how to stop logging blocked LAN IGMP?
-
Hey all -
My Netgate 2100 is logging blocked outgoing LAN multicast packets several times a minute. These come from the wireless access points on my network and some Windows hosts.The log entries list the block being performed by the default PASS rule for the interface, which seems odd on the surface, but it does look like that rule takes it on itself to block IGMP.
I believe this behavior is new since 24.03.
I don't want to log these blocks because it obscures more interesting log entries. Suggestions?
-
@JeremyJ-0 Here are a few references:
https://forum.netgate.com/topic/187316/multiple-users-24-03-r-20240410-1729-igmp-block-gets-logged
https://forum.netgate.com/topic/187663/just-installed-the-release-something-wrong-with-multicasthttps://redmine.pfsense.org/issues/15400
https://redmine.pfsense.org/issues/15415 -
@dennypage thanks for the information - looks like this has been thoroughly discussed but I can't replicate the resolution.
I tried checking the 'allow IP options' box in the advanced settings on the rule, saved and reloaded, and the behavior did not change. Apparently, the new code does not consider IGMP an IP option.
I tried copying the default pass rule, changing the protocol to IGMP and the action to block, and placing that rule above the default pass rule, and reloading (leaving the 'log packets' box unchecked, obv). The behavior did not change.
I think a code change that requires user action to preserve previous behavior deserves a mention in the release notes - and I don't see anything there to clue us in.
-
@JeremyJ-0 said in how to stop logging blocked LAN IGMP?:
I tried checking the 'allow IP options' box in the advanced settings on the rule, saved and reloaded, and the behavior did not change. Apparently, the new code does not consider IGMP an IP option.
IGMP is a protocol above IP. The 'options' refer to options at the IP layer. IGMP packets require the use of IP options. By default, the firewall blocks packets that have options are the IP layer.
To allow IGMP, you will need to have a pass rule that specifies Protocol IGMP, and has "Allow IP options" checked in the Advanced section.
-
Thanks, that explains it. I added 'allow IP options' to the new 'silent block IGMP' rule, and it works now.
-
@JeremyJ-0 said in how to stop logging blocked LAN IGMP?:
I added 'allow IP options' to the new 'silent block IGMP' rule, and it works now.
For me the IGMP-block-rule worked without the IP-options.
-
@Bob-Dig if you put in a rule to block igmp or destination before it hit your allow rule that would match on the traffic, like an any any where it would see the igmp, and say hey wait this has ip options set vs allowing this I am going to block it then yes your block rule without logging would work.
-
IGMP isn't a bad thing. On LAN interfaces, it is something you should pass rather than block.
If you really don't want to use IGMP, you should turn it off in your switch or router rather than blocking it on the firewall.
-
@dennypage good point.
I changed the 'silent block' to a 'silent pass', but it behaved the same as the default pass rule: it blocks IGMP (even though the rule is explicitly a pass) and logs each instance (even though the rule is set to not log).
It appears that the new release has some kind of special code path for this that defies normal handling.
So, back to blocking it. I don't have the skills or energy to turn off the IGMP sources on my LAN and I don't want those log entries.
-
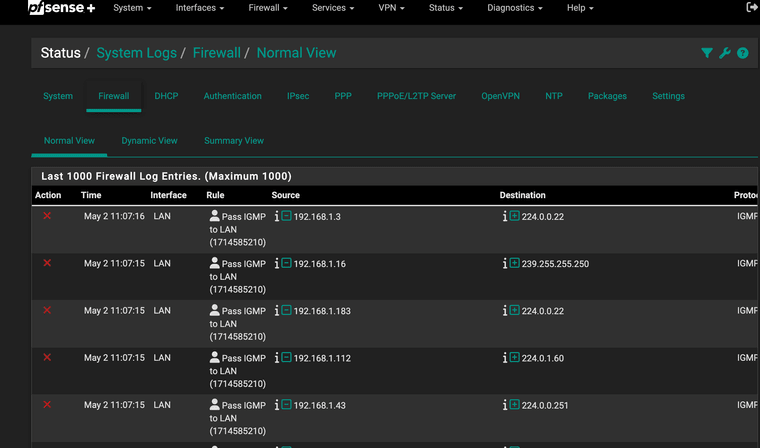
@JeremyJ-0 You have to have IP options enabled in the pass rule.
