So why is my firewall logs full of mDNS pings that should pass??
-
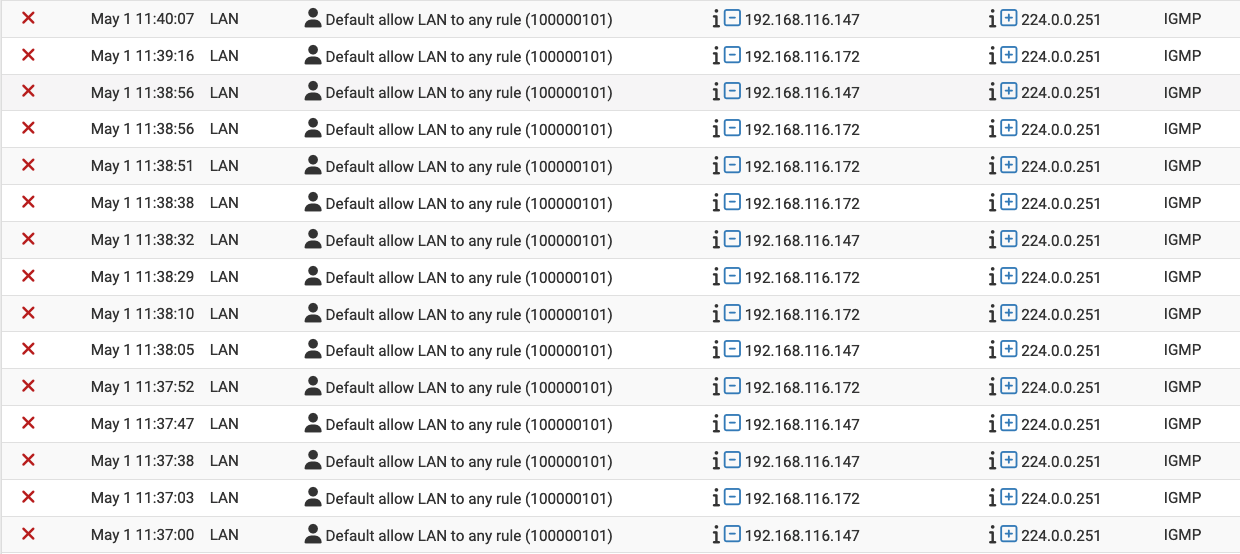
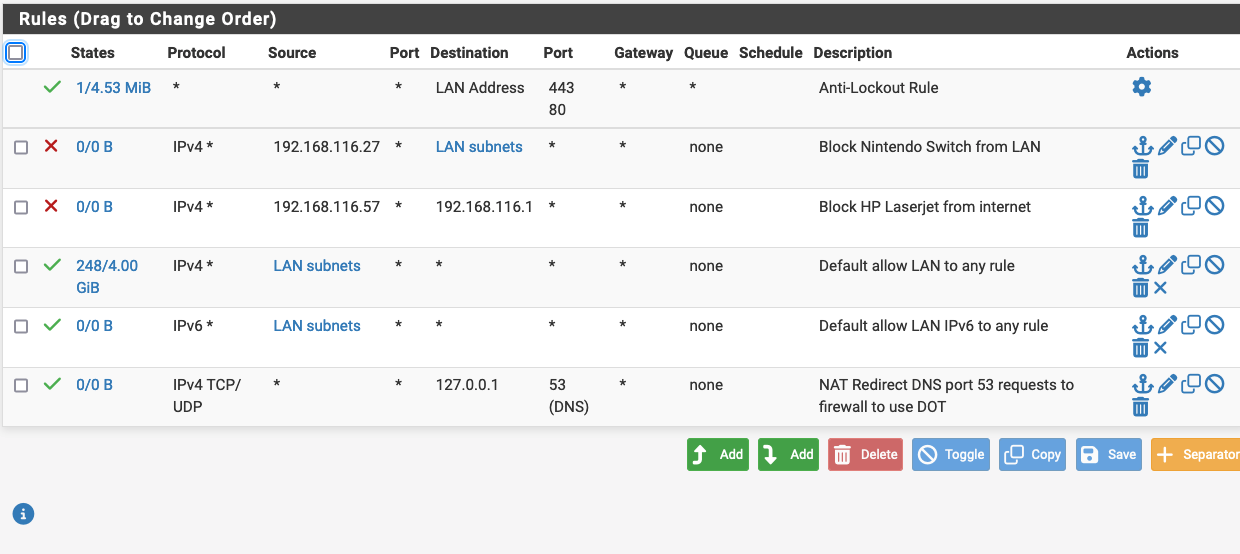
I've noticed that my firewall logs are full of blocked mDNS firewall ping entries that should pass. The default firewall rule is referenced but that rule is a pass any rule. Ideas? The pings are coming from 2 iPhones. I do have Avahi running but am not repeating the mDNS packets across subnets. I have attached log entries and my rules for LAN.
