Internet only subnet
-
@Bob-Dig
I have a dynamic IPv4 and 6 indeed. Now that you mention it; the gateway is indeed an fe80 address from my pfsense box.
What is the difference with the WAN_DHCP6 gateway?
-
@Bob-Dig said in Internet only subnet:
Think about it this way. If IPv6 traffic wants to go from LAN1 to LAN2, will it go through the WAN-gateway? Hint: No. After entering the firewall, it will go out at LAN2 directly, it will not hit WAN or the WAN-gateway at all. But is there a rule allowing that route? In my picture there isn't for IPv6, so it will get blocked.Now if IPv6 traffic wants to go to google.com, will it go through the WAN-gateway? For sure! Is there a rule allowing that? Yes, there is. -
@Bob-Dig
Thanks for the clear explanation! Learned a lot about the gateway configuration today! I'm going to apply it in my own network. IPv6 is still a learning curve for me in some ways, but I'm getting there :)
-
@gwabber said in Internet only subnet:
Thanks for the clear explanation! Learned a lot about the gateway configuration today!
To be honest, I realized, that my explanation was wrong,
the end result is the same though.Traffic will not be blocked at this stage, it will be forced through the wan gateway and then, I actually don't know. Maybe @johnpoz could enlighten us, after some coffee.Edit: I tested this further and pings still can cross over, so this might not work at all for IPv6...
-
@Bob-Dig then the only solution is to create a seperate rule for every subnet. Good thing is that I only have to do it once haha!
-
@gwabber so you don't want your internet only vlan to be able to go to any of your other networks via IPv6 either gua or ula?
The simple solution would be to just not allow IPv6 on this network.. Unless there was some IPv6 IP out on the internet that your internet only vlan/network needed to get to? Which i am not aware of a single resource where this is the case currently.
Just use IPv4 to let this network talk to anything.. Be it locally or on the interent. I wouldn't even give anything on this network an IPv6 address to be honest.
There are only a couple of devices on my network that even have Ipv6 addresses, I have not run into any resource on the internet that I can not get too.
Unless these devices on this network have need to connect to some internet resource that is only IPv6.. Which I am not aware of single major/popular resource where this would be the case.. Do they need to talk to some private website or something, where the host is behind a cgnat and can only publish via IPv6? Those would be really rare to be honest.. And very special use case.. If that was the case you could allow only IPv6 to that destination/prefix..
But if going down the road in your firewall rules where you allow this but block that, then yeah you're going to need more than 1 rule ;) The more specific your allow/deny rules are - the more you will need. You can't do everything with 1 rule when you are wanting to be specific on what is allowed or denied.
Having more rules is not going to slow down anything, nor is it going to make pfsense work harder, etc. Well it might be more work for you to set them up.. That is the nature of the beast when you are trying to be very specific in what you allow or deny.
-
@johnpoz thanks for your reply!
I indeed don't need any V6 networking on that VLAN, It works fine with V4. The reason I want to try it, is because I want to learn how to setup IPv6 and how the config is different from V4.
For now I just leave it as is with IPv4, but I will make a seprate subnet to fiddle arround and see if I can create what I want with v6 :) -
@gwabber If its just a learning thing, there isn't much to learn really.. just create the rules you want.. There are many ways to skin the cat.. But again, the more specific you get with your allow/deny rules - the more rules you are going to have.
if you want to allow specific this, and block specific that your not going to be able to do it with 1 rule ;)
And to be honest, what does it matter if you have 10 rules or a 100 rules.. The more explicit the rules are, the more control you have - and to be honest the easier it is to read the rules.
Creating rules with a aliases that allow this port and that port, and these Ips while ok can keep trim down your rules.. But why? When now when looking at them you have to figure out what exactly is in this alias, what is in that alias, etc.
Just create your rules as specific as you want.
if you don't want your specific network to be able to go to your wan IP address.. Then use the wan address in your firewall rule - this would include ipv6 and IPv4, be it gua or ula.. And if its link local, doesn't matter device on lan can not talk to the link-local address of the wan.
While you could prob combine that into a IPv4+6 rule, if your goal is learning IPv6 - I wouldn't use combination rules, and would keep my IPv4 and IPv6 rules separate
-
-
@Bob-Dig policy routing is going to force traffic only to that gateway.. Yeah that would block access to your other IPv6 networks, because your gateway your sending the traffic to can not get there.
That would be the same for IPv4 or 6..
Like I said there are many ways to skin the cat, you could have 1 set of rules that skins it one way, and another set of rules that skins it a different way.. You still end up with the same skinned cat ;)
I personally wouldn't do it that way.. I like to be very explicit in what rules do, so the goal is easy to see.. Forcing traffic out a specific gateway might accomplish blocking client X from talking to destination Y.. But its not really clear that was the goal to the rule.. But if I have a specific rule that says X can not talk to Y.. Then its very clear what the point of that rule was.. Vs just a policy route - was the goal to block x from talking to y, or was the goal just to send traffic out a gateway.. Blocking x to y could be a byproduct of the rule - but is that something they actually wanted, or just something that happened.
Explicit rules are always best.
-
@johnpoz said in Internet only subnet:
policy routing is going to force traffic only to that gateway.. Yeah that would block access to your other IPv6 networks, because your gateway your sending the traffic to can not get there.
But it is not working like my intention was. At least with ping, I can ping from my PC devices in the other subnet via IPv6 and vice versa...
-
@Bob-Dig you sure you don't have an existing state? Or a rule say in floating that allows it..
