LDAP Authentication with Active Directory Windows Server 2025, bind fails
-
Hello,
Can anyone confirm that LDAP authentication works with Active Directory of Windows Server 2025 ? I can access and use the LDAP on all of my other services like proxmox etc but pfsense refuses to bind.pfsense can ping the windows server and there is no firewall rule restrictions.
Current Settings below:
host: 192.168.1.32 Port: 389 Transport: Standard TCP Peer Certificate Authority : Global Root CA list Client Certificate: None Protocol version: 3 Server Timeout: 25 Search scope Level: Entire Subtree Base DN: DC=ad,DC=my,DC=org Authentication containers: OU=den;CN=Users;DC=ad,DC=my,DC=org Extended query: Disabled Bind anonymous: Disabled Bind credentials: CN=administrator,CN=Users User naming attribute: samAccountName Group naming attribute: cn Group member attribute: memberOf RFC 2307 Groups: Disabled Group Object Class: posixGroup Shell Authentication Group DN: UTF8 Encode: Disabled Username Alterations: Disabled Allow unauthenticated bind: DisabledApr 17 02:56:16 php-fpm 307 /diag_authentication.php: ERROR! Could not bind to LDAP server AD. Please check the bind credentials. Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: LDAP connection error flag: false Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: Group Filter: Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: Filter: (samaccountname=Administrator) Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: Extended Query: Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: Attrs: Name: samaccountname / Group: memberOf Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: Container: OU=den;CN=Users;DC=ad,DC=my,DC=org Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: Auth Bind DN: CN=administrator,CN=Users,DC=ad,DC=my,DC=org Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: Scope: subtree Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: Base DN: DC=ad,DC=my,DC=org Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: URI: ldap://192.168.1.32:389 (v3) Apr 17 02:56:16 php-fpm 307 /diag_authentication.php: LDAP Debug: Attempting to authenticate Administrator on AD -
It probably requires an encrypted connection, so STARTLTLS or LDAPS. See:
