IPSec DNAT not working
-
10.199.47.1 = Provider VTI
10.199.47.2 = Customer VTIPART 1
Last 500 IPsec Log Entries. (Maximum 500)
Jan 16 14:40:07 charon 75651 06[CFG] vici client 1276 disconnected
Jan 16 14:40:07 charon 75651 12[CFG] updated vici connection: con2
Jan 16 14:40:07 charon 75651 12[CFG] id = CUSTOMER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] class = pre-shared key
Jan 16 14:40:07 charon 75651 12[CFG] remote:
Jan 16 14:40:07 charon 75651 12[CFG] id = PROVIDER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] class = pre-shared key
Jan 16 14:40:07 charon 75651 12[CFG] local:
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 2880
Jan 16 14:40:07 charon 75651 12[CFG] over_time = 2880
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 25920
Jan 16 14:40:07 charon 75651 12[CFG] reauth_time = 0
Jan 16 14:40:07 charon 75651 12[CFG] keyingtries = 1
Jan 16 14:40:07 charon 75651 12[CFG] unique = UNIQUE_REPLACE
Jan 16 14:40:07 charon 75651 12[CFG] childless = 0
Jan 16 14:40:07 charon 75651 12[CFG] fragmentation = 2
Jan 16 14:40:07 charon 75651 12[CFG] dpd_timeout = 0
Jan 16 14:40:07 charon 75651 12[CFG] dpd_delay = 30
Jan 16 14:40:07 charon 75651 12[CFG] encap = 0
Jan 16 14:40:07 charon 75651 12[CFG] dscp = 0x00
Jan 16 14:40:07 charon 75651 12[CFG] aggressive = 0
Jan 16 14:40:07 charon 75651 12[CFG] mobike = 0
Jan 16 14:40:07 charon 75651 12[CFG] ppk_required = 0
Jan 16 14:40:07 charon 75651 12[CFG] ppk_id = (null)
Jan 16 14:40:07 charon 75651 12[CFG] send_cert = CERT_SEND_IF_ASKED
Jan 16 14:40:07 charon 75651 12[CFG] send_certreq = 1
Jan 16 14:40:07 charon 75651 12[CFG] remote_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] local_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] remote_addrs = CUSTOMER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] local_addrs = PROVIDER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] version = 2
Jan 16 14:40:07 charon 75651 12[CFG] copy_dscp = out
Jan 16 14:40:07 charon 75651 12[CFG] copy_ecn = 1
Jan 16 14:40:07 charon 75651 12[CFG] copy_df = 1
Jan 16 14:40:07 charon 75651 12[CFG] sha256_96 = 0
Jan 16 14:40:07 charon 75651 12[CFG] hw_offload = no
Jan 16 14:40:07 charon 75651 12[CFG] remote_ts = 172.16.100.0/24|/0 0.0.0.0/0|/0 ::/0|/0
Jan 16 14:40:07 charon 75651 12[CFG] local_ts = 172.16.200.253/32|172.16.210.253/32 0.0.0.0/0|/0 ::/0|/0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
Jan 16 14:40:07 charon 75651 12[CFG] inactivity = 0
Jan 16 14:40:07 charon 75651 12[CFG] label_mode = system
Jan 16 14:40:07 charon 75651 12[CFG] label = (null)
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in_sa = 0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] interface = (null)
Jan 16 14:40:07 charon 75651 12[CFG] priority = 0
Jan 16 14:40:07 charon 75651 12[CFG] tfc = 0
Jan 16 14:40:07 charon 75651 12[CFG] reqid = 5003
Jan 16 14:40:07 charon 75651 12[CFG] close_action = none
Jan 16 14:40:07 charon 75651 12[CFG] start_action = start
Jan 16 14:40:07 charon 75651 12[CFG] dpd_action = start
