Can pfSense's DHCP server (securely) update Microsoft DNS?
-
I'm also interested in knowing whether dynamic updates of a MS DNS server would be possible from a pfSense DHCP server.
And for those that are curious, we have many site-to-site TUN VPN connections (something outside of my ability to change). From my reading this type of VPN tunnel does not allow for DHCP broadcasts so instead I wanted to see if it's possible for the client-side pfSense DHCP service to update the remote MS DNS server with the DHCP leases that it hands out. And yes, MS clients will automatically handle their DDNS registrations, but there are other non-MS clients that would have to rely on the pfSense DHCP server to do that for them. This would save me a lot of typing from adding DNS entries manually…
thanks,
Mike -
From my view this topic is still unaswered.
All related topics are only targeting at not to register dhcp clients in MS DNS.
But thats exactly what some users seem to need in some situations.I tried running DNS on pfsense as well, but unbound crashes really often when performing zone transfers. I need unbound and cannot use bind instead because I'm using pfblocker to filter public DNS. So in my environment it makes sense to keep local DNS Zone on the existing AD Servers.
-
@tomahawk said in Can pfSense's DHCP server (securely) update Microsoft DNS?:
I tried running DNS on pfsense as well, but unbound crashes really often when performing zone transfers. I need unbound and cannot use bind instead because I'm using pfblocker to filter public DNS
Checkout https://en.wikipedia.org/wiki/Comparison_of_DNS_server_software
Bind is capable of doing what you want, as it is designed to be an "Authoritative server" : it can do zone transfers.
Unbound can do some of the tricks of what bind does : resolving, DNS caching (and others), but, as you can see :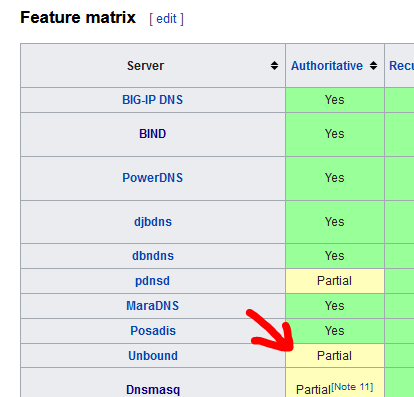
Btw : I guess I have to ask this question several times a day : how often does your unbound restart each day (hint : the logs ...).
If some transfer is in progress (dono how that works for unbound) and it gets kicked around(restarted) then yeah, no good.Keep in mind that unbound was used for pfSense so the 'network' has a centralized, DNSSEC capable DNS cache and resolver. No special settings needs. It works out of the box.
Just perfect for pfSense.
Most probably, Netgate's developers didn't have in mind that interfacing was needed with "AD Servers".Btw : Unbound is build, designed, maintained and upgraded here : https://www.nlnetlabs.nl/projects/unbound/about/ as Netgate did not write this thing, a project as big as pfSense itself.
-
@tomahawk said in Can pfSense's DHCP server (securely) update Microsoft DNS?:
From my view this topic is still unaswered.
All related topics are only targeting at not to register dhcp clients in MS DNS.
But thats exactly what some users seem to need in some situations.I tried running DNS on pfsense as well, but unbound crashes really often when performing zone transfers. I need unbound and cannot use bind instead because I'm using pfblocker to filter public DNS. So in my environment it makes sense to keep local DNS Zone on the existing AD Servers.
If you have a MS DNS server, why not also use the MS DHCP service? MS DHCP can seamlessly update MS DNS in a secure fashion.
So disable DHCP on pfSense and enable it on the MS server, then your LAN clients will use the MS DHCP server which will seamlessly update DNS if you also enable that on the Microsoft side.
As for using pfBlocker and
unbound, simply configure your MS DNS server to be a forwarder and to forward external DNS requests (i.e., for zones it is not authoritative for) tounboundon pfSense. Thenunboundis configured to resolve (which is its out-of-the-box configuration anyway). -
@tomahawk said in Can pfSense's DHCP server (securely) update Microsoft DNS?:
From my view this topic is still unaswered.
Hello!
John
-
https://japtaincack.blogspot.com/2018/02/pfsense-dhcp-dynamic-dns-updates-to.html
I think this is what you want.
-
Here's another use case that the suggestions provided don't address.
pfSense is the main router for a home Internet subscription which has dynamic IP through PPPoE.
There's an FTP server sitting behind the pfSense router which needs the WAN interface IP to properly process passive mode transfers. This can be configured using a host name but the host name has to resolve to the WAN interface address.
The LAN side of the network (where the FTP server sits) is serviced by a MS DNS server, which hosts the same zones as the ones updated by pfSense's Dynamic DNS service on the WAN side. Local clients get local addresses from the local MS DNS server while public clients get the WAN address from public DNS servers. The local MS DNS server forwards requests for zones it doesn't host to public DNS servers but, since the same zones are used internally and externally, it never forwards requests for the zone used to the public DNS servers.
Ideally it would be possible to setup the pfSense Dynamic DNS engine to update a specific host name on the local MS DNS server with the WAN IP. the FTP server could then reference that host name to get the WAN IP and process passive mode requests properly. DHCP is not in use in this use case therefore the solution linked by @Volans doesn't apply.
-
@IamGimli If I’m following correctly, can a CNAME be set up to point wan.example.com to the dynamic DNS hostname? Or use the latter directly? Which isn’t what you asked but gets to the same place.
There are detection sites like checkip.dyndys.com. I would think a script on the server could detect the IP and create/update an A record in DNS.
https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/dnscmd#dnscmd-recordadd-command -
Both internal and external zones have the same name so a CNAME in the internal zone will resolve to the internal IP.
Let's say Dynamic DNS sets WAN.example.com on the outside zones. The internal zone would either resolve WAN.example.com to the local address of an internal system (whatever is set by CNAME) or return a non-existent record. The local DNS server would never forward the request to an external DNS server because it hosts a zone called example.com.
-
@IamGimli I’m suggesting something like
Dyn: wan.dynprovider.com
Internal: wan.example.com CNAME wan.dynprovider.com
External/public: wan.example.com CNAME wan.dynprovider.com
That needs the third party dyn though.
Alternatively, it should work to create zone wan.example.com on Windows and delegate to public DNS/NS via NS records. Which needs wan.example.com to resolve there as well.
-
As there was no option covering all my use cases I decided a full redesign of my DNS setup. (but it is quite komplicated if you want to use all features like I do)
I am now running a BIND on top of PFSENSE as primary server for my internal DNS Zones. The MS DNS gets a copy of it using Zone Transfers.
All MS AD Zones like "_msdcs" or "_tcp" are deligated to the MS DNS server to be the primary and the BIND gets a copy of them using Zone Transfers.
The DHCP is configured to update Subdomain(s) primary hosted by BIND - works well.As I wanted to use DNS Filtering using PFBlocker I also needed to have Unbound in place.
Unbound is configured to be the primary DNS for all DHCP clients. (this allows per client logging and blocking/unblocking)
It gets a copy of the Internal Zones using Zone transfers (from MS DNS and from BIND.
MS DNS and BIND DNS are forwarding all requests for non-local domains to the unbound. (so they are getting filtered, too)This setup is running stable since some time.