https://docs.netgate.com/pfsense/en/latest/usermanager/ldap.html#adding-an-ldap-serverSteve
-
After a sleepless night with lots of troubleshooting, I managed to fix the issue. Anyone who came across this can try the below.
Apparently for some reason pfsense and DC fails to negotiate a proper signing requirements.
I noticed this after inspecting the packet captures which gives me an "unknown CA" error when trying to use SSL.After modifying the Domain Controller Policy like below, it works now both with SSL disabled and enabled.
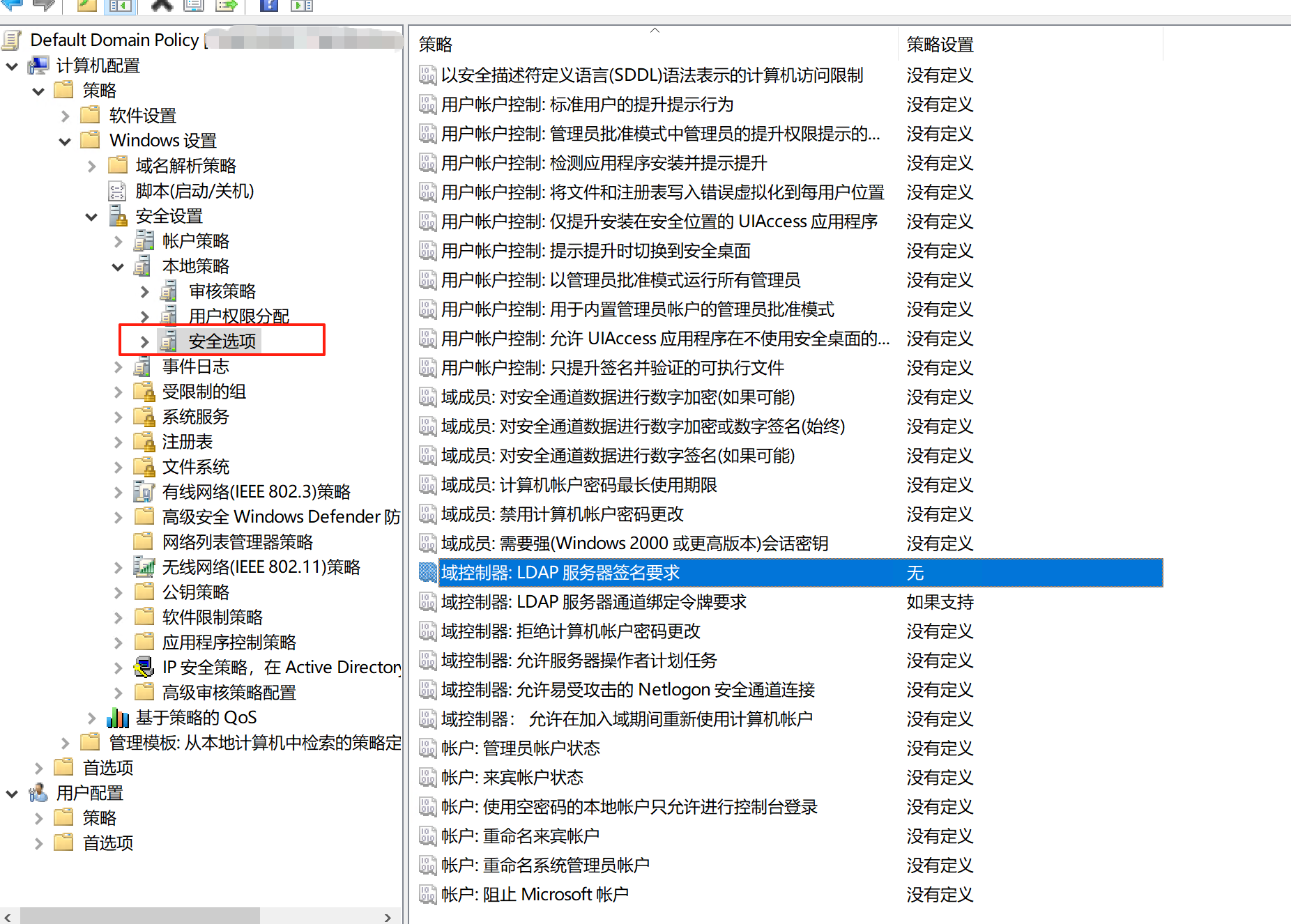
Domain Controller Policy
===Computer Configuration
======Policies
=========Windows Settings
============Security Settings
===============Local Policies
==================Security Options
=====================Domain controller: LDAP server channel binding token requirements: "When Supported"
=====================Domain controller: LDAP server signing requirements: "None"
=====================Domain controller: LDAP server Enforce signing requirements: "Disabled"
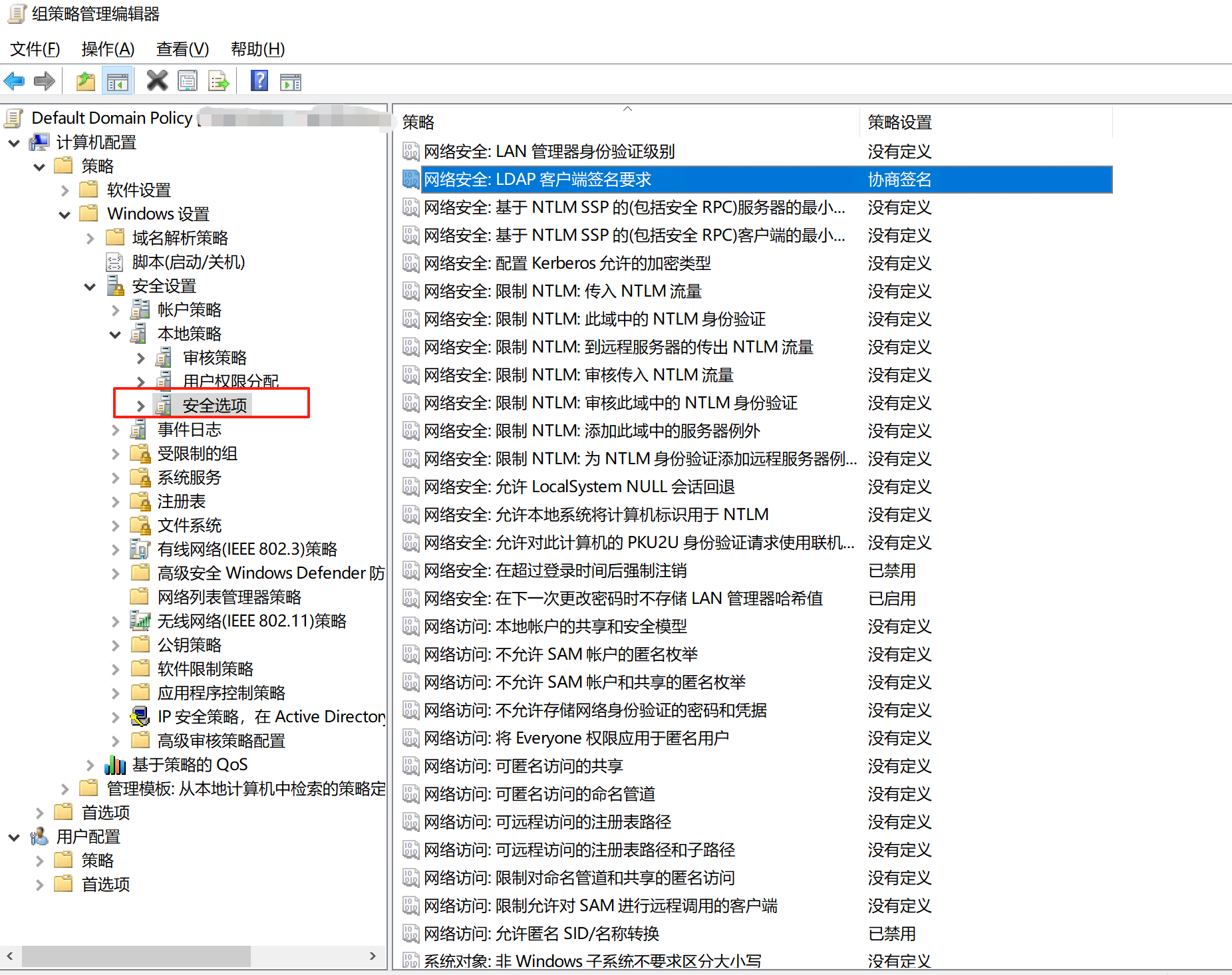
=====================Network security: LDAP client encryption requirements: "Negotiate Sealing"
=====================Network security: LDAP client signing requirements: "Negotiate Signing" -
@stephenw10 Thanks for the input and you were very close but even after setting the SSL with proper certs, I was not getting it through without the above mentioned DC settings.
-
An update after further testing, details below:
After getting the unencrypted TCP working reliably, I wanted to verify the SSL with LDAPS and noticed that the SSL auth was randomly failing with the same bind error. I could not fix this one no matter what I tried and eventually it started failing all the LDAPS binds.
Everything works fine with LDP and Apache Directory Studio but for some reason pfSense just does not want to work with SSL.
I use LE certs on my server and in theory the LE CA should work since it is working in every other application like LDP and Apache Directory Studio.
The only major change to pfsense was the updated OpenSSL package. Might it be possible that this is the reason? If anyone can confirm that I would be happy to open a bug report but I don't want to waste anyone's time over there if this is a configuration mistake on my part.