Jan 16 14:40:07 charon 75651 12[CFG] policies_fwd_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] policies = 1
Jan 16 14:40:07 charon 75651 12[CFG] mode = TUNNEL
Jan 16 14:40:07 charon 75651 12[CFG] ipcomp = 0
Jan 16 14:40:07 charon 75651 12[CFG] hostaccess = 0
Jan 16 14:40:07 charon 75651 12[CFG] updown = (null)
Jan 16 14:40:07 charon 75651 12[CFG] rand_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 360
Jan 16 14:40:07 charon 75651 12[CFG] life_time = 3600
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 3240
Jan 16 14:40:07 charon 75651 12[CFG] child con2_3:
Jan 16 14:40:07 charon 75651 12[CFG] copy_dscp = out
Jan 16 14:40:07 charon 75651 12[CFG] copy_ecn = 1
Jan 16 14:40:07 charon 75651 12[CFG] copy_df = 1
Jan 16 14:40:07 charon 75651 12[CFG] sha256_96 = 0
Jan 16 14:40:07 charon 75651 12[CFG] hw_offload = no
Jan 16 14:40:07 charon 75651 12[CFG] remote_ts = 10.199.47.2/32|/0 0.0.0.0/0|/0 ::/0|/0
Jan 16 14:40:07 charon 75651 12[CFG] local_ts = 10.199.47.1/32|/0 0.0.0.0/0|/0 ::/0|/0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
Jan 16 14:40:07 charon 75651 12[CFG] inactivity = 0
Jan 16 14:40:07 charon 75651 12[CFG] label_mode = system
Jan 16 14:40:07 charon 75651 12[CFG] label = (null)
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in_sa = 0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] interface = (null)
Jan 16 14:40:07 charon 75651 12[CFG] priority = 0
Jan 16 14:40:07 charon 75651 12[CFG] tfc = 0
Jan 16 14:40:07 charon 75651 12[CFG] reqid = 5002
Jan 16 14:40:07 charon 75651 12[CFG] close_action = none
Jan 16 14:40:07 charon 75651 12[CFG] start_action = start
Jan 16 14:40:07 charon 75651 12[CFG] dpd_action = start
Jan 16 14:40:07 charon 75651 12[CFG] policies_fwd_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] policies = 0
Jan 16 14:40:07 charon 75651 12[CFG] mode = TUNNEL
Jan 16 14:40:07 charon 75651 12[CFG] ipcomp = 0
Jan 16 14:40:07 charon 75651 12[CFG] hostaccess = 0
Jan 16 14:40:07 charon 75651 12[CFG] updown = (null)
Jan 16 14:40:07 charon 75651 12[CFG] rand_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 360
Jan 16 14:40:07 charon 75651 12[CFG] life_time = 3600
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 3240
Jan 16 14:40:07 charon 75651 12[CFG] child con2_2:
Jan 16 14:40:07 charon 75651 12[CFG] conn con2:
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: load-conn
Jan 16 14:40:07 charon 75651 12[CFG] updated vici connection: con1
Jan 16 14:40:07 charon 75651 12[CFG] id = AZURE_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] class = pre-shared key
Jan 16 14:40:07 charon 75651 12[CFG] remote:
Jan 16 14:40:07 charon 75651 12[CFG] id = PROVIDER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] class = pre-shared key
Jan 16 14:40:07 charon 75651 12[CFG] local:
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 2880
Jan 16 14:40:07 charon 75651 12[CFG] over_time = 2880
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 0
