Route subnet through VPN Client - Outbound NAT
-
Hi Forum
I have a torguard VPN - that I'd like to move from a VM to be handled by PFsense.
My Public IP is handled by the ISP as DHCP statis lease.
Following the link from Torguards own GuidesI have a couple of LAN and VLANS running- but will only allow 1 subnet 172.16.40.0/27 (VLAN40) to access the Internet through the Clients.
I've created the VPN client and can activate it so it's working - but not as intended.
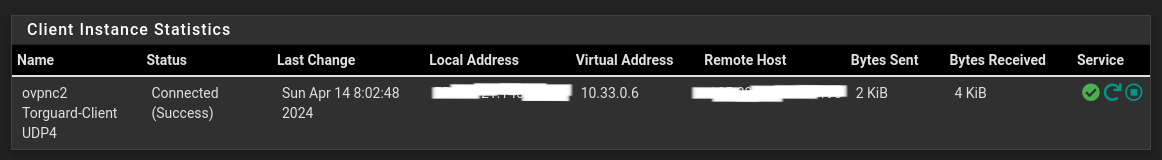
Adding as Interface
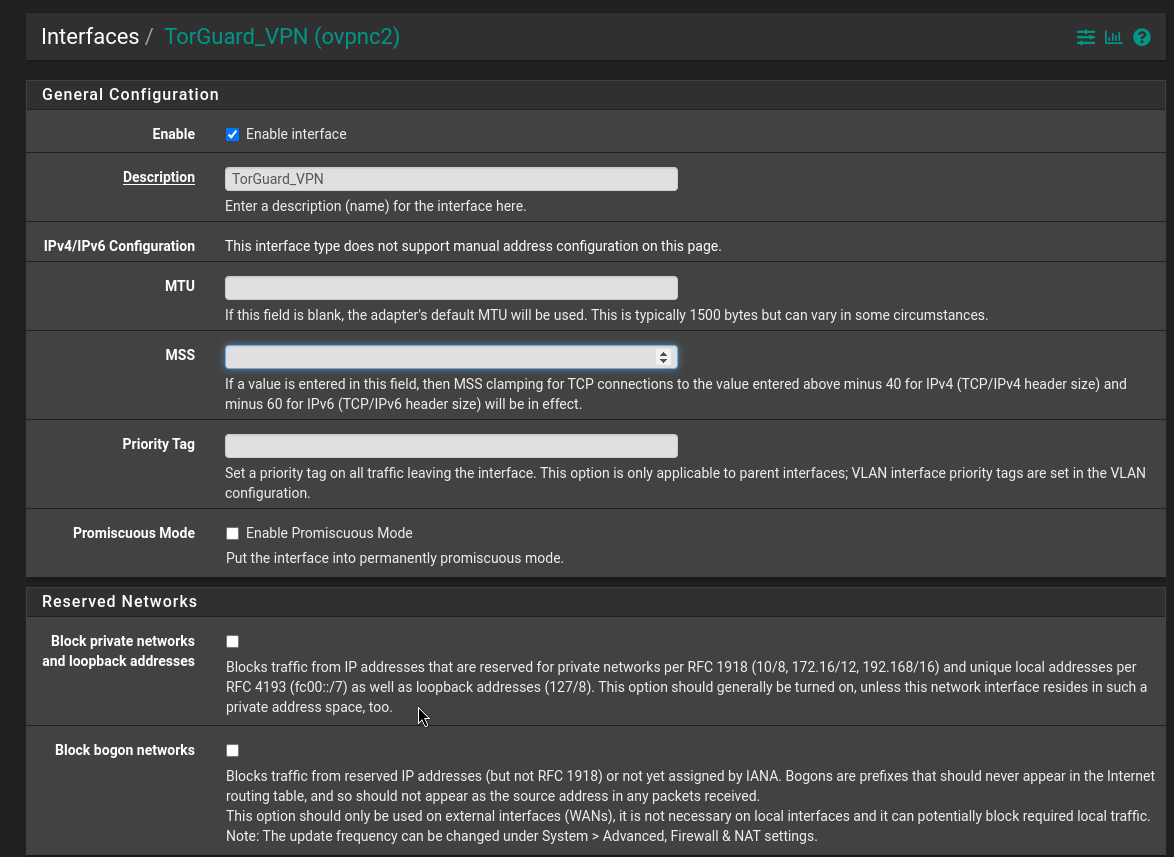
I've added the subnet and the VPN client.
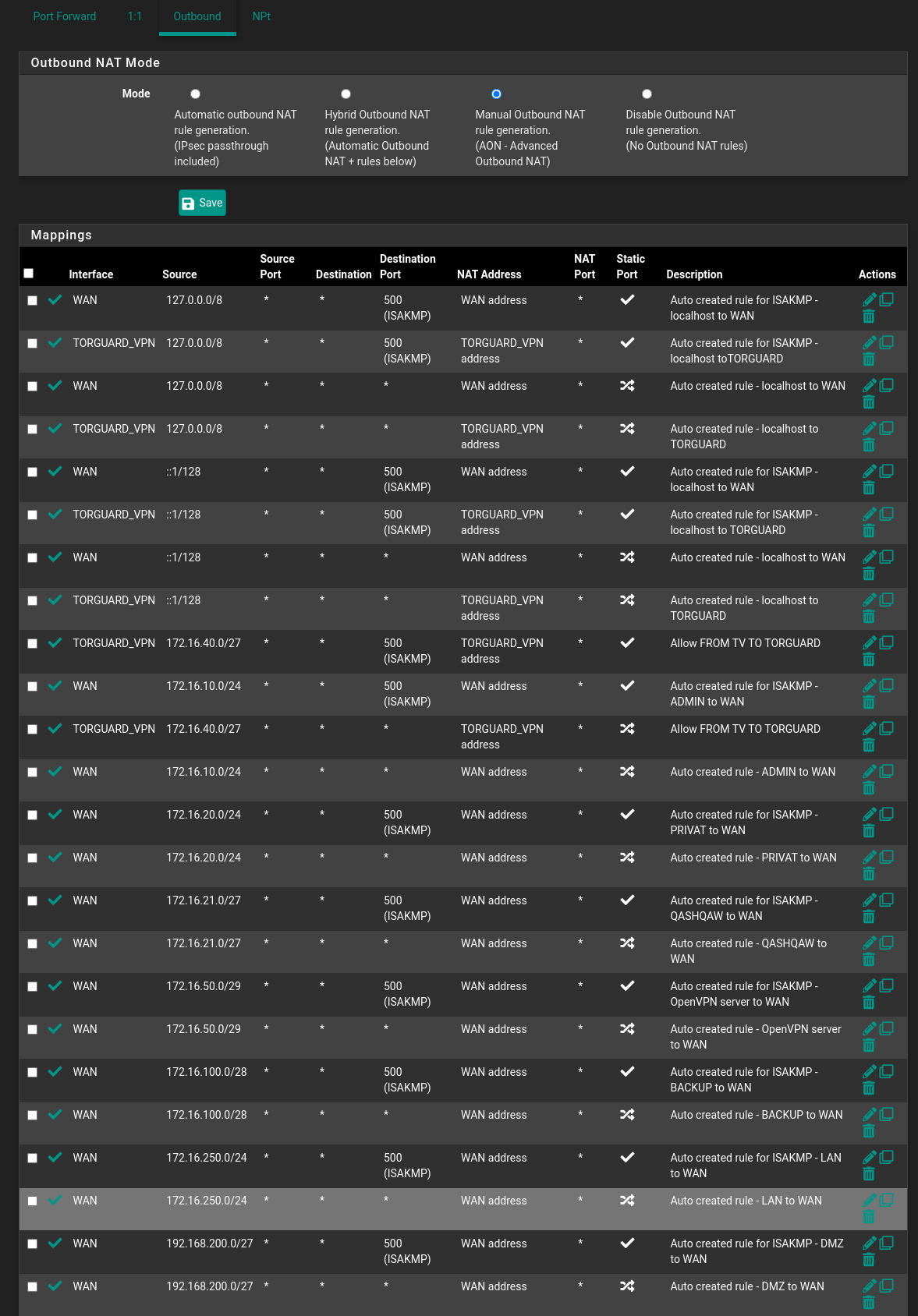
I've added outbound NAT - but properly here something goes wrong since the guide - one described allow all traffic through VPN - which is not the same as I want. I only want the single subnet running through the VPN and not all. Since when I changed it from Hybrid Outbound NAT to Manual Outbound