GRE Tunnel using Proxy ARP
-
The basic problem here is that you're trying to use something that is expected to be in the same layer 2 but route it across a layer 3 tunnel.
So the two solutions would be to either make it routed properly as I suggested in the other thread. Or to switch to a completely layer 2 setup using something like OpenVPN TAP mode and bridges.
You said you tried to add the gateway as outside the subnet and it didn't work?
-
@stephenw10 How would it work by making it go over a complete layer 2 using OpenVPN in TAP mode?
Yes, it basically considers the gateway as non-local but doesn't work.
We've tried using Wireguard before but it just went deprecated, so any idea on the OpenVPN? I would need to close the GRE tunnels and make everything go through the vpn?
Best regards
-
Wireguard is not deprecated but it is layer 3. It won't help here.
To use OpenVPN create the tunnel with both ends configured in TAP mode. Then bridge the remote end to the WAN and the local end to the LAN. The local LAN will then be in the same layer 2 segment as the VPC side WAN so devices will see each other and everything will use the VPC side gateway directly. The local LAN could use one of the available IPs you have or have no IP address if the local pfSense does not require access to the subnet directly.
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-bridged.html
-
@stephenw10 Ok, so if I'm getting this right, my local pfsense should connect to the OpenVPN as a TAP client and get the openvpn interface assigned to the lan 185.113.141.0/24 network?
-
It doesn't matter which end is client but I would probably choose the local end, yes.
The OpenVPN interface is not assigned as LAN. You have to bridge it to the LAN by creating a bridge and adding both LAN and OpenVPN to it. At the other end it's bridged to the WAN.