Jan 16 14:40:07 charon 75651 12[CFG] reauth_time = 25920
Jan 16 14:40:07 charon 75651 12[CFG] keyingtries = 1
Jan 16 14:40:07 charon 75651 12[CFG] unique = UNIQUE_REPLACE
Jan 16 14:40:07 charon 75651 12[CFG] childless = 0
Jan 16 14:40:07 charon 75651 12[CFG] fragmentation = 2
Jan 16 14:40:07 charon 75651 12[CFG] dpd_timeout = 60
Jan 16 14:40:07 charon 75651 12[CFG] dpd_delay = 10
Jan 16 14:40:07 charon 75651 12[CFG] encap = 0
Jan 16 14:40:07 charon 75651 12[CFG] dscp = 0x00
Jan 16 14:40:07 charon 75651 12[CFG] aggressive = 0
Jan 16 14:40:07 charon 75651 12[CFG] mobike = 0
Jan 16 14:40:07 charon 75651 12[CFG] ppk_required = 0
Jan 16 14:40:07 charon 75651 12[CFG] ppk_id = (null)
Jan 16 14:40:07 charon 75651 12[CFG] send_cert = CERT_SEND_IF_ASKED
Jan 16 14:40:07 charon 75651 12[CFG] send_certreq = 1
Jan 16 14:40:07 charon 75651 12[CFG] remote_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] local_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] remote_addrs = AZURE_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] local_addrs = PROVIDER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] version = 1
Jan 16 14:40:07 charon 75651 12[CFG] copy_dscp = out
Jan 16 14:40:07 charon 75651 12[CFG] copy_ecn = 1
Jan 16 14:40:07 charon 75651 12[CFG] copy_df = 1
Jan 16 14:40:07 charon 75651 12[CFG] sha256_96 = 0
Jan 16 14:40:07 charon 75651 12[CFG] hw_offload = no
Jan 16 14:40:07 charon 75651 12[CFG] remote_ts = AZURE_LAN|/0
Jan 16 14:40:07 charon 75651 12[CFG] local_ts = 172.16.200.0/24|/0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_GCM_12_256/NO_EXT_SEQ, ESP:AES_GCM_8_256/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_12_128/NO_EXT_SEQ, ESP:AES_GCM_8_128/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ
Jan 16 14:40:07 charon 75651 12[CFG] inactivity = 0
Jan 16 14:40:07 charon 75651 12[CFG] label_mode = system
Jan 16 14:40:07 charon 75651 12[CFG] label = (null)
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in_sa = 0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] interface = (null)
Jan 16 14:40:07 charon 75651 12[CFG] priority = 0
Jan 16 14:40:07 charon 75651 12[CFG] tfc = 0
Jan 16 14:40:07 charon 75651 12[CFG] reqid = 0
Jan 16 14:40:07 charon 75651 12[CFG] close_action = none
Jan 16 14:40:07 charon 75651 12[CFG] start_action = trap
Jan 16 14:40:07 charon 75651 12[CFG] dpd_action = trap
Jan 16 14:40:07 charon 75651 12[CFG] policies_fwd_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] policies = 1
Jan 16 14:40:07 charon 75651 12[CFG] mode = TUNNEL
Jan 16 14:40:07 charon 75651 12[CFG] ipcomp = 0
Jan 16 14:40:07 charon 75651 12[CFG] hostaccess = 0
Jan 16 14:40:07 charon 75651 12[CFG] updown = (null)
Jan 16 14:40:07 charon 75651 12[CFG] rand_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 360
Jan 16 14:40:07 charon 75651 12[CFG] life_time = 3600
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 3240
Jan 16 14:40:07 charon 75651 12[CFG] child con1_1:
Jan 16 14:40:07 charon 75651 12[CFG] conn con1:
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: load-conn