NAT - there is a lot of extra entries that I'm not sure of - should all of these be there if only VLAN40 ashould be allowed out through the Client - where everything else is in the normal WAN connections
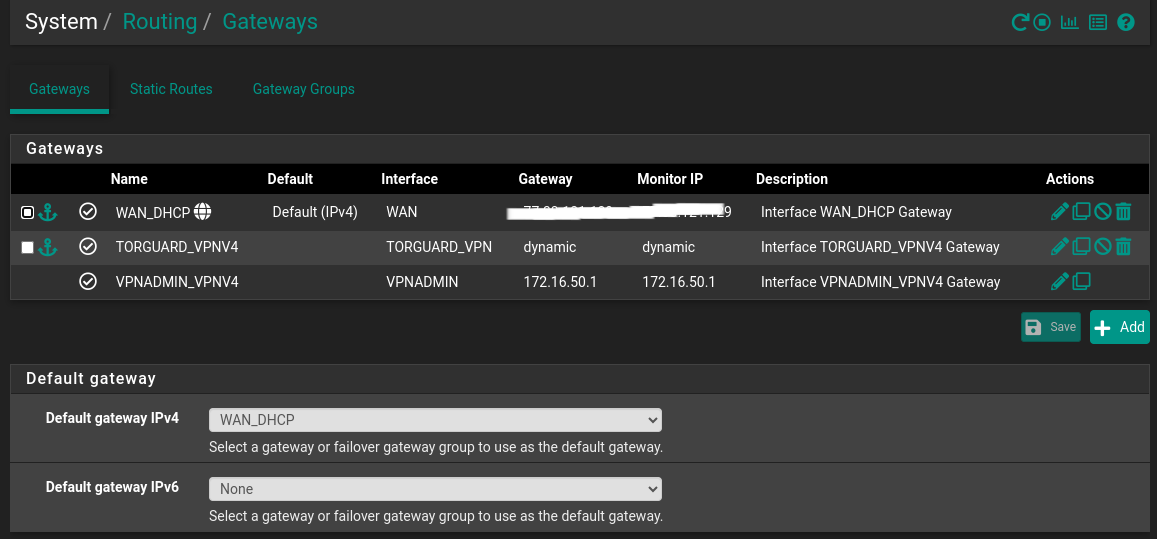
And the Gateways are set as this:
But when I'm enabling the VPN client - its working - since the TV Subnet are working - getting the right Public IP for this subnet.
From all other Interfaces - it'll look as I'm missing some kinds of route or elseEnabling the VPN client:
Logging in to PFsense - I can ping outbound.
Can not ping or traceroute from all other subnets that TV -Disabling the VPN client
No traffic on VLAN40 (offcarse)
All other interfaces worksSo any help are appriciated - regarding these outbound NAT rules so I can make it work.
/P
-
@Udbytossen
When you want only certain subnet to go out over the VPN, you have to policy route them.In the actual state, I guess, the VPN server pushes the default route to the client, hence all upstream traffic is sent to Torguard, but you only have outbound NAT rules for VLAN 40 and pfSense itself.
To avoid this go to the VPN client settings and check "Don't pull routes".
Then add a policy routing rule to the TV interface to direct all upstream traffic to the VPN gateway.BTW: There is no need to set the outbound NAT into manual mode. Just set the hybrid mode, so you can add rules for your needs as well.
-
@Udbytossen policy routing docs: https://docs.netgate.com/pfsense/en/latest/multiwan/index.html
-
@viragomann
Thanks for the reply.
Changed the settings to hybridI'm in doubt when you wrote:
Then add a policy routing rule to the TV interface to direct all upstream traffic to the VPN gateway.
I'm not sure what you mean here - or how to do it right - can you explain it a little more ?From the manual
Since I've tried setting the gateways on the rules under Firewall Rules TV