-
@jeff3820 Those are not mDNS, they are IGMP multicast group membership queries. They will be coming from your switch. They are showing up because IGMP has IP options set, and the "Default allow LAN to any" rule does not allow packets with IP options to pass.
-
@jeff3820 Here are a few references that will tell the story:
https://forum.netgate.com/topic/187316/multiple-users-24-03-r-20240410-1729-igmp-block-gets-logged
https://forum.netgate.com/topic/187663/just-installed-the-release-something-wrong-with-multicasthttps://redmine.pfsense.org/issues/15400
https://redmine.pfsense.org/issues/15415 -
@dennypage said in So why is my firewall logs full of mDNS pings that should pass??:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html#packets-with-ip-options
Thanks...that makes sense. I've allowed IO options on the default any rule and the logging has stopped!! Thanks.
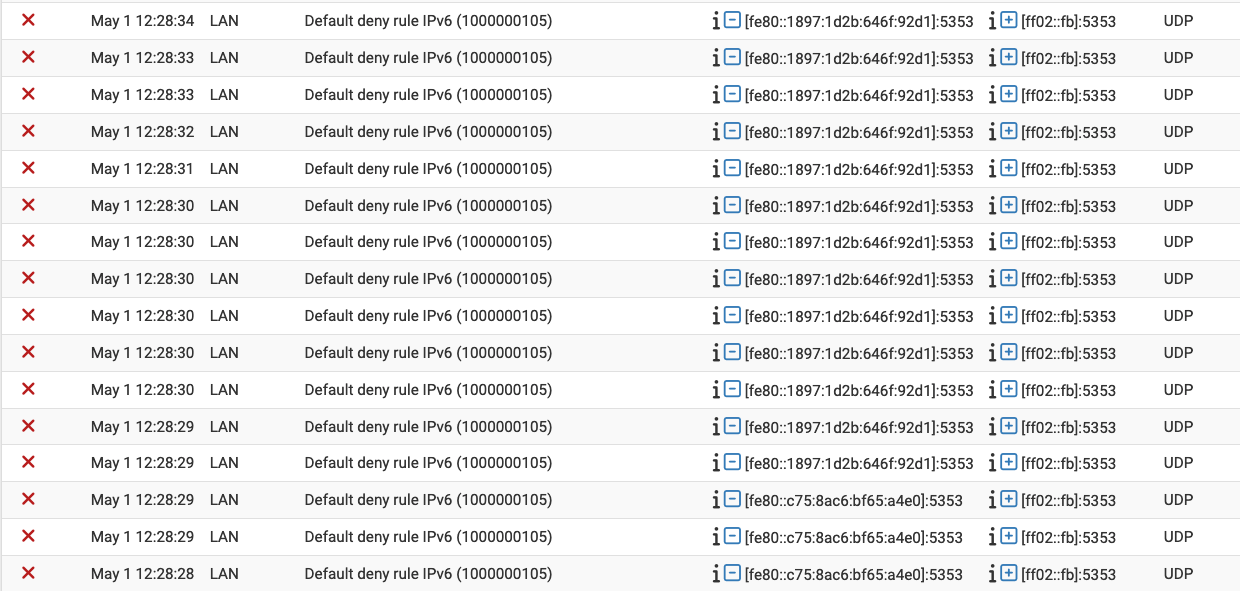
I also see this reoccurring entry in firewall logs...any ideas?
-
@jeff3820 now that is mdns.. and its ipv6 link-local can just create a rule not to log that, unless your doing something with avahi and breaking your L2 boundary for discovery pfsense sure and the hell not going to do anything with that - its just noise.
You can just not log it, but its still there. Or what I like to do is look to the source and try to turn off the noise. I do this for ssdp noise, and anything else mostly windows clients and apple devices that just create a bunch of noise on the wire or worse is when its wireless.
Windows you can easy turn off ssdp/upnp and mdns with a reg entry etc.. or just disable service.. I discovered one I had missed the other day, freaking msedge running stuff in the background and sending out freaking ssdp..
one of them in edge://flags/
Allow cast device discovery with DIAL protocol
Enable/Disable the browser discovery of the DIAL support cast device.It sends a discovery SSDP message every 120 seconds – Mac, Windows, LinuxAnd setting to allow extension to continue running in background, etc.. a few different things to toggle to turn down the noise..
1 packet ever couple minutes is not big of a deal.. But that looks like multiples a second your seeing.. Again not horrible.. but multiple that by a bunch of machines, if your trying to do packet captures it just fills them up if you don't filter on the capture.. Not a fan of noise on my wire.. Anything going on the wire should have an actual purpose.. Software or OSes looking for shit they are never going to find or get an answer to does not serve a purpose ;)
So when possible I turn it off at the source.. I have one that still bugs me, freaking plex sending out ssdp.. There is no way to turn it off, I looked and looked and looked.. Finally just blocked it at the freaking switch port ;)
Apple devices love to send out shit dns queries - like this
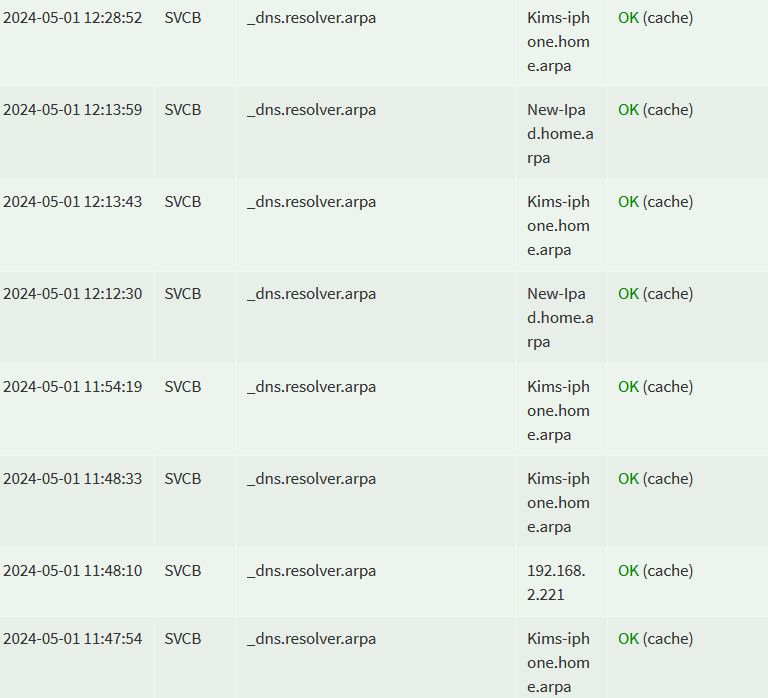
Dude your not going to find that - DDR (Discovery of Designated Resolvers) stop asking!! but have not been able to find a way to turn it off.. There are multiple other nonsense dns query that are not viable on my network.. I should be able to tell the device, hey if you want to send those when other networks fine - but when your on this network, it makes no sense!! stop sending them..
There is a bunch of stuff it looks for when it joins a network, sure ok fine - sure it makes stuff easier for some users, etc.. But you were just on this network 5 minutes ago.. Did you get any answers - NO!! so why ask again.. Hey if you hadn't been on this network in say 72 hours or something.. But you were just on it, you went to sleep and now your awake 5 minutes later, no reason to ask again I didn't enable it while you were sleeping for 5 minutes ;)
-
@johnpoz said in So why is my firewall logs full of mDNS pings that should pass??:
ipv6 link-local can just create a rule not to log that
I'm going to search for the sources but how can I create the rule not to log that traffic??...
-
@jeff3820 just create a rule at the end that blocks traffic on IPv6 to ff02::fb and doesn't log.. That log you show there is the default deny which is at the very end (hidden) and blocks anything that was not allowed..
Other option is just turn off logging of default deny, and just log what you want to log..
-
@johnpoz The block rule to ff02::fb worked great! Still looking for the sources...
-
-
@jeff3820 said in So why is my firewall logs full of mDNS pings that should pass??:
Still looking for the sources...
You most likely will need to sniff and see the mac address of the sender, then you should be able to at least get a clue to who it is by the maker via the first 3 of the mac, if its wired you can track that down to what port its plugged into. Wireless can block the mac and see who screams or what device stops working.
You could do the same on pfsense, once you know the mac you can see what actual IP it has and that can be helpful, maybe it registered a name with dhcp, etc.