Jan 16 14:40:07 charon 75651 12[CFG] updated vici connection: bypass
Jan 16 14:40:07 charon 75651 12[CFG] remote:
Jan 16 14:40:07 charon 75651 12[CFG] local:
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/AES_CTR_128/AES_CTR_192/AES_CTR_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/CAMELLIA_CTR_128/CAMELLIA_CTR_192/CAMELLIA_CTR_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_CCM_16_128/AES_CCM_16_192/AES_CCM_16_256/CHACHA20_POLY1305/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/AES_CCM_12_128/AES_CCM_12_192/AES_CCM_12_256/AES_CCM_8_128/AES_CCM_8_192/AES_CCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 1440
Jan 16 14:40:07 charon 75651 12[CFG] over_time = 1440
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 14400
Jan 16 14:40:07 charon 75651 12[CFG] reauth_time = 0
Jan 16 14:40:07 charon 75651 12[CFG] keyingtries = 1
Jan 16 14:40:07 charon 75651 12[CFG] unique = UNIQUE_NO
Jan 16 14:40:07 charon 75651 12[CFG] childless = 0
Jan 16 14:40:07 charon 75651 12[CFG] fragmentation = 2
Jan 16 14:40:07 charon 75651 12[CFG] dpd_timeout = 0
Jan 16 14:40:07 charon 75651 12[CFG] dpd_delay = 0
Jan 16 14:40:07 charon 75651 12[CFG] encap = 0
Jan 16 14:40:07 charon 75651 12[CFG] dscp = 0x00
Jan 16 14:40:07 charon 75651 12[CFG] aggressive = 0
Jan 16 14:40:07 charon 75651 12[CFG] mobike = 1
Jan 16 14:40:07 charon 75651 12[CFG] ppk_required = 0
Jan 16 14:40:07 charon 75651 12[CFG] ppk_id = (null)
Jan 16 14:40:07 charon 75651 12[CFG] send_cert = CERT_SEND_IF_ASKED
Jan 16 14:40:07 charon 75651 12[CFG] send_certreq = 1
Jan 16 14:40:07 charon 75651 12[CFG] remote_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] local_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] remote_addrs = 127.0.0.1
Jan 16 14:40:07 charon 75651 12[CFG] local_addrs = %any
Jan 16 14:40:07 charon 75651 12[CFG] version = 0
Jan 16 14:40:07 charon 75651 12[CFG] copy_dscp = out
Jan 16 14:40:07 charon 75651 12[CFG] copy_ecn = 1
Jan 16 14:40:07 charon 75651 12[CFG] copy_df = 1
Jan 16 14:40:07 charon 75651 12[CFG] sha256_96 = 0
Jan 16 14:40:07 charon 75651 12[CFG] hw_offload = no
Jan 16 14:40:07 charon 75651 12[CFG] remote_ts = 172.16.200.0/24|/0
Jan 16 14:40:07 charon 75651 12[CFG] local_ts = 172.16.200.0/24|/0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = ESP:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_CBC_128/AES_CBC_192/AES_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/NO_EXT_SEQ
Jan 16 14:40:07 charon 75651 12[CFG] inactivity = 0
Jan 16 14:40:07 charon 75651 12[CFG] label_mode = system
Jan 16 14:40:07 charon 75651 12[CFG] label = (null)
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in_sa = 0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] interface = (null)
Jan 16 14:40:07 charon 75651 12[CFG] priority = 0
Jan 16 14:40:07 charon 75651 12[CFG] tfc = 0
Jan 16 14:40:07 charon 75651 12[CFG] reqid = 0
Jan 16 14:40:07 charon 75651 12[CFG] close_action = none
Jan 16 14:40:07 charon 75651 12[CFG] start_action = trap