Edit: Mine is a floating rule, but here's what it looks like:
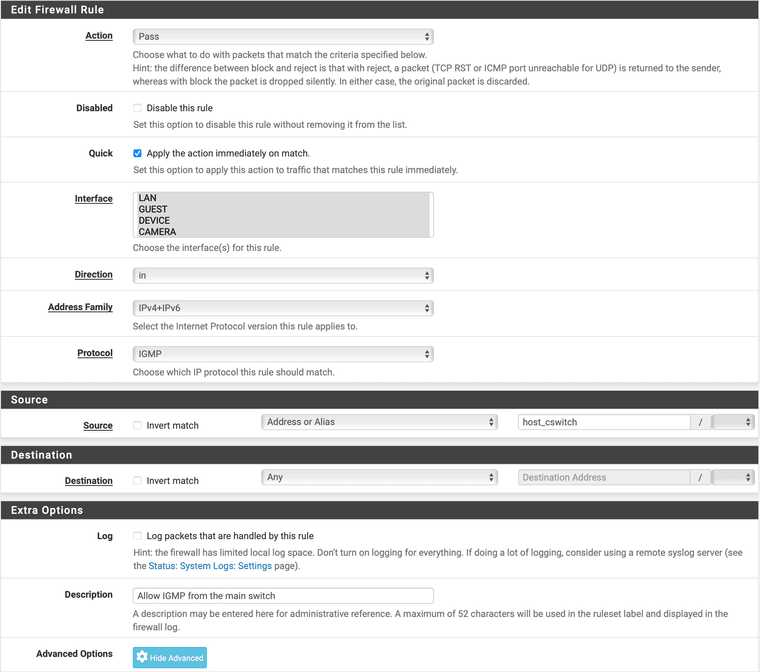
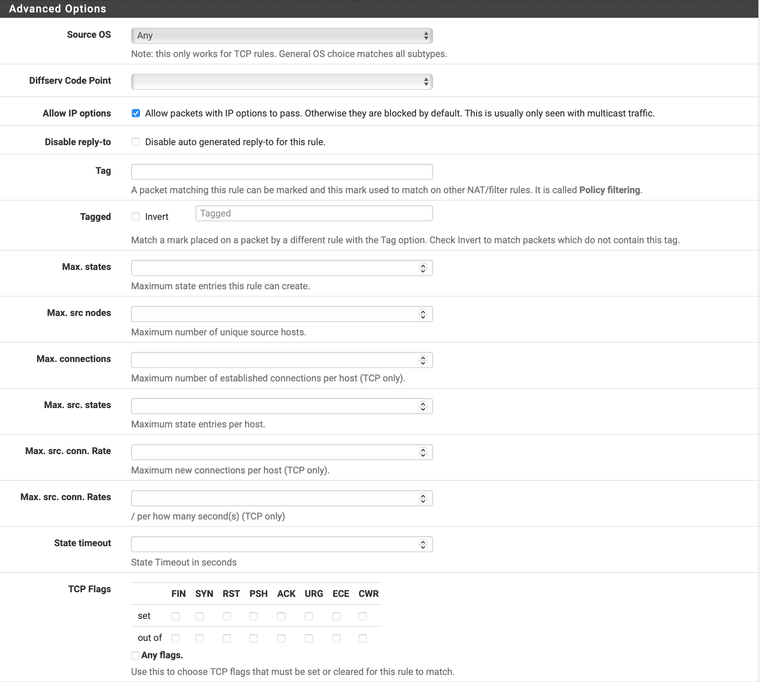
-
@dennypage actually tried it both ways. same result. it's silent as a block rule, and noisy as a pass rule.