How much latency is there between the pfSense instances? High latency across a layer 2 link can cause problems.
-
@stephenw10 Whenever I start the OpenVPN interface, after a few seconds it just stops my connection to pfsense, any idea why?
The latency is 9ms. It always worked fine, without any issues...
-
@Xuap Just forget the part where it stops my connection. It was lacking the port 80 pass rule loool
-
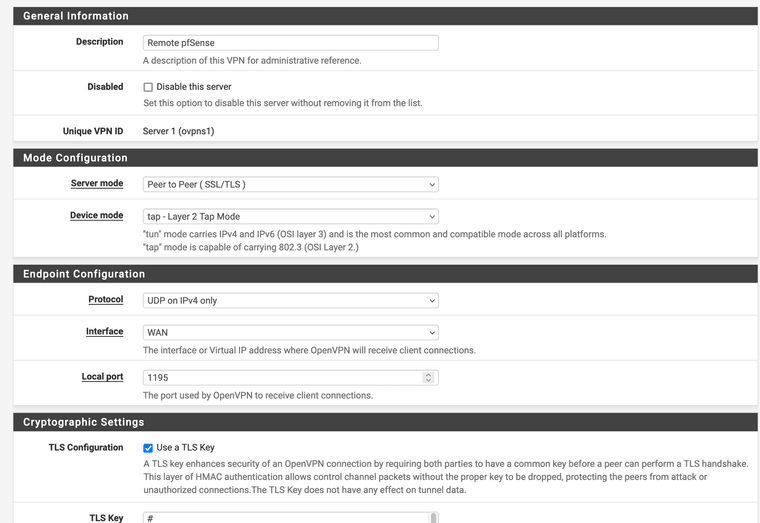
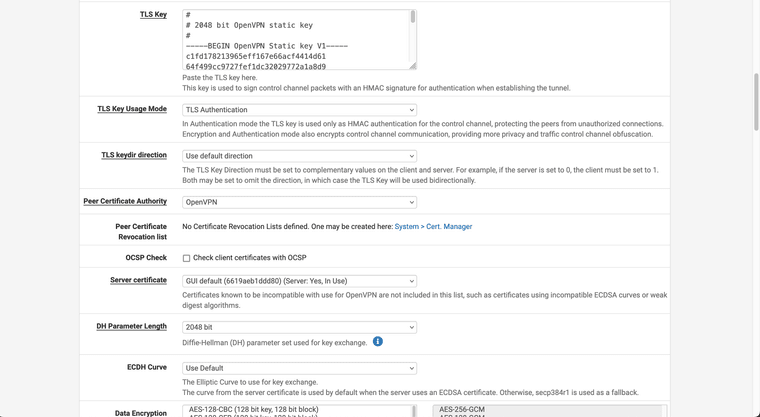
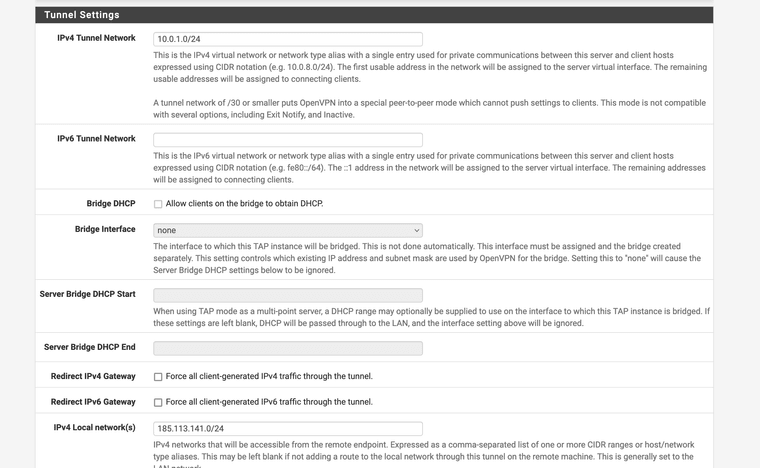
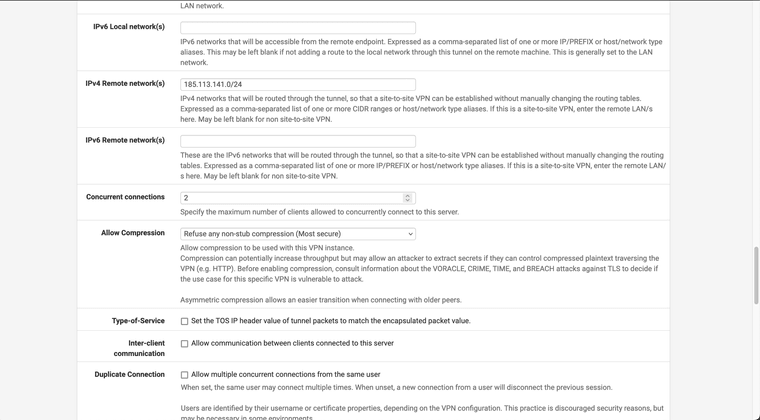
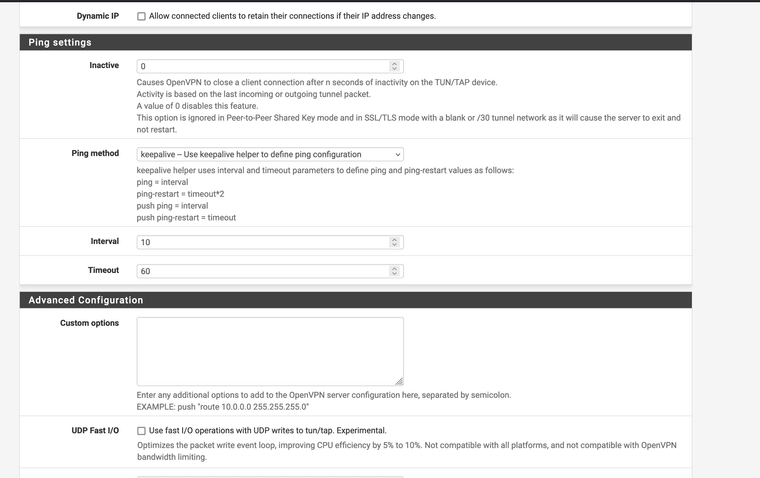
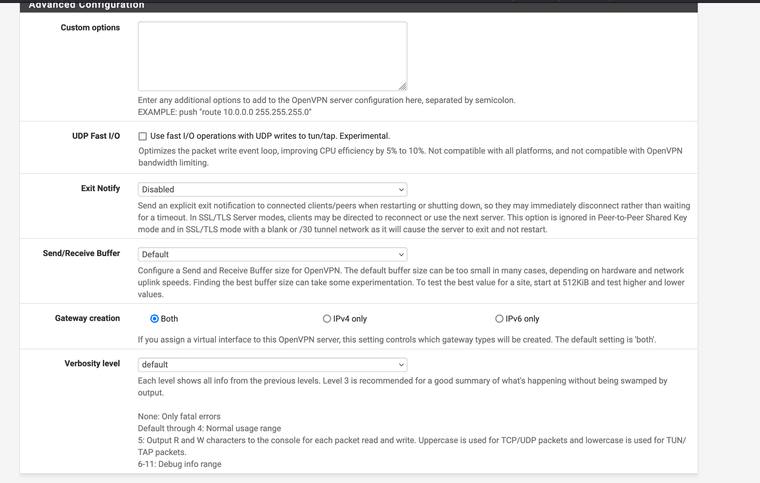
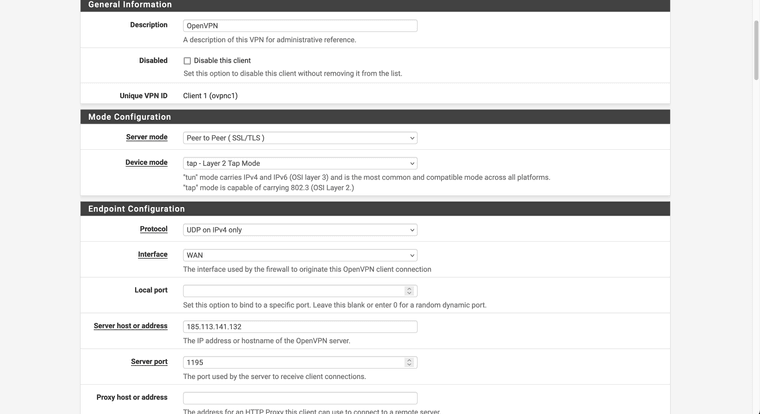
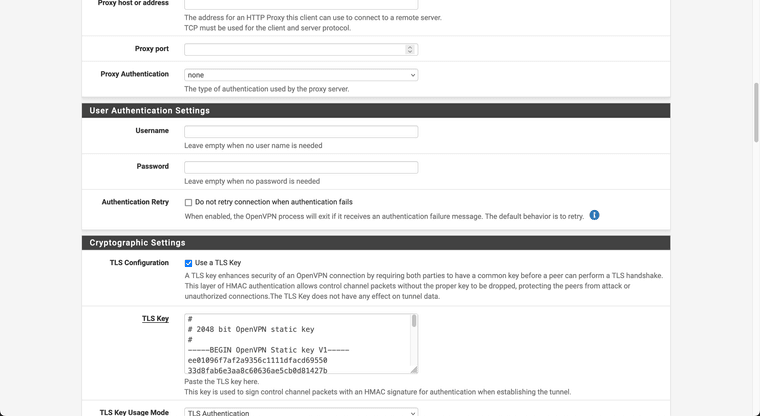
@Xuap Ok.. so I tried creating the tunnel as follows:
Remote

Local
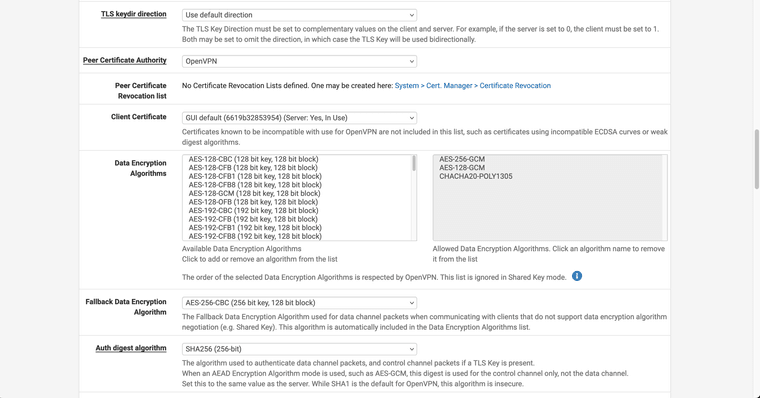



Local pfsense rules:
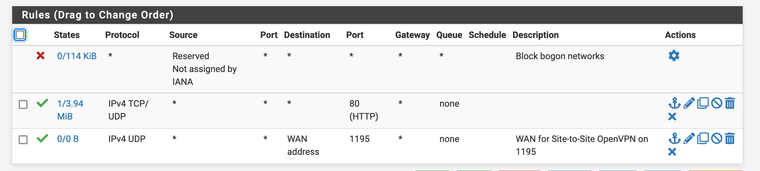
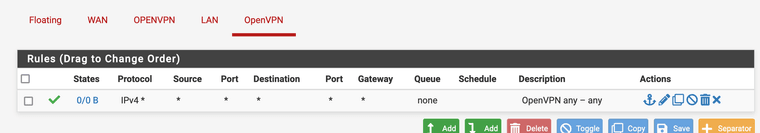
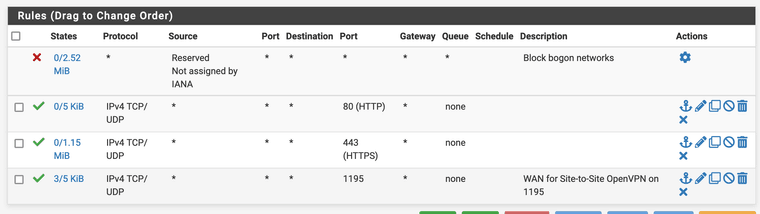
Remote pfsense rules:
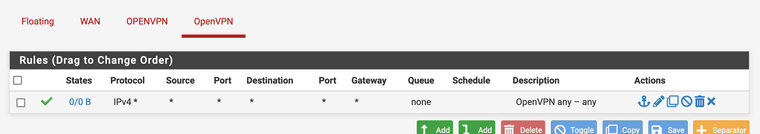
Any error here?
Because the status is just that it don't connect...
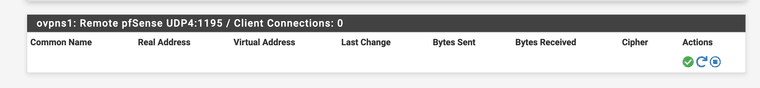
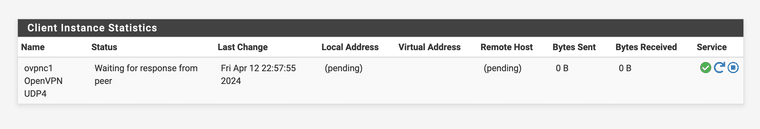
-
@stephenw10 Any idea?
-
@Xuap I tried the same setup as you and got the same problem.
-
Sorry missed the replies here.
It looks like you're using the webgui cert as the server cert? It has to be a cert created against the server CA.
It also looks like the TLS key is different. Both ends must have the sane TLS key.
You also still have a bunch of routed tunnel settings like pushing routes and adding gateways. But I'd fix up the cert/key first before looking at that.
Steve
-
 S stephenw10 referenced this topic on
S stephenw10 referenced this topic on