Jan 16 14:40:07 charon 75651 12[CFG] dpd_action = none
Jan 16 14:40:07 charon 75651 12[CFG] policies_fwd_out = 0 -
Jan 16 14:40:07 charon 75651 12[CFG] policies = 1
Jan 16 14:40:07 charon 75651 12[CFG] mode = PASS
Jan 16 14:40:07 charon 75651 12[CFG] ipcomp = 0
Jan 16 14:40:07 charon 75651 12[CFG] hostaccess = 0
Jan 16 14:40:07 charon 75651 12[CFG] updown = (null)
Jan 16 14:40:07 charon 75651 12[CFG] rand_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 360
Jan 16 14:40:07 charon 75651 12[CFG] life_time = 3960
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 3600
Jan 16 14:40:07 charon 75651 12[CFG] child bypasslan:
Jan 16 14:40:07 charon 75651 12[CFG] conn bypass:
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: load-conn
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: get-conns
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: get-pools
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: get-authorities
Jan 16 14:40:07 charon 75651 12[CFG] loaded IKE shared key with id 'ike-1' for: '%any', 'CUSTOMER_WAN_IP'
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: load-shared
Jan 16 14:40:07 charon 75651 12[CFG] loaded IKE shared key with id 'ike-0' for: '%any', 'AZURE_WAN_IP'
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: load-shared
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: get-shared
Jan 16 14:40:07 charon 75651 14[CFG] vici client 1276 requests: get-keys
Jan 16 14:40:07 charon 75651 14[CFG] vici client 1276 connected
Jan 16 14:40:07 charon 75651 07[CFG] vici client 1275 disconnected
Jan 16 14:40:07 charon 75651 07[CFG] loaded 0 RADIUS server configurations
Jan 16 14:40:07 charon 75651 07[CFG] loaded 0 entries for attr plugin configuration
Jan 16 14:40:07 charon 75651 07[CFG] ipseckey plugin is disabled
Jan 16 14:40:07 charon 75651 07[CFG] vici client 1275 requests: reload-settings
Jan 16 14:40:07 charon 75651 14[CFG] vici client 1275 connected
Jan 16 14:40:07 charon 75651 05[IKE] <con2|4> keeping statically configured path PROVIDER_WAN_IP - CUSTOMER_WAN_IP
Jan 16 14:40:07 charon 75651 05[KNL] 10.199.47.1 appeared on ipsec2
Jan 16 14:40:07 charon 75651 13[KNL] interface ipsec2 appeared
Jan 16 14:40:07 charon 75651 13[KNL] interface ipsec2 disappeared
Jan 16 14:40:07 charon 75651 09[KNL] interface ipsec2 deactivated
Jan 16 14:40:07 charon 75651 09[KNL] 10.199.47.1 disappeared from ipsec2
Jan 16 14:40:06 charon 75651 09[IKE] <con1|3> nothing to initiate
Jan 16 14:40:06 charon 75651 09[IKE] <con1|3> activating new tasks
Jan 16 14:40:06 charon 75651 09[NET] <con1|3> sending packet: from PROVIDER_WAN_IP[500] to AZURE_WAN_IP[500] (92 bytes)
Jan 16 14:40:06 charon 75651 09[ENC] <con1|3> generating INFORMATIONAL_V1 request 2819744997 [ HASH N(DPD_ACK) ]
Jan 16 14:40:06 charon 75651 09[IKE] <con1|3> activating ISAKMP_DPD task
Jan 16 14:40:06 charon 75651 09[IKE] <con1|3> activating new tasks
Jan 16 14:40:06 charon 75651 09[IKE] <con1|3> queueing ISAKMP_DPD task
