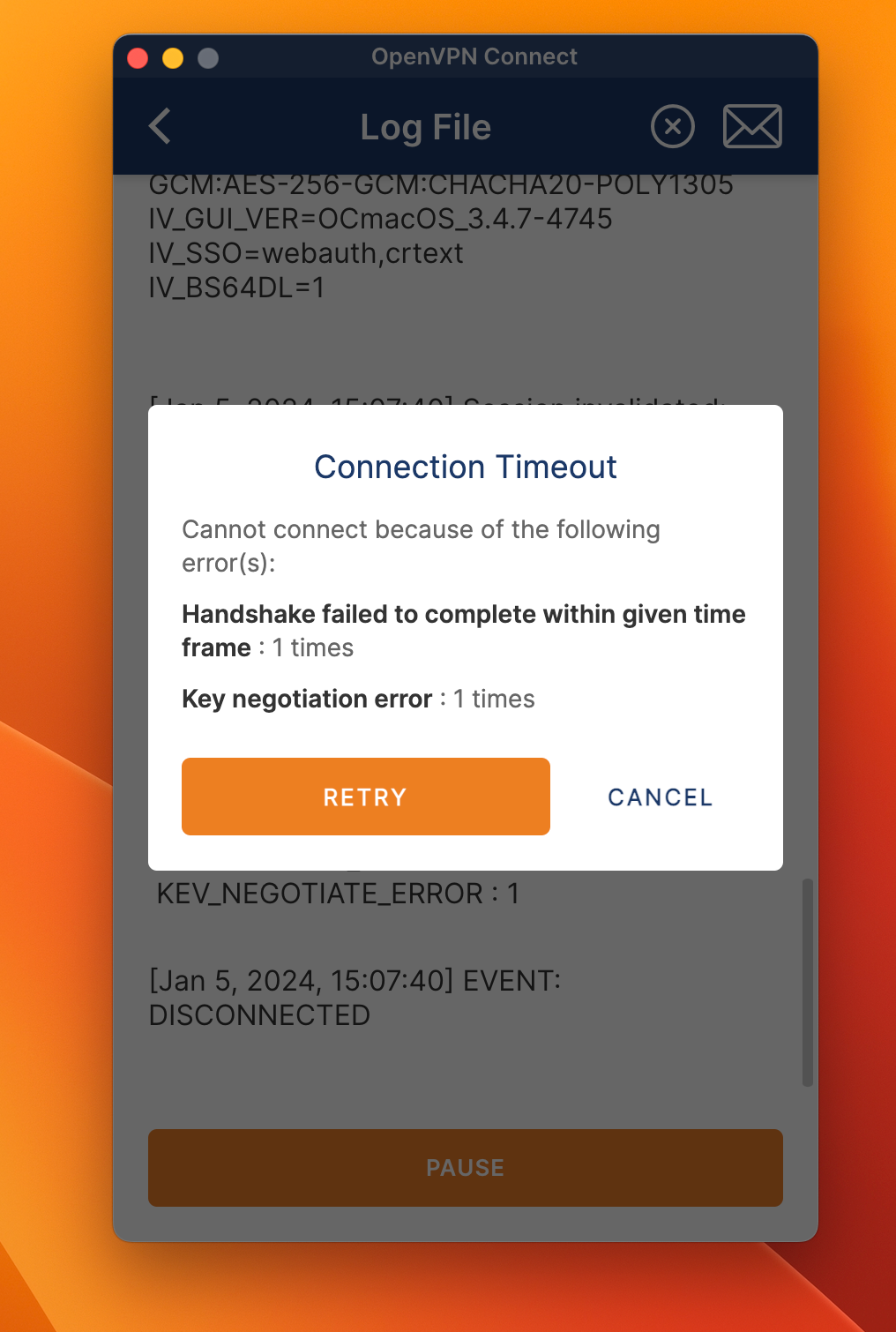
-
@george1116 Just to confirm are you using the user profile you created in pfsense to log on?
-
Yes, I am. I am sure this issue has nothing to do with the credentials because it already works, I can verify it on another network.
-
@george1116 interesting, does the equipment in front of pfSense have any logs you can get to?
-
No logs, the device comes from my ISP, and because I already set that device to bridge the LAN port it doesn't show any details about connected LAN devices either.
-
My set up works like this DSL modem has 4 ports, one port goes to my power over AC over to the other side of the house the second power over AC plugs into my firewall wan port modem is gives my firewall a wan address after I have my AP plugged into the lan of the firewall.
ISP dmark——>dsl modem——>firewall—->access point
I vpn onto the firewall with my static wan address, my IP address has not changed in years. I can see it connect into the firewall on the openVPN tab it shows states, after I have rules for what the vpn can access, it can only access my NAS.
Does yours do this? I think you said you have this,
ISP dmark——>modem——->router——->firewall bridged——>iMac you want to access
You’re gonna need to set a default route for that traffic on your router. Can you ping the iMac from the router?
-
This post is deleted! -
@george1116 said in OpenVPN does not work on bridged PFsense router:
My pfsense router is installed behind my home router, the LAN port on my home router which pfsense is connected to is set in bridged mode, so my pfsense WAN side is getting a public IP in the 199.x.x.x.x range.
I then installed openVPN on my pfsense router, but when I am connected directly to my home router (the bridged router) openVPN is not able to connect, however, when I connect via tethering to my mobile device hotstpo OpenVPN connects successfully.
What is the error I am getting:
When connecting to openVPN I get the below error message after some time.2024-01-03 08:30:08.123554 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) 2024-01-03 08:30:08.123640 TLS Error: TLS handshake failedWhat have I checked:
- I checked my home router to see if port 1194 is blocked, and it isn't
- I verified that my pfsene router WAN side is indeed getting a public IP and it is.
- I ensured there is no double NATing, this is evident from the public IP on pfsense WAN
- I used Packet Capture to verify that indeed there was an outbound connection from my machine to pfsense router, and there was.
- I changed the Tunnel Network of OpenVPN, but it didn't help
- I used different authentication Modes, but it didn't work
I have been going on for 2 days now, has anyone experienced this or knows what the problem could be
I think the router in front of your firewall is causing the issues, is this a standard ISP issued router with a dmark or a modem?