THe rules can here be set on either
Floating - WAN - TV or TorGUARD_VPNThanks
-
@Udbytossen
In the rule for allowing access to "TV address" you have to remove the gateway.Did you check "Don't pull routes"?
-
@viragomann
Hi and thanks again for replying. As I've tried this for some time now - and are properly as confused as a chicken - so I do appriciate your input. At this point I can not figure out what I have already tried while getting this up.
Yes I did check the don pull route:

Created TV as Interface

Created the Torguard as an Interface

Changing my Outbound NAT from Manual to Hybrid - and are now looking like this:

Rules for my TV interface:
Reading the link from SteveITS - makes me actually more confused - since It also where I read regarding the policy Routing (But I cannot see the red line in this)
The TV Rules Now:
And for TV it'll look like this now - loowing the traffic against external DNS and NTP :

But no rules under the Torguard Interface - I've also tried setting a rule on Torguard Interface - that if the source is NOT from TV - block - but still nothing gets througfh the VPN client.

As I get this:
This could only be an issue on the routing siince the traffic is getting out but on the wrong interface -
@Udbytossen said in Route subnet through VPN Client - Outbound NAT:
The TV Rules Now:
And for TV it'll look like this now - loowing the traffic against external DNS and NTP :Policy routing DNS and NTP to the VPN gateway is only meaningful if either
- the TV is configured to use public servers for this or
- you forward DNS and NTP requests from the TV to a public server.
Is any point of these applied?
If not both will fail.Normally the TV uses the router (pfSense) for DNS and NTP. Forwarding DNS to a public DNS server is useful to avoid DNS leaking, if this is necessary.
Forwarding NTP makes no sense at all.So I recommend to remove the NTP rule and disable the DNS rule for testing.
Your first common rule allows both protocols to pfSense.
If you have issues due DNS leaks later, forward it to a public service or even to the VPN providers DNS server.
Maybe you should also remove the "Pull DNS" check in the OpenVPN settings. -
@viragomann
Hi agianNormally on my other zones I'm blocking outside DNS and ntp request. So this was yet another try -. where the confusion is total :-(
So changing the TV rules so they look as this

Unchecking "Don't pull routes" makes the traffic from VPN work - getting the right IP from the VPN - and the TV subnet work .
But then all other subnets are now not working outside my PFsense - can't ping or traceroute anything outside my PFsense.
Only the TV subnet are now working - So I guess some rules are working.
The gateways still looks like this

So Activating the "Dont pull Routes" - make the VPN up - but don't route anything from TV through the VPN - only through own Public IP - using curl ipinfo.io as do all the Subnets
Deactivating make the TV VPN works - but all other subnets are not working - and getting stop after reaching my pfsense using traceroute and times out.But After editing my Torguard GW and did this:

With both Gateway monitoring disabled (Don't understand why - but do not work if I remove it)
And the Static Route - saying do not add static route.And that did the trick (and still haven't the Do not pull Route under the VPN client unchecked )
- and for some reason that I do not get - but it'll looks like it works
-
@Udbytossen
Yes, this was my next thought. Checking Status > Gateway.
The VPN gateway has to be shown up as online for the policy routing rule to work.With both Gateway monitoring disabled (Don't understand why - but do not work if I remove it)
If the gateway status is offline, it means that the gateway is not responding to the monitoring pings.
If you need to know the gateway status for failover or whatever, you can state any other public IP for the monitoring in the gateway settings, which is responding to continuous pings, e.g. 1.1.1.1. This IP will be routed over the VPN than, so the monitoring gives a proper feedback. -
@viragomann
Super - and thanks for the patience anf final explanations
anf final explanations