Jan 16 14:40:06 charon 75651 09[ENC] <con1|3> parsed INFORMATIONAL_V1 request 1404219913 [ HASH N(DPD) ]
Jan 16 14:40:06 charon 75651 09[NET] <con1|3> received packet: from AZURE_WAN_IP[500] to PROVIDER_WAN_IP[500] (92 bytes)
Jan 16 14:40:05 charon 75651 09[CFG] vici client 1274 disconnected
Jan 16 14:40:05 charon 75651 09[CFG] vici client 1274 requests: list-sas
Jan 16 14:40:05 charon 75651 15[CFG] vici client 1274 registered for: list-sa
Jan 16 14:40:05 charon 75651 15[CFG] vici client 1274 connected
Jan 16 14:40:02 charon 75651 09[IKE] <con1|3> nothing to initiate
Jan 16 14:40:02 charon 75651 09[IKE] <con1|3> activating new tasks
Jan 16 14:40:02 charon 75651 09[ENC] <con1|3> parsed INFORMATIONAL_V1 request 1532146135 [ HASH N(DPD_ACK) ]
Jan 16 14:40:02 charon 75651 09[NET] <con1|3> received packet: from AZURE_WAN_IP[500] to PROVIDER_WAN_IP[500] (92 bytes)
Jan 16 14:40:02 charon 75651 09[IKE] <con1|3> nothing to initiate
Jan 16 14:40:02 charon 75651 09[IKE] <con1|3> activating new tasks
Jan 16 14:40:02 charon 75651 09[NET] <con1|3> sending packet: from PROVIDER_WAN_IP[500] to AZURE_WAN_IP[500] (92 bytes)
Jan 16 14:40:02 charon 75651 09[ENC] <con1|3> generating INFORMATIONAL_V1 request 1473236439 [ HASH N(DPD) ]
Jan 16 14:40:02 charon 75651 09[IKE] <con1|3> activating ISAKMP_DPD task
Jan 16 14:40:02 charon 75651 09[IKE] <con1|3> activating new tasks
Jan 16 14:40:02 charon 75651 09[IKE] <con1|3> queueing ISAKMP_DPD task
Jan 16 14:40:02 charon 75651 09[IKE] <con1|3> sending DPD request
Jan 16 14:40:00 charon 75651 09[CFG] vici client 1273 disconnected
Jan 16 14:40:00 charon 75651 15[CFG] vici client 1273 requests: list-sas
Jan 16 14:40:00 charon 75651 11[CFG] vici client 1273 registered for: list-sa
Jan 16 14:40:00 charon 75651 11[CFG] vici client 1273 connected
Jan 16 14:39:55 charon 75651 15[CFG] vici client 1272 disconnected
Jan 16 14:39:55 charon 75651 11[CFG] vici client 1272 requests: list-sas
Jan 16 14:39:55 charon 75651 08[CFG] vici client 1272 registered for: list-sa
Jan 16 14:39:55 charon 75651 11[CFG] vici client 1272 connected
Jan 16 14:39:52 charon 75651 08[IKE] <con1|3> nothing to initiate
Jan 16 14:39:52 charon 75651 08[IKE] <con1|3> activating new tasks
Jan 16 14:39:52 charon 75651 08[NET] <con1|3> sending packet: from PROVIDER_WAN_IP[500] to AZURE_WAN_IP[500] (92 bytes)
Jan 16 14:39:52 charon 75651 08[ENC] <con1|3> generating INFORMATIONAL_V1 request 316903062 [ HASH N(DPD_ACK) ]
Jan 16 14:39:52 charon 75651 08[IKE] <con1|3> activating ISAKMP_DPD task
Jan 16 14:39:52 charon 75651 08[IKE] <con1|3> activating new tasks
Jan 16 14:39:52 charon 75651 08[IKE] <con1|3> queueing ISAKMP_DPD task
Jan 16 14:39:52 charon 75651 08[ENC] <con1|3> parsed INFORMATIONAL_V1 request 2810856974 [ HASH N(DPD) ]
Jan 16 14:39:52 charon 75651 08[NET] <con1|3> received packet: from AZURE_WAN_IP[500] to PROVIDER_WAN_IP[500] (92 bytes)
Jan 16 14:39:50 charon 75651 08[CFG] vici client 1271 disconnected
Jan 16 14:39:50 charon 75651 16[CFG] vici client 1271 requests: list-sas