Packet capture shows TLS 1.3 auth -
@Laxarus said in LDAP Authentication with Active Directory Windows Server 2025, bind fails:
After a sleepless night with lots of troubleshooting, I managed to fix the issue. Anyone who came across this can try the below.
Apparently for some reason pfsense and DC fails to negotiate a proper signing requirements.
I noticed this after inspecting the packet captures which gives me an "unknown CA" error when trying to use SSL.After modifying the Domain Controller Policy like below, it works now both with SSL disabled and enabled.
Domain Controller Policy
===Computer Configuration
======Policies
=========Windows Settings
============Security Settings
===============Local Policies
==================Security Options
=====================Domain controller: LDAP server channel binding token requirements: "When Supported"
=====================Domain controller: LDAP server signing requirements: "None"
=====================Domain controller: LDAP server Enforce signing requirements: "Disabled"
=====================Network security: LDAP client encryption requirements: "Negotiate Sealing"
=====================Network security: LDAP client signing requirements: "Negotiate Signing"@Laxarus, your solution works like a charm here! Wouldn't have found this without your help! Thanks a lot for sharing!
-
@Laxarus Thanks for the help my friend. It helped me a lot!! After 12 hours of migrating 4 domain controllers, I almost hit the rollback button until I saw your tip. I tried this and it worked for two systems that had problems. The only two systems that we could not test in our lab environment.
-
My operating system is Windows Server 2022. I noticed that the default group policies of my domain controller are somewhat different from yours. Currently, I'm also having issues with failing LDAP connections via ports 389 and 636, but I can connect successfully using GSS-API SASL. I almost gave up, but after seeing your post, I've regained hope. Since various systems currently only support connections via port 389 or 636, I still hope to prioritize using port 389.