Renewing Self Signed WebConfigurator Cert Breaks HA Node Access
-
Ran across something interesting today that I wanted to bring to peoples attention, or maybe I'm doing something wrong?
In an HA setup, the self signed cert for the GUI expired, I went ahead and renewed that on the primary node, this synced the cert over to the secondary; however, the secondary was still using the old cert and showed that no HTTPS certs were available in the admin access settings area (the correct cert was on within System > Certificates).
So I went ahead and disabled HTTPS temporarily to see how it would be have, but now whenever trying to login the Sign In button just redirects me to the login page again. The firewall then logs a successful admin sign in.
Rebooting, restarting web configurator, restarting php, nothing will resolve this issue.
So far I am still trying to get into this firewall so I can re-enable HTTPS.
This seems to be a bit of an oversight when it comes to HA setups.
-
As an update, I was able to resolve this, it required using a different browser, clearing cache, site data, etc... would not work with Chrome, no matter what, it still would just redirect to the login page instantly when pressing login.
Firefox, after clearing all data, was able to access it, now HTTPS is back enabled and working with the cert the primary node created.
I think there needs to be something done here to prevent this in the future though, renewing the self-signed cert which syncs over to the secondary node, shouldn't cause the secondary node to not use it.
-
@planedrop Can’t say I’ve run into that but don’t recall offhand the last time I renewed ours.
Was HSTS enabled by chance?
-
@SteveITS Yeah it's a bit odd, I'm going to spin up a test HA environment and mess with it some more to see if I can replicate the exact steps and figure out the best way to do this going forward.
HSTS was enabled, but I was accessing via IP address, unless I'm mis-remembering HSTS shouldn't mess with something that isn't via domain name.
Either way though, when the webConfigurator cert is renewed in the GUI, doesn't it restart the GUI and php? I guess the issue is the second node doesn't restart those services, so probably a reboot of the secondary would have resolved it?
-
@planedrop On our HA we are using a public cert for the web GUI because we have a wildcard cert we can use.
The self signed CA was renewed in Dec 2022 and I don't recall a problem but presumably it wasn't being used.
We have a FreeRADIUS CA and cert but again not being used by the web GUI.
-
@SteveITS Gotcha, yeah I probably should be using a proper cert anyway.
I'll still see if I can replicate this with another HA setup though and post back here.
-
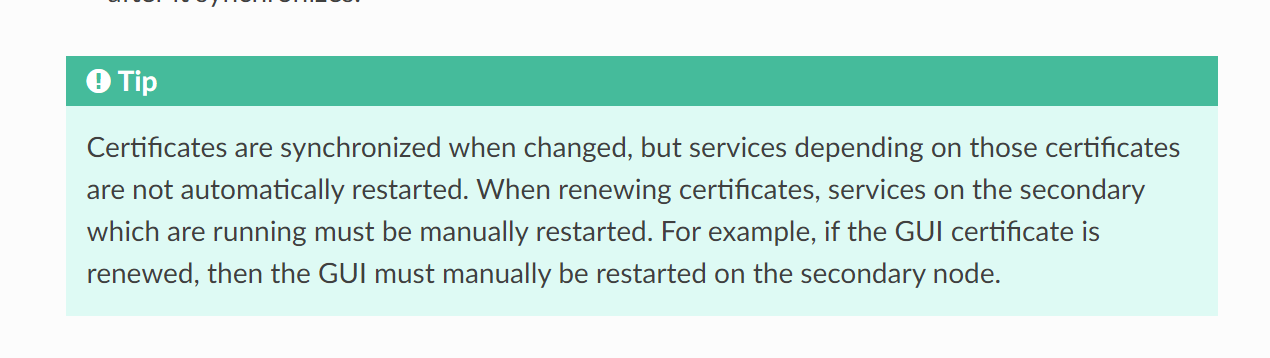
Finally got around to testing this and confirmed it is how it works.
If you renew the self signed cert in an HA cluster, it will replace the cert on the secondary, but the secondary will NOT start using this cert until the firewall is either rebooted or the webConfigurator is restarted.
I think this should be adjusted in the documentation so people don't end up locking themselves out or mucking something up. Or the other solution would be to figure out a way to force the webConfigurator to restart on the secondary node whenever this cert replacement happens in an HA cluster, but not sure if that's even possible without a lot of work.
IMO it might also be worth having a webConfigurator restart option in the Diagnostics drop down.
-
Remine created: https://redmine.pfsense.org/issues/15450
-
And it's been updated on the docs now, woohoo!
-
@planedrop FWIW I restarted our backup router just now. The "wait" counter never reset because our a/v was interrupting the "up?" check due to the self-signed cert. (this is not going to happen to most people, but is expected behavior in this case, with Bitdefender)
Turns out the web GUI was using a new "GUI default" cert that it created at the boot instead of the real cert I mentioned above. Not real sure of the path there. I thought when I posted above it had already been set to use the new cert, but I can't go back and look again, now.