Jan 16 14:39:50 charon 75651 16[CFG] vici client 1271 registered for: list-sa
Jan 16 14:39:50 charon 75651 16[CFG] vici client 1271 connected
Jan 16 14:39:48 charon 75651 11[IKE] <con1|3> nothing to initiate
Jan 16 14:39:48 charon 75651 11[IKE] <con1|3> activating new tasks
Jan 16 14:39:48 charon 75651 11[ENC] <con1|3> parsed INFORMATIONAL_V1 request 1390613614 [ HASH N(DPD_ACK) ]
Jan 16 14:39:48 charon 75651 11[NET] <con1|3> received packet: from AZURE_WAN_IP[500] to PROVIDER_WAN_IP[500] (92 bytes)
Jan 16 14:39:48 charon 75651 11[IKE] <con1|3> nothing to initiate
Jan 16 14:39:48 charon 75651 11[IKE] <con1|3> activating new tasks
Jan 16 14:39:48 charon 75651 11[NET] <con1|3> sending packet: from PROVIDER_WAN_IP[500] to AZURE_WAN_IP[500] (92 bytes)
Jan 16 14:39:48 charon 75651 11[ENC] <con1|3> generating INFORMATIONAL_V1 request 2462119987 [ HASH N(DPD) ]
Jan 16 14:39:48 charon 75651 11[IKE] <con1|3> activating ISAKMP_DPD task
Jan 16 14:39:48 charon 75651 11[IKE] <con1|3> activating new tasks
Jan 16 14:39:48 charon 75651 11[IKE] <con1|3> queueing ISAKMP_DPD task
Jan 16 14:39:48 charon 75651 11[IKE] <con1|3> sending DPD request
Jan 16 14:39:45 charon 75651 11[CFG] vici client 1270 disconnected
Jan 16 14:39:45 charon 75651 16[CFG] vici client 1270 requests: list-sas
Jan 16 14:39:45 charon 75651 06[CFG] vici client 1270 registered for: list-sa
Jan 16 14:39:45 charon 75651 06[CFG] vici client 1270 connected
Jan 16 14:39:39 charon 75651 06[CFG] vici client 1269 disconnected
Jan 16 14:39:39 charon 75651 16[CFG] vici client 1269 requests: list-sas
Jan 16 14:39:39 charon 75651 10[CFG] vici client 1269 registered for: list-sa
Jan 16 14:39:39 charon 75651 10[CFG] vici client 1269 connected -
@Matt_Sharpe said in IPSec DNAT not working:
Jan 16 14:40:07 charon 75651 12[CFG] remote_ts = 172.16.200.0/24|/0
Jan 16 14:40:07 charon 75651 12[CFG] local_ts = 172.16.200.0/24|/0Did you replace one of these wrongly?
Remote and local network cannot be the same. -
@viragomann It appears in the log several times, can you confirm what line number you're looking at? I have this open in N++
-
@Matt_Sharpe
Check your tunnel settings. Both local network or BINAT network must not overlap the remote network. -
@viragomann The VTI tunnel is set with a random/unique IP subnet we used for the VTI routing on both sides:
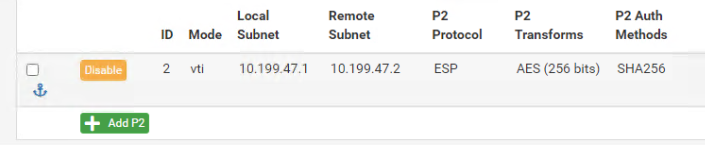
This doesn't overlap with any of the local/remote/isolated ranges?
-
@Matt_Sharpe
What's with the other tunnel? -
@viragomann The Azure tunnel?
-
@Matt_Sharpe
No, the one doing NAT.
But obviously you've deleted it already. So do you still see these log entries? -
@viragomann the other tunnel has been removed, as it impacts the live IPsec when enabled. If we tweak it to include the ranges in this forum post:
172.16.100.1 > IPsec tunnel > 172.16.200.253 (NATs to) 172.16.210.253
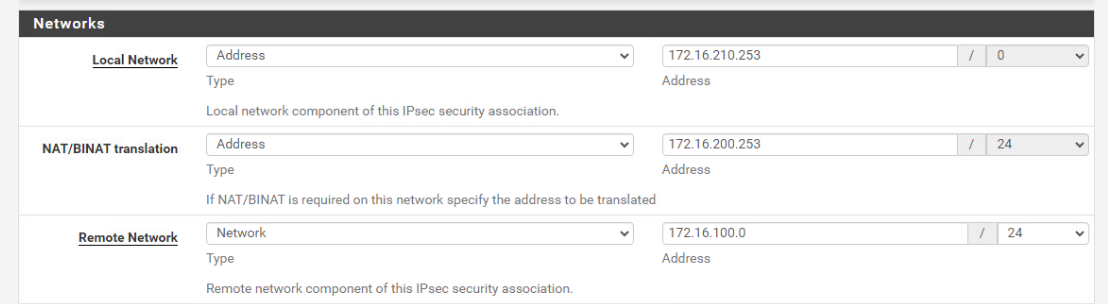
-
@Matt_Sharpe
This looks well for what you try to achieve.And I cannot find a hint for the disconnection of the other tunnel in the log.