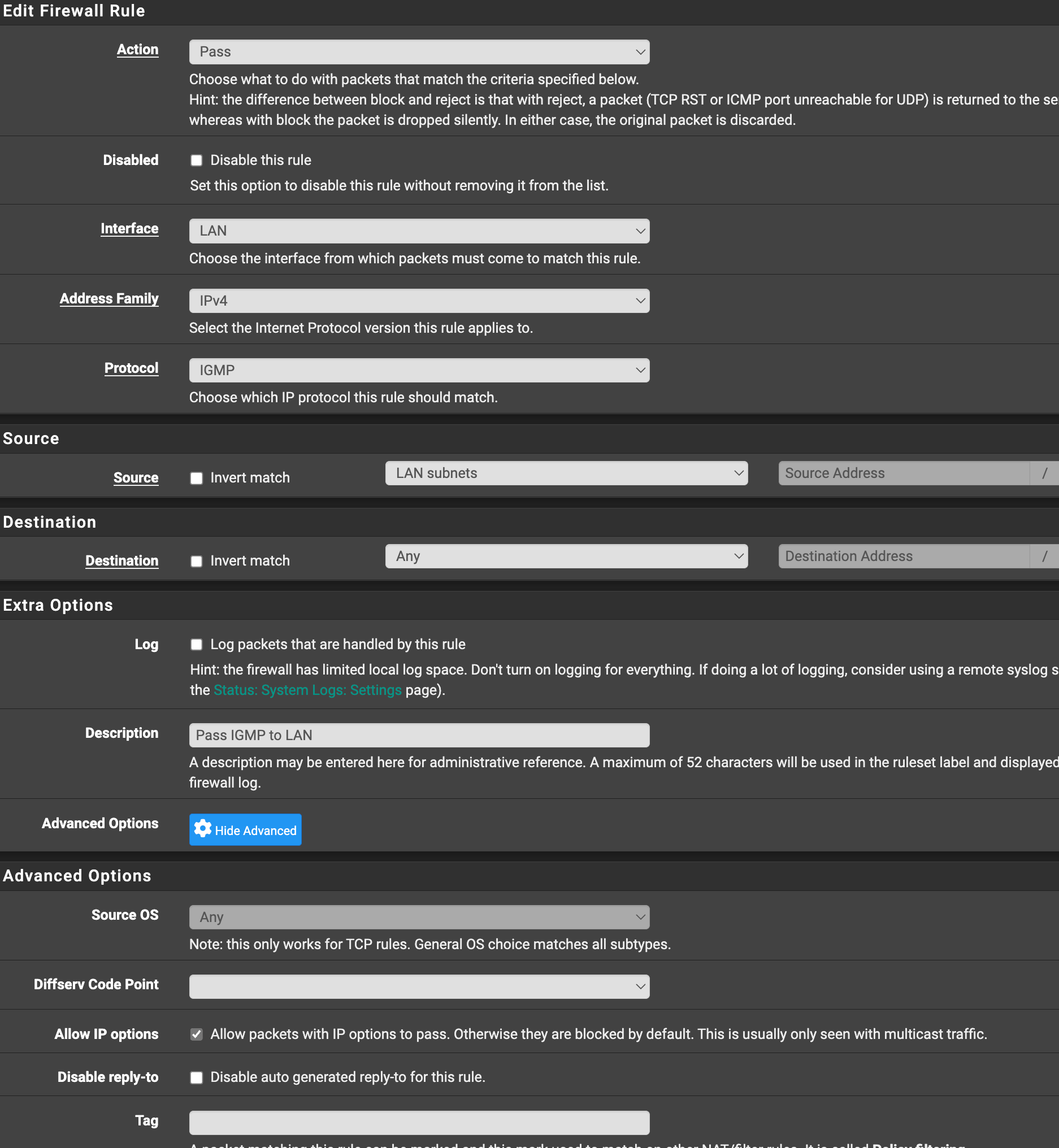
-
@JeremyJ-0 Source should be any rather than LAN subnets.
I edited my post above and put in my floating rule which handles IGMP.
-
@dennypage did my level best to match your rule: made mine floating, checked 'quick', changed direction to 'in'. It's not exact because I need it to apply to multiple sources where yours is specific to one so left source as 'all'.
Still getting deny entries in the log.
-
@JeremyJ-0 You do not need to restrict it. You can, and should, use "any" unless you have a good reason not to.
Do exactly this:
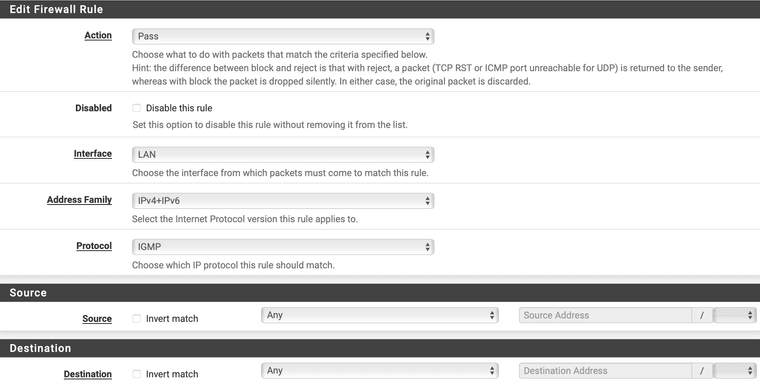

Make sure the rule is above your default allow.
-
@JeremyJ-0 Just to be sure, you are doing Apply Changes after modifying the rules, yes?