A ping to a dest where the pinger rules does not force out a gateway, would allow the return traffic even if where your pinging had a rule to force out a gateway.. because the state would be evaluated first, etc.
-
@johnpoz said in Internet only subnet:
you sure you don't have an existing state? Or a rule say in floating that allows it..
Yep, nothing.
-
@Bob-Dig It would take me a bit to duplicate the IPv6 stuff..
But can easy duplicate a policy route with IPv4 gateway..
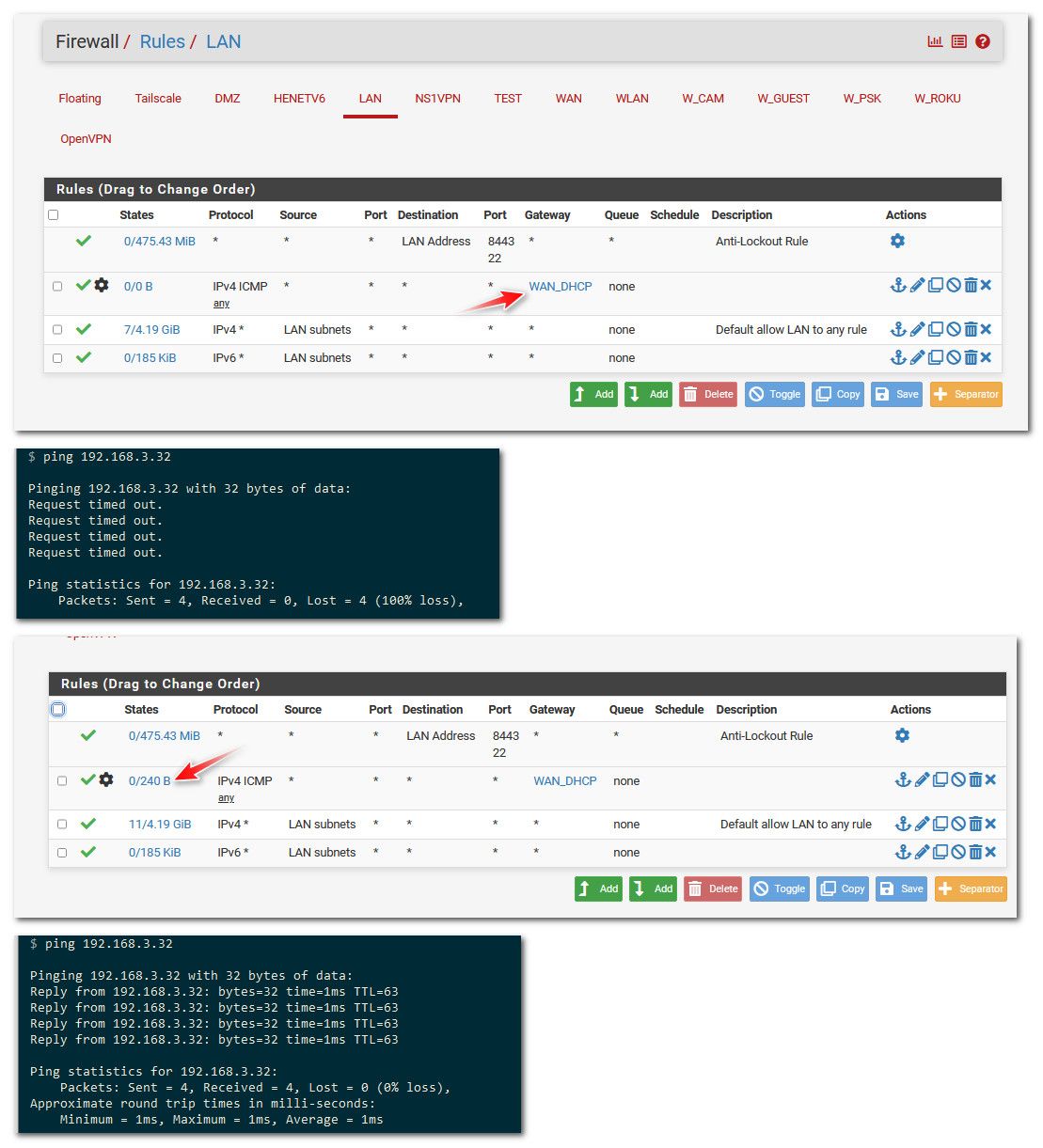
Create a policy route rule to send traffic out my wan dhcp gateway..
I can not ping device on my other network.
Notice the rule has been evaluated.
Remove the rule and now I can ping..
-
@johnpoz said in Internet only subnet:
It would take me a bit to duplicate the IPv6 stuff..
I wanted to try some linux machine but they all don't get an IPv6 address with their configuration so I am stuck with my windows machines for this test. But at least here it stands.
Now if you want to test this you probably have to disable the patch from the other thread but I am sure you have read this today.
-
I guess I can do both... create rules to block traffic to my other subnets and a policy rule for the gateway. At least I have stuff to tinker with now!
Thanks!
-
@gwabber said in Internet only subnet:
and a policy rule for the gateway. At least I have stuff to tinker with now!
If you want to tinker, try if the policy rule alone is preventing the crosstalk of the subnets with IPv6. For me it is only for IPv4 but my network is complicated.
-
@Bob-Dig Gonna do that after the weekend! I will let you know!
-
@Bob-Dig sorry for my late reaction. Work was busy. The gateway rule does the trick with me!