But maybe there is an issue if you route the remote subnet over the VTI and also state it in the policy-based tunnel as remote network. -
@viragomann is there any other way we can achieve this? With native NAT rather than a profile on the IPSEC?
-
@Matt_Sharpe
I reread your intention. If your only aim is to access 172.16.210.253 from the remote site via RDP, it should also work with a simple NAT rule. You can add the rule to IPSec on pfSense like this:
interface: IPSec
source: may be limited to the remote network
destination: 172.16.200.253
redirect target: 172.16.210.253You can also limit it to RDP by stating
protocol: TCP/UDP
dest. and target port: RDPIt should also be possible to add this rule to the VTI IPSec interface instead.
If packets are coming in on IPSec interfaces addressed to the destination IP pfSense will redirect them to the target. The source IP in response packets will be translated back to the origin destination address due to the state table entry.
However, access in the other direction would not work this way, even not with NAT 1:1 or outbound NAT."Any" for interface as you mentioned above is not available in pfSense, however, you can create interface groups and apply rules to them. So the rules will be applied to all member interfaces of the group.
-
@viragomann I'm pretty sure I've already tried this as it's the most obvious solution:


How do we create interface groups?
-
@Matt_Sharpe found a deny in the logs from target NAT to source range IP. (Changed to our masked IPs in this forum post)

I do not have ANY deny rules set in IPsec interface, so why is it blocked??
-
@viragomann also TCP:SA packets blocked by same rule.

We have TCP IPv4 allowed in both directions, so why would it be blocked...
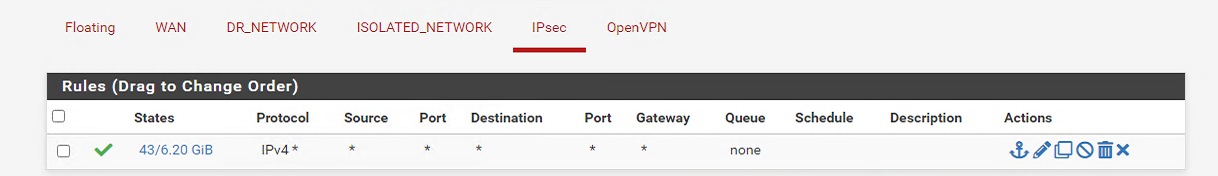
-
@Matt_Sharpe
Obviously pfSense has no proper state for the response. Search for it in Diagnostic > States.Is the RDP server on a remote site or is local?
How do we create interface groups?
Interfaces > Interface GroupsI assume, you won't use a group rule for this case?
-
@viragomann The RDP server (the target of the NAT rule) is in the same site as the PFsense we're applying it on.
No, not used for this case. Just curious for future use.
-
@Matt_Sharpe said in IPSec DNAT not working:
The RDP server (the target of the NAT rule) is in the same site as the PFsense we're applying it on.
Then I'm wondering, why a respond packet from the RDP server is shown up as entering IPSec.
So I'm out of ideas, what could be the reason for this blocks.
But you can probably circumvent it with a sloppy state rule (I don't like this):
action: pass
interface: IPSec
source: RDP server
source port RDP
destination: remote network
destination port: any
open the Advanced Options
at State type select SloppyI don't like it, but it should work.
-
@viragomann is that a NAT or FW rule?