Btw, in Redmine 15415 there is a small patch that you can use to enhance the hover tooltip in the firewall log. It will show "block/ip-option" in the tooltip if the packet was blocked due to the presence of IP options.
-
@dennypage said in how to stop logging blocked LAN IGMP?:
It will show "block/ip-option" in the tooltip if the packet was blocked due to the presence of IP options.
Isn't that kind of obvious when the rule name is pass, but its a block and the protocol is IGMP ;)
-
Yes, I 'apply changes' and wait for the filter to reload.
Update: after the last round of changes (moving rule to floating etc.) things were worse: the silent block rule was logging the blocked packets too.
I rebooted. The excess logging stopped.
Is there some part of the firewall that reads the rules on startup and does not re-read on a filter reload?
-
@JeremyJ-0 said in how to stop logging blocked LAN IGMP?:
Is there some part of the firewall that reads the rules on startup and does not re-read on a filter reload?
Not that I am aware of.
The reload of rules failing would explain your results however.
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on
-
 K keyser referenced this topic on
K keyser referenced this topic on
-
Ran into the same problem today. I tried the suggestions in this thread, short of rebooting, but none work for me on 25.07.1.
I was trying to get the rules and packages right to pass HDHomeRun traffic from my Entertainment VLAN to the other VLANs.
I have had no logging of IGMP packets before doing the following:
I added package avahi but that didn't do it, so I removed that.
I then found and did discussed in the following referenced Reddit thread that solved the problem with passing HDHomeRun traffic to my other VLANs:
https://www.reddit.com/r/PFSENSE/comments/1g2c9qb/hd_homerun_across_vlans/
-
Added package udpbroadcastrelay, which, by itself did not allow the HDHomeRun traffic to pass across my VLANs.
-
Added a floating rule as specified. This rule does not log and allows the desired traffic.
Doing the above seems to have triggered the IGMP logging and there seems to be nowhere to turn it off. I get IGMP packet blocks on the Entertainment VLAN interface logged with a rule number I cannot locate anywhere. I went through all of my explicitly defined rules and none have the number referenced in the logs. (Aside: it would be EXTREMELY helpful to make these numbers hyperlinks that link back to the rule definition.)
I cannot reboot now but maybe will get a maintenance time at some point in the not-too-distant future.
This appears to be a noxious bug that would be valuable to fix. It consumes disk and log space with no value added, no request to do so, and no way to shut it off short of disrupting production with a reboot...assuming that works.
I'll be happy to take a stab at any other ideas to try to find this rule and shut off the logging.
Thanks in advance!
-
-
@Mission-Ghost Specifically on the IGMP issue, you have to add a pass rule for IGMP with IP options enabled. Like this:
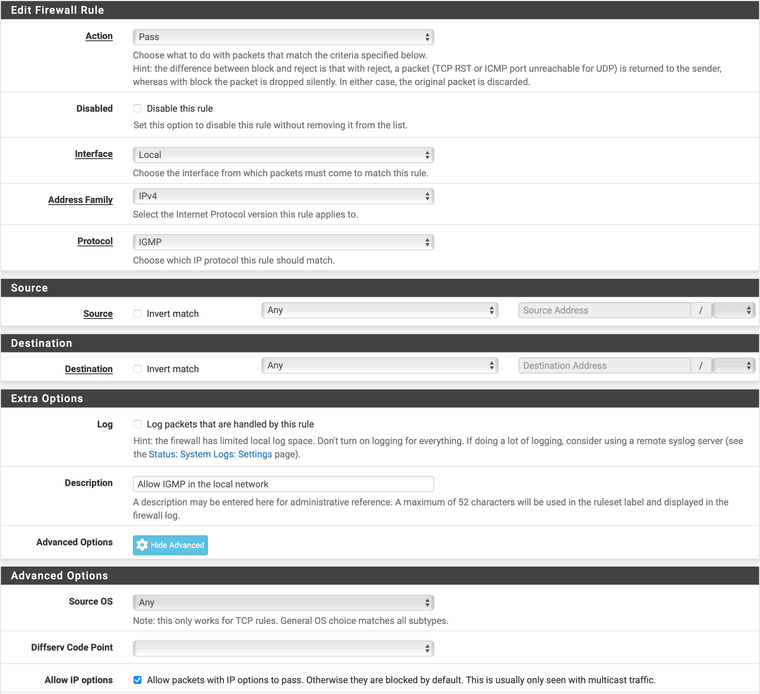
NB: Local on my firewall is an interface group that contains all the local networks (non WANs).
As to your parent problem, I am not familiar with HDHomeRun so I cannot offer